Every Active Directory (AD) admin is familiar with nested groups. Rights are assigned to objects by virtue of their location in the tree; that’s just how things work. It’s convenient and makes entitlement management easier… until you consider its lack of maturity for identity governance. What once worked well now increases security risks and management overhead.
Cloud directories have the benefit of shedding that type of technical debt. However, it’s a change in how admins think about how entitlements are handled. The benefits that a flat structure brings to IT efficiency and security may not be obvious, even when attribute-based access control (ABAC) solves identity governance problems that have been festering over the past 20 years.
This brief examines why nested groups have become undesirable and discusses how cloud directories automate user/device lifecycles and enable more effective work through dynamic groups. You’ll also learn how cloud directories will increase your security.
What Are Nested Groups?
AD is a directory services database and uses Lightweight Directory Access Protocol (LDAP) for interacting with data. Its architecture enables admins to make one AD security group a member of another, thus “nesting” one group within another. Members of that group then inherit the permissions and rights assigned to the parent group. That concept is simply referred to as nested groups.
Security groups in AD assign users and resources permission to access shared IT assets, and user assignments are either granted manually or by using PowerShell to create elaborate if-else conditions. Nesting is convenient for user provisioning when there are well-specified roles/functions; however, it’s vulnerable to human error. It’s important that best practices are followed to avoid security breaches due to forgotten users or overprovisioning.
Add-ons such as Microsoft Identity Manager (MIM) were created out of necessity to manage the identity lifecycle, because nested groups lack automated user management or the ability to synchronize identities between systems. An entire ecosystem of add-ons exists for this purpose.
Admins that don’t take a proactive approach to lifecycle management through access governance, or purchasing add-ons to extend AD’s capabilities, will encounter problems.
MIM is being phased out and replaced by Entra ID’s premium SKUs for privileged access management. AD’s access control model is being modernized by cloud directory services.
What Problems Can Occur with Nested Groups?
The biggest issue with nested groups is that members of child groups inherit the entitlements of their parent group(s)… which sounds intentional, but unfortunately can result in unintended entitlements, entitlement conflicts, and troubleshooting challenges. This can be especially problematic when there’s a complex organizational structure.
Child groups aren’t members of the parent object, but they inherit entitlements from it. It can be difficult for IT admins to unravel user entitlement issues if those entitlements are buried deep within those parent/child entitlement relationships. Nested groups can also lead to individuals gaining improper access to files because of over permissioning.
Group Policy Objects (GPO) are applied to groups for security. However, past configurations can unintentionally expose the environment. Today’s cyberthreats aren’t the same as before; they are more sophisticated. Configurations are layered on to deal with emerging threats, which adds to the complexity.
GPOs can overwrite each other, and that makes audits/compliance more difficult than it has to be. There’s also no certainty that groups are secure.
This scenario, coupled with continued reliance on nested groups, increases the security risks inherent to using these legacy technologies. Cloud directories don’t have that technical debt.
Cloud Directories Deprecate Nested Groups
Cloud directory vendors, including JumpCloud and Microsoft, operate multi-tenant environments where organizational hierarchies had to be reimagined. Managing nested groups across different tenants would introduce complexities, performance problems, and issues with scalability. Implementing nested groups also fails to ensure interoperability and compatibility with other services. A more uniform approach is necessary in the cloud.
Note: Don’t be fooled: Microsoft’s Entra ID is previewing a feature that replicates nested groups, but it doesn’t revert back to the legacy way of doing things in AD. Users are still members of both the parent and child groups. Therefore, its entitlements are explicit and not inherited.
Modern Directories Offer a Simpler, More Secure Experience
Modern directory services utilize a flat architecture where memberships are based upon the attributes of the user object within each organization. Entitlements are then applied directly to groups rather than through an indirect inheritance from the parent group object. This makes it much easier for admins to determine why a user object has a particular entitlement.
In short, ABAC enables a more mature approach to entitlement lifecycle management through the creation of dynamic groups that can automate membership changes. There are numerous benefits including easier on/off boarding, increased efficiency and responsiveness, and stronger privileged access management (PAM).
Better Alignment Between HR and IT
Dynamic groups streamline lifecycle management and break down silos between IT and HR. For example, a cloud directory can be integrated with human resources (HRIS) systems so that changes made by HR are immediately reflected in access rights. Group memberships, which provide privileges to resources, change when a user moves to another department or leaves the organization.
Increased Admin Efficiency and Responsiveness
IT becomes more efficient and responsive to business requirements simply by having ABAC.
