This is the ultimate FAQ for Microsoft Active Directory — built to answer all of the most frequently asked questions about the legacy, on-prem directory service. We’ll get into the what, when, why, who, and how of Microsoft Active Directory — otherwise known as AD.
AD is both widely used and widely misunderstood. Developed by Microsoft in the late 1990s, AD is the world’s most well-known on-prem directory service and is often referred to as an identity provider (IdP). AD ushered in the era of modern identity management in the early 2000s, but with today’s shifting IT landscape there are a number of questions that IT admins and organizations have about what AD is, how it works, and why it matters.
Microsoft has extended AD, which it now considers to be a legacy product, from the LAN to the web with an assortment of services for user, device management, and security. This hybrid cloud paradigm expands its ecosystem with an emphasis on directing users to even more Microsoft’s technologies while retrofitting its local LAN solution for the WAN.
We’ve identified some of the most common questions about Microsoft’s approach to Active Directory device management identity management and answer them below. It includes guidance on how to modernize AD to meet new requirements.
Modernize Your Infrastructure
See why an open directory platform can help you to unify your environment.
Active Directory Basics
Active Directory is a directory service/identity provider that enables administrators to connect users to Windows-based IT resources. Further, with AD, IT can manage and secure their Windows-based systems and applications. AD stores information about network objects (e.g., users, groups, systems, networks, applications, digital assets, and many other items) and their relationship to one another.
Admins can use AD to create users and grant them access to Windows laptops, servers, and applications. They can also use AD to control groups of systems simultaneously, enforcing security settings and software updates.
Access and controls are enabled using the concept of a domain. The domain concept is essentially a concept of inclusion and exclusion. Traditionally, this approach was leveraged for physical locations. Historically, many IT resources were hosted on-prem and were a part of the domain — i.e., internal network — and when a user was in the physical location they would have access to all of their requisite resources on-prem. If a user was off-prem, they would need a VPN to make it appear that they were on-prem. This approach worked well when IT resources and people were in the same physical proximity.
AD is part of the wider identity and access management (IAM) space and is often supplemented with single sign-on (SSO) or mobile device management (MDM) solutions among many others. JumpCloud Directory Platform is a cloud-based alternative to Active Directory.
Check out our AD to Cloud “translation” guide. The guide is a Rosetta stone to help you understand the concepts and terms that are specific to AD and the cloud.
Microsoft first introduced the world to Active Directory in 1999 and released it alongside Windows® 2000 Server edition.
Active Directory takes advantage of the networking protocols for DNS/DHCP and the Lightweight Directory Access Protocol (LDAP), alongside Microsoft’s proprietary version of Kerberos for authentication within internal networks (LANs). Kerberos was considered secure when it was introduced during the late 1990s, but it’s now vulnerable to attack methods involving Kerberoasting, forged tickets, and stolen tickets. That means spending a lot of time and resources for mitigations and security controls to improve security. Failure to do so may place valid account credentials at risk.
Many people ask why AD doesn’t natively support more modern protocols, such as SAML, OIDC, and RADIUS. We won’t speculate on their reasoning, but we do believe that a multi-protocol approach is the future of cloud IAM architecture. Support for protocols such as SAML, OIDC, and RADIUS can be accomplished through Microsoft add-on solutions as well as third-party solutions.
Our best guess is that AD is called “Active” Directory because it actively updates information stored in the directory. For example, when an administrator adds or subtracts a user from the organization, Active Directory automatically replicates the change to all of the directory servers. This happens at a regular interval so that the information always remains up to date and synchronized.
Today, this “active” type of behavior is expected in IT systems. But, before the era of computerized directory services, the concept of a directory that kept itself up to date was pretty innovative. Keep in mind that when the Active Directory moniker was coined, physical encyclopedias were still commonly used and the “active” Wikipedia hadn’t yet launched.
Generally speaking, when an organization leverages Active Directory, every single employee uses Active Directory every day without even knowing it. People use Active Directory when they log in to their work machines and when they access apps, printers, and file shares.
But the primary users of Active Directory are the admins who operate, manage, and configure AD. AD admins likely include all of the IT team and may also include members of the organization’s security, DevOps, or engineering teams.
Virtually all organizations around the world use a solution such as Active Directory or other identity provider. Enabling and controlling access to IT resources is one of the most important aspects of operating and securing an organization. Solutions such as directory services enable organizations to be productive.
Whether people realize it or not, Active Directory has been making the business world go ‘round since the turn of the century. AD is in place at almost every large organization and many small ones. It’s a legacy foundational tool that hums away quietly in the background, so many people who use AD every day don’t even realize what it is — the secure access key to their laptops, applications, network, and files. In short, a directory service is what connects users to their IT resources, and AD has done that for users to their Windows resources for almost two decades.
Looking for a more in-depth answer? We have a blog that covers the purpose of Active Directory.
Active Directory Definitions
An object is the generic term for any unit of information stored within Active Directory’s database. Objects can include users, laptops, servers, and even groups of other objects (explained below).
AD enables admins to manage sets of multiple objects known as groups. Using GPOs (group policy objects), an admin can make a change to one group and have that change apply to all objects within that group. They’re often used to segment users or systems by department or clearance.
That convenience comes at the cost of IT security. Nested groups can be very useful if they’re used wisely. However, they can also be the source of over-provisioned users, putting at risk data confidentiality, integrity, and insurance. AD’s group management is manually driven, which offers the least mature level of entitlements management. Controls and measures are manual and ad hoc, entitlements are identified but need regular oversight, least privilege is policy driven, and remediation is manual.
The bottom line is that group-based management makes IT administration more efficient, but efficiency comes at the cost of security if admins don’t carefully manage identities and entitlements. Active Directory, developed nearly two decades ago, wasn’t designed with Zero Trust concepts as a guiding principle or for the web.
