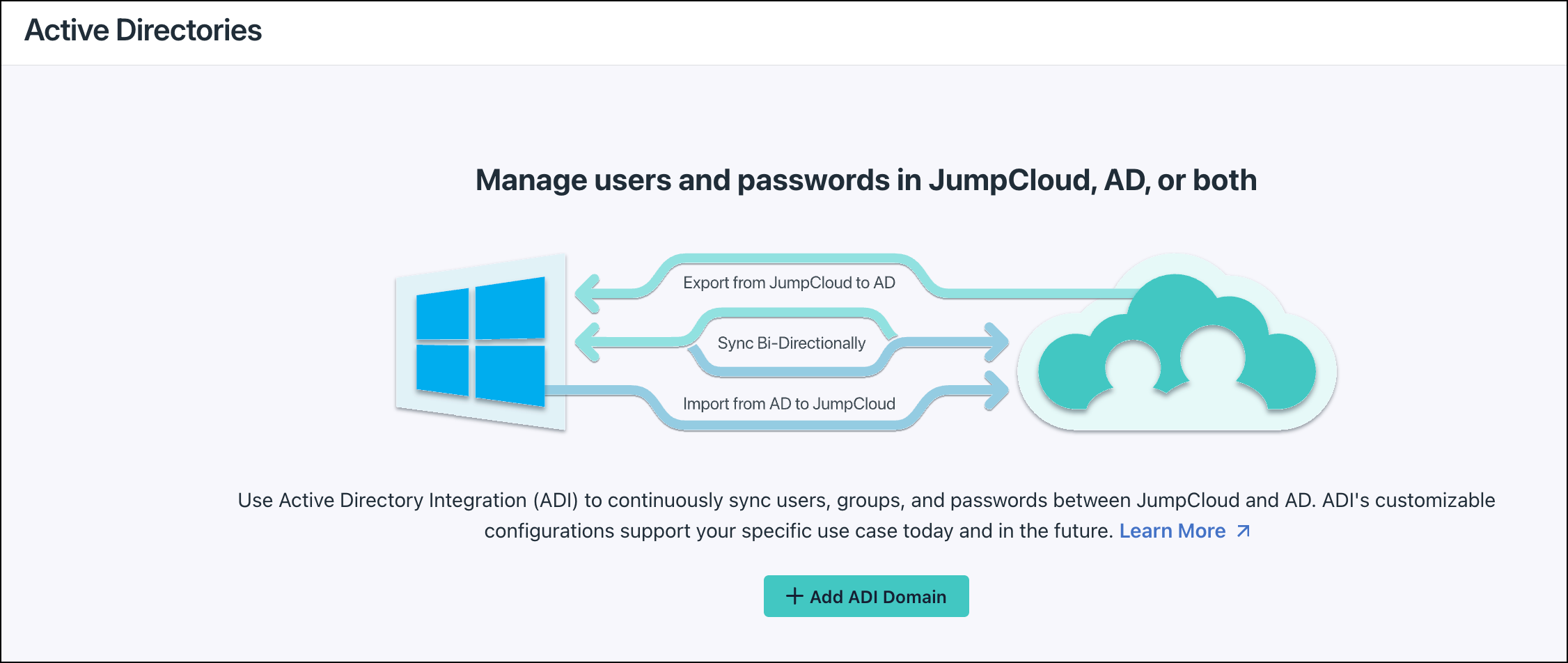
This article provides a step-by-step guide for configuring ADI to manage users, security groups, and passwords in AD, JumpCloud, or both. This configuration allows AD and JumpCloud to co-manage users, groups, and access in a full two-way sync, providing the greatest flexibility. This configuration supports:
- Syncing data bidirectionally between JumpCloud and AD (two-way sync)
- Managing passwords in either system or both
- Creating, updating, and deactivating users in either system or both
- Creating and managing user (security) groups in either system or both
- Managing group membership in either system or both
Deployment Configuration Overview
- Use both the ADI import agent and ADI sync agent
- Install agents on either domain controllers (DCs) or member servers
To sync passwords from AD to JumpCloud, the import agent must be installed on all DCs.
- Add users and security groups under the ADI security group in AD to sync from AD to JumpCloud
- Assign users and user groups to the ADI AD domain in JumpCloud to sync from JumpCloud to AD
To explore the use cases and benefits of this configuration see Manage users and passwords in either system, or both in the Configure Active Directory Integration (ADI) help center article.
Workflows
Two-way sync – single domain

Two-way sync – multiple domains

To learn more about the general user identity workflow and expected behavior for any user, group, and password change after the AD Import and AD Sync agents have been configured, read Use and Manage the Active Directory Integration (ADI) .
System Requirements
- 64-bit Windows Server (versions 2012, 2016, 2019, 2022)
- Server Core installation is also supported for Windows Server versions 2016, 2019, and 2022. You will need to include the /msiexec parameter when running the agent installer
- 15MB disk space
- 10MB RAM
Installation Steps Overview
The main steps you will take to install and configure AD for bi-directional use are:
- Determine on which servers the AD import agents will be installed: member servers or domain controllers (DCs).
