Microsoft has established itself in identity and mobile device management (MDM) markets through Microsoft 365 (M365). Many organizations, especially managed service providers (MSPs), are considering Entra ID (formerly, Azure Active Directory) with Intune™ for access control and unified endpoint management (UEM). This solution most strongly benefits the Microsoft ecosystem alongside features to support other platforms, and is a gateway to a broad portfolio of security products. Many of its capabilities are designed with enterprises in mind and implementing it can become resource intensive. M365 provides an expansive bundle of features and products.
JumpCloud takes a different approach with its open directory platform, which can consume identities from multiple providers and enable frictionless access into a wide variety of resources using standard protocols. The platform is designed so that small and medium-sized enterprises (SMEs) can follow Zero Trust security strategies in identity and access control (IAM) by combining access control with UEM. It automates the user identity lifecycle for organizations that don’t have large IT departments to implement those technologies.
JumpCloud’s Multi-Tenant Portal also makes it possible for MSPs to provision the best resources, from any vendor, to build out their optimal stacks to take on new clients.
SMEs may have a difficult time selecting the appropriate solution when Microsoft and JumpCloud both provide cloud-based IT management tools for identity management and device management. There are, however, some differences and important considerations IT teams should be aware of. This article examines how they compare and the best fit for each platform.
What Is Entra ID (Azure AD)?
Entra was created for the express purpose of extending Microsoft’s presence into the cloud. It connects users with Microsoft 365 services, providing a simpler alternative to Active Directory Federation Services (ADFS) for single sign-on (SSO). There’s similar nomenclature, but it doesn’t replace all the features of Active Directory and lacks support for key authentication protocols including LDAP and RADIUS without add-ons. It provides SSO and multi-factor authentication (MFA) for the Microsoft ecosystem as well as some external resources.
Microsoft uses a structured gated licensing model with trial subscriptions and a free tier of Entra with some restrictions. For example, there are limits on stored objects and the number of apps a single user can access with SSO and group management with role-based access control (RBAC) costs extra. Microsoft also charges for MFA for external identities. Entra’s features, which include some time-limited trial services when users sign up, are listed on its website.
It also serves as Microsoft’s approach to a multi-tiered portfolio of identity, compliance, device management, and security products. The permutations of its cloud products, and challenges of migrating from Active Directory to the cloud, have given rise to a cottage industry of consultants. This is due to the breadth of configurations, and resulting complexity, that many enterprise use cases require. However, some organizations may benefit from this approach. Integrations with other Microsoft services are aggressively marketed, and are oftentimes bundled together.
What Is Intune?
Microsoft Intune serves as a UEM solution to administer features and settings for Android®, iOS®/iPadOS®, Linux, and Windows. Windows receives the deepest level of support, but Microsoft is increasing its coverage for other platforms over time. For instance, Intune supports custom/templated profiles for macOS, compliance policies, shell scripts, Apple Business Manager (ABM), and user/device enrollment options. Linux support has rolled out slowly and focuses on compliance policies. Microsoft Edge is obligatory to utilize some of its features, such as conditional access policies for privileged users, extending Microsoft’s overall footprint.
However, Intune bolsters Microsoft products such as Edge and Configuration Manager as first-class citizens. Windows administrators will be familiar with aspects of how it works, such as ADMX templates. Intune is most robust when it is used to manage Windows systems that are hybrid AD-joined, in combination with other services and security solutions. Separate license requirements and costs may impact which security services will integrate with Intune.
