Updated on November 5, 2024
Active Directory (AD) is a directory service/identity provider (IdP) that administrators use to connect users to resources on Windows-based networks. It’s built into Windows Server and works through Active Directory Domain Services (AD DS) to secure PCs, file shares, and applications. AD DS stores information about network objects (e.g., users, groups, systems, etc.) and their relationship to one another. Your organization may still be using AD because it can provide user-based policies for access control and you feel that it’s necessary.
Attributes are what determine user permissions and make it possible for admins to query AD and produce compliance reports. Understanding how AD stores this user information makes it easier to manage multiple domains, configure single sign-on (SSO) when it’s necessary to access external resources or create information barriers between departments.
SSO breaks down identity silos and makes it possible to centralize your policies and controls with groups. However, that’s not possible if users aren’t decorated with the right attributes, or attributes aren’t mapped to a cloud directory that modernizes AD. This article focuses on users and how AD stores information that can be used for group management and flow into identity and access management (IAM) systems to make access decisions in your network and beyond. The goal is to increase IT efficiency and establish stronger security for users and devices.
Object Classes Defined
First, let’s cover some core terminology:
User objects: User objects represent individuals within your organization who are a part of the domain. The user object resides within the higher level user class, and attributes determine what information each class can hold. This concept is called a Directory Information Tree (DIT). These concepts are outlined in more detail below.
Directory Service Tree: The DIT consists of the Distinguished Names (DNs) of directory service entries, a unique identifier that’s familiar to AD administrators and PowerShell users. For example, a DN makes it possible to execute a command on an object such as a user account. Microsoft uses “tree” as terminology for when multiple domains are grouped together; multiple trees form a forest, which can encapsulate multiple locations and IT teams. Organizational units (OUs) organize groups, users, and devices at all levels of the AD forest.
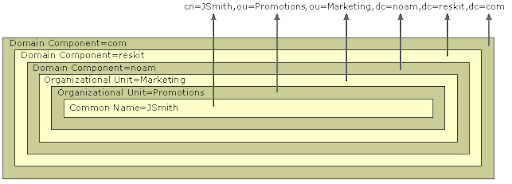
Object attributes: Object attributes define basic properties/information about them, such as first or last name. Attributes are essential to how the directory functions. Think of them as key-value pairs in a database that have predefined names so that Lightweight Directory Access Protocol (LDAP) can function as an open protocol in an IdP. A collection of attributes is an entry, such as an individual user in AD.
Entries are differentiated from one another using their DN. Attributes can belong to multiple classes in AD, because the classScheme and attributeSchema are defined separately. Windows admins who have the schema master role can use the Schema Management Microsoft Management Console (MMC) snap-in to introduce custom attributes by registering schemas.
ObjectClasses: ObjectClasses are essentially a collection of attributes (a container). The LDAP standard uses directory schemas to define ObjectClasses and class hierarchy to store and retrieve data. Attributes that are associated with ObjectClasses are used to describe something, such as a person, so a person would fall within the user class type. ObjectClasses can also be an attribute that’s used in directory search operations and reporting. ObjectClasses are outlined by the LDAP standard, which AD was built on, and fall into three categories:
- Abstract class: Recall the concept of object-oriented programming where abstractions make code reusable and extendable. It indicates the top of the inheritance chain in LDAP. The “top object” class, which serves as root classes for most other object classes, is a well-known example. Abstract classes are sub-classed entries that inherit attribute types, which make them useful as templates for creating new classes in AD. They create a common definition of a base class that multiple subclasses can share. The function is nearly identical to structural classes in AD, but objects that are instances of abstract classes aren’t instantiated within AD DS.
- Structural class: These classes outline where entries may occur in the DIT and what attributes are allowed. These are the only classes that have instances in AD DS.
- Auxiliary class: Auxiliary classes are included in the schema definition of all classes and list the attributes for an entry/class. They don’t define a core entry but establish the requisite characteristics. For instance, AD uses “Must-Contain” or “May-Contain” to mandate (or make optional) attributes when a class is created by governing its values. Active Directory’s technical specification supports statically linking auxiliary classes to the ClassSchema other object classes in order of inheritance from the top class. “securityPrincipal” is an example of an auxiliary class in Active Directory that Windows uses then to permit or deny entities (groups or users) rights to the operating system.
Note that AD has syntaxes, called DataType, that determine what type of data can be stored within an attribute. It can be a confusing topic because there may be more than one name for the same attribute in AD.
Common Active Directory Object Attributes
Active Directory stores attributes for applications, computers, printers, shared folders, and users. Think back to the AD user object. An organization would store attributes such as:
- First name
- Last name
- Telephone
- Title
- Department
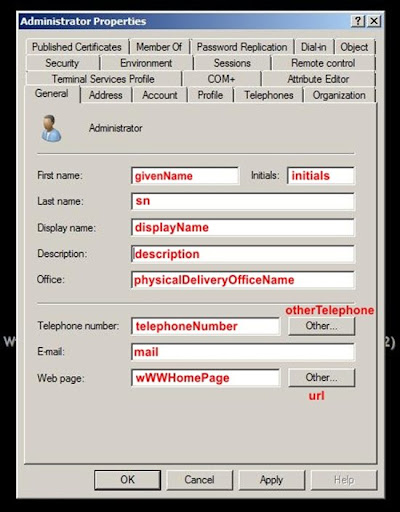
AD object attributes make it possible to drill down into events to learn which user on which computer (by computer name) may have accessed a particular resource. This is possible because LDAP requires that every attribute has an LDAP name that can be used in queries.