- Complete the prerequisite checklist.
- Determine the Root User container in AD.
- Create the JumpCloud ADI Integration Security Group in AD.
- Create the AD Import Service Account.
- Create the AD Sync Service Account.
- Delegate control for the AD Import and AD Sync Service Accounts.
- Create an AD domain instance in JumpCloud.
- Select your configuration and download the agents.
- Run the the AD Import Agent installation wizard.
- Reboot each AD server where the import agent was installed.
- Verify the Import Agent Service started.
- Complete post-installation AD import agent configuration on each DC.
- Run the AD Sync Agent installation wizard.
- Verify AD sync and AD import agents in the JumpCloud Admin Portal.
Considerations
Agent Version Considerations
Import Agent
When upgrading from AD import agent v2.6.0 or lower, you must select Install New Agent from the Downloads dropdown menu in the ADI Details page to get the connect key, which is required to complete the upgrade of the agent on the AD server.
Member Server Installation Considerations
The following are considerations only if you choose to install the ADI agents on member servers:
Import Agent
- The AD password does NOT sync from AD to JumpCloud - users imported and synced from AD will not have a password in JumpCloud
- Reboot required
Sync Agent
- If you have member servers in your AD environment, installing the sync agent on member servers is the recommended option
- All sync agent functionality works when the agent is installed on member servers
- Reboot NOT required
Domain Controller (DC) Installation Considerations
The following are considerations only if you choose to install the agents on DCs:
Import Agent
- Reboot required - downtime should be scheduled
- ADI import agent must be installed on all Domain Controllers.
- AD passwords will sync from AD to JumpCloud
Sync Agent
- A sync agent does NOT need to be installed on all Domain Controllers
- Installing the sync agent on more than one DC is recommended for redundancy and high-availability
- The installation does not require a server reboot
- JumpCloud passwords will sync from JumpCloud to AD
Security Considerations
- It is STRONGLY recommended to install and use LDAPS for the ADI. Configuring and using LDAPS when agents are installed on a member server secures any sensitive information that is exchanged between the JumpCloud agents, the member server, and the Domain Controller, and protects against malicious users
- We recommend periodically rotating the passwords for the server accounts used by the integration e.g., jcimport and jcsync) for security reasons
Agent Upgrade Considerations
You must use the same AD admin account used to initially install the agents. Otherwise, the agent services won't start due to a credential error. The agent service account password is machine + user encrypted when stored in the registry.
If you don't know which account was used:
- For import agent, you must re-enter the credentials for the import agent service account in the registry.
- For sync agent, you will need to select the option to review existing configuration settings and enter the credentials in the LDAP credentials screen
- The import agent installation wizard prompts for minimal information when upgrading:
- Agent connect key, when upgrading from import agent v2.6.0 or lower
- ADI deployment configuration
- Prompts for configuring new settings
- Directory for where the installation should occur
- Finish screen
- The sync agent installation wizard gives you an option to see all installation screens or only the ones for configuring the new settings.
User Sync Considerations
Review Use and Manage the Active Directory Integration (ADI) for detailed information about syncing and managing users, user (security) groups, and passwords.
- Synced users must have values for <First Name> and <Last Name>, i.e., the first name and last name fields cannot be empty, otherwise the users will fail to sync.
- The JumpCloud ADI import and sync agent services use TLS for all communication. If no network connectivity exists to JumpCloud, the ADI won’t work properly
Delegated Authentication Considerations
The delegated authentication functionality is specific to the ADI AD import agent. Review ADI: Use AD Delegated Authentication for specific considerations and more information about delegated authentication to AD.
General Installation Considerations
All installed agents should be the same version to avoid unexpected behavior or the potential for users not being able to log in if the primary agent is switched.
You must reboot the servers after the AD Import Agent installation.
You DO NOT need to reboot the servers after the AD Sync Agent installation.
- The AD sync agent does not need to be installed on all servers.
- Connect Keys are one-time use keys required for installing the agents on a new AD server. They expire in seven days.
- The AD Domain and Root User container DN must be the same for both the AD import agent and AD sync agent
- Non-standard ASCII characters are not supported in the Root User DN.
- When upgrading an agent, the installation wizard will have a few different prompts :
- Upgrading from AD import agent v2.6.0 or lower to v3.0.0 or higher will also prompt for the import agent connect key.
- An ADI integration specific Security Group (e.g., “JumpCloud”) must be configured within the root user container or root OU to import and sync users from AD to JumpCloud:
In multi-domain environments, the security group must have a unique name within each domain (e.g., “JumpCloud (mydomain1)” and “JumpCloud (mydomain2)”)
- Demoting a DC installation to a member server and promoting a member server installation to a DC aren’t supported. The agent(s) must be uninstalled first and then installed on the other type of server.
- A reinstall of the same ADI import agent is treated as an update.