A forest is at the top of Active Directory’s logical structure, which also includes objects, trees, domains, and organizational units (OU). A forest describes a collection of trees, which denote a collection of domains. So, what are trees and domains?
Well, a domain is a collection of users, computers, and devices that are part of the same Active Directory database. If an organization has multiple locations, they may have a separate domain for each one. For example, an international organization could have a domain for their London office, another one for their New York office, and a third one for their Tokyo office. IT admins also sometimes isolate their user accounts into a separate forest to maximize security. These configurations aren’t rudimentary and oftentimes require hiring external resources to set up.
A tree could be used to group all three of those domains as branches belonging to the same tree, so to speak. An organization that has multiple trees could then group them into a forest.
This is a core concept of Active Directory and it can be complicated. If you have questions, drop us a note and we’d be happy to help you work through what type of AD structure makes the best sense for your organization. Meanwhile, check out the Active Directory to cloud translation guide for additional context and definitions.
A domain controller (DC) is any server that is running Active Directory Domain Services (AD DS). At least one domain controller is necessary to use Active Directory, though most organizations have at least two per location. Large, multinational organizations may require dozens of domain controllers across each of their physical locations in order to ensure high availability for their AD instance.
Generally, DCs are thought of as being tied to a physical office, which in the current remote work environment can be challenging. IT teams that are AD centric must connect remote users to their LANs through VPNs or alternatives including a software-defined WAN (SD-WAN) and secure access service edge (SASE). Otherwise, purpose-driven cloud services can more easily manage remote endpoints and identities with less infrastructure and overhead.
Individual users and their systems are connected to the domain controller through the internal network. When users request access to objects within the Active Directory database, AD processes that request and either authorizes or prevents access to the object.
Once within the domain, a user doesn’t need to input another username and password to gain access to the domain-bound resources that they have rights to. The authentication and access occurs seamlessly. That’s the beauty of the domain. But this concept begins to fall apart as non-Windows resources are introduced. It also struggles if users are remote and not physically attached to the domain — in this case, the end user will need a VPN to the network and be authenticated by the DC in order to gain access to their on-prem, Windows-based resources.
Note that Microsoft has also extended the concept of a domain to Azure. Organizations can create a separate domain at Azure through Active Directory Domain Services (AD DS). This domain is separate and distinct from the on-prem domains, although the two can be bridged through a variety of connective technology including Azure AD Connect and Azure AD. AAD is, however, a separate directory service from the legacy on-premises directory. It’s not possible to access Microsoft services such as Microsoft 365™ (M365) without AAD if your existing directory resides in AD.
Microsoft has also branched into mobile device management (MDM) and premium identity management services through its SKUs. Likewise, those are dependent upon AAD.
Gated Licensing Structure
Microsoft has implemented a gated licensing scheme for AAD services. For instance, there are two distinct subscription levels for AAD Premium; and other services for MDM, advanced identity management, and Zero Trust security policies are either included or available as separate subscriptions.
IT organizations often work with partners to navigate this web. We should also note that there is a new concept called the Domainless Enterprise, which takes the approach of eliminating the domain concept, but still retains the idea of securely and frictionlessly accessing IT resources wherever they may be through an open directory platform. This concept is especially helpful for organizations that leverage web applications, cloud infrastructure, and non-Windows platforms (e.g., macOS, Linux).
AD DS basically sets up the database of objects that serves as the foundation for AD management. AD DS isn’t the only server role associated with Active Directory, but you could argue that it’s the server role that corresponds most directly to the core functionality that people associate with AD.
Technically, yes, Active Directory can work for Macs. But the user and system management capabilities of AD are curtailed with Macs when compared to the functionality with Windows systems. Deep, automated control over Mac systems has conventionally been achieved only with the help of third-party directory extensions or MDMs (mobile device managers). Tight control over users including provisioning, deprovisioning, and permission modifications are also challenging on Macs when using AD. Microsoft provides Mac MDM for an additional cost.
We’ve put together a resource on this topic called best practices for integrating Macs with Active Directory.
Knowing how to use AD is a valuable skill — and one that’s broadly applicable at organizations worldwide. Learning AD is particularly valuable if you want to work in IT supporting Windows devices, Azure cloud services, SharePoint, and many other enterprise softwares and platforms.
However, it is possible to advance a career in IT without ever learning AD.
Modern, cloud-forward organizations are bypassing on-prem AD altogether and going straight to cloud-based directory services. You can practice with directory services by taking advantage of a free JumpCloud Directory Platform account. JumpCloud University can also help you learn the concepts around a cloud directory platform and the domainless enterprise.
How Does Active Directory Work?
