The JumpCloud agent lets you set user access controls to elevate the standard permissions on a user to Admin/Sudo or Passwordless Sudo. Specific, privileged permissions on devices ensure that your company's devices are secure and protected.
There are two ways to manage access levels of users:
- User Groups
- Setting Permissions on a User Group per Device Group Bind
- Setting Permissions on a User Group for All Associated Device Groups
- Users
- Setting Permissions on a User per Device Bind
- Setting Temporary Permissions on a User per Device Bind
- Setting Permissions on a User for All Associated Devices
Windows users need to log out and log back in for permissions changes to take effect.
User Groups
Setting Permissions on a User Group per Device Group Bind
Setting permissions at the user group level centralizes management of elevated device permissions in a single place. Permissions set at the user group level will be applied to associated device groups. Group members will inherit permissions to devices that are associated with those device groups.
Considerations:
- Permissions that are granted directly on a user supersede permissions granted at a user group level.
- Permissions set at the user group level supersede any permissions previously set on the user group’s bind to a device group.
- It’s possible to have permissions added on both the direct user association to the device and the indirect group association to the device. This is visible on the association of a user and a device. However, if there is an indirect group association to the device, you won't be able to apply elevated permissions directly between a user and device. To be able to apply elevated permissions directly between the user and device, the user or device needs to be removed from the user group.
- It's possible to remove duplicate permission assignments on a user to device association via removing the elevated permission on the associated device by selecting No Elevated Permissions or by removing the user from the group.
- If group permissions are inherited globally on a user group, the permissions can show up as inherited group permissions.
There are two ways to provide Admin/Sudo access through user groups:
- Via the Device Groups tab, so that all users in a user group have access to a specific device group(s) associated to that user group.
- Via the Details tab, so that all users in a user group have access to all device groups that are bound to that user group.
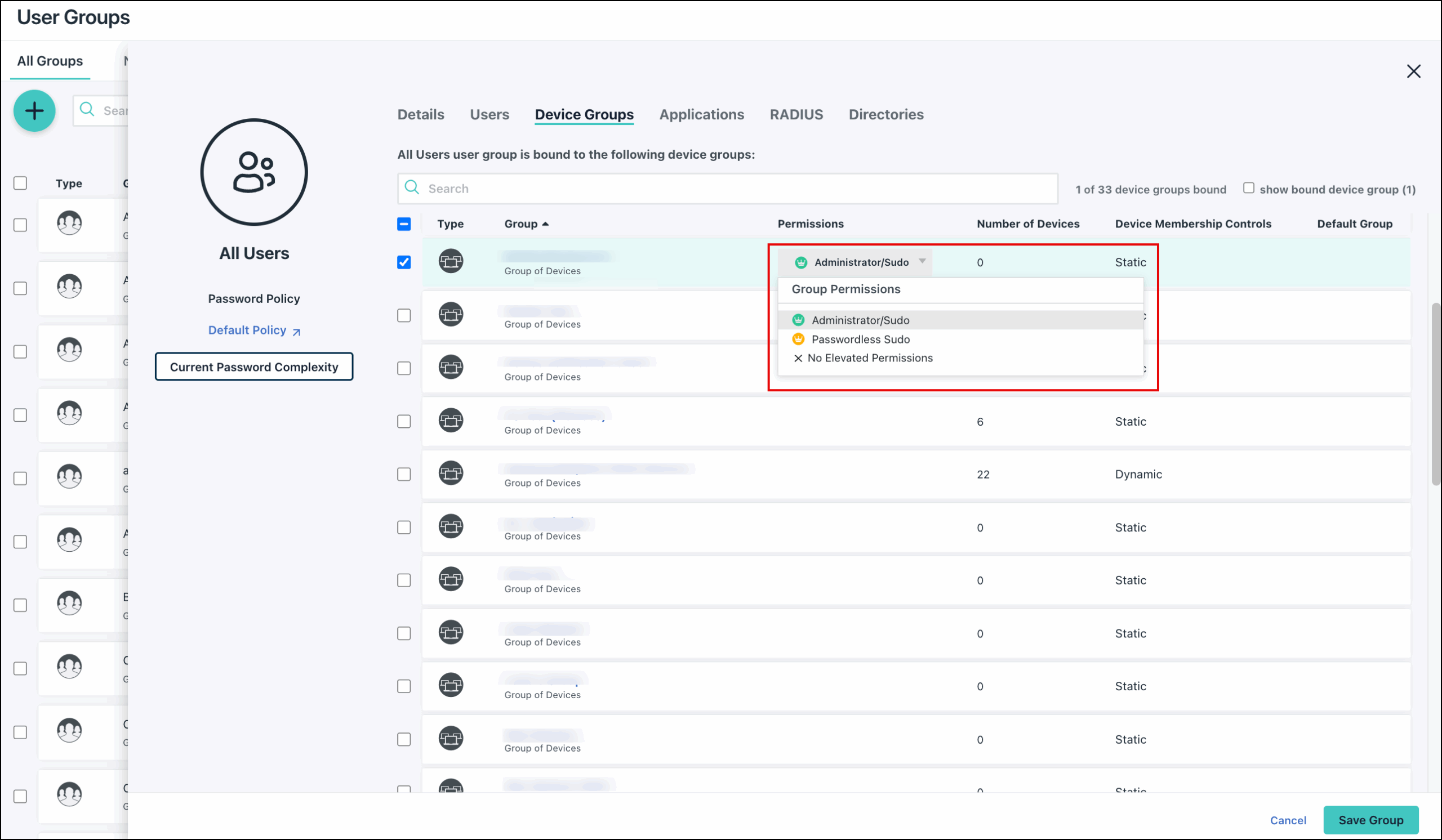
To give users within a user group Admin/Sudo access to devices via the Device Groups tab:
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to User Management > User Groups.
- Select the applicable group by clicking on the User Group name under the Group column.
- Click the Device Groups tab and then select the applicable device group under the Group column.
- Click the dropdown arrow under the Permissions column, select the desired permission, and click save. The sudo permission is now set for users in that user group for every device associated with the device group.
- When unchecked, permissions can be managed from the Device Groups tab or on an individual user/device basis.
- Passwordless Sudo is applicable to Linux and Mac devices and only recommended for service accounts.
Setting Permissions on a User Group for All Associated Device Groups
To give users within a user group Global Admin/Sudo access via the Details tab:
- From the JumpCloud Admin Portal., go to User Management > User Groups.
- Select a User Group from the list. The administrator will see the Details tab for that user group by default.
- Click the Enable users as Global Administrator/Sudo on all devices associated through device groups checkbox and click save. All users in that user group will be given global admin permissions on all devices bound to any device group associated with the user group.
- Passwordless Sudo is applicable to Linux and Mac devices and only recommended for service accounts
- You can also go to the Device Groups tab to control this setting on a group to group basis
- A Permission Settings Update email notification is sent.

Users
Setting Permissions on a User per Device Bind
Users that aren't admins on all of their devices can be given elevated permissions on a per-device basis.
Considerations:
- Elevated rights are only granted on the devices you explicitly choose. By default, users don’t have administrator permissions.
- The only exception to this are Apple Device Enrollment (AD) enrolled users, who do have admin permissions.
- If the user is bound to the device via group membership, an indirect device binding is created. To remove access to the device, remove the user from the group.
- If you still wish to assign elevated permissions on a per device basis, make sure the device is not part of an existing user group. See Best Practices for Migration of Device Permissions from a User to a Group for more information.
- Suspended or revoked users won’t have access to the device. See Suspend and Reactivate User Accounts to learn more.
- You can also manage device level permission from Device Management > Devices > Users.