IT Efficiency and Zero Trust Security
AD DS relies on an access control entry (ACE) to grant or deny an object (such as a user or group) access to a resource. Entries are collectively known as an access control list (ACL). An ACL contains many different ACEs, which presents the risk of many outdated group memberships or the wrong denial rule grinding operations to a halt.
Nested groups streamline granting permissions, but also have downsides and risks. AD’s access control is a manual process that’s prone to human error. Moreover, there’s no context in the authentication decision that takes risk(s) into account. The good news is that attributes from AD can be leveraged to automate access resources in IAM systems.
For example, JumpCloud’s Active Directory Integration (ADI) syncs with AD and places users into groups based on their attributes. This is made possible via attribute-based access control (ABAC), which works a bit differently than AD admins may be used to. For instance, a user that changes departments may no longer require access to an accounting system.
AD DS would grant any user that belongs to a group access, despite organizational attributes having changed. AD creates higher administrative overhead and it doesn’t offer Zero Trust security. Meaning, AD has no insight into system state or user and session risks and nothing challenges the authentication decision. That places information and identities at risk.
Note: Some AD admins like having user-based policies on shared devices. It helps to think of that approach as building a wall in the front yard but leaving the backyard open. It makes more sense to apply a strong posture across all users on all devices.
How to Find Active Directory Attributes
Admins can query AD from the Active Directory Users and Computer (ADUC) console, an add-on to MMC in Windows Server. It’s the go-to tool for managing objects and their attributes. There’s a hidden tab in ADUC called Active Directory Attribute Editor that lists all attributes and their corresponding values, including hidden attributes. Some attributes are marked confidential and values can be hidden from admins.
PowerShell
The Active Directory PowerShell module is part of the Remote Server Administration Tools (RSAT) for Windows and can be used as an alternative method by command line gurus. The Get-ADUser command is used in combination with filtering to return user properties.
For example:
Get-ADUser -Identity WorthingtonDavid -Properties *
Surname : David
Name : Worthington David
UserPrincipalName :
GivenName : David
Enabled : False
SamAccountName : WorthingtonDavid
ObjectClass : user
SID : S-2-6-31-47795136661-7810167215-4424248291-7722
ObjectGUID : 4bec018b-dbbc-4adc-8872-a6b182ac1e5d
DistinguishedName : CN=Worthington David,OU=NorthAmerica,OU=Marketing,OU=UserAccounts,DC=JUMPCLOUD,DC=COM
It’s also possible to use services that integrate with AD to review attributes and more, including managing access control to your web applications. Integrations with directory services such as JumpCloud and Entra ID can extend authentication to SaaS applications for SSO with the ability to permit AD to make access decisions when it makes sense to.
JumpCloud also provides access to network devices, similar to the Network Policy Server (NPS) role for Windows, but without additional overhead. It can also contain AD’s footprint for lower costs and higher efficiency: containing head count, server room expenses, and hardware costs.
AD Attributes and JumpCloud
Your AD user attributes can become a useful element of your IAM strategy. JumpCloud’s groups utilize ABAC and can automate membership changes or make suggestions that admins can act on. JumpCloud also imports the preexisting group structures and memberships from AD. Additional user attributes may be imported from an HRIS system to align HR and IT operations.
JumpCloud’s ABAC establishes more mature entitlement management than AD with less administrative overhead. Group memberships can be combined with environment-wide multi-factor authentication (MFA) and conditional access for privileged users. The directory supports OIDC, RADIUS, LDAP, and SAML authentication methods with MFA everywhere.
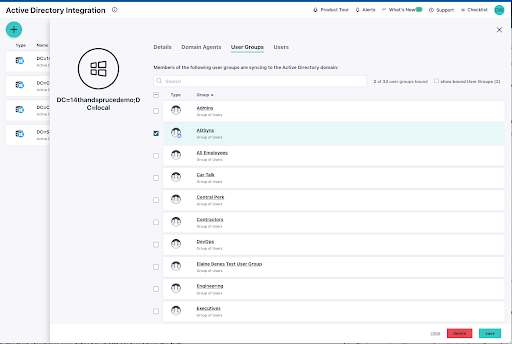
AD attributes can be managed through JumpCloud when Windows domains are integrated with JumpCloud’s open directory. JumpCloud’s PowerShell Module will query all user attributes in addition to taking bulk actions to add, modify, or implement custom attributes to AD.
For example:
Set-JCUser -username bobby.boy -NumberOfCustomAttributes 2 -Attribute1_name Department -Attribute1_value Dev -Attribute2_name Location -Attribute2_value Boulder
AD is otherwise maintained as the “system of record” for your attributes.