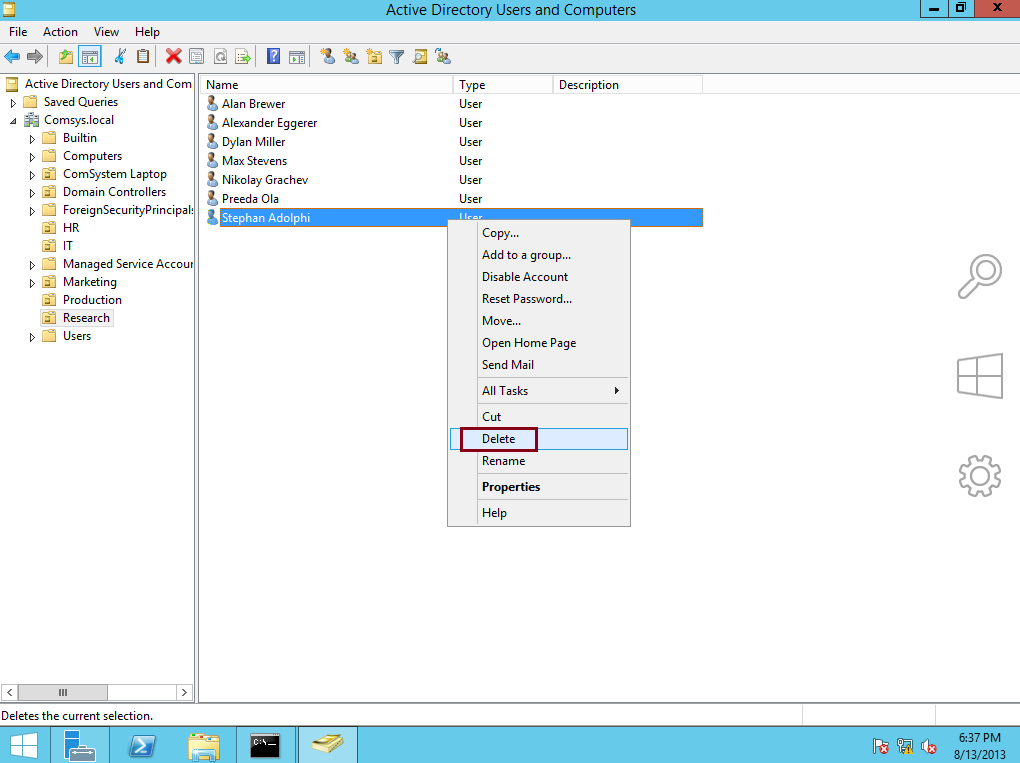
When Active Directory Domain Services is installed on a server, it becomes known as a domain controller. This server stores the Active Directory database, which contains a hierarchy of objects and their relationship to one another.
Active Directory is managed by an admin through a thick-client GUI (graphical user interface) that resembles the file manager in Windows (pictured above). This application runs on a Windows server and is not a modern browser-based application. Admins can point, click, and drag objects within AD and adjust their settings with a right-click via the mouse to access the dropdown menu.
AD can also be controlled via the command line and through tools that leverage PowerShell, Microsoft’s language for automation and API-level tasks.
Management Applications, Integrations, and Interfaces
Active Directory is managed on premises by several different applications. Many organizations opt to license third-party applications and snap-ins to simplify the experience, make workflows more accessible, and improve reporting. Applications also exist to integrate AD with Azure AD. AAD and Microsoft’s endpoint management products also have separate interfaces.
A change or workflow made in AD cannot be executed on AAD (and vice versa), so you have two different management paradigms, two different security paradigms, and two different interfaces and workflow potentials.
What Is Entra ID (Azure Active Directory)?
The biggest misconception around Azure AD is that it’s Active Directory in the cloud. But the truth is that Azure AD wasn’t built to be a standalone AD in the cloud. Instead, Azure AD is designed to extend an existing Active Directory instance to the cloud.
To better understand the AD and AAD relationship, Microsoft’s reference architecture diagram is helpful.
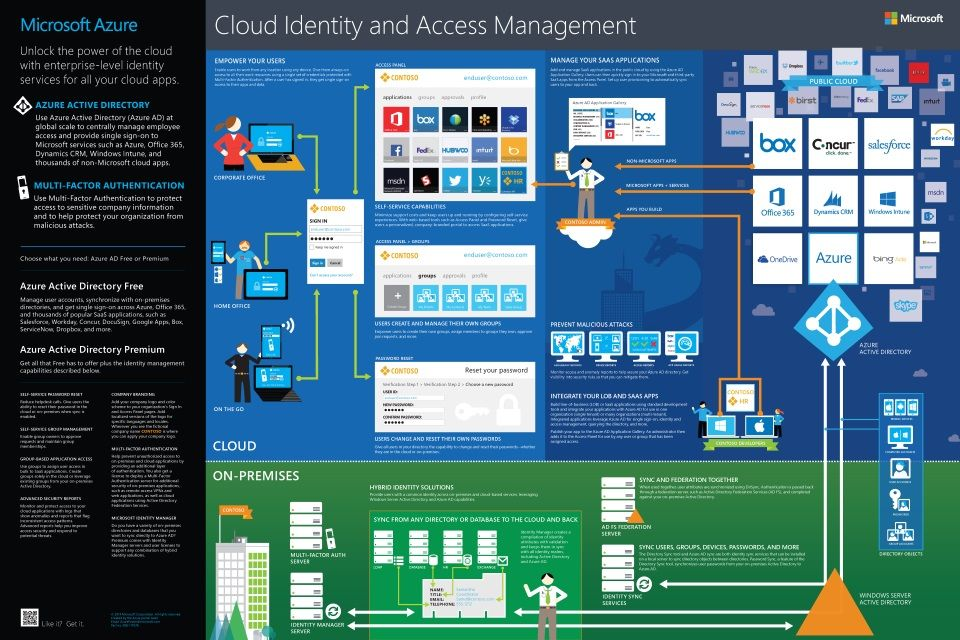
The concept has a lot of moving parts: you can synchronize your on-prem AD with Azure AD Connect and connect your existing database of user identities and groups to Azure cloud-based resources. Of course, you need Azure AD and then if you would like to create a domain within Azure, the Azure AD DS product as well.
Azure AD can do many things that AD can’t (e.g., it has an integrated web application single sign-on component) — and the wider umbrella of Microsoft’s Azure platform spans functionality so broad that it may be considered a competitor to Amazon Web Services. But don’t be fooled into thinking that means that Azure AD can do everything that on-prem Active Directory can.
