The most important thing to know about dynamic groups in JumpCloud is that it scales how admins manage users and devices via rules-based automation. Dynamic groups can improve security while optimizing IT management. Admins spend less time worrying about which users or devices are entitled to access resources and can achieve more mature lifecycle management.
Groups are a time-tested approach to access control, policy management, and authorization to resources from directories. Active Directory (AD) popularized groups in the early 2000s and simplified permission inheritance for trusted users and devices connected to a wire, behind a firewall, but not the open web. Requirements have changed dramatically with the establishment of Zero Trust architecture, distributed teams, and the accelerating pace of IT automation. Assigning memberships has become time-consuming and inadequate for today’s security needs.
Let’s take a closer look at JumpCloud’s groups and the use cases that they enable for small and medium-sized enterprises (SMEs), without charging a premium price for it. The platform’s integration of identity and access management (IAM) and unified endpoint management (UEM) enables scenarios where simple automations can deliver device compliance with less effort.
How JumpCloud Groups Are Different
JumpCloud’s approach to group management provides access control without the need for domain controllers or expensive hardware to bridge your offices. Its architecture is built on commonly leveraged user and device attributes and operators that add context and automations to IAM in a way that’s still accessible to SMEs. Dynamic groups create insights that translate into actions, such as proactively changing group memberships and enforcing multi-factor authentication (MFA) for users, or executing commands and installing apps for devices. Dynamic groups work alongside the option for making manual assignments as needed.
Policies that govern the user lifecycle and device compliance serve to continuously reinforce Zero Trust principles.
The capabilities sound very different from what’s possible with AD’s groups. That’s because JumpCloud’s attribute-based access control (ABAC) works differently. Attributes flow from directories or human resource systems, making it possible for instant cross-checks of users within a group to manage access to resources, as opposed to inheriting permissions from a hierarchy. The next section explores some of those scenarios and their practical benefits.

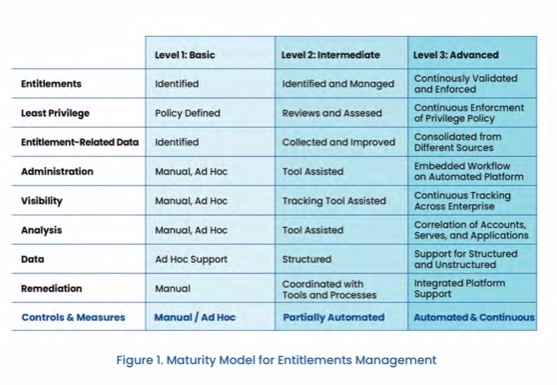
Dynamic groups advance your maturity model for entitlements management. Continuously validating and identifying entitlement issues delivers an “intermediate” level of controls and measures for this aspect of access control. Full automation will make it “advanced.” AD cannot deliver beyond “basic” maturity without add-ons and customizations, because user management is a manual process that adds to administrative overhead. Complexity is the enemy of security.
What’s Possible with Groups?
JumpCloud’s groups are collections of objects such as users, policies, and devices. These logical groupings make it possible to use a single platform for user and device lifecycle management. New organizations receive default dynamic groups to help categorize their users and devices from the onset; existing tenants adhere to those rules. Here’s what’s possible with groups:
- Dynamically manage user group membership based upon user attribute-driven rules. This can be either fully automated or require review.
- Dynamically manage device group membership based upon device attribute-driven rules. This can be either fully automated or require review.
- Dynamically manage device and user group membership based upon both user and device attribute-driven rules.
These capabilities coalesce into “smart” groups that unify and automate the process of managing devices and identities in a way that places less onus on administrators to keep up with organizational changes. It serves as an extra pair of eyes to verify that permissions are correct and that users aren’t over (or under) provisioned, based upon their job roles and supervisors. Permissions are no longer static and stagnate, which avoids security and user experience issues that could otherwise occur if access control was simply inherited by groups.
