Organizations are migrating to Microsoft 365 (M365) from Google Workspace at an increasing rate due to the perceived benefit of consolidating onto a single vendor that bundles many tools for one price. That strategy may work well for some organizations, but we postulate this increases risk, reduces agility, and locks-in organizations into Microsoft. With an explosion of cutting edge technology, there is no reason for organizations to compromise.
We understand that you have compelling reasons why you are thinking about switching from one foundational platform to another. But think of this transition as akin to remodeling your home — plumbing, electricity, replacing the roof, and everything else — while you are living in it. Since the business has no choice but to operate within a major renovation like this, the reasons to significantly overhaul the entire “home” should go well beyond simple costs or a technical preference from a few individuals. There must be sound logic on the business benefits.
Understanding the next order costs and risks of revamping your infrastructure is critical. These costs can be unpredictable and influence more than just IT budgets: your organization’s productivity and business agility are affected as well. The potential risks for IT and security also go beyond the traditional calculations. The act of mapping out the knowns, unknowns, and unknown unknowns is one of the hardest parts of the job and also one of the most important business considerations.
It’s a Collection of Products Either Way
One of the most compelling reasons to shift to a “single vendor solution” is that it’s a one-stop shop; a single product. Here’s the thing: an IT team may feel as if it’s consolidating its infrastructure with M365, but it’s really just shifting from one multi-product solution to another, but in the case of M365 you don’t get the choice to use best-of-breed solutions.
Each component of M365 has its own sprawl of challenges and complexities, as well as operational, support, and security considerations. Ironically, this migration could increase complexity in spite of your intentions to reduce it via M365’s bundling.
For example:
- Intune is separate and MDM must be enabled in Entra with Intune as the MDM “provider”. There’s even separate products within Intune, depending on what’s being managed, as well as add-ons including remote assistance that M365 doesn’t provide. Learn more about Intune pricing and inclusions.
- There are different products and interfaces for OS patching, depending on the OS.
- Even E5, the most expensive M365 SKU, doesn’t include security products such as Sentinel, which might be necessary due to the integrated nature of Microsoft’s stack – yet more costs.
- The interplay of different components and services is complex. Security architect level knowledge that’s unique to Microsoft is required to know the reference model(s).
One price does not equal integrated. You get all of these disparate tools and consoles, and then you need to do the integration. Just because it comes in one price and from one vendor doesn’t mean it is integrated. It’s more work for you and more on-going work in terms of management.
This article dives into some of the most impactful factors that your leadership should consider if you’re considering migrating to M365, focusing on potential business impacts as well as technical considerations. Those impacts will increase payroll, and change your organizational structure and procedures. Every organization will have different circumstances and considerations, and ensuring that a well thought out decision is made should be the goal.
Potential Business Impacts
The decision to lift and shift from one platform to another may appear to be a technical challenge, but the business implications of migrating to M365 are compelling enough to take them into consideration on their own. Consider the people who are living in your “home”.
Lost Flexibility
Standard Microsoft tools included in their bundle are being imposed on your organization when you migrate. Not only are they technically different, but Microsoft’s approach creates different use cases and different user experiences. The entire foundational IT platform is migrating, not just specific workloads or applications, and a great deal of upfront work is required. The impact on the employee user experience is often not well considered or even properly calculated as a critical factor.
Assume that you are going to be locked in to Microsoft indefinitely, and getting out is going to be extremely difficult. A key mechanism that Microsoft uses to do that is Entra ID (formerly Azure Active Directory) which ties many independently managed Microsoft services together. The deeper you go, the harder it is to change, and with break-neck technological innovation you should ask yourself what your organization could be missing out on in the next few years by being locked in.
You’ll have significant resources allocated into configuration, deployment, and training for Microsoft’s products. The larger an organization gets, the more it matters. This can become unmanageable and cause a significant burden on IT and close stakeholders, not to mention the learning curve for non-technical end users.
Cultural Resistance
It’s also important to consider how people work, how they’re willing to work, and what frustrations they might have when flexibility is lost. There’s a ‘culture’ around tools and platforms, and that could stall migrations, despite pressure from the top.
Don’t just take our word for it: Harvard Business Review (HBR) uncovered some stark findings with 59% of employees indicating that, “their collaboration tools are not aligned with how their teams prefer to work.” With Microsoft as the market share leader, it would seem to indicate that the majority of their customers are unhappy with their choices. HBR recommended empowering employees to have a voice in choosing applications that solve their business needs. With Microsoft, that forum is closed due to their tying and bundling within their suite. It seems as though choice is what the best people want.
