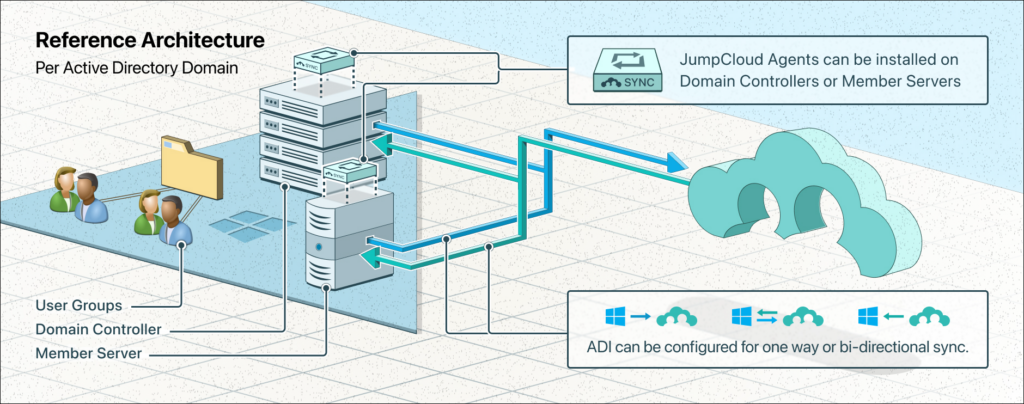
JumpCloud is an open directory platform that allows you to manage and secure user identities across devices, applications, and resources using multiple protocols. JumpCloud can integrate with Active Directory (AD) using the JumpCloud Active Directory Integration (ADI). ADI enables the syncing of user information and groups between JumpCloud and on-premise or off-premise AD and using the same user login for all AD and JumpCloud managed resources. ADI can be deployed in flexible configurations to support your specific use case, goals, and AD environment.
This article series presents the different configurations, workflows, and frameworks that can be leveraged for an integration between JumpCloud and AD.
ADI Deployment Configurations and Use Cases
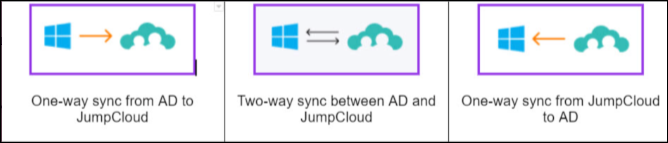
ADI can be configured to support a variety of use cases. The three (3) most common use cases for ADI are:
- Extending your AD environment to support additional capabilities in the cloud and greater flexibility.
- Minimizing the number of resources managed by AD without replacing your AD environment.
- Migrating away from AD completely.
There are three (3) possible ADI deployment configurations for syncing data between AD and JumpCloud.
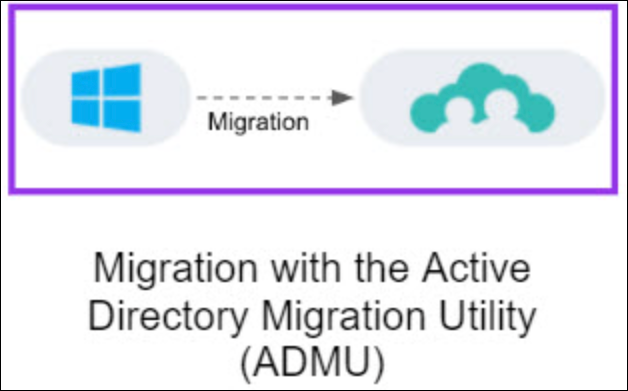
There is also an Active Directory Migration Utility (ADMU) for migrating device management from AD to JumpCloud.
JumpCloud Terminology & Glossary
The full integration that enables the syncing of users and groups between JumpCloud and AD, as well as a single login for all AD and JumpCloud managed resources. The integration consists of two agents; the Import Agent and Sync Agent. The integration can be configured to use one or both of the agents. Your use case determines which agents are required, the direction of the sync, and which system is the authority.
The JumpCloud Active Directory Migration Utility (ADMU) is a tool that automates the migration of AD domain users to JumpCloud managed users and AD bound Windows devices to JumpCloud managed devices. The utility automates the tedious steps required to convert AD user profiles to local user profiles that can be managed by JumpCloud, simultaneously removing the device from the AD domain and installing the JumpCloud agent. The utility can be used to a migrate a single device or many devices at once.
JumpCloud’s lightweight agent imports user identities and certain security groups from AD to JumpCloud. It can also be configured to import passwords if installed on DCs. It can be installed on all the DCs or one or more member servers. This agent pushes or sends all user, group, and, if applicable, password changes that have occurred in AD since the last sync to JumpCloud. Syncs occur every 90 seconds by default.
JumpCloud’s lightweight agent that pulls user identities, user groups, and passwords from JumpCloud and syncs that information to AD. It can be installed on one or more Domain Controllers (DCs) or member servers within an AD environment. This agent communicates to JumpCloud from the server(s) every 5 seconds to get all changes that have occurred in JumpCloud since the last sync, for any users and user groups connected to the ADI in JumpCloud.
The directory considered to be the source-of-truth or the primary or authoritative directory for user identities and groups.
A stand–alone instance of AD that contains a collection of one or more domains and acts as the security boundary within an AD environment.
A single AD domain within a forest that contains a collection of users, security groups, and other AD objects that share a domain name.
Two or more AD domains within a single forest.
Containers of objects within AD's logical structure in which security groups and users reside and can be nested. OUs are important within the ADI configuration as they are the search base used by the JumpCloud Import and Sync Agents.
The Security Group created by you during the ADI Import installation process and used by the JumpCloud Import Agent to determine which users and groups to sync from AD to JumpCloud. This Security Group will be created in the Configuration article’s instructions. Only members of this group are synced between AD and JumpCloud.
The main container or path containing the users and groups you'd like to sync between JumpCloud and AD. This can be a top-level OU, a sub-level OU, or the default “Users” container within AD. JumpCloud’s ADI is configured to reference this as the Root User Container for which all users integrated with JumpCloud should reside. The AD Import and Sync agents use this Root User Container as a search base by default. If users are outside of the root User container, or its sub-level OUs, but are bound to the JumpCloud ADI Security Group, then user identity or credential issues may arise between JumpCloud and AD.
Ready to Configure?
Check out the next article in this document series, Configure the Active Directory Integration (ADI), to determine which ADI deployment configuration is best for your use case. You'll get an overview of the benefits, example use cases, workflows, and implementation steps and a link to the step-by-step configuration article for each available ADI deployment configuration.
Want additional assistance from JumpCloud?
JumpCloud now offers a myriad of professional services to assist you with implementing and configuring JumpCloud. If you’re looking for assistance with Migrating from AD or integrating AD with JumpCloud, we recommend you reach out to JumpCloud’s Professional Services team on the following page: Professional Services - JumpCloud.
Learn More
Need help troubleshooting?
If you’re having issues getting JumpCloud’s ADI working, try Troubleshoot: ADI.
Want more information?
- [web page] Modernize Active Directory
- [eBook] Breaking Up with Active Directory
- [eBook] Modernize Active Directory: Break Free from the Limitations of AD
- [eBook] How to Modernize Your AD Instance: The IT Professional’s Roadmap to Augmenting or Replacing AD
- [blog] Modernizing AD is Possible
- Modernize Active Directory: Everything you need to know in less than 3 minutes
- [webinar] How To Modernize AD: An Admin’s Journey to IT Flexibility
