Active Directory (AD) modernization should be on your radar. It’s no longer elective and only for cloud migrations, it’s an actuality that every organization using AD is facing. Microsoft has revised its reference architecture and access models into a hybrid cloud solution; on-premise products that provide privileged access and secure AD from threats are being phased out.
Investment into new features to modernize, secure, and protect AD has shifted into Microsoft’s cloud ecosystem. The end result is a vertically integrated suite of services and tools that’s one-size-fits-all. This is a prescribed path for every size business that uses AD and can expand Microsoft’s footprint into nearly every facet of your IT stack by virtue of its product bundling.
Many IT admins tuned out Microsoft’s declarations about a cloud future over the past decade and went about their business as usual, but its vision has become prescriptive and productized, and change is imminent. Controlling user identities is a key element. However, its architecture may not work well for every organization, either technically or in real-world IT operations. Fortunately, options such as JumpCloud’s open directory platform exist to modernize AD, which adhere to the same principles for Zero Trust security that Microsoft ‘s architecture follows.
Active Directory as a Legacy Product
AD has been designated as a legacy product in Microsoft’s publications and in communications from its team members (it’s impolite to call anyone out, but check out their LinkedIn posts). These things don’t happen in isolation; believe what it is saying. It’s well known that foundational elements of the Windows Server stack have long been cloud bound: Exchange, aka Exchange Online, and Windows Server Update Services (WSUS), which is now Configuration Manager. Configuration Manager is optimized for cloud co-management, which “unlocks” features such as conditional access that Microsoft says are essential to protect users.
Note: Microsoft’s tools for AD security and compliance are limited without its cloud services. Extended support for fully featured on-premise products won’t last forever.
Additionally, mainstream support has ended for Advanced Threat Analytics (ATA). Defender for Identity is its cloud replacement, which is just one part of a broader cloud-based security model. Microsoft Identity Manager, which manages privileged access for AD, is also marked for a gradual phase out over the next few years with Entra ID’s most premium SKUs as its designated replacement. These changes are occurring as part of a major shift in how AD is managed.
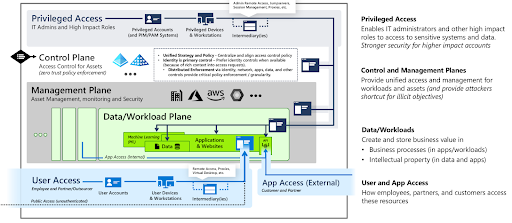
The revised reference models and modernization plans include:
- The enterprise access model for managing privileged access.
- The Microsoft Cybersecurity Reference Architecture (MCRA), which layers multiple cloud services around AD, with identities being managed by Entra ID. Microsoft is investing in development of these cloud services to secure and protect AD, versus improving AD.
- The Zero Trust Rapid Modernization Plan (RaMP), which recommends that cloud identity and access management (IAM) and unified endpoint management (UEM) be deployed.
Next, we’ll explore the products and services that Microsoft recommends be used with AD in order to modernize it to meet today’s IT requirements and secure users and resources. The overall path that it prescribes doesn’t distinguish between small and medium-sized enterprises (SMEs) that might struggle to implement these services, or very large organizations.
Microsoft’s Plan for AD: Use More Microsoft Products
Microsoft’s approach to modernization isn’t just about supporting non-Windows devices or using a centralized Identity Provider (IdP) to reestablish access control across all of your apps and resources. The MCRA prescribes using Entra ID Premium 2 with Defender security services to prevent lateral movement through its stack in response to the latest cyber threats. Standalone AD is vulnerable without modernization, and Microsoft is layering on more products in response. You’ll find yourself subscribing to the following if you follow its suggestions:
- Entra ID Premium 2 (P2) includes Identity Protection to detect, investigate, and remediate identity-based risks in organizations that have modernized AD by using Entra. For example, password spray attacks occur when attackers attempt to compromise accounts by using a curated list of passwords that may be associated with those users. Identity Protection assists with limiting the risk of identity-based attacks across its stack.
- Intune to manage your endpoints, including Windows. Its latest preview features, such as Group Policy analytics, will analyze on-prem Group Policy Objects (GPO) and map them to Intune. This foretells a fully cloud-managed infrastructure.