There are cases where the move to M365/Azure never happens due to the fact that Microsoft is simply not popular within some departments and with different demographics, and usage is then limited to where it makes sense. Often, the full value of M365 is never realized and both platforms may co-exist. Even worse, some employees may just move on and work elsewhere if they become too frustrated with the tools they feel “forced” to work with. Their goal, afterall, is to get their jobs accomplished, not be tied to solutions that don’t support their work.
Fully Realized Cost of Moving
The potential downtime / loss of productivity for employees, cost of change management, and cost of program management should all be taken into account. The impact of these activities can become more widespread than thought and there may be considerations that you’re less able to anticipate. The greatest costs can be those that are least likely to be seen right away; only the most straightforward costs are likely to be calculated. In fact, past customers migrating have struggled with simple issues such as migrating calendars, the impacts of which may span from inconveniencing employees’ internal meetings to disrupting active sales opportunities, marketing campaigns, and project milestones. The main problem area surrounds business operations and productivity — costs that are not as easy to calculate.
In short, switching from one foundational platform to another isn’t always worth the lost effectiveness of your people.
Some of these cost centers from M365 migrations might include:
- Managing the lifecycle of documents that lack full compatibility
- Migrating calendars, collaboration technology, and compliance data
- Employees having to relearn productivity skills in M365
- Having to manage an increase in spam due to less effective email filtering
- Anything that makes you stop and say, “Oh wait, I didn’t think of that”.
Don’t be overlooked by your current provider. Voice your concerns, work with support, and consider talking about moving as a best alternative if your new needs aren’t being addressed. Regular communication could be all it takes to get the attention you need and solve the challenges you are facing.
Business Growth
While this example isn’t an everyday scenario, long term planning is essential and thus this consideration should be accounted for: flexibility extends to business growth strategies. For example, mergers and acquisitions (M&A) become harder to do, because you will need to migrate the acquired organization to Microsoft, which can be challenging even within Microsoft-centric organizations due to version incompatibilities. Let’s explore how creating a connected organization for M&A or subsidiaries would work in M365.
Entra ID has external collaboration settings that can absorb other organizations using M365 via cross-tenant access settings. That’s the best case scenario. Consuming other Identity Providers (such as JumpCloud or Google) and managing external entitlements is more challenging and could raise your costs if you require license upgrades in order to use Entra’s identity governance features.
IT’s focus will be on foundational capabilities for the Microsoft platform instead of empowering people to get work done the way they want to in order to solve business problems, as HBR recommends. Mergers are challenging times for employees, and aren’t the moment to reduce their flexibility.
M365’s B2B use cases are well-conceived, but will draw organizations deeply into Microsoft’s orbit, especially if you have to allocate external resource(s) to support your migration to M365. Microsoft has a mature partner network, but engaging with it increases your dependence and costs. Greater dependence means less flexibility and more lock-in, horizontally, across all services.
Supply Chain Management Risks
Lock-in is not just about lost flexibility; it increases the power of your single supplier, the vulnerability of your supply chain, and, ultimately, the risk of disruption. Total dependence on Microsoft’s stack makes it difficult to onboard new software providers to manage vendor risks. It’s unlikely that the aggressive pricing that Microsoft is giving SMEs will last forever. In fact, Microsoft has a strong history of providing significant incentives for organizations to shift including paying for licenses, migration services, and more, but once the new platform is in place, the discounts evaporate and customers cite continually increasing prices.
Technical Considerations
The M365 platform features a patchwork of many services, integrated into a whole. Microsoft-centric organizations may find its interfaces to be familiar and welcoming, but licensing, training, and its overall complexity are important considerations for prospective buyers. There are also security risks via lateral movement given its security monoculture and tiered pricing model for its security tools.
Challenging Implementations
Reskilling your existing team and/or obtaining external resources is often necessary during a full platform migration. You should also consider the potential cost to raise salaries to match market levels for speciality admin roles as more and more M365 features are implemented. Also examine potential changes to organizational structure and procedures in order to fully implement all the products that you’ll be paying for.
For example:
- Defender for Cloud apps integrates with Entra, but it’s a separate console and requires a unique skill set that an admin will become a designated expert in. The same goes for features such as Privileged Identity Management (PIM), which many admins must participate in. Using certain M365 features will expand your organizational chart.
- Even the same product can have a different admin UX depending on licensing. For example, Entra ID Premium 2 has identity governance, which introduces a different experience for enabling multi-factor authentication (MFA). It’s also important to know how roles work in Entra and when additional (or different licenses) are necessary.
- Understanding those intricacies takes considerable hands-on experience and training. More products and licensing options can be a selling point for organizations that are migrating to M365 from Google, but that flexibility adds complexity.