Here’s an overview of its features:
- Cloud-based UEM to control features and settings
- Isolation of corporate data for certain apps such as MS Office
- The Intune admin center offers status updates and alerts as well as device configuration and other administrative settings
- Connectors for Active Directory (for autopilot enrollment) and certificate-based authentication for endpoints
- ADMX templates to deploy Windows policies and benchmark group policies and Graph API for scripting, when the appropriate licensing is in place
- Integration with Entra, Windows (Win32) LoB apps, and other Microsoft-centric services; however, these are different products with different interfaces and pop-ups in the UX
- Application deployments and user assignments
- Compliance settings creation and the ability to lock down services with granular conditional access rules based upon group memberships, location, device state, and triggers for specific application access rules (Note: Additional Microsoft products and Premium licenses are necessary to govern identities based upon risk as well as to monitor and control cloud application sessions)
- Reporting on apps, device compliance, operations, security, and users
- Device-only subscriptions for single-use devices such as kiosks
- Remote support is available as a premium add-on to Intune, even with an M365 E5 license
What’s possible to do is dependent on what other Microsoft services are being licensed (standalone or bundled), knowledge of Microsoft’s administrative tools, and how invested an organization can become in the Microsoft ecosystem. Intune has morphed into a product family that’s best suited for enterprise-level compliance with enterprise-sized budgets and resources.
What Are Configuration Manager and Endpoint Security?
Many admins are familiar with Microsoft Configuration Manager (ConfigMgr), an enterprise system management product for Windows systems. It’s the evolution of what was once known as Microsoft System Center Configuration Manager (SCCM). ConfigMgr is included in Intune and integrates with other Microsoft cloud products as well as on-premises components when it’s set up for co-management. The experience can be very confusing, because Microsoft has folded its overall suite of UEM capabilities into an interface called Endpoint Security, but aspects of managing endpoints are handled outside of it under “devices” from the main interface.

What Is JumpCloud?
JumpCloud is an open directory platform for small to medium-size enterprises (SMEs) that includes IAM, UEM, and more. Supported platforms include Android, Linux, macOS, iOS/iPad OS, and Windows. JumpCloud is cloud-based and can be deployed for a domainless enterprise, without the need for AD or Entra, or to extend your existing AD domains. JumpCloud is tailored specifically to the needs of SMEs.
IAM
- Unlimited, True SSO that delivers SAML, OIDC, and password-based authentication for any web application, as well as SCIM and RESTful support to manage user onboarding/authorization to third-party applications
- JumpCloud provides ready-to-consume connectors for many popular services
- A decentralized password manager for when SSO is not possible
- Cloud LDAP and RADIUS
- Push and TOTP MFA everywhere, including RADIUS and LDAP connections
- Phishing-resistant modern authentication (coming soon)
- Built-in MDM, without extra costs
- A cloud-based LDAP directory
- The ability to sync with Active Directory or import users from it
- Integrations with popular HRIS systems for rapid user onboarding and provisioning
- Pre-built conditional access capabilities that restrict access by location, whether a device is being managed by JumpCloud, and to enforce MFA for specific groups of users (optional)
- Federation with other identity providers (coming soon)
- API-based provisioning
UEM
- Application install and management on remote systems
- Integrated remote assistance with Remote Assist, free of charge
- Zero-touch enrollment and deployment for Apple devices
- Automated dynamic group memberships that leverage attribute-based access control (ABAC) to modernize the user identity lifecycle and enhance security, providing entitlement management maturity beyond what’s possible with legacy access control paradigms
- Cross-OS policies and root-level CLI interfaces for centralized IT management and commands
- A streamlined dashboard for IT teams and technicians
- Reporting for Device Insights, Directory Insights, and Cloud Insights for AWS
- JumpCloud Patch Management for operating systems and web browsers (optional)
Comparing JumpCloud to Entra ID with Intune
Intune overlaps with JumpCloud on a feature-by-feature basis, and it makes sense for organizations to evaluate all of their cloud-based identity and system management options. The comparison between JumpCloud and Entra ID (Azure AD) with Intune is really about having adaptability and independent security controls versus monoculture and vendor lock-in risks.
The greatest difference lies in Microsoft engineering its products for the enterprise in service of the Windows ecosystem, tooling, and its accompanying cloud services. It’s a horizontally integrated stack. There’s deep integrations with Microsoft products and specialized services that mostly benefit larger organizations. If you have an all-Windows® network, and are already implementing Azure with Active Directory® on-premises, then Entra ID (Azure AD) and Intune could be the right addition for your organization. Using tools created by Microsoft in a Windows environment would make sense. Mobile-heavy organizations may also benefit from using Intune’s mobile device management capabilities to manage other operating systems.