- When multiple AD agents are installed, one import agent and one sync agent are designated as the primary agent by the ADI service. All create and change requests are sent to that agent. If that agent becomes unavailable, another active agent is automatically designated as the primary. For the import agent, all delegated authentication requests are also sent to the primary agent.
- When updating an existing agent installation, only minimal installation screens are shown:
- Directory for where the installation should occur
- Finish screen
Migrating device accounts from AD Managed to JumpCloud Managed
- JumpCloud has a tool, called the ADMU, which is used to migrate end-user Windows computers from AD to JumpCloud
Attributes
The user attributes that sync from AD to JumpCloud and JumpCloud to AD are:
- First Name
- Last Name
- Username
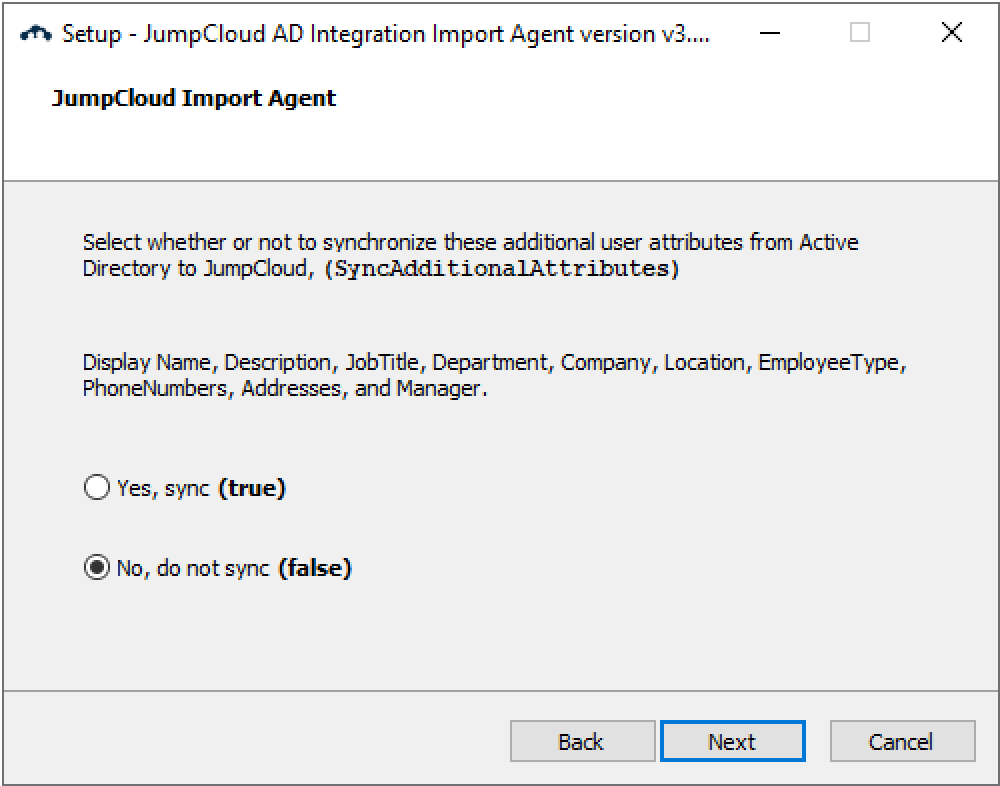
If the SyncAdditionalAttributes setting is true in the jcadimportagent.config.json file, the following attributes are also synced from AD to JumpCloud:
- displayname
- description
- JobTitle
- department
- company
- location
- employeeType
- phoneNumbers
- addresses
- manager
These attributes become read-only (restrictedFields) in JumpCloud when a user's Password Authority is set to Active Directory. The Password Authority setting can be changed for a specific user directly from their User Details page or for multiple users from Users >More Actions>Set External Password Authority.
Prerequisite Checklist
Before installing the AD import and AD sync agents, we recommend completing each of the following checklist items before continuing.
- Know your AD Domain Admin credentials.
- Decide whether you want to install the sync agents on your AD domain’s non-DC Domain Member Servers (member servers) or Domain Controllers (DCs).
- When installing the import agent on DCs, schedule downtime. Installation requires server reboot!
- If installing the AD sync agent on DCs, we recommend that you install the AD Sync agent on your Primary DC and any DC impacted by extended replication delays.
- Verify you have access to all DCs or member servers in the AD domain.
- Ensure your DCs or member servers are running on a JumpCloud supported 64-bit Windows Server version (2012, 2016, 2019, 2022).
- Verify DCs or member servers have networking access to the internet and are able to communicate outbound to console.jumpcoud.com over HTTPS port 443.
- Verify all users to be synced from AD to JumpCloud and JumpCloud to AD have a value for first name and last name.
- Align password complexity requirements between AD and JumpCloud as closely as possible. Otherwise, passwords may not replicate if they’re rejected by the destination directory’s complexity requirements.
- (Recommended) Verify all users you plan to import into JumpCloud live in a single OU or are nested underneath a chosen OU (Root user container) in AD. This can be the default CN=Users container in AD or an alternate custom OU in the directory.