For example, a finance department can be granted access to AWS in order to do some audit work simply by adding a new attribute rule for that group. A “nested” or parent/child group structure could create compliance, licensing, and security issues that would limit IT’s ability to support finance. Adding finance to the “AWS” group would also grant access to applications that members don’t really need or shouldn’t have access to for compliance purposes.
Privileged Access Made Easy
Access control is also strengthened when dynamic groups are used with conditional access (CA) and technologies like phishing-resistant modern authentication to manage privileged access from users to resources.
Don’t Waste Your Licenses
SaaS management is another benefit. You’ll save on licenses for apps that are over provisioned to people who don’t need access. That will make better use of your budget, resources, and prevent SaaS sprawl without the slow, manual process of auditing licenses.
JumpCloud’s Dynamic Groups
JumpCloud uses dynamic groups to automatically organize users and devices using basic attributes. It also includes basic operators to create compound queries, which will increase admin efficiency even further and streamline device and identity lifecycle management. Admins can also create custom attributes and configure the directory to fit their business needs.
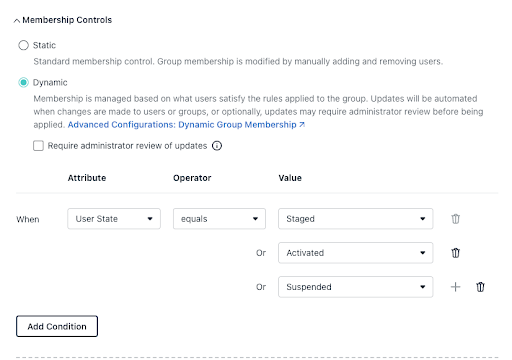
If needed, static groups with explicit assignments are always an option.
The open directory platform reestablishes the strong access control that Active Directory once provided in a domain-bound environment and extends it to all of your users and devices. It’s possible to create dynamic groups for users and devices with a few simple steps, which reduces administrative overhead and provides security that’s built around your assets.
Effective, Asset-Based Security
Group memberships in JumpCloud follow the ABAC model where entitlements are applied to individual groups. It offers a stronger approach to entitlement lifecycle management than nested groups by automating membership changes using attributes, which helps to enforce the principle of least privilege.
Dynamic groups have the added benefit of helping to protect confidential/private information with less effort. Admins can configure simple logic using operators to become even more efficient through approvals and automated workflows. JumpCloud makes it easier for admins to determine why a user has access to something for easier auditability and increased visibility.
It’s also easier to introduce PAM. JumpCloud Go™ works hand-in-hand with CA and dynamic groups to provide modern authentication while eliminating passwords and multi-factor authentication (MFA) fatigue. JumpCloud Go will soon be available for step-up authentication whenever an additional layer of verification is necessary. This feature supports heterogeneous environments including macOS, Linux, and Windows and will work with most browsers.
A Workflow-Friendly Platform
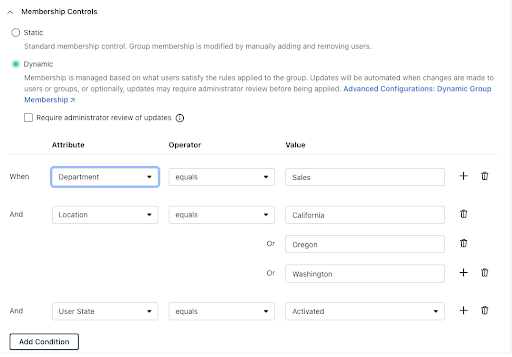
Membership conditions can be as simple as devices being automatically categorized into a group by operating system. However, compound queries, using operators, will introduce autonomous administration while strengthening device and identity lifecycle management by taking more actions against groups.
For example, you could automate deployments by associating group memberships with a manager. HRIS integration expedites onboarding new team members through automation, which is made possible by using these expressions.
Note: An admin could easily create one user group that “contains” everyone in sales instead of managing multiple user groups for each region.
The real-world impact is that onboarding is less time-consuming, permitting IT to move on with confidence that the user entitlements are correct. There’s continuous evaluation/attestation of user entitlements from that point onward, thanks to dynamic groups. Modern authentication and CA keep privileged resources more secure with less effort. Ultimately, IT team members will be freed up to focus on the deeper, more complex parts of their jobs to add more business value.
You won’t get any of that with nested groups.
JumpCloud’s PowerShell module makes it even easier to report on users and their associated groups and systems.
Try JumpCloud
Dynamic groups are a core part of the JumpCloud platform and don’t cost extra to use. Try JumpCloud for free and find out if it’s the right option for your organization. You can also try a guided simulation and see what it’s like to create dynamic user and device groups.