- There’s just a lot of material to learn. A junior level admin can cause a lot of harm without the appropriate support and knowledge of M365 administration. The solution is to either expand your team using separation of duties and RBAC for admin roles or to purchase Entra ID Premium 2 (P2) for PIM to elevate admins on a case-by-case or group basis. Access reviews are recommended for larger teams following RBAC, which also requires P2.
Despite all of this, M365 makes sense for some organizations, but migrating Workspace to M365 is often cumbersome and disruptive no matter how well the requirements fit. Even if you’re fairly big, Microsoft is not flexible and throws the standard tooling on your plate, and doesn’t solve everything you need for business continuity without facing major obstacles ahead.
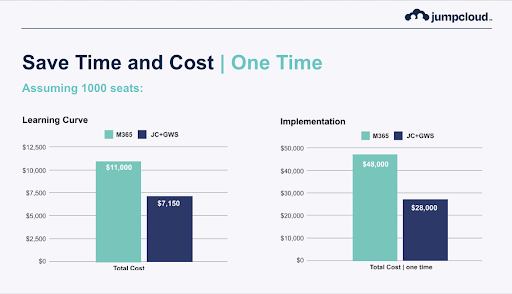
Image Credit: JumpCloud. Data is based upon what JumpCloud customers have experienced.
Security Risks
M365 is a monoculture solution that introduces unique security risks where hackers can navigate through the Microsoft stack. Cloud vulnerabilities in Entra, and the subsequent incident response, led to espionage against the United States, prompting a Department of Homeland Security (DHS) security review. Lateral movement from service to service and down to the datacenter is possible. A breached cloud identity can lead to privilege elevation on premise.
No system is totally secure, but software monoculture leads to unique risks. For example, legacy apps are a selling point for end users but also introduce vulnerabilities to mitigate and patch. This highlights the importance of security controls that are independent from M365, and continuous.
Microsoft has features to detect and try and prevent lateral movement, but they’re gated licenses:
- Identity Protection is protection that seeks out exploited credentials is an Entra P2 only feature.
- All features for user risk and anything identity governance related is also P2.
- Even M365 E5 doesn’t include Defender for Servers, which protects virtual machines and other server instructure that’s tied back into Azure cloud services.
- Sentinel threat hunting / SIEM is an add-on, even to M365 E5.
Microsoft continues to struggle with securing their platforms as evidenced by numerous breaches. It’s critical that as a potential customer you understand the risks that you are absorbing due to this decision. Objectively, Google Workspace has better security, with even reputable cyber insurance providers preferring the solution over M365.
Google WorkSpace Better Secures Email
Google Workspace is outperforming Microsoft in a vital way: email security. According to Coalition, a leading managing general agent for cyber security risk:
The risk of claims for business email compromise (BEC) and funds transfer fraud (FTF) events were found to be equally as bad with M365 as on-prem Exchange. This is in stark contrast to companies using Google Workspace, which experienced a 25% risk reduction for FTF or BEC claims and a 10% risk reduction for ransomware claims.
During the first half of 2023, organizations using M365 email were more than twice as likely to experience a cyber insurance claim as Google users.
Control Your Identities for Flexibility, Independence, and Security
If you are intent on going down this path, we strongly suggest one key thing to do: keep your identity provider independent. You will have very little hope of getting out and/or leveraging other tools, e.g., Macs, Linux, AWS, Zoom, Slack, Salesforce, CrowdStrike, Gmail, etc. if Microsoft “owns” your identity. Keeping your identity independent makes it possible to:
- Retain freedom of choice and lower supply chain risks
- Enable teams to be more productive (they can still use other tools that are better for them)
- Avoid monoculture security risks
- Increase agility/flexibility
- Utilize security controls outside of a single cloud provider
Going “all in” Microsoft can provide benefits, especially when many helpful products and services are bundled, but you could be creating some significant new risks. If you want to go down that path, you can manage that risk by keeping the identity provider independent. It’s also important to account for the process management impact of trying to do too much at once. A company is made up of people who use technology as tools to work. A major disruption impedes their work, which is what supports the business’s financial and strategic objectives.
Have A Discussion With JumpCloud
This article highlighted important considerations that are not typically covered in a standard evaluation, but ultimately the best thing you can do is to talk to the vendors you have in front of you to make sure that everything is understood and covered. Whatever your decision ultimately is, it’s important (to us too) that you have all the information you need. Contact us and connect with your account team and JumpCloud experts today; we’re committed to giving you all the time you need to get exactly the information you need to the right determination.