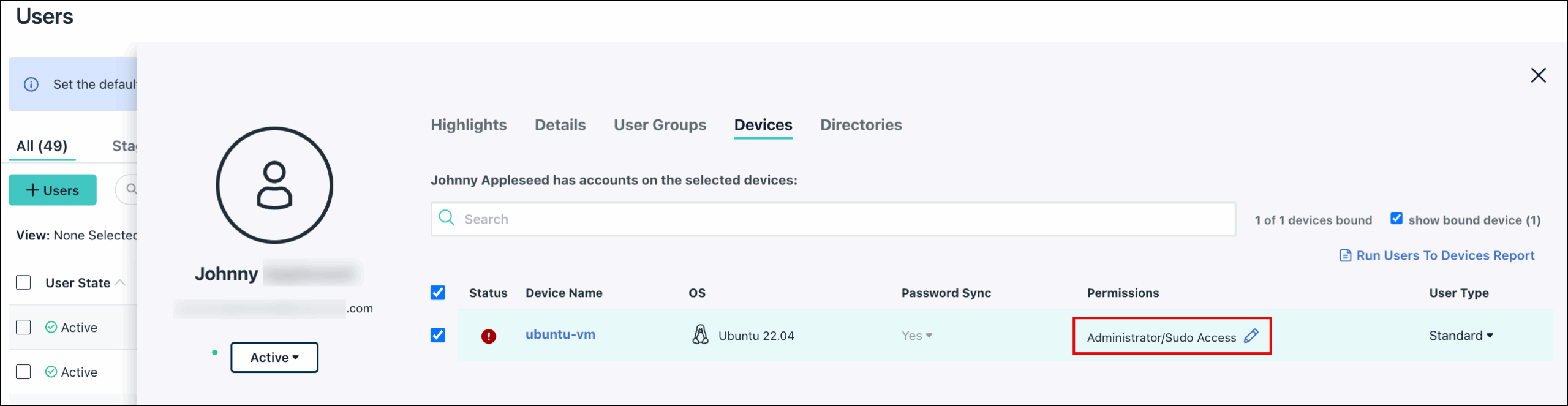
To set a user as an Admin/Sudo on a connected device:
- From the JumpCloud Admin Portal, go to User Management > Users.
- Select a user and click the Devices tab to view the devices connected to this user.
- (Optional) To display both bound and unbound devices, clear the show bound device check box.
- On the desired device, go to the Permissions column and click the pencil to Edit permissions.
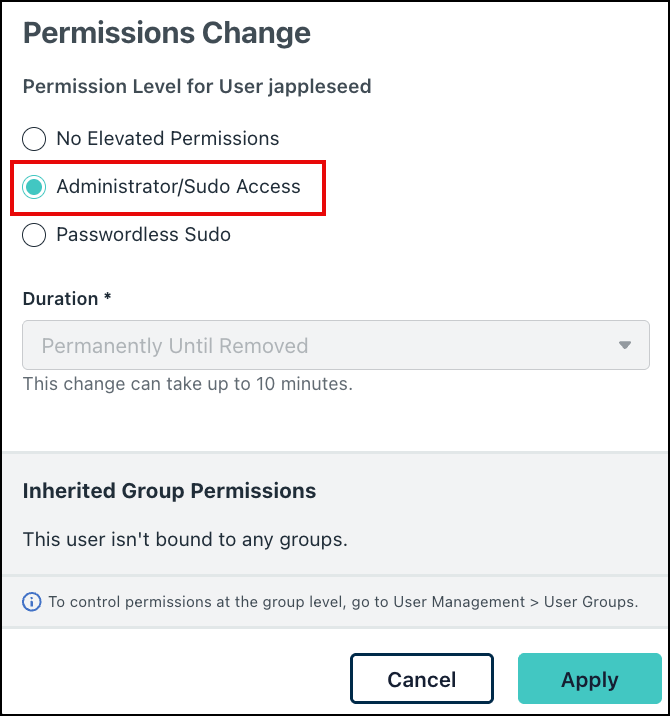
- In the Permissions Change window, select Administrator/Sudo Access and set the Duration to Permanently Until Removed.