JumpCloud addresses needs specific to the SME market, as evidenced by how its features are packaged and implemented for ease of use. One admin can manage a deployment. It was created to address the constraints that arise when a legacy on-prem directory is modified for a new era in computing (that crosses domains). The open directory platform solves the challenges faced by modern IT professionals versus extending an existing ecosystem into the cloud.
It also securely connects users to more resources without the need for additional servers or add-ons. If your organization has AWS, macOS®, Linux®, Okta®, Google Workspace™, and other non-Windows platforms as core parts of the infrastructure, then you would benefit by choosing JumpCloud’s open directory platform. SMEs can choose the vendors that are best suited for users both now and in the future as opposed to restricting flexibility and choice.
Ease of Use
JumpCloud is easiest to implement and manage with a more intuitive administrative UI, and pricing that’s based on use cases versus features. A common complaint is that Microsoft’s interface changes frequently and causes confusion as more products are added into the mix. That’s a consequence of bundling and frequent product family/branding changes. This Reddit thread captures numerous user-reported usability problems. Here’s a summary of them:
- Unpredictable time spent importing provisioning of devices, assigning profiles, and deploying apps—Microsoft’s default polling interval for policy refreshes is 8 hours
- Simple mistakes can cause actions to fail, such as a Registry key requirement rule filtering out devices
- Problems with assigning available licenses to new users
- Configuration changes taking a long time to go into effect
- Debugging events and sync logs requiring additional third-party tooling
- Loss of internet connectivity causing Windows Autopilot to fail
Testing any feature takes days to weeks because I go “hmm what does this do? changes setting 3 hours later huh, still no change…
Reddit User
Centralized Policy Management
A key component of Active Directory is a feature known as Group Policy Objects (GPOs). GPOs allow IT admins to control the behavior of Windows systems in their environment with great precision. Microsoft’s GPOs only work for Windows systems and are not applicable in the cloud via Entra ID (Azure AD). Microsoft has extended its tooling to Intune, but it’s not a 1:1 replacement. It also handles compliance for non-Windows devices through Intune.
JumpCloud offers GPO-like policies for all three major platforms—Windows, Linux, and macOS®—by using agents that also provide system management and telemetry. IT admins are able to remotely disable virtual assistants, enforce full disk encryption (FDE), and configure system updates with just a few clicks in addition to options such as integrated remote assist.
Enterprise Mobility Management (EMM) for Android and MDM for Apple products and Windows offer tamper-proof endpoint management by leveraging the latest platform technologies. For Windows, it’s possible to toggle between agents and MDM deployment models.
When a prescribed policy isn’t sufficient, JumpCloud enables IT admins to create and execute their own commands and scripts on all three desktop platforms. JumpCloud also provides optional policies for cross-OS patching for systems and browsers for compliance and security.
Open Directory Platform
The JumpCloud platform does not need to fully own an identity to manage it. Rather, it can consume identities from different sources and sits in the middle to orchestrate access and authorization to resources. This simplifies IT management for SMEs by addressing the access control and security challenges stemming from having identities exist in silos. An Entra ID (Azure AD) user also won’t be able to use RADIUS to access Wi-Fi without Network Policy Server (NPS) or third-party cloud service. SMEs can dramatically improve security as well as save on licensing, headcount, time, and effort by consolidating orchestration into a single directory and keeping identity independent from Microsoft’s security monoculture.
Mobile Device Management Capabilities
Intune and JumpCloud have MDM services for managing BYOD and BYOC devices.
Microsoft delivers cross-platform support, but Windows is the favored tenant with the capacity for zero-touch onboarding that would benefit Microsoft shops. Microsoft is also well-suited to support enterprise-level compliance use cases. JumpCloud is easier to adopt and learn. The open directory platform also adds additional value for EMM/MDM users to import user identities from non-Microsoft platforms to centrally manage or utilize them all.
