Microsoft’s Active Directory (AD) has been entrenched in IT infrastructure since its debut in 1999. It established a client/server model that was intended for private networks. The world has changed significantly since then: our digital estates cross domains. People work differently and the types of apps and devices that they now use aren’t all Windows-based or behind a firewall. JumpCloud is an open directory platform that was designed for this new normal. It manages identities with unified endpoint management (UEM) to secure access to every resource, all from the cloud. Microsoft created Entra ID (formerly Azure AD) in response to shifting requirements, which includes a patchwork of services that can extend AD to manage your entire digital estate.
This article compares AD with JumpCloud by outlining the benefits of each platform and how they differ. Today’s challenge is to make identity the new perimeter, and assume breach with a Zero Trust security strategy, while remaining agile and productive. It’s not possible to accomplish that objective with standalone AD; cloud services are necessary to modernize AD to meet modern IT requirements. Microsoft offers Entra ID for that purpose, but its features are intended for enterprises and can create lock-in through its monoculture. Whereas, small and medium-sized enterprises (SMEs) may benefit more by using JumpCloud’s open directory platform with AD.
Directory Needs and Considerations
The classic AD scenario where an SME is running Windows PCs exclusively with native apps and resources is today’s exception, not the rule. That shop would quickly fail to achieve recommendations for cyber defenses and compliance without substantial risks. Microsoft shops that have been slow to enact proactive security measures to safeguard their data and identities (even for legitimate reasons) should assume that Entra will be their predetermined course.
Some organizations will do well with Microsoft’s prescribed stacks of cloud services being layered on top of AD. However, AD + Azure may not be the optimal fit for an SME’s technical requirements or budget. Consider that an SME’s general IT requirements should now include:
- Single sign-on (SSO) to all IT assets from managed devices
- Multi-factor authentication (MFA) and/or modern authentication
- The capacity to manage identities and access control on any device, anywhere
- Advanced identity lifecycle management
- A Zero Trust security strategy
- Meeting rising compliance requirements, including patching and device posture
- Managing supply chain risks and unifying IT systems
Google recommends JumpCloud for SMEs to manage IAM and devices.
SSO to Everything
AD: Microsoft provides several options for integrations, but AD cannot provide SSO directly. Protocols such as RADIUS authentication require installing and maintaining the NPS server role, FreeRADIUS, or purchasing a subscription to a stand-alone cloud service.
- Active Directory Federation Services (AD FS) provides self-managed SSO capabilities, but you’ll encounter a complex setup. It takes a server farm in order to function.
- SCIM provisioning is only available by purchasing an add-on SCIM product or Microsoft DirSync using LDAP. Otherwise, Entra and a hybrid configuration is required.
- Entra provides SSO, including SAML and OIDC; standalone AD will not.
- A free tier is available, but has limited functionality, specifically for group management, provisioning, device management, and security configurations.
- Premium tiers of Entra are necessary for Application Proxy for on-premises, header-based, and Integrated Windows Authentication. Kerberos, NTLM, LDAP, RDP, and SSH authentication are available from Entra’s free tier. Identity protection that extends to AD is available, but it’s a premium feature.
- AD isn’t capable of managing non-Windows devices without the Intune service, placing identities that reside on those devices and the resources that they access at risk.
- AD Connect creates a hybrid configuration between AD and Entra with several potential deployment models; a newer cloud-based agent is also available. It’s a premium-level feature beyond 500,000 directory objects such as PCs, groups, and users.
Useful features such as password write-back are premium only.
JumpCloud: JumpCloud features “SSO to everything” as part of its core functionality.
- SAML, OIDC, and RESTful API provisioning are included in the platform.
- SCIM provisioning is included to streamline lifecycle management.
- Cloud RADIUS and LDAP, with the option to federate credentials for authentication, are integrated and have MFA. This ensures that network devices don’t become identity silos.
- JumpCloud syncs with Entra/Microsoft 365, AD, Google Workspace, and Okta identities for SSO at no additional charge. It also syncs user information into Amazon’s IAM Identity Center, securing access to your AWS resources.