Azure AD Connect is a tool used to federate on-prem Active Directory identities to resources that are hosted within the Azure platform through integrations with Entra. Features such as password write-back and group syncing are limited to premium SKUs. AAD does the “heavy lifting” to federate identities, and AD serves as an entry point to AAD. These resources could include M365 and Azure systems, servers, and applications. Users could experience limitations when accessing resources outside of the Microsoft ecosystem.
What AD Is and Isn’t
You could say that Active Directory was SSO before SSO existed. By that, we mean that AD provided a single sign-on experience for users by centralizing access to all Windows-based resources within the database. Further, those resources were all on-prem or at minimum connected to the domain.
That said, what the industry conventionally considers to be SSO (web app SSO) is very different from AD — and in fact, conventional SSO arose out of AD’s inability to authenticate users into web apps during the mid-2000s. Today, many organizations still supplement their Active Directory with a browser-based web application SSO tool.
Azure AD is Microsoft’s attempt at web SSO, but it’s optimized for the Microsoft ecosystem. Its interoperability starts to break down as you expand beyond Microsoft services — particularly to things that don’t support SAML or OIDC.
However, new business requirements have driven the concept of SSO to now extend to devices, networks, file servers, and more, so the modern concept of SSO goes beyond just access to Windows resources or even web applications. The concept of True SSO is even more expansive and highly relevant for modern organizations where users and their IT resources may be all over the world.
Yes, Active Directory is software developed by Microsoft that is installed, maintained, and updated on Windows-based server hardware. The AD software is licensed through a concept called CALs (client access licenses) among other mechanisms. Licensing for AD software can be quite complex, so discussing your options with a Microsoft reseller is your best bet.
Further, the AD software and hardware is not a complete solution. You need to procure other components to help make AD run including solutions for security, high availability, backup, VPN, and more.
Not exactly. Active Directory requires a Windows server in order to function. A server running Active Directory Domain Services software is known as a domain controller — whether that server is physical hardware located on-prem or virtualized.
It would be more accurate to say that Active Directory contains a database. The Active Directory database stores all the users, groups, systems, printers, and policies within the network. These are known as objects and can be manipulated by admins using Active Directory.
No. Active Directory was developed privately by Microsoft and its code has not been made available to the public like an open source tool. The primary open source alternative to Active Directory is OpenLDAP (others include FreeIPA, Samba, 389 Directory, and others). You can learn more about OpenLDAP vs Active Directory.
Active Directory isn’t LDAP, but it uses LDAP. AD is a directory service that is capable of communicating through the LDAP protocol and managing access to LDAP-based resources. AD’s primary protocol is a Microsoft proprietary version of Kerberos.
Active Directory Functionality
Generally, to operate AD you need a server, a backup, data center space, and VPNs. That’s just to get through the basics, but for most organizations you also need to figure out security, load balancing/high availability, data backup, and much more. You also need an IT admin who is technically adept enough to install, manage, and maintain AD.
Note that the hardware and software requirements necessary to operate Active Directory are unique to each organization. Some aspects to consider when determining what you need to operate AD include the following:
- Number of users
- Number of systems
- Level of RAM required
- Network bandwidth needs
- File storage capacity and performance demands
- Processing power
Accurately assessing your IT environment is crucial for effective use of Active Directory, and taking shortcuts could result in performance issues down the line. For more information, check out Microsoft’s capacity planning article. It is also recommended that you talk to a Microsoft reseller regarding licensing as it can be complex and include server software, client access licenses, and more.
Of course, if you have non-Windows systems, applications, file servers, and network infrastructure, you need to purchase add-ons as well such as web application SSO, multi-factor authentication (MFA), privileged access management, governance and auditing, and more.
Yes, there are limits in Active Directory. From maximum number of objects to maximum number of GPOs applied, Active Directory has its restrictions. Here are a few of them:
- A domain controller can create “a little bit less” than 2.15 billion objects during its lifetime
- Users, groups, and computer accounts (security principals) can be members of a maximum of approximately 1,015 groups
- You can apply a limit of 999 Group Policy Objects (GPOs) to a user account or a computer account
- You should avoid performing more than 5,000 operations per LDAP transaction when writing scripts or applications for an LDAP transaction
- It cannot support anything that is within the realm of Azure AD
It Cannot Address Modern Security Needs
Premium AAD subscriptions, several ad hoc Azure services, or third-party solutions are required to implement a Zero Trust security posture. Identity management is an essential aspect of the modern attack surface. Any unattended credential, or elevated access to applications or data, is of particular interest to cybercriminals. Therefore, compromising AD is the first step for hackers that want to penetrate the enterprise’s network.
As more companies migrate their operations to the cloud and workforces become distributed outside of on-prem network perimeters, AD is increasingly becoming a focal point for cybercriminals. While AD is not inherently insecure, the complexities associated with implementing it can leave the network susceptible to attackers. For example, cybercriminals can take advantage of replication processes in AD and steal signing certificates, potentially launching catastrophic attacks.
It Doesn’t Integrate Well with Third-Party Platforms
When Microsoft unveiled AD, most of the applications that companies used were largely Windows-based and resided in on-prem servers called domain controllers (DCs). However, web-based applications that are not native to Microsoft dominate today’s enterprise IT environments. Linux and macOS systems have also replaced Windows workstations in most organizations.
Since Active Directory wasn’t built with the integration of third-party solutions in mind, connecting non-Microsoft systems to the platform is a challenging task. While you could achieve integration with additional configurations, the process isn’t as seamless as how AD natively supports Windows-based applications. Microsoft’s cloud services aren’t much different.
Some of Azure AD’s identity and access management features don’t extend to non-Microsoft services, unless you pay more. Single sign-on (SSO) and multi-factor authentication (MFA) are examples of this.