Android, Apple, and Linux Devices
Intune has Mac and iOS/iPadOS support for the supervision of Apple devices through user login, device enrollment/deployment, configuration management, patch policies, and software distribution. It also offers services to manage Android devices and Linux. Microsoft’s full offering requires Entra, Intune, and an understanding of its Windows templates and tooling. It also has extended requirements for other Microsoft products such as Edge to be able to manage Linux users, limiting customer choice.
JumpCloud’s Apple and Linux UEM capabilities are extensive, beginning with a pre-built collection of policies, configuration options, security functions, and culminating in zero-touch device enrollment. Android EMM is expanding with each new release of the platform. UEM is immediately available as a core feature of the platform versus being a separate product. JumpCloud supports the most popular Linux distros and doesn’t impose any browser mandates.
Affordability and Implementation
With consideration to Microsoft’s extensive stack requirements and gated licensing, JumpCloud’s integrated UEM is more affordable and user-friendly. It’s also easier for IT teams and MSP technicians to learn and manage. Note: A junior level technician could do a lot of harm in Entra/Intune due to the level of understanding that’s required to use those products.
The first thing an Intune admin will notice is that it’s confusing, even if you already have a domain in Entra. For starters, it’s not an integrated product experience: there’s a setting in Entra to bridge it with Intune and scope memberships. It’s not automatic, and you may not even realize it until Intune doesn’t do what it’s supposed to (and you’re left wondering why).
Recall the different device management interfaces mentioned above. Here’s where it gets tricky:
- Device configuration profiles: These are configured separately and easily get lost or click the wrong thing, ending up somewhere you didn’t intend to be. Intune device management uses AD’s ADMX templates, which are separate from endpoint management, where system baselines reside. This is the Microsoft way of doing things.
- Configuration manager: You must use configuration manager for on-premises Windows server, apps, and devices. It enables co-management with Intune.
Device Enrollments
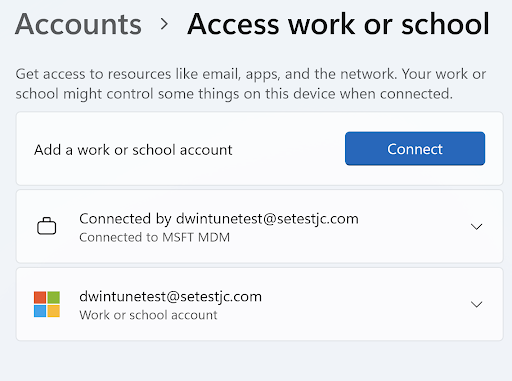
Many admins have encountered issues/difficulty enrolling Windows endpoints that are already registered in Entra and already deployed versus being provisioned with Intune/Entra from the start. This affects Entra users who may be upgrading licenses/packages or haven’t deployed it.
Here’s a scenario that an admin may encounter:
- The admin wants to use Intune and configures MDM/MAM in Entra to include all users or uses scoping for a group.
- The admin enables Intune and creates a group. The user (or device to cover all users on it) is added to the group. The group is assigned to a benchmark in endpoint security.
- The user signs into Entra under accounts | Work.
- Nothing happens, because MDM isn’t enabled at the device level.
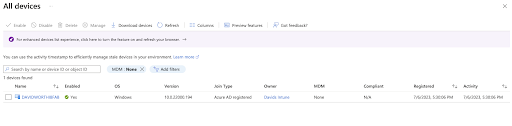
You’ll then need to troubleshoot using local registry/GPO, PowerShell, or Registry. You need local admin rights. Then, it creates a task in Task Scheduler to enroll MDM. There are entire
web pages external to Microsoft that are dedicated to resolving this challenge. You may also configure a “company portal” in Intune or log into MDM from Windows settings, even if the user is signed into their Entra account. They end up signing into Microsoft twice with two different account logins listed for the same account/identity. More options can create more complexity.
Dynamic Groups
JumpCloud utilizes dynamic groups by default with the capability to sort devices into the appropriate groups using rules. Attributes make it possible to provide workflows and automations to simplify identity lifecycle management. No premium licensing is required.