- Review Advanced Configurations for Active Directory Integration to understand the configuration settings available for the import agent and note any default values that need to be changed as part of the installation.
- (Strongly recommended) Install LDAPS when installing the agents on a member server.
We strongly recommend installing and using LDAPS for the ADI when the agents are installed on a member server. Configuring and using LDAPS on the Domain Controller that the JumpCloud ADI agents will connect to from a member server secures any sensitive information that is exchanged between the JumpCloud agents, member server, and the Domain Controller and protects against malicious users.
Prepare AD for the Agent Installations
The steps outlined below must be done on a DC, even if you plan to install the import agents on member servers. A server reboot is NOT required after completing these changes.
Determine Root User Container
Prepare for the agent installations in AD by determining the Root User Container.
The DN must be the same for both the AD import agent and AD sync agent.
To use a Root User Container other than Active Directory's default (CN=Users), you'll need its distinguishedName value. You'll enter this value in two places:
- During the AD import agent installation.
- During the AD sync agent installation.
To obtain the User Container distinguishedName:
- Verify the full LDAP path for the chosen Root user container you have selected in ADUC:
- From the ADUC panel’s View menu, enable Advanced Features.
- Right-click the container and select Properties.
- Select the Attribute Editor tab.
- Select the “distinguishedName” attribute, then click View.
- Note the value. It will need to be entered during both the AD import and AD sync agents installation.
You will need to replace the commas (,) with semicolons (;) when entering the DN during the agent installation
AD Import Agent
The AD import agent installation wizard prompts you to enter the Root User container's Distinguished Name (DN) which will be stored in the import agent configuration file
If you want to use AD’s default Root User container, the value you will need to enter during the AD sync agent installation is CN=Users;DC=example;DC=com. Otherwise it will be the path you noted after following the steps in the section above.
AD Sync Agent
The AD sync agent installation wizard prompts you to enter the Root User Container during the JumpCloud AD sync agent installation.
If you want to use AD’s default Root User container for the JumpCloud AD Integration, the value you will need to enter during the AD sync agent installation is CN=Users;DC=example;DC=com. Otherwise it will be the path you noted after following the steps in the section above.
Create the JumpCloud ADI Integration Security Group in AD
A Security Group for the integration must be created within the Root User Container you’ve defined in the previous step. This Security Group is required. Any member of this group will be synced from AD to JumpCloud.
If you do not create this group or give it a unique name across domains, the ADI sync from AD to JumpCloud will fail to function properly.
- Open the ADUC Menu, click the Start button, type “dsa” and click the Active Directory Users and Computers icon.
- Find your Root User Container.
- Right-click the Root User Container’s folder and click New > Group.
- Ensure the Security Group is a Global Security Group.
- Give the Security Group a name that helps identify it as the group used by the ADI (e.g., “JumpCloud” for single domain environments, “JumpCloud-Domain” for multi-domain environments).
- Click OK.
In multi-domain environments, the security group must have a unique name within each domain (e.g., “JumpCloud-mydomain1” and “JumpCloud-mydomain2”).
Create the AD Import Service Account in AD
After you identify the ‘Root user DN’ that you want to use with your JumpCloud integration, you proceed by creating a new AD-based service account (standard user account) that allows the JumpCloud AD import agent to manage users and groups.
- Open the ADUC Menu, click the Start button, type “dsa” and click the Active Directory Users and Computers icon.
- Find your Root User Container.
- Right-click the container and click New > User.
This user cannot:
- Be a Domain Administrator
- Be a member of the JumpCloud integration security group
- Have a username of “JumpCloud”
- Enter the following values for the JumpCloud Import Service Account user:
- First Name: JumpCloud
- Last Name: Import
- User logon name: jcimport
Use jcimport to distinguish what this user is for and to which agent it is attached.
- Enter a password for the jcimport user and ensure that it is set to Never Expire since this will be a service account for the Import Agent.
This password should still be rotated periodically for security reasons.
- Click Save.
Create the AD Sync Service Account in AD
After you identify the Root User Container (‘Root user DN’) that you want to use with your JumpCloud AD integration, create a new AD-based service account (standard user account) that allows the JumpCloud AD sync agent to manage users and groups.
- Open the ADUC Menu, click the Start button, type “dsa” and click the Active Directory Users and Computers icon.
- Find your Root User Container, right-click the container and click New > User.
This user cannot:
- Be a Domain Administrator.
- Have a username of “JumpCloud”.
- Be a member of the JumpCloud security group.
- Enter the following values for the JumpCloud Import Service Account user:
- First Name: JumpCloud
- Last Name: Sync
- User logon name: jcsync
Use jcsync to distinguish what this user is for and to which agent it is attached.
- Click Next
- Enter a password for the jcsync user and ensure that it is set to Never Expire since this will be a service account for the Sync Agent.
This password should still be rotated periodically for security reasons.
- Click Save.
Delegate Control for the AD Import and Sync Service Accounts in AD
If you will be using a Root user container DN other than the ‘Users’ default, you need to do these steps on that chosen container in your AD.