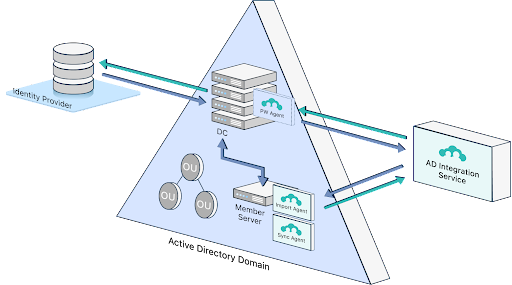
- Active Directory Integration (ADI) is free to help modernize AD.
- JumpCloud is making ADI much easier to scale with a new deployment model that uses a member server versus a domain controller to configure syncing. It’s possible to sync multiple domains to JumpCloud at once. JumpCloud is adding delegated authentication (similar to Entra’s passthrough authentication) to leverage existing credentials from AD without forcing password resets.
- Identities and assets are protected, because JumpCloud also manages the device.
Advanced Lifecycle Management
AD: Advanced Lifecycle Management is only possible through integrations with Entra and Lifecycle Workflows (in preview), third-party services, or extensive customizations.
- Workarounds, such as custom PowerShell scripts, are needed to enable or disable user accounts on a schedule.
- External identities may only be managed through a combination of Entra and Microsoft Entra, another paid Azure service.
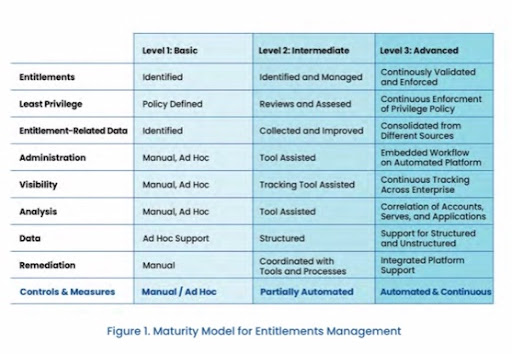
- Default user management is manual, creating the potential to over/under provision users through human error, or even failure to disable accounts. This is considered “basic” entitlements management due to the manual and ad hoc nature of user maintenance.
- Attribute imports from other directories is a manual process, requiring PowerShell and other tools. Entra has dynamic groups with scoping rules, but it’s not a default setting.
- AD doesn’t manage users on devices beyond Windows — without additional paid subscriptions to Microsoft’s Intune platform.
- Integrations are possible with third-party lifecycle management systems. That approach requires dedicating users that have administrative privileges to those solutions. AD is popular, so many premium third-party solutions exist for enterprise-grade management.
- Entra makes it possible for a zero-touch onboarding experience, but not AD.
- SSO to everything is only available through add-ons to AD and/or Entra.
- The Schema Management Microsoft Management Console (MMC) snap-in makes it possible to highly customize AD for niche requirements.
JumpCloud: JumpCloud integrates with human resources systems and other sources, automates group memberships, schedules user on/offboarding events, and provides SSO.
- User provisioning/deprovisioning can be scheduled from the GUI console.
- JumpCloud is an open directory platform that enables attributes to be imported from other “sources of truth,” including AD, Entra, Google, Okta, and more.
- JumpCloud manages external identities at no additional cost and is adding federation to ensure that you may use the identity provider of your choice.
- JumpCloud centrally manages identities on Apple devices, Android, many popular Linux distributions, as well as Windows through MDM and agents.
- MDM provisioning package enrollments provide a light touch deployment model where a preconfigured Windows onboarding workflow can be generated for new PCs. You will be able to skip the Windows out-of-the-box experience.
- Zero-touch onboarding is available for Apple devices.
- JumpCloud’s dynamic groups for users and devices continuously validate and identify entitlement issues (through attributes and rules) to deliver group membership automations and suggestions. That provides a more mature level of security controls and advanced entitlement management without extra effort.
- SSO is built into the platform, eliminating siloed point tools to manage identity/user lifecycles.
Compliance and Security
AD: Active Directory is well documented and understood. Qualified consultants and solutions are plentiful and can increase its security to comply with compliance regimes or regulations. However, achieving this level of security entails a significant commitment in budgets and people.
- AD doesn’t provide MFA everywhere, and “out-of-the-box” Entra or third-party solutions are necessary to extend MFA to common SSO protocols (and beyond).
- AD wasn’t designed with a Zero Trust security strategy in mind. Features such as conditional access rules are only found through Entra or third parties.
- Achieving a baseline level of hardening and implementing recommended best practices requires substantial work and knowledge.
- AD was designed for the network boundary to be the perimeter.