Rapid User Onboarding
User lifecycles start with onboarding, and JumpCloud makes it easy to import identities and attributes from identity providers (IdPs) including Active Directory, Microsoft 365, and Google Workspace. JumpCloud also extends support to HRIS services, to automate and schedule new user provisioning. Imported attributes can be used to determine group memberships, which saves admins time and mitigates errors, compliance, and security risks.
Google recommends JumpCloud for SMEs to manage users and devices.
Attribute-driven group suggestions work like this: after an admin imports someone from an HRIS with their department populated as “sales,” they receive a pop-up asking if they want to add a user to the sales group. The platform also has built-in SCIM provisioning and a REST API interface for custom integrations to reduce the workload to bind users to integrated applications.
Admins can automate the process of:
- Authorizing users to access resources
- Changing user permissions
- Adding users to downstream directory groups
- Provisioning resource accounts/licenses for users
Exemptions and Scoping
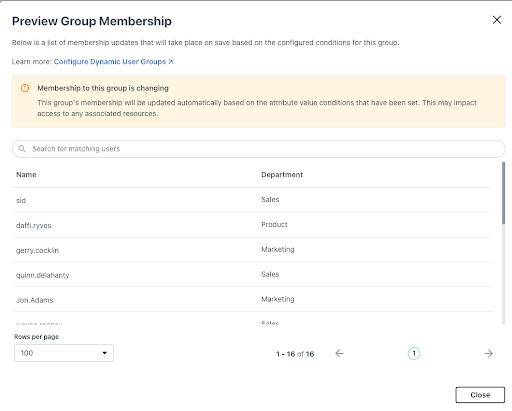
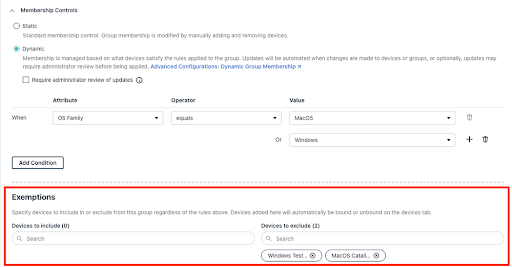
An administrator can also create exemptions for a dynamic user or device group by selecting whether or not that user or device should either (1) always be a member of the group or (2) never be a member of the group. Administrators can also make manual membership changes to a dynamic group straight from the users or devices tab. A user’s state is also considered (activated, pending, suspended) to scope out rules, depending on their status.
UEM and Device Lifecycle Management
JumpCloud’s UEM provides optionality to manage your entire fleet. It features:
- Agents to manage desktop operating systems with telemetry for auditing and reporting as well as unlimited remote assistance through the admin console. Other features include a command console and SSH key management for device administration.
- Enterprise Mobility Management (EMM) for Android.
- Mobile Device Management (MDM) for Apple products and Windows.
Device administration and lifecycle management activities follow this process:
- Establishing device groups for enrollment, deprovisioning, and reprovisioning.
- Setting your desired security posture by leveraging JumpCloud’s targeted policies and templates with policy groups. Automations may include managing software installation and security requirements around software access.
- Configuring admin access and policy application for endpoints.
- Executing commands and patching for system maintenance through the console.
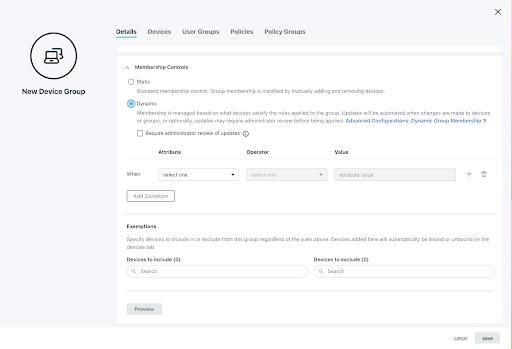
It all begins when admins configure dynamic groups to manage device and user group membership based upon both user and device attribute-driven rules. The security posture of a device is determined when a user is assigned to it. It’s then possible for admins to automate the process of identifying devices that need remediations to remain compliant, based upon criteria such as “last contact” or “out of security posture.”
Microsoft’s Entra ID only permits dynamic groups in its Premium 1 tier or above. It’s opt-in and intended for users only versus JumpCloud’s “first run” ability to make determinations.