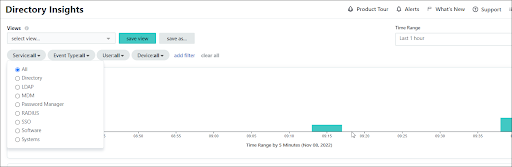
There are even more ways to capture your AD attributes within JumpCloud. The Directory Insights reporting tool captures telemetry, including user attributes. The Directory Insights API may also be used to review activity within your directory using other reporting tools.
One of the many benefits of AD integration is that JumpCloud’s Active Directory Integration (ADI) application will automatically import basic attributes from AD, including:
- First name
- Last name
- Password
- Password expiration
- Username (logon name in AD)
- User state
- Department
- Employee type
- Job title
- Company
- Manager
Changes made within AD will reflect in the JumpCloud tenant within 90 seconds.
Note: Organizations that are also using Azure Active Directory (AAD) can perform bilateral attribute mapping with JumpCloud.
Try JumpCloud
JumpCloud provides a smooth path to migrate off or modernize AD. ADI has configuration options that will enable you to determine where and how you want to manage users, groups, and passwords. It also provides a migration tool to transfer identities.
Cross-OS device management is a critical component to control and protect modern IT infrastructures. JumpCloud pairs the ability to manage every endpoint with an open directory platform to secure every identity and resource. This unified approach delivers strong access control while consolidating your tools for increased IT operational efficiency.
JumpCloud also provides SSO, cloud RADIUS to manage access to network devices and Wi-Fi, and additional IT management features including a free Remote Assist tool, patch management for devices and browsers, and a password manager to keep your identities and resources safe.
Try JumpCloud for free and find out if it’s the right option for your organization’s journey away from AD.
Our customers tell us that asset management is also important for security and IT operations. JumpCloud is enhancing its platform to unify SaaS, security, and IT asset management.
Learn more about how admins will be able to consolidate security, asset, device, access, and identity management with JumpCloud and how those features go hand in hand.
Active Directory Attribute FAQs
Active Directory attributes are properties that define characteristics of objects stored in the Active Directory database, such as users, computers, groups, and organizational units (OUs).
Active Directory attributes can be categorized into two types: built-in attributes, which are predefined by the system, and extension attributes, which can be customized to meet specific organizational needs.
Common built-in attributes in Active Directory include username (sAMAccountName), full name (displayName), email (mail), phone number (telephoneNumber), and group membership (memberOf).
Yes, you can extend the Active Directory schema to create custom attributes tailored to your organization’s requirements. However, schema modifications using the Active Directory Schema MMC Snap-In should be done with caution and proper planning. Creating objects is a permanent operation, and while objects may be disabled, they cannot be deleted.
Attributes including username and password are crucial for user authentication in Active Directory. Domain Controller checks these attributes for validity when a user attempts to log in.
The distinguishedName (DN) attribute uniquely identifies each object in Active Directory and represents its hierarchical path within the domain.
Active Directory attributes can be managed using various tools, such as Active Directory Users and Computers (ADUC), PowerShell cmdlets, and third-party management consoles.
Yes, computers in Active Directory have unique attributes, including hostname (name), operating system (operatingSystem), and service pack version (operatingSystemServicePack).
LDAP (Lightweight Directory Access Protocol) queries allow you to search and retrieve specific attributes from Active Directory, providing valuable information for various administrative tasks. However, LDAP auditing must be enabled on your endpoints in order to do this.
Yes, you can use Active Directory’s delegation features to grant non-administrative users permission to modify specific attributes while restricting access to other parts of the directory. This requires using the Delegate Control wizard in Active Directory Users and Computers.
Attribute constraints and validation can be enforced using custom scripts, PowerShell validation functions, or by setting attribute limits in the schema.
Attributes such as user group membership and computer attributes are essential for applying Group Policy settings to specific users and computers within the domain.
To control access to sensitive attributes, use attribute-level permissions and Active Directory security groups to restrict modifications to specific users or administrative roles.
The “Read-Only” attribute in Active Directory allows you to mark certain attributes as non-modifiable, ensuring that sensitive information remains immutable, even for administrators.
Active Directory does not provide attribute-level encryption, but you can encrypt sensitive data using encryption mechanisms within applications or third-party encryption solutions before storing them in Active Directory.
Regularly review access permissions, configure attribute-level security, and provide proper training to administrators to prevent the unintentional disclosure of sensitive information.
Implementing attribute-level filtering in LDAP queries restricts the attributes returned in query results, reducing the risk of exposing sensitive data to unauthorized users.
Active Directory does not natively support data masking, but you can implement data masking solutions at the application layer to protect sensitive attribute values.
During migration or integration, ensure proper attribute mapping and consider the security implications of attribute synchronization to maintain data integrity and security across systems.
Misconfigured attributes can lead to privilege escalation, data leakage, unauthorized access, and account compromise. Regular security assessments can help identify and mitigate these risks.