- Domain admins represent a potential security risk and additional solutions are necessary to limit access by temporarily elevating privileges or creating a separate forest.
- Security group memberships must be carefully maintained.
- Delegating tasks to non-administrators should be logged and tracked.
- The potential for privilege abuse is higher when there’s more admins.
- Managing on-premise servers, server roles, and other add-ons increases management overhead and the potential attack surface area.
- AD servers must be patched/mitigated, secured, and maintained. Privilege escalation attacks, using malware-free techniques, have become more common.
- Physical protection from people, fires, floods, and natural disasters is necessary.
- Domain controller backups should be encrypted; backups must be performed correctly to ensure granular restores of all the objects or attributes within a forest.
- AD health monitoring is advisable to analyze the replication status for domain controllers, abnormal behaviors and events, etc., using built-in tools. Azure AD Premium subscriptions are necessary for more robust monitoring of on-premise identity infrastructure.
- AD Group Policies provide intricate control over Windows systems, but only Window systems. Compliance for non-Windows devices requires Intune or third-party services.
- Microsoft and other parties maintain numerous Administrative Templates (.admx).
- Microsoft provides tools such as Advanced Threat Analytics to monitor AD.
- Constant VPN connections are necessary to manage remote Windows Devices through Group Policy.
- Only basic password policies are available to admins without Entra integration. Microsoft offers even more functionality through Defender for Identity and its security business.
- Selling security solutions on top of the AD ecosystem has become a cash cow for Microsoft. Numerous enterprise-grade services are available.
- Microsoft Defender for Endpoint is also recommended if you to extend monitoring to server threats, which also places Microsoft in control of your Endpoint Detection and Response (EDR).
- Reporting is basic, performed through queries, and may require licensing third-party applications and snap-ins to meet compliance needs.
- Patching requires add-on components and services, especially for non-Windows devices.
- The certificate authority (CA), i.e. Windows Server’s Certification Authority role, must be segmented from your primary domain controller, adding another server into your datacenter. Entra also has a certificate-based authentication as an option.
- The RDS server role for remote system access is limited to domain-joined Windows devices; it shouldn’t run off of your domain controller and requires maintaining a Security Group.
- The most premium tier of Entra offers robust identity governance; other Microsoft security service subscriptions such as Sentinel, Defender for Servers, Microsoft Defender for Identity, Defender for Cloud, and more provide enterprise-level tooling. Lateral movement through the Microsoft stack has been observed when an identity is compromised; some organizations may be compelled to purchase these add-ons.
JumpCloud: JumpCloud assists a Zero Trust approach to security through environment-wide MFA, optional conditional access rules, and device trust. Infrastructure may be cloud-only. Commands, pre-built policies, and reports are included. Reporting tools are standard.
- Push or TOTP MFA is present everywhere, including RADIUS and LDAP authentications.
- JumpCloud supports several biometric methods.
- Delegated authentication makes it possible to leverage your existing Entra security policies while using JumpCloud.
- JumpCloud Go, a hardware-bound, phishing resistant credential provides modern authentication.
- Optional conditional access policies offer Privileged Access Management (PAM).
- Policies examine location, mandatory MFA prompts, and whether a device is being managed by JumpCloud. Device state, such as full disk encryption (FDE), is also considered.
- Very little configuration is necessary to achieve security best practices.
- Cloud-based infrastructure reduces attack surface area.
- Pre-built GPO-like policies are available for every supported OS for controls such as FDE. MDM provides tamper-proof compliance.
- Sudo console/terminal and PowerShell commands can be used to deploy compliance benchmarks across your fleet, similar to templates for AD.
- The full JumpCloud platform manages your devices no matter where they are, no VPN required.
- JumpCloud manages identity as your perimeter and devices are the gateway to resources.
- An optional decentralized password manager and vault is integrated into the platform.
- Basic cross-OS patching policies are included; a premium offering provides greater granularity.
- Directory Insights and System Insights offer comprehensive reporting that can be exported to a SIEM. Numerous reports, including Users to SSO, are pre-made.
- JumpCloud offers certificate-based authentication for a passwordless experience on RADIUS and will soon function as its own CA, no additional infrastructure required.
Remote system access (for support purposes) is provided for free using the JumpCloud desktop client and can be toggled “off” by admins from the console.
Total Cost of Ownership
TCO can be a complicated topic. Check out JumpCloud’s TCO calculator.