- Click Apply.
- Click save user.
Setting Temporary Permissions on a User per Device Bind
You can also assign a user that's not admin on all of their devices temporary elevated privileges. A user can perform needed administrative actions on their device for a fixed period of time, and then their permissions are automatically revoked.
Considerations:
- You can only grant temporary elevated permissions on a direct user to device association. Group associations aren’t supported.
- You can't assign temporary elevated permissions to a user that's set as a Global Admin/Sudo on all devices. See the following section Setting Permissions on a User for all Associated Devices to learn more.
- Permission changes can take up to 10 minutes to expire on the device.
- A network connection is required to make permissions changes. If a device’s network connection is interrupted when the temporary permissions are scheduled to expire, the temporarily assigned permissions may persist until the device reconnects and receives new instructions to revoke the elevated permissions.
- Windows users may need to log out and log back in for changes to take effect.
Here's a guided simulation: Temporary User Permissions per Device.
To assign temporary Admin/Sudo access to a user’s device:
- From the JumpCloud Admin Portal, go to User Management > Users.
- Select a user. The user Highlights tab displays.
- Click the Devices tab to view the devices connected to this user. The user’s bound devices display by default.
- (Optional) To display both bound and unbound devices, clear the show bound device check box.
- On the desired device, go to the Permissions column and click the pencil to Edit permissions.
- In the Permissions Change window, select Administrator/Sudo Access and select the appropriate Duration from the dropdown.
- For example, if the user needs to install software on their device, select a short time period such as 1 hour. After the designated time, the user’s permission returns to No Elevated Permissions
- Click Apply.
- Click save user.
Revoking an Existing Temporary Permissions Change
You can remove a user’s temporary elevated privileges ahead of the expiration time set in the previous step.
To modify existing temporary Admin/Sudo permissions:
- From the JumpCloud Admin Portal, go to User Management > Users.
- Select the user in the list. The user Highlights displays.
- Click the Devices tab and locate the device with remaining time on Administrator/Sudo Access.
- In the Permissions column, click the pencil to Edit the elevated permissions.
- In the Permissions Change window, select No Elevated Permissions to change the user’s permission level for this device.
- Click Apply.
- Click save user.
Setting Permissions on a User for all Associated Devices
Admins can assign global Admin/Sudo permissions on a user to apply to all devices associated with that user.
Considerations:
- The enabled user is given global Admin/Sudo privileges on all devices to which they are bound.
- When the Enable as Global Administrator/Sudo on all device associations option is cleared, you can manage global Admin/Sudo privileges on a per-device basis from the Devices tab.
- Passwordless Sudo can also be assigned to Device Admins for Mac and Linux. You need to configure Windows device UAC settings to require an admin password.
- Global settings can't be modified on a per-device basis.
- You can also manage a user's permission level from DEVICE MANAGEMENT > Devices > Users.
To set a user as a global Admin/Sudo on all associated devices:
- From the JumpCloud Admin Portal, go to User Management > Users.