- Navigate to the Root User Container in ADUC that you have selected, right-click the container and select Delegate Control. This launches the Delegation of Control Wizard.
- Click Next.
- Add the newly created service account user to the Delegation of Control Wizard.
- Click Next, then select the following tasks:
- Create, delete, and manage user accounts.
- Reset user passwords and force password change at next logon.
- Read all user information.
- Create, delete, and manage groups.
- Modify the membership of a group.
- Click Next, then click Finish at the final screen.
- Right-click the Root User Container in ADUC again and select Delegate Control.
- Click Next.
- Add the JumpCloud Import Agent account to the Delegation of Control Wizard.
- Click Next, then select Read all user information.
- Click Next, then click Finish at the final screen.
Install the AD Import and Sync Agents
Create an ADI AD Domain in JumpCloud
Create a new ADI domain instance in JumpCloud if one does not already exist.
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to User Management > Active Directories.
- Click ( + Add ADI Domain ).
- Select Manage users and passwords in JumpCloud, AD or both.

- Enter the name of an Active Directory domain that you want to integrate with your JumpCloud tenant. For example, “DC=example;DC=com”.
The “DC” must be in capital letters. Each value must be separated with a semicolon (;) not a comma. There should be no spaces. The domain case must be the same as it is in the AD import configuration file.

- Click Save.
- If you want to use delegated authentication, select the checkbox for Delegated Password Validation.
- This option may be useful when importing existing users from AD to JumpCloud. It allows them to log in to the JumpCloud User Portal using their existing AD credentials for the first time.

Download the agents
- Click Download Import Agent.

- The Import Agent installer will automatically save to your local Downloads folder.
- Click Copy and save the import agent connect key to a password manager for later use.
- This is the unique one-time use key that is required to connect the Import Agent to your JumpCloud Org and this specific AD domain within JumpCloud. You will input this key during the AD Import Agent install in the steps below.
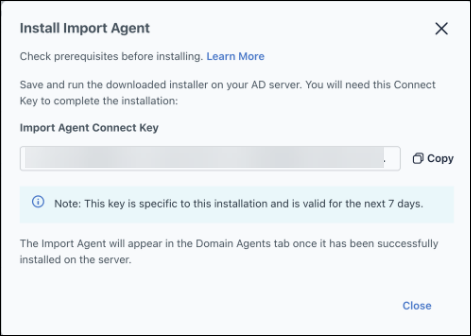
- Click Close.
- Click Download Sync Agent.
- The Sync Agent installer will automatically save to your local Downloads folder.
- The Install Sync Agent modal appears and you will be presented with the Sync Agent Connect Key. This is the unique one-time use key that is required to connect the Sync Agent to your JumpCloud Org and this AD domain Integration within JumpCloud. You will input this key during the AD Sync Agent install in the steps below.
- Click Copy and save the sync agent connect key to a password manager for later use.
Connect keys will expire in 7 days if it is not used.
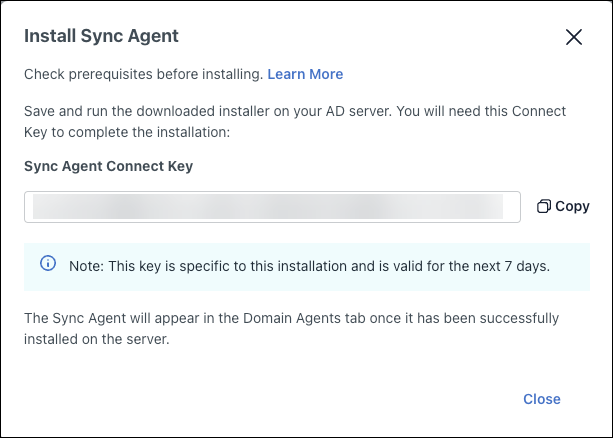
- Click Close.
- Save the downloaded installers to the AD servers.
Set Default External Password Authority
- Go to Users > Settings.
- Set Password Authority to "None (JumpCloud)".
- Click Save.
Install the AD Import Agent on Your AD Servers
When upgrading the import agent, you must use the same AD admin account used to initially install the import agent, or the import agent service won't start due to a credential error. If you don't know which account was used, you must re-enter the credentials in the registry after the upgrade and before the reboot.
- Navigate to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\JumpCloud\AD Integration Import Agent\ldap in the Registry Editor.
- Select bind_password
- Enter the JumpCloud ADI import account password
- Click OK
If you are installing the AD import agent on your DCs, the AD import agent must be installed on all of the write capable DCs within the domain. This does not apply to Read-Only DCs (RODCs).
If you are installing the AD import agent on non-DC domain member servers, we recommend installing on at least 2 servers.
Now you are ready to install the JumpCloud AD import agent.
- Browse to where you saved the AD Import installer file on the server.
- Right-click the file, then select Run as administrator.
- The Install Wizard will start and prompt you to agree to the C++ license terms and conditions.