AD: Active Directory may be free, but it includes inherent infrastructure, licensing, and IT talent costs. You may even need to budget for outside consultants. Those associated costs all rise as your setup becomes more extensive or complex. Entra and other services must be licensed in order to manage non-Windows services, SSO, external identities, and enhanced security.
- The setup for multiple locations requires regional administrators when multiple domains are grouped together into a forest, creating staff and infrastructure redundancies.
- AD best practices cost time and money to implement.
- Account for hardware, network, fire protection, HVAC, power, and other facilities costs.
- Cost will rise as you add server roles and more dedicated servers.
- High availability (HA) is automatic whenever there’s more than one datacenter. Only that configuration makes it possible to shut down a server for maintenance without impacting your end users and stifling business operations.
- Backup and disaster restoration planning, simulations, and execution can become a considerable investment in time and resources.
- Account for current and future Microsoft licensing costs to modernize identity and access management (IAM) and manage users on non-Windows devices.
- Client access licenses (CALs) and core licensing.
- Azure services such as Entra, AutoPatch, Lifecycle Workflows, Entra, Intune, and more might be required to meet modern IT requirements. These are additional costs on top of AD.
- Microsoft charges extra to manage and authenticate external identity providers with Entra.
- Azure licensing is complex and features are gated off into tiers. You can learn more about that in an article that explores the TCO for Entra.
- Account for patching solutions using either third-party tools, WSUS for Windows, or new AutoPatch (a premium Azure offering) for non-Microsoft OSs.
- Account for significant IT management overhead and training costs.
- Maintaining domain controllers and other servers.
- Configuring Microsoft’s synchronization apps for Entra or migrating from AD FS.
- Responding to zero-day vulnerabilities in Windows.
- Third-party security solutions such as Extended Detection and Response (XDR) or purchasing Windows Defender from Microsoft.
- Vendor lock-in and monoculture creates a high dependence on Microsoft. This makes it more difficult to adopt “best-of-breed” solutions, limiting your flexibility and ability.
Note: One price does not equal integration. M365 has numerous disparate tools and consoles, and you need to do the integration to make everything work together as well as with AD. It’s more work for you and more ongoing work in terms of management.
JumpCloud: JumpCloud is cloud-based, which eliminates most infrastructure costs. It integrates advanced lifecycle management and IAM, along with key IT management apps. JumpCloud is an open directory, so there’s no penalty for bringing your own identities.
- HA is available by default without any setup.
- Remote offices can be configured into groups without complex configurations such as organizational units.
- Licensing is workflow-based, versus feature-based. It’s possible to license what you need or adopt the entire platform for advanced lifecycle management with Zero Trust security.
- SSO, MFA, advanced lifecycle management, policies, remote assistance, UEM, and reporting are included in the platform.
- Conditional access, advanced patch management, and the password manager are optional add-ons, but work seamlessly with the platform.
- Services such as RADIUS and LDAP are cloud-based and immediately available.
- There’s no upcharge for managing external identities or authentication.
- JumpCloud integrates and syncs with AD, but can also function as a standalone directory to enable a domainless enterprise configuration.
- JumpCloud is an open directory platform that assists with unifying IT resources. It’s possible to avoid vendor lock-in and select best-of-breed solutions.
- The interface is simpler and more streamlined than many AD and Azure features.
Reskilling your existing team and/or obtaining external resources is often necessary to adopt Entra, Intune, and other M365 services. You should also consider the potential cost of higher salaries to match market levels for speciality admin roles as M365’s advanced features are implemented. Also explore any potential changes to your organizational structure and procedures in order to fully implement all the Microsoft products that you’ll be paying for.
Accounting rules make a distinction between software and services. Using services helps your organization to lower its income taxes and free up cash. Services may make it easier to budget when you already know what the ongoing costs will be.
Can I Replace Active Directory with JumpCloud?
It’s possible to manage your organization’s IT infrastructure with JumpCloud or to modernize AD to meet the demands of today’s requirements. It’s architectured for small and medium-sized enterprises (SMEs), keeping its complexity low but its value high.
The choice is yours: Entra isn’t mandatory to accomplish what you need and may not be the best fit, or its enterprise-grade features might be more helpful for your situation. The best way to determine how well JumpCloud’s open directory will work for you is to schedule a free demo.