- Dynamically manage user group membership based upon user attribute-driven rules—can be either fully automated or require review
- Dynamically manage device group membership based upon device attribute-driven rules—can be either fully automated or require review
- Dynamically manage device and user group membership based upon both user and device attribute-driven rules
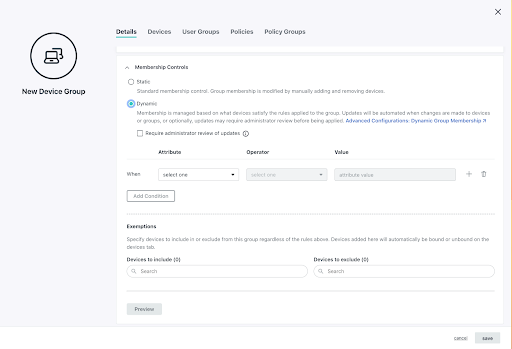
In contrast, Entra only permits dynamic groups in Premium 1 tier or above. It’s opt in and for users only, and admins must create expressions to make them work. JumpCloud enables dynamic groups to help categorize users and devices by default at no extra cost.
The admin experience is very different. You must specify device types in Intune by creating a device category and adding scoping tags (optional), and then you must create a security group back in AAD with the “deviceCategory” attribute. Admins will have to bounce back and forth between Entra and Intune in order to do this.
Patching
JumpCloud optionally includes cross-OS patching and supports the patching of leading browsers in a unified interface. Admins may fully manage Chrome by enrolling in Chrome Browser Cloud Management. EMM and MDM policies will configure mobile device update settings.

Intune has disparate offerings for OS and browser patching, and some have unique technical quirks. Windows AutoPatch is an Intune feature that’s only available for Windows. It uses Windows Update for Business and requires Windows Enterprise E3 licensing. There are several other service components involved with making all of that happen. Separately, you may also designate an update band for Windows under the Endpoint Security interface blade.
Azure Update Center (in preview) is another option, and its status as either an add-on for Intune or included feature is unknown. It’s intended to become a “unified service to help manage and govern updates for all your machines. Monitor Windows and Linux update compliance across your deployments in Azure, on-premises, and on other cloud platforms from a single dashboard. Make updates in real time or schedule them within a defined maintenance window.”
Browser updates are impacted by the Microsoft model. For instance, some ADMX files have dependency prerequisites. To import Mozilla Firefox ADMX and ADML files, you:
- Import the mozilla.admx and mozilla.adml files
- Import the firefox.admx and firefox.adml files
- Then you configure it with configuration profiles in Endpoint Security
Software Management
JumpCloud features software management for Android, Apple, and Windows (using Chocolatey). A private repository will be available soon. Admins will soon be able to upload, deploy, and update private Windows and macOS apps using a private repository.
- Files are scanned for integrity on upload and controlled versioning
- File size limits are removed for custom macOS apps
- Extended fee-based storage is available if it’s needed
Intune’s Mobile Application Management (MAM) configures, monitors, pushes, secures, and updates mobile apps. “Intune Protected Apps” such as MS Office secure corporate data. The Windows interface under “apps” has different features to assign apps to groups of devices. Many of its features are intended for enterprise deployments, as opposed to SME use cases. It also has the capacity to inventory and “discover” apps on registered Windows endpoints.
Customers have said that Intune software deployment and polling works on Microsoft’s schedule, creating management “unknowns.” The workflow is as follows: upload an MSI, create a package, apply it to a machine … and it will install at some point. This procedure, coupled with a confusing interface, creates a learning curve.
Platform
Microsoft has devised an extensive cloud services productive portfolio in service of its enterprise customers. It’s a stepwise architecture that enlists adjunct services to build out a broad stack. The Microsoft ecosystem is as comprehensive as a Microsoft shop needs it to be. Reskilling your existing team and/or obtaining external resources is necessary. You should also consider the cost of raising salaries to match market levels for cloud roles as more and more M365 features are implemented, even within Intune. All of this could change organizational structures and procedures in order to fully implement all of the products that Microsoft packages together.