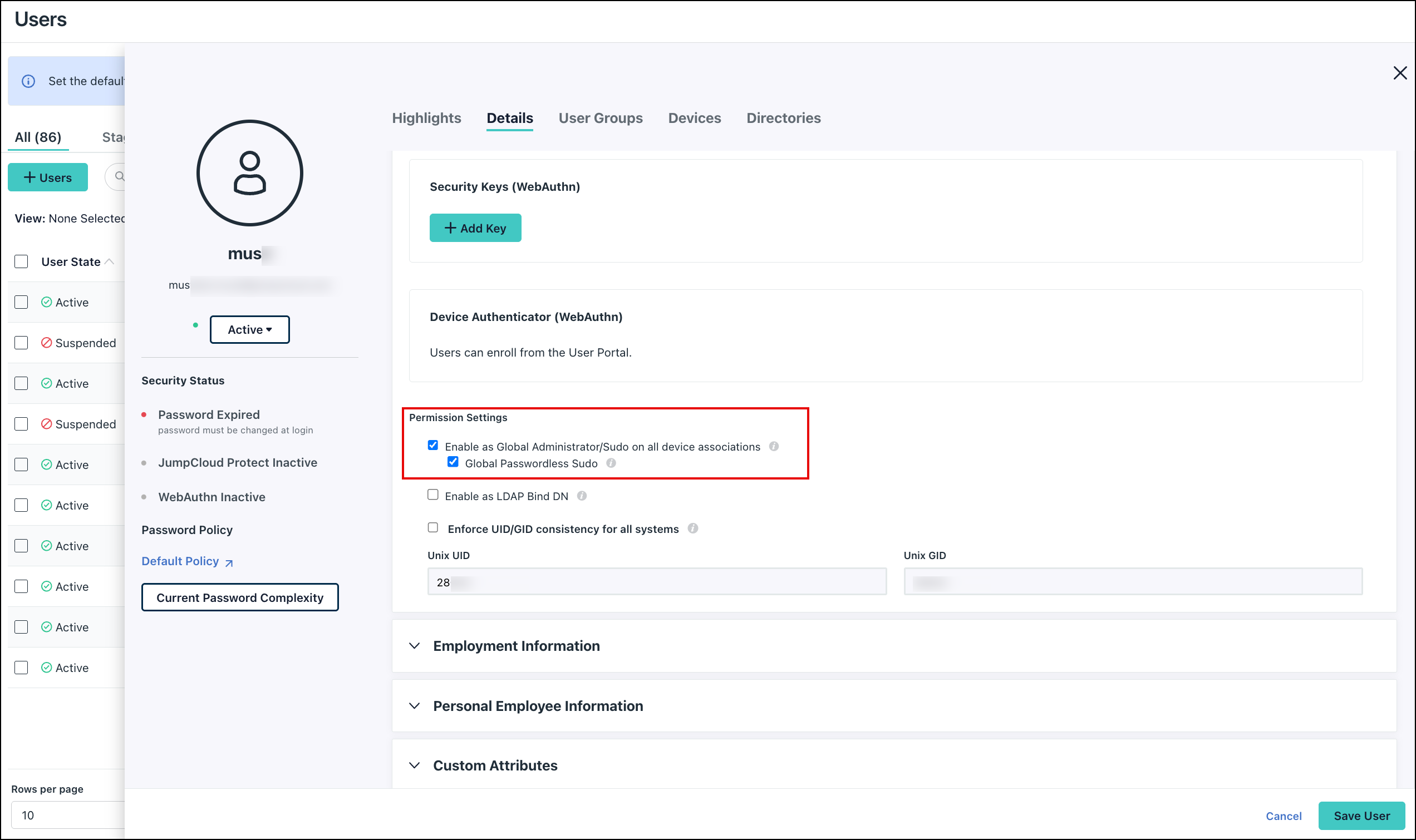
- Select a user and click the Details tab.
- Expand the User Security Settings and Permissions section.
- Click the Enable as Global Administrator/Sudo on all device associations checkbox to select it and click save. You'll receive an email from JumpCloud confirming that the user now has global Admin/Sudo permissions on all associated devices.
- To remove global Admin/Sudo permissions for all of a user's devices, uncheck the Enable as Global Administrator/Sudo on all device associations checkbox and click save.