- Defender for Identity is a safeguard that protects AD against lateral spread through the Microsoft stack. It’s not included with Entra P2 and must be licensed separately. Standalone AD is vulnerable to privilege escalation when unpatched (or zero-day vulnerabilities) or misconfigurations are exploited to bypass its security.
- Defender for Identities won’t work to its full potential without Microsoft Defender for Endpoints, an endpoint detection and response solution, being installed to account for server threats.
- Defender for Servers is recommended if you host AD in AWS or GCP for cloud security posture management (CSPM).
- You cannot utilize Microsoft’s cloud security services for AD without adopting Entra ID. AD will interoperate with other identity providers (IdPs), but it’s still central to your IT infrastructure under Microsoft’s new architecture that surrounds AD.
Drawbacks for SMEs
Microsoft’s prescribed pathway to AD modernization has several major drawbacks.
Those include:
- Locking SMEs (and AD) into a suite of vertically integrated tools.
- Limiting freedom of choice to utilize today’s best-of-breed technologies by bundling unrelated IT services with IT management products.
- Microsoft’s guidance suggests that customers partner with vendors to completely implement these services and any handle change management. This makes system management more complex and costly.
- Distracting IT from its core mission by diverting resources to using its ecosystem.
Its plan for AD modernization may work out well for some Microsoft shops, but SMEs don’t have unlimited assets to update a legacy solution. If you’re thinking “we don’t need all of that,” please remember that AD modernization can’t be disregarded. Consider JumpCloud as an alternative.
JumpCloud’s Open Directory Platform Modernizes AD
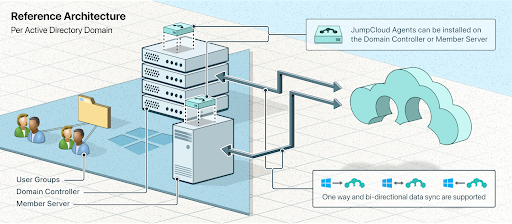
Think back to RAMP, Microsoft’s guidance to adopt a Zero Trust security strategy. JumpCloud manages identities as a full-fledged IdP, but it can also sync and federate with other IdPs. That includes Active Directory Integration (ADI), which has multiple deployment models to meet your company’s needs and objectives. ADI has a scalable deployment model that uses member servers to configure syncing with AD. It’s even possible to sync multiple domains to JumpCloud.
Integrated UEM (which contains, among other things, MDM and EMM services) secures access to resources from every device. Single sign-on (SSO) supports web authentication (RESTful API, OIDC, and SAML) in addition to commonly used network protocols (RADIUS and LDAP). This posture ensures that multi-factor authentication (MFA) will be used everywhere it should be. JumpCloud Go™ delivers a modern authorization that’s phishing-resistant via a hardware-bound credential. Likewise, JumpCloud features optional conditional access, which is central to Microsoft’s new enterprise access model for AD.
Note: You can follow Microsoft’s guidance without following Microsoft.
Other features that can modernize AD include:
- A large catalog of pre-built SSO apps and the ability to create custom apps
- A decentralized password manager with business collaboration features and management for when SSO isn’t an option
- Dynamic groups to automate lifecycle management and simplify onboarding users and devices. Pre-built integrations with popular HR systems keep entitlements up to date
- SCIM provisioning to streamline app authorizations from groups at no additional cost
- Certificate-based authentication for RADIUS to secure your Wi-Fi in addition to dynamic VLAN assignments
- Pre-built reports and telemetry from your devices, directory, and SSO apps
- Software management and a private repository (coming soon)
- Commands and scripting with a virtual command line interface (coming soon)
- Optional cross-OS system and browser patch management
- Optional Remote Assist
SMEs can use JumpCloud to modernize AD from a single console due to its integration with AD, and unification of IAM with UEM. Essential management tools are optional help to ensure that systems are patched and supported. And you don’t have to enlist vendors to implement it.
Read more about how JumpCloud compares to Entra ID and Intune.
Modernize AD on Your Terms
AD modernization is important, no matter where you land on that journey. There’s more than one way to accomplish it, and Microsoft’s way may not be what’s best for you. Get started with a trial today, or contact us to discuss your needs and how JumpCloud can help. We provide complimentary support to get you started and professional services that are tailored for SMEs.