- Select the type of server on which you are installing the AD import agent:

- If you selected Domain Controller, skip to step 9.
- If you selected Member Server for the server type, provide the FQDN or IP address for that server. We recommend using FQDN.



- Confirm your LDAP connection type and decide if you want to allow the use of LDAP if the connection using secure LDAP fails.

We STRONGLY recommend against allowing the use of LDAP if the connection using secure LDAP fails. LDAP is not secure and increases your potential risk of cyberattacks as it sends unencrypted data. Attackers can spy on the connection and intercept packets sent over the network. We STRONGLY recommend the use of LDAPS only when installing the agents on a member server.
If are installing the AD import agent on a member server and have not or cannot install LDAPS or TLS, you must select the "Allow insecure connection (LDAP) to a Domain Controller if secure connection fails"option. Otherwise, the integration will fail.
- If you checked Allow insecure connection (LDAP) to a Domain Controller, if secure connection fails, you must confirm that you understand the risk before you can proceed.

- Enter the jcimport account and password, then click Next. Be sure to use the NetBIOS domain format and not the full DNS name. (For example, example\jcimport and the user password).
If you’re unsure of the NetBIOS name, right-click the domain name in ADUC and select Properties. Use the value labeled Domain name (pre-Windows 2000).

- Enter the import agent connect key, then click Next.
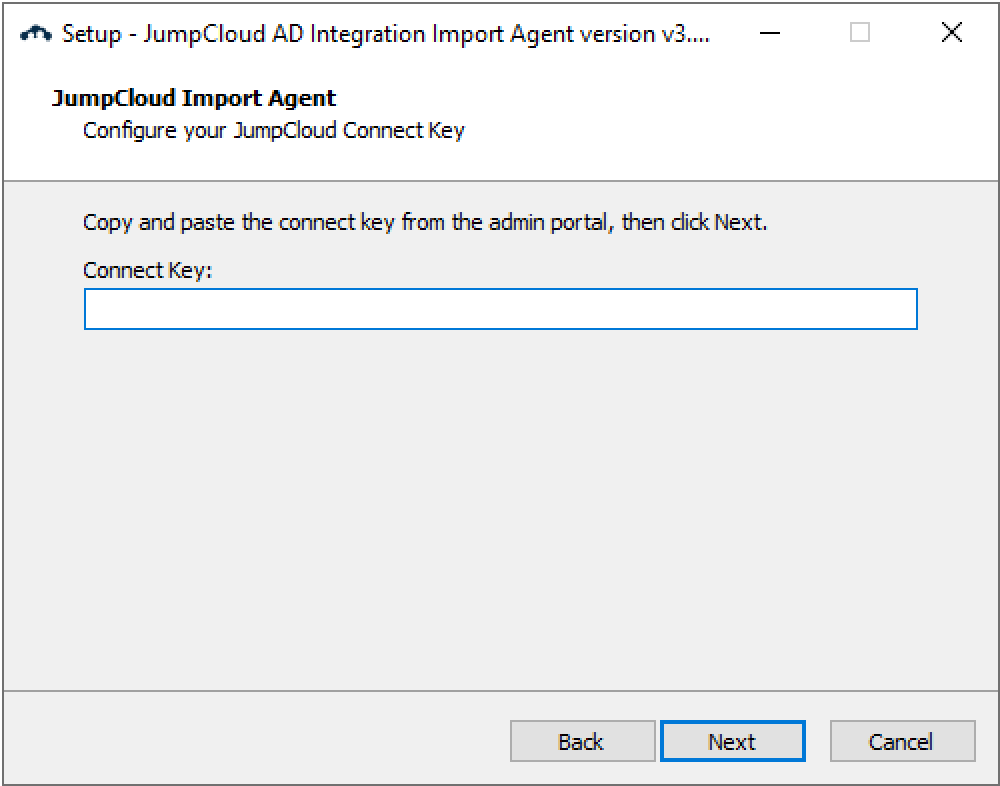