JumpCloud is specifically designed for what SMEs need, and sheds the complexity of Microsoft’s ecosystem. It offers far more functionality through one solution for identity and devices (even network), rather than purchasing the entire Microsoft IT stack and everything else required for modern offices to manage users. SMEs that adopt JumpCloud for UEM are more likely to benefit from this integrated approach as well as its streamlined administration.
Microsoft 365 and Google Workspace Sync
With Microsoft 365™/Google Workspace sync, organizations can access either productivity platform at will with JumpCloud credentials. The open directory platform imports attributes that decorate users with entitlements, streamlining admin workflows, increasing the accuracy of user profiles, and delivering smooth onboarding. IT admins can also manage groups in Workspace. Google has partnered with JumpCloud for IAM/UEM and recommends it for SMEs.
You can add Google as an identity provider within Entra ID’s B2B collaboration. Specifically, federation with SAML/WS-Fed identity providers for guest users. You may require knowledge of how access packets are used to provide entitlements to members of external organizations in addition to the appropriate identity governance licenses.
Non-System Needs
When evaluating which identity management provider is right for you, you also want to consider your non-system needs. For instance, if you are interested in LDAP, RADIUS, Samba, SSH, and other protocol support, you might consider JumpCloud’s protocol-level hosted services. JumpCloud also implemented MFA for its LDAP and RADIUS services, which is significant when highly regulated industries like cyber insurance companies require MFA to be enabled for network devices. Otherwise, additional servers and services may be needed to be compliant.
Vendor Lock-In
Vendor lock-in is an important consideration for MSPs and IT organizations alike. Microsoft is financially motivated to keep you on the Windows and Azure platform track, which includes its ecosystem of administrative tools and templates. Often, you need a number of additional Microsoft tools on the Entra ID (Azure AD) and Intune path. Most organizations with Entra also use AD on-prem, Azure AD Connect, Azure Active Directory Domain Services (Azure AD DS), or even third-party tools to create a holistic IAM and device management approach. That’s a deep investment in budget and training that builds a deep dependency on Microsoft.
Intune belongs to an evolving family of IAM products that have undergone multiple re-namings and repackaging. Growing with Intune means licensing Intune as well as other complementary services for security and system analytics. Note that the selections are in flux, making direct comparisons with alternatives more challenging. Buying Intune sinks organizations deeper into the Microsoft stack, which limits their ability to purchase solutions outside the Microsoft domain and customize their stack for their needs. It also introduces some unpredictability in budgeting.
JumpCloud’s open directory platform allows for greater flexibility and shopping around for services, such as adding best-of-breed XDR integration from CrowdStrike or Sentinel One to secure identities and endpoints, versus a monolithic supply chain from Microsoft.
Total Cost of Ownership
Microsoft’s legacy requirements frequently mandate a hybrid infrastructure configuration. A hybrid infrastructure adds complexity, and complexity correlates to bigger budgets. Managing and licensing your physical servers is expensive (people, hardware, facilities, maintenance, and utilities), and the increase to your potential cyberattack surface area are all factors to consider. These factors combined raise the total cost of ownership for Entra.
A common refrain is that “Microsoft stuff works well together.” In practice, transitioning on-premises Microsoft solutions to the cloud isn’t always straightforward. For example, AD groups don’t all automatically sync over to Entra. One Intune administrator recently recounted how his organization, which is invested in Microsoft, was experiencing difficulty transitioning to Entra and Intune from AD FS and Active Directory.
In this example, consultants were brought in to set up Intune. The consultants attempted to turn on “full blown Entra” for the environment. That decision resulted in downstream problems with Virtual Desktop Infrastructure (VDI), because only persistent virtual machines (where every user’s personal desktop settings are set for each virtual desktop) are supported in on-premises ADFS.
This scenario may seem arcane, but it illustrates that even migrating to Microsoft’s latest and greatest services isn’t always straightforward. Microsoft has a multitude of legacy components for SSO that tie back to AD, which introduces difficulties that are unique to its ecosystem.