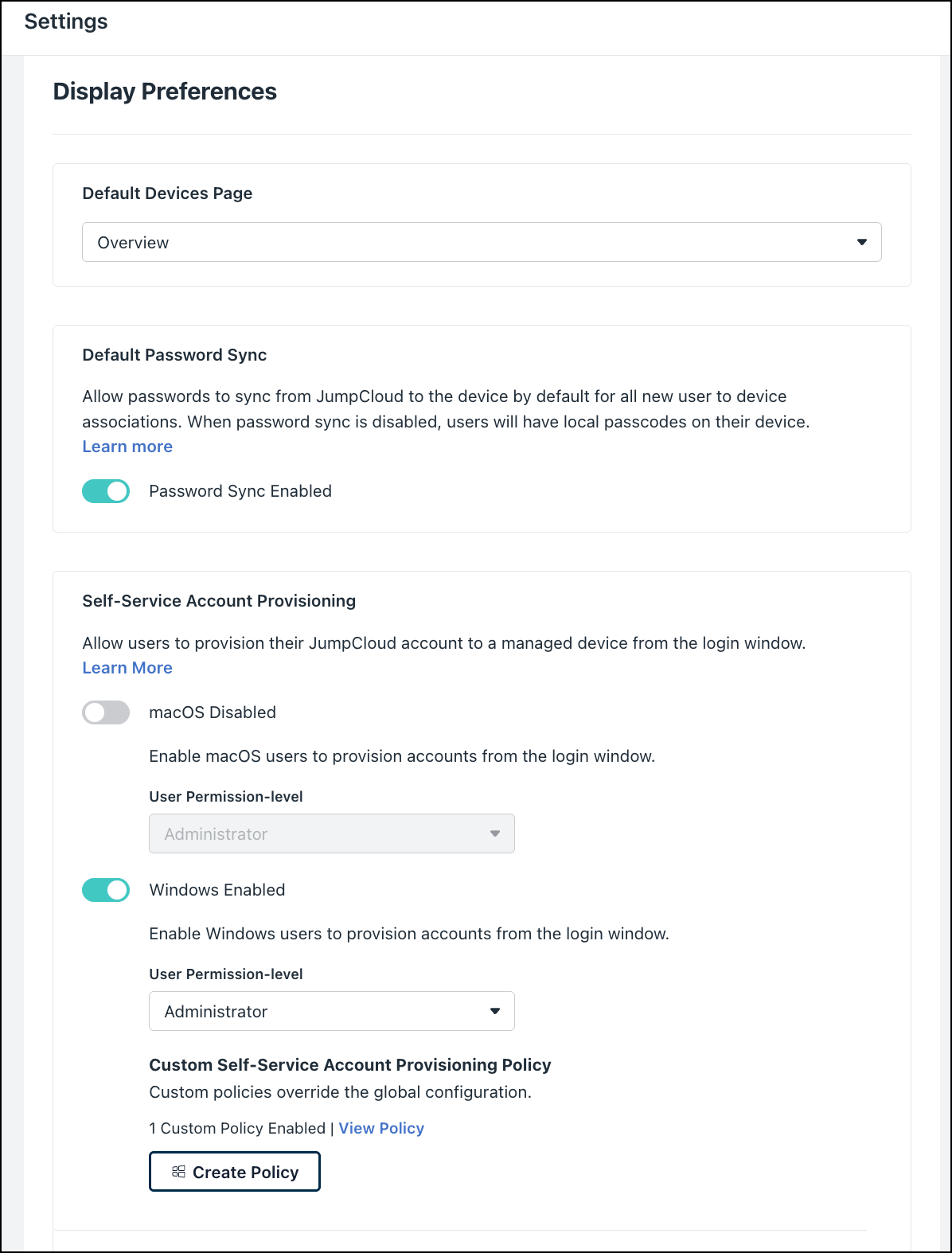
Setting Permissions with Self-Service Account Provisioning
If you’ve enabled Self-Service Account Provisioning, you can set Admin/Sudo permissions for newly joined accounts from the Device Settings menu. See Provision New Users on Device Login.
A user’s permission level can be adjusted after provisioning by Setting Permissions on a User per Device Bind.