Now, let’s explore some of JumpCloud’s UEM features in greater detail.
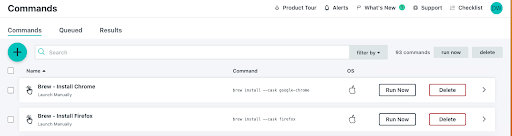
Commands
Admins have the capacity to execute commands against groups, en masse, with sudo access. Commands are currently in the process of being revamped for more automation and orchestration with granular queuing and timeout options. Groups can also be used to associate devices by operating systems (or other criteria) for patch management, a JumpCloud feature.
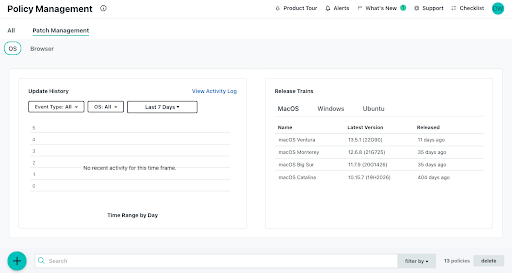
Patch Management
JumpCloud provides a unified patch management console, with full OS parity and browser updates, that leverages groups to organize devices for patch scheduling. The user experience is optimized for each OS to balance usability and security.
We’ve covered user access and authorization with device management; the next section focuses on assigning users to resources through single sign-on (SSO) and MFA.
Connect to More Resources, in More Ways
JumpCloud provides multiple options to connect to your apps, network and storage devices, services, servers, and more. Group memberships and rules grant (or remove) access; groups are bound to the respective resources. The following interfaces are included with the platform:
- SSO: JumpCloud believes that you should “own” your identity. The platform supports SAML SSO and OpenID (OIDC) for SSO connectivity. Admins can select from hundreds of preconfigured connectors or use custom configuration settings. Federation with other identity providers for scenarios such as UEM only is coming soon.
- RADIUS servers: The platform provides RADIUS services that can be used to log in users into devices and networks, such as Wi-Fi, along with custom VLAN settings.
- LDAP: LDAP connects users to anything that supports the standard without the overhead of maintaining your own servers or buying add-ons subscriptions.
- Password management: JumpCloud includes a decentralized password manager to support use cases where SSO isn’t an option and gets passwords out of browsers.
Authentication factors are configured at the group level, or when a group is bound to a service.
MFA and Conditional Access
LDAP, RADIUS, and SSO services all provide the option for push MFA via the JumpCloud Protect™ app. The platform can also be integrated with biometric factors, such as Apple’s FaceID. Admins can alternatively opt for TOTP (time-based one-time passwords) as an alternative. Push MFA is preferred, because it’s considered to be the most user-friendly method of authentication. JumpCloud Go is a hardware-bound credential that’s phishing resident to enable more passwordless workflows to complement automation via dynamic groups.
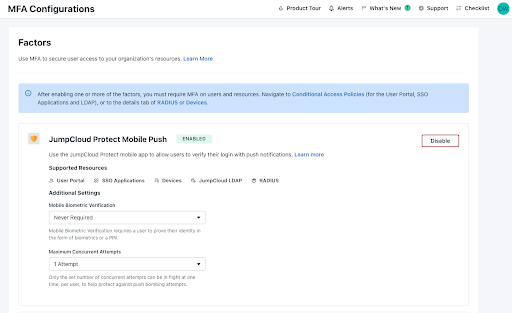
Some accounts require additional protection, so JumpCloud also offers optional conditional access policies that take into account the sign-in location of users, device trust, or dedicated IPs. Policies can be configured with specific application assignments and members can be easily bound to them from user groups.
Getting Started with Groups
JumpCloud Support provides detailed tutorials about how to get started with groups.
- Getting Started with Groups
- Getting Started with Device Groups
- Implement RADIUS Reply Attributes
- Configure Dynamic User Groups
- Configure Dynamic Device Groups
See Dynamic Groups in Action
There’s no additional charge for smart groups, which is a core platform feature that’s enabled from day one. Schedule a free demo today to learn more.