The Intune administrator summed it up as: “I need to focus all my time [elsewhere] but can’t because I get pulled in every direction [due to the complexity of Microsoft’s ecosystem].” Simply put, if your infrastructure’s a mess, everything’s a mess … and costs more than is necessary. The more an organization sinks into Microsoft, the less flexibility it has to go elsewhere.
Service Licensing
Cost of ownership is a key differentiator between Entra + Intune and JumpCloud. Entra is initially a great value — if you’re a heavy user of the Microsoft stack — but costs mount as use increases and third-party services and non-Windows devices are added to your infrastructure. Navigating Microsoft’s complex gated licensing scheme is another driver of rising subscription costs.
For example, organizations that are considering M365, which can bundle Intune, must assess the differences of all of its license variations. Some consultants even specialize in demystifying Microsoft’s licensing options. Basic tiers are only the price of admission. There are additional costs involved simply to obtain a few fundamental capabilities, such as federated identity, in Entra to securely access resources outside of Microsoft’s stack using SSO. That’s the real-world starting point for modern IT versus the sticker price, before Intune or other subscriptions factor in.
In contrast, JumpCloud’s foundation supports expanding capacity to accept and incorporate other identities into workflows through directory synchronizations or federation.
IT Infrastructure Consolidation
IT tool sprawl is just one of the many unintended consequences of today’s remote-first workforce. Adopting a consolidated stack is beneficial to avoid overlapping feature sets from many different software products. A Microsoft shop may not need to look elsewhere to meet compliance, IAM, IT management, and highly advanced security requirements with its stack (assuming they have the budget). However, there are downsides.
Smaller organizations may find themselves overextended by the breadth and complexity of Microsoft’s components and services that form its hybrid architecture. Buying, operating, and supporting a datacenter is just the start. It’s very likely that IT teams will have to employ external resources to assist with Entra + Intune implementations. Those decisions involve a substantial and costly long-term commitment.
Azure works best if organizations are fully incorporated into a Microsoft tech stack environment, but not outside of Microsoft’s cloud infrastructure (i.e., it can’t be used to manage non-Windows servers hosted in Amazon or Google clouds).
JumpCloud’s open directory platform enables IT teams to assemble a stack of best-of-breed solutions that are secure, on managed devices, and available through the identity provider of their choosing. Optional products assist with security, IT hygiene, and password management without extensive management overhead or mandates to deploy them successfully.
What’s Best for Your Shop?
If you are locked into Microsoft solutions, are a heavy Windows user, have strict compliance mandates, or if you have corporate-owned mobile devices, then Azure solutions may be the most acceptable fit. However, its platforms are intended for the enterprise and extend broadly through products connected via gated licensing. Alternatively, if you are an SME that’s invested in other non-Windows platforms and non-Microsoft services and identities, and wish to (or see a path to) consolidate IT resources, then you should consider JumpCloud’s open directory platform. A third option is to use both to obtain the greatest value for your organization.
JumpCloud centralizes user and system management, regardless of platform or where identities reside. This includes our Multi-Tenant Portal (MTP), designed specifically for MSPs to manage multiple client organizations from one pane of glass. JumpCloud offers cross-platform GPO-like capabilities to manage fleets of systems with policies, including local admin system controls, full disk encryption with FileVault 2 and Bitlocker, screen lock regulations, and more. MSPs also won’t have to turn away business from organizations that opt to use Google Workspace.
JumpCloud offers more immediate actions for commands and policies than Intune.
For MSPs, consolidation gives you the chance to proactively manage and monitor your clients’ tech with fewer providers. It decreases your monthly expenditures without sacrificing efficiency or usability, and frees you up to spend more time helping your clients reach their goals. IT consolidation has many benefits for MSPs and their clients, including cost savings, a streamlined user (and management) experience, and an increase in client trust.
The Choice Is Yours
However you choose, all options present benefits to an organization. To learn more about JumpCloud versus Entra ID (Azure AD) with Intune, contact us or join our community to engage your peers in conversation. And, as always, signing up for a platform demo is completely free.
Sometimes self-service doesn’t get you everything you need. If that’s how you’re feeling, schedule a demo to discuss options for implementation assistance, migration services, custom scripting, and more.