Implementing AD Can Be Costly for the Organization
Active Directory is technically a free solution, with no additional costs if you’ve already subscribed to Windows Server OS. However, setting up SSO can be expensive for the organization and adds a higher total cost of ownership than anticipated. For example, besides the initial server and setup costs, you have to figure out the maintenance expenses. Microsoft’s core-based licensing approach has added complexity and costs for many organizations that are updating legacy hardware to newer server racks.
You can read more about other Active Directory limitations here. From a practical standpoint, there are limitations due to server hardware capacity, bandwidth, performance latency, and more. IT admins need to understand their entire infrastructure to identify how their users are impacted by these types of limitations.
Take a moment to think about all of the hard work you’ve put into creating a secure, seamless IT environment. You’ve nailed providing users with just the right amount of access in all of the IT resources they need to get work done. You’ve got all the right GPOs in place. Your logical structure is pristine.
Unfortunately, with no backup, you run the risk of having to start all over.
Not only is it a pain to set everything up again, but the rest of the company will be significantly delayed in getting back to work. Employees won’t be able to access their IT resources until you’ve rebuilt your Active Directory setup. So, having a backup strategy for your Active Directory instance can save a lot of pain and time in the event you experience a failure or disaster. For advice on what to consider for your disaster recovery plan, read this r/sysadmin Reddit post.
Of course, backing up AD is only one of the disaster scenarios that you need to account for: internet connections can be severed, hardware can fail, human errors can occur as well, and more. Those all need to be accounted for as well. As IT admins know, authentication services are generally a 100% uptime initiative.
Microsoft also cautions, “Choosing a more recent backup recovers more useful data, but it might increase the risk of reintroducing dangerous data into the restored forest.” It notes that there’s a trade-off between recovering more useful data and the safety of the restored data.
The estimated lifespan for a server is generally about five years. After that, you’re on borrowed time. If you’re still using Windows Server 2003 or Windows Server 2008, then you should definitely think about getting a new domain controller. The EOL for Windows Server 2003 occurred in July 2015 and the EOL for Windows Server 2008 was January 14, 2020. As mentioned, core-based licensing has replaced prior licensing regimes and might raise costs.
Organizations that migrate to the cloud from AD have ample time to decommission it. You can’t turn off AD until the last resource that requires it is also turned off. It’s possible to adopt more capable solutions for modern problems without prematurely “pulling the plug” on AD.
Are There Any Active Directory Best Practices?
When building out Active Directory infrastructure, there are some best practices that can help you maintain strong security and also avoid configuration issues. Here are a few recommendations (please note that you may require external consultants to accomplish these tasks):
- Change the default security settings: Attackers have a good understanding of the default security settings within AD, so it’s best to change these from their defaults (BeyondTrust).
- Consider having administrative accounts exist within a separate forest (Red Forest model) from other users by implementing authentication policy silos. This may require external experts and add-on tools to enact.
- Implement new Active Directory enhanced features such as protected groups, restricted RDP, time-based group membership and testing.
- Only make changes using dedicated administrative workstations.
- Utilize principles of least privilege in AD roles and groups: By giving employees the least amount of access that they need to do their jobs, you reduce the attack surface for intruders (BeyondTrust).
- Control administration privileges and limit accounts in the Domain Admins group: Similar to the point above, you want to minimize who has superuser access (BeyondTrust). IT admins should ideally never run as super users except for time-based intervals where accounts are temporarily elevated to perform tasks. This requires either additional setup or third-party security hardware and software solutions.
- Don’t use a domain controller like it’s a computer: In other words, don’t install software or applications on a domain controller. It is best if a domain controller is a server dedicated solely to this function. Generally, admins follow the concept of one server, one function (Iperius Backup). Supply chain management best practices should be followed.
- Patch AD regularly: Attackers can also easily exploit unpatched applications, OS, and firmware on AD servers. Some Microsoft defects permit attackers to go from a user to an admin in mere minutes. Avoid giving them this foothold by regularly patching (BeyondTrust).
- Monitor and audit AD health: Doing so will enable you to troubleshoot outages and other issues more quickly (Active Directory Pro).
- Define a naming convention at the beginning: This will go a long way in keeping AD organized as you scale (Active Directory Pro).
- Clean up AD regularly: Remove obsolete users, computers, and group accounts on a regular cadence. Doing so will help maintain security and organization (Active Directory Pro). Active Directory has no automation to accomplish this.
- Get your domain time right: Having the right time on all domain controllers, member servers, and machines is important for Kerberos authentication and for making sure changes are distributed correctly (Active Directory Pro).
- Maintain: These tasks help to ensure a healthy directory.
- Upgrade domain function levels to supported versions of Windows Server.
- Run Active Directory Health Checks.
- Don’t Run Your CA on Your DC: Setup the Enterprise PKI role to separate your certificate authority from the primary domain controller. That may require standing up another server.
- Set up Microsoft ATA (Advanced Threat Analytics): Do this to detect attacks against your server infrastructure that fall outside of typical system behavior(s).
- Compliance: Create documentation and contingency plans.
These suggestions could take five to six full days of work to implement, but are worth the investment in view of the multitude of security risks that AD is vulnerable to when it’s not hardened.
How Do You Secure Active Directory?
Many of the best practices listed above get to the heart of this: keep your AD instance patched and up to date, and utilize principles of least privilege. Don’t use your domain controller for anything other than the roles required for domain services. Administrative accounts should be isolated from regular users and only used to perform tasks. Never run as a super user.
When it comes to physical security, you should consider locking up the server room, having alarms at all access points, keeping the premises under video surveillance, and also setting up flood alarms and fire prevention systems. Server rooms often accumulate associated costs such as modifying a server room to be airtight as well as dedicated HVAC systems.
You also have to train any users who have access to AD about how to stay secure. Read our in-depth guide to security training, Security Training 101: Employee Education Essentials.
Of course, for many organizations the concept of physical security can be left to a cloud provider, if one is utilized.
There’s no one-size-fits-all formula for how to achieve high availability (HA) for your Active Directory instance. Different organizations have different uptime needs and standards. But redundancy is a “must-have” for all except the least risk-averse admins.
The approach we see most commonly at small to medium-sized businesses (SMBs) is to have one direct domain controller in the production environment and then a second DC to serve as a failover. An active server is responsible for providing IP addresses and configuration information to all clients in a scope or subnet and the secondary server assumes the responsibility if the primary server becomes unavailable. This general strategy of redundancy can be scaled up for larger organizations and enterprises.
HA Increases Administrative Complexity
It’s sometimes recommended that a HA cluster include separate hardware or even be located at a different physical location within a facility. Running AD in this mode changes management procedures. For instance, updates will have to be cycled per DC, and any software that’s required to run on a DC must be updated on each device.
There are a number of network infrastructure and hardware components that are necessary to ensure high availability, including DHCP HA. Many organizations are shifting to the cloud and leveraging cloud providers to help them solve the HA and load balancing concerns.
Microsoft’s enterprise access model supersedes and replaces AD’s tier model where there’s only a logical separation of AD assets within a single domain. The new model spans AD installations, is multi-cloud, and includes users from several IdPs. Microsoft has positioning Entra ID as the solution to this, along with a vertically integrated suite of tools and services. However, JumpCloud also offers conditional access, multi-factor and passwordless authentication, and the capacity to federate other IdPs.
image credit: Microsoft
How Do You Modernize Active Directory?
IT infrastructures have shifted to the cloud, and now support multiple device types, hybrid work, and much more — all in an effort to enable organizations to grow more quickly, access the best talent around the globe, and protect their organizations from a potential breach. Active Directory (AD) is a legacy technology that’s central to digital estates, but it doesn’t meet today’s requirements.
That’s because AD lacks the ability to explicitly validate trust for all access requests. This weakness, along with security vulnerabilities within Windows, has opened the door to privilege escalation through sophisticated techniques such as forged Kerberos trust tickets to gain unauthorized access within AD domains, or simply by taking advantage of poorly managed trusted PCs as an entry point into networks. AD treats the firewall, not identity, as the perimeter. Even AD’s Domain Isolation Zones don’t account for device state.
The likelihood of unmanaged endpoints extends far beyond Windows desktops and servers. AD was designed and built only to manage Windows endpoints, so any attempt to manage and control a heterogeneous OS environment will require additional tooling. More importantly, not every device that accesses resources via AD has to be compliant or managed. That includes devices that are employee owned or corporate owned and personally enabled. AD’s inadequate device management coverage enables attacks to occur.
AD also requires add-ons to provide single sign-on (SSO), privileged access management (PAM), and multi-factor authentication (MFA). AD lacks essential identity and access management (IAM) capabilities that are required for modern IT environments. Those include:
- Single sign-on
- MFA/user verification
- Conditional access/ZTNA policies
- Modern authentication schemes like OIDC
- Advanced user lifecycle management
- Cross-platform device management
Modern directory services, especially those born and managed from the cloud, fill the gaps in your identity security strategy by providing unified endpoint management (UEM) and introducing Zero Trust security controls to increase security. Microsoft has a prescribed path to modernize AD, which includes enterprise IAM and security services, and are all additional Microsoft-created/offered solutions. The path bakes AD into your infrastructure as a legacy technology that’s secured with additional subscriptions. Customers are locked into a hybrid architecture that mixes legacy on-premises technology with cloud infrastructure that’s entirely Microsoft centric (even when you’re using other vendors).
This is all prescribed without consideration to whether it’s appropriate for your organization or not. Its security services are now being recommended for all AD installations, even when organizations aren’t cloud-first and rely upon their on-premise instructure for user and device management.
Other options, such as JumpCloud’s open directory platform, may be a better fit for your organization. JumpCloud helps you to maintain the flexibility to choose products and services that matter to your organization while modernizing AD for you. It provides the IAM capabilities that AD lacks while integrating UEM to secure devices before they access your resources. Ultimately, it’s up to you to select the best technologies to modernize and secure AD.
This section outlines the architecture/approach to modernize AD using Microsoft. It includes all of the tools that you to need to buy and integrate together and the associated costs.
Microsoft’s approach to modernization isn’t simply about supporting your cloud services or the convenience of deploying SSO across all of your endpoints. Microsoft’s cybersecurity reference architecture (MCRA) prescribes using Entra ID Premium 2 and additional services to prevent lateral movement through its stack and to modernize AD’s defenses to resist today’s cyber threats. Standalone AD is vulnerable without modernization, and Microsoft is ushering its customers, even those with on-premise installations, toward its security stack as a supplement.
- Entra ID Premium 2 (P2) includes Identity Protection to detect, investigate, and remediate identity-based risks in organizations that have modernized AD by using Entra. For example, password spray attacks occur when attackers attempt to compromise accounts by using a curated list of passwords that may be associated with those users. Identity Protection assists with limiting the risk of identity-based attacks across its stack.
- Defender for Identity is a safeguard that protects against lateral spread through the Microsoft stack. It’s not included with P2 AD and can be licensed separately. Standalone AD is vulnerable to privilege escalation when unpatched (or zero day vulnerabilities) or misconfigurations are exploited to bypass its security. Microsoft provides protection against these flaws by selling you cloud security services with your Entra subscription.
- You cannot utilize Microsoft’s cloud security services for AD without adopting Entra ID. AD does interoperate with other identity providers (IdP), but it’s still central to your IT infrastructure.
This solution may work well for organizations that are all Microsoft shops, aren’t fully moving to the cloud, and have other resources to deal with security. Very large organizations that face compliance mandates may benefit from the enterprise compliance and security features.
Organizations that are evaluating Microsoft to modernize AD should consider these additional costs and potential risks:
Active Directory may be required indefinitely. Microsoft has a committed roadmap that has no definitive end date, essentially locking in the need for Windows Server and CAL licensing. Leveraging your cloud provider (e.g., AWS, Google, or Azure) and self-hosting Windows server to run a domain controller infrastructure prevents your organization from achieving a complete cloud architecture. By continuing to rely on 25+ year-old technologies, you risk integration and networking complexity and potential security vulnerabilities to your perimeter.
Entra ID and Microsoft Defender products are inherently complicated, from licensing through to implementation. This may require you to re-skill your team, onboard new hires at market rates, and enlist a vendor to handle the various automations and workflows you’ll have to build to make the most of all of the products that Microsoft bundles together.
- Entra changes frequently, and Microsoft’s reference materials suggest that an internal team would have difficulty keeping pace and could lose sight of higher priorities if they do. A vendor may “own” maintaining these crucial components of your tenant.
- Consider that these commitments make it difficult, if not impossible, to ever leave Microsoft.
You may lose the flexibility to select “best-of-breed” apps and tools. Microsoft 365 is horizontally integrated due to bundling. Microsoft will establish a presence within your infrastructure that extends outward from AD to the productivity apps that are at your organization’s disposal. Research demonstrates that employees are more productive when they’re able to choose the apps that are best for how they work.
Even third-party apps and cloud resources are managed through Defender for Cloud, if you follow Microsoft’s prescribed architecture. AD instances that run in non-Microsoft clouds are also managed by Defender for Servers. Modernizing AD by following Microsoft’s prescribed path(s) is essentially a generational commitment as a customer.
Microsoft provides UEM through a separate product called Intune. Intune also introduces new deployment options for Windows endpoints that aren’t available in AD. Windows Autopilot, which drives Out of Box Experience (OOBE) flows, requires Premium Entra ID licensing, even if you’re fully federated with another provider and not using Intune for any device management.
In summary, the following Microsoft subscriptions and tools are necessary to modernize AD:
- Continued licensing and support of your on-premises infrastructure
- Azure AD Connect or agent-based provisioning to Entra
- Entra ID
- Premium 2 is required to enable identity protection and OOBE provisioning for Windows; this safeguards against password spray attacks
- Premium 1 and 2 are necessary for password write-backs to AD
- Intune for UEM
- Defender for Identity to detect intrusions (optional, but recommended)
- Microsoft also recommends working with vendors to manage your configurations
JumpCloud’s open directory platform manages identities as an independent IdP, but it can also sync and federate with other IdPs. Integrated UEM secures access to resources from every device. Its cloud-based SSO adds support for web authentication and common network protocols with integrated MFA. The platform also features JumpCloud Go, phishing-resistant modern authentication that’s a hardware-bound credential. It also features:
- Pre-built integrations with popular HR systems
- A decentralized password manager with business collaboration features and management for when SSO isn’t an option
- Dynamic groups to automate lifecycle management
- SCIM provisioning and an API for authorizations
- Essential conditional access policies for privileged access management
- Certificate-based authentication for RADIUS to secure your Wi-Fi
- Reports and telemetry from your devices and directories
- Optional cross-OS system and browser patch management
JumpCloud makes it possible for a smaller team to accomplish more out of the box by integrating IAM and UEM without having to enlist outside vendors to implement it.
Learn how JumpCloud compares to Entra ID and Intune.
JumpCloud’s Active Directory Integration (ADI) provides multiple options for configuring AD to work with JumpCloud, depending on your company’s needs and objectives. ADI has a scalable deployment model that uses member servers to configure syncing with AD. It’s even possible to sync multiple domains to JumpCloud.
Evaluating Active Directory
This is a common misconception. While AD is technically included with Windows Server, the servers it runs on certainly aren’t, and Microsoft cleverly makes its money from AD customers through licensing to Windows Server. The cost of CALs (client access licenses) ensures that organizations using AD will keep paying Microsoft month after month.
But CALs are just the surface-level cost. We’ve created a guide to budgeting for Active Directory that includes the cost of associated infrastructure, Windows Server software, Mac and Linux® binding, identity federation, maintenance and administration, and security. The cost of AD varies widely from organization to organization, but it is never completely free.
We have a pretty straightforward equation for estimating the cost of AD:
Costs of Active Directory = servers + software + hosting + backup + security + monitoring + VPNs + IT admin + third-party SW + multi-factor authentication + governance
This free TCO calculator assists with these calculations. Further costs might include external resources to configure advanced AD capabilities for better security and high availability.
It is important to note that the real cost of AD for your specific use case is not always straightforward. If you would like access to our directory service ROI calculator, you can request one here.
The larger a company is the more likely it is to use Active Directory. Enterprises, universities, and government organizations all need directory services in order to efficiently and securely manage access to their thousands of IT resources.
While smaller organizations have been able to get by without Active Directory (some use Google Workspace or SSO solutions as their user directory), many small teams still choose to implement AD in order to improve security and efficiency. Usually, it’s when an organization grows to about 20 team members that the people responsible for all of the IT infrastructure begin to think that it’s time for directory services.
As organizations grow the cost and complexity to operate AD can scale dramatically. Many IT organizations have been searching for different ways to address this and ultimately look for Active Directory alternatives.
But Active Directory also comes with disadvantages:
To put it in terms of simple benefits, Active Directory offers these advantages:
- Greater administrative control over Windows resources
- Improved efficiency for users and admins
- More secure Windows systems, networks, and data
- Reliable and thorough reporting for auditing and compliance
But Active Directory also comes with disadvantages:
- Reduced functionality with Android, Mac, and Linux systems
- Difficult to configure and manage
- Potential requirements for third-party solutions and consultants
- Requires on-premises hardware
- High upfront costs
- Limited connectivity to cloud apps and infrastructure
- Higher costs and complexity to set up and license AAD services
Most anything that Active Directory does can be done on an individual system without Active Directory. For instance, setting up a new user for a laptop or instituting a certain security setting can all be done manually from the OS. But the key word there is “manual.” Active Directory is needed once an organization has reached a size where manual administration over its systems and IT resources is no longer feasible. The ability for AD to perform group-based management tasks across users and Windows systems, at scale, is what has made it a “must-have” at large organizations.
Another common reason Active Directory is needed is when an organization is subject to auditing and compliance requirements. The stringent security demands of regulatory statutes such as HIPAA, PCI DDS, and GDPR often “force the hand” of organizations that may otherwise not need AD.
As more organizations shift to the cloud, leverage web applications, utilize modern platforms, and more, the need for AD is waning, although the requirement for a holistic identity and access management solution is more critical than ever.
This really depends on your compliance needs — are you facing an audit from PCI, HIPAA, SOX, SSAE 16, or ISO? But the short answer is that you never need AD to pass an audit. Generally speaking, directory services can be very helpful in achieving compliance since they can (1) secure identities, (2) limit access to critical resources and data, and (3) simplify the auditing, logging, and reporting processes. Active Directory is only one of an assortment of possible directory solutions that can help boost your security.
Learn more about how JumpCloud helps with security and compliance.
Active Directory is ideal for on-prem, all Windows-based IT environments. If your IT environment doesn’t fit within this model, you should consider looking into Active Directory alternatives. For example, if you leverage Mac and Linux systems, web-based applications, cloud servers, wireless networks, or non-Windows files servers, you will need add-on solutions in order to integrate these resources with Active Directory. That includes integrating Microsoft’s cloud and on-premises solutions. In the long run, this will end up increasing costs and reducing productivity.
As many organizations shift to the cloud, the opportunity to use modern cloud directory platforms increases. These can create agility for organizations and save significant costs.
There are a few alternatives to Microsoft Active Directory. It all depends on what you want, but increasingly, compliance standards and security professionals stipulate that devices should be your perimeter. Every device is a gateway where identities access resources and should be managed to provide a baseline posture. Identity management and device management go hand in hand; it’s not possible to follow a Zero Trust security strategy with unmanaged devices.
The traditional on-premises competitor to AD is OpenLDAP™. You can think of it as the open source alternative to AD. But OpenLDAP isn’t really a true alternative to AD. It is a directory service, but it doesn’t match up with AD feature for feature, and the overall level of technical expertise to configure and maintain an OpenLDAP instance is demanding. Specifically, OpenLDAP doesn’t help manage systems (e.g., like the GPO capabilities of AD).
That’s where JumpCloud comes in. Its open directory platform provides unified endpoint management (UEM) and integrated IAM. Google recommends JumpCloud as the directory for small and medium-sized enterprises (SMEs) to manage Workspace users, unify device management, and secure access to every resource. JumpCloud also integrates with Active Directory, enabling use cases where SMEs that still require AD can expand its capabilities.
Open Directory Platform
JumpCloud’s open directory platform empowers your employees by provisioning the best resources from any vendor they need to do their job using the best protocol for each resource. Active Directory Integration makes it easy to modernize AD, even when you have multiple domains or the requirement to use AD as your authentication store. Its features include:
- Cloud LDAP is available along with pre-built integrations for other directory services, including Google, Microsoft, and Okta. JumpCloud also integrates with popular HR systems to help streamline identity lifecycle management.
- Servers use SSH keys, which are more secure than passwords.
- Passwordless certificates can secure RADIUS Wi-Fi access.
- Web applications use SAML and OIDC for authentication. A RESTful API is also available for integrations.
- An optional password manager for when SSO is not a possibility.
- Conditional access rules and biometrics for privileged access management.
- JumpCloud Go, a hardware-bound, phishing resistant credential.
- JumpCloud is also working to add federation to its platform to permit SMEs that use other identity providers to benefit from its UEM and other value-added services.
JumpCloud’s diverse feature set includes the robust, group-based system management that directory services are known for, but it does it across Android, Mac, Linux, and Windows devices — securely connecting a single user identity to all their workstations, files, network resources, and apps. It can work without a domain controller or extend what’s possible for SMEs that aren’t yet ready to leave Active Directory behind.
JumpCloud adheres to a Zero Trust security model with features such as MFA everywhere, pre-built conditional access policies, and a groups model that automates memberships and entitlements based upon user attributes. Attributes may be imported from an HRIS system, streamlining the entire identity lifecycle. JumpCloud also provides cross-OS patch management and IT remote assistance capabilities to enable IT teams to unify their resources.
The open directory platform integrates with AAD (and other) credentials to authenticate, authorize, connect, and provision identities to services. This grants you the flexibility to build and evolve your own IT and security approach without locking you into any specific technology choices. Your resources will change and so will your working patterns. The one foundation that can accommodate your organization now and into the future is JumpCloud.
Still Looking for Answers? What Did We Miss?
We want this to be an authoritative guide, so if you have any additional questions that we didn’t answer, please reach out and let us know. We’re also happy to take a swing at additional questions about AD or consider amending an answer if you can shed further light on one of them.
If you would like to try JumpCloud, you can sign up for a free trial.