- Select your ADI deployment configuration
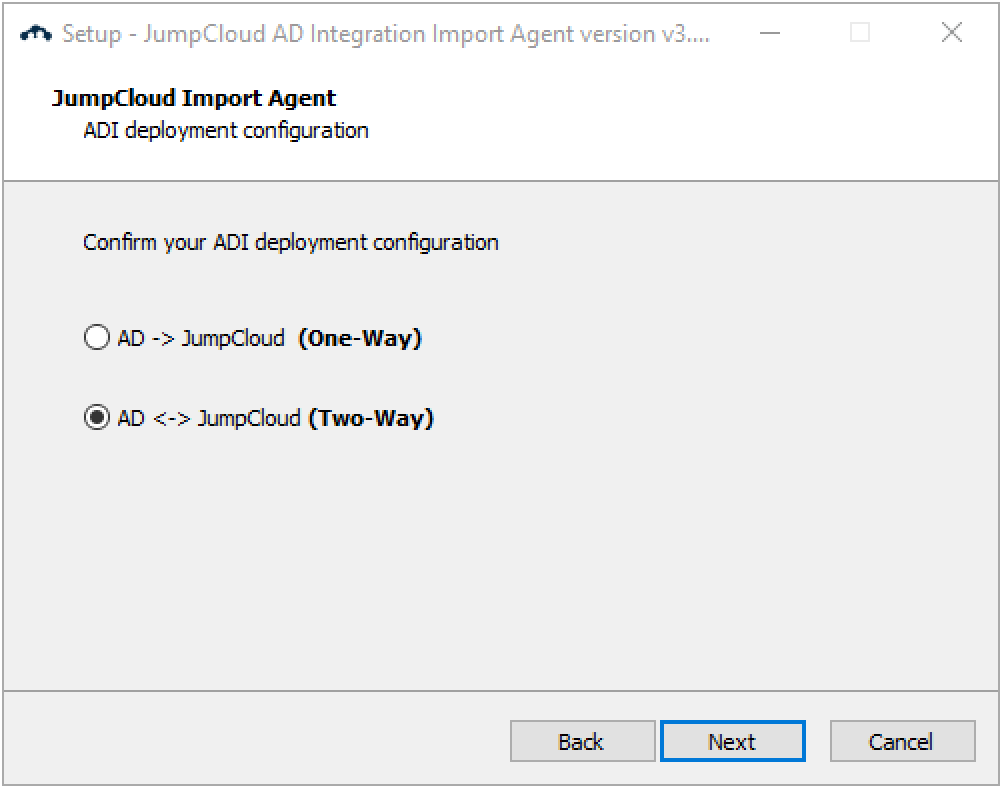
- Answer the question about whether you already have a sync agent installed
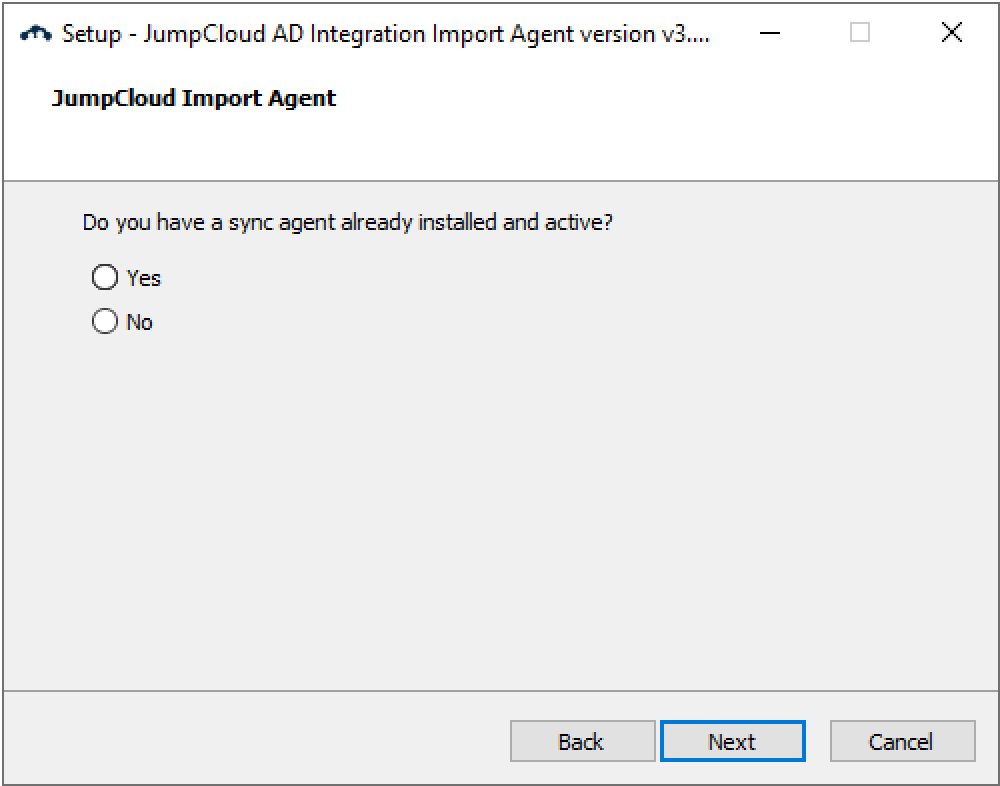
- Enter the security group DN
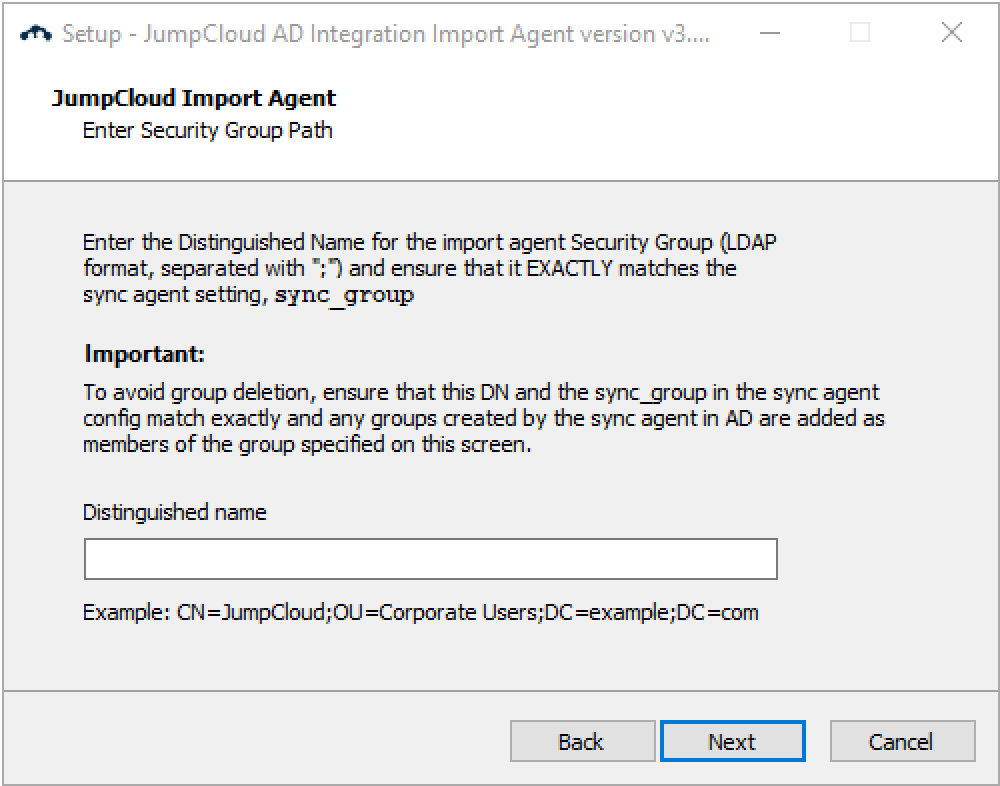
- If you answered yes to the question about having a sync agent installed
- If you answered no
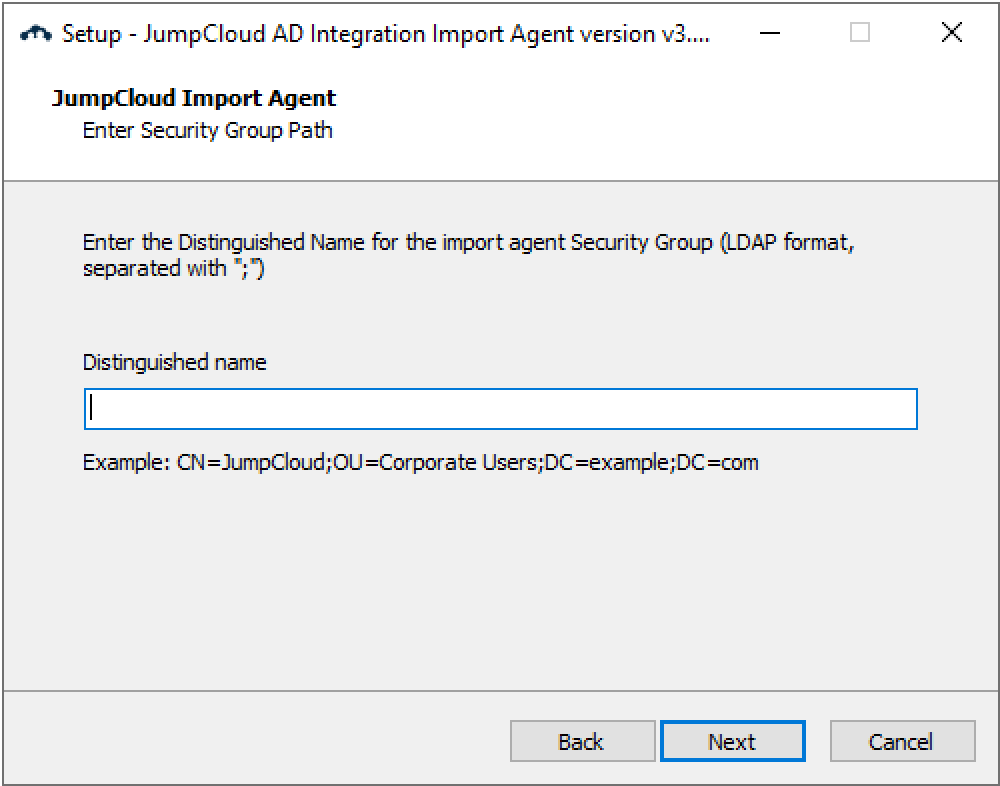
- Be sure to place semicolons ( ; ) between the values, e.g., “CN=JumpCloud;OU=Corporate Users;DC=example;DC=com”.
- The DN must be the same for both the AD import agent and AD sync agent.
- Select whether to sync the lock status from AD to JumpCloud. Choose "Yes, sync (true)" if you want to sync the lock status.
- If you answered yes to the question about having a sync agent installed, you will see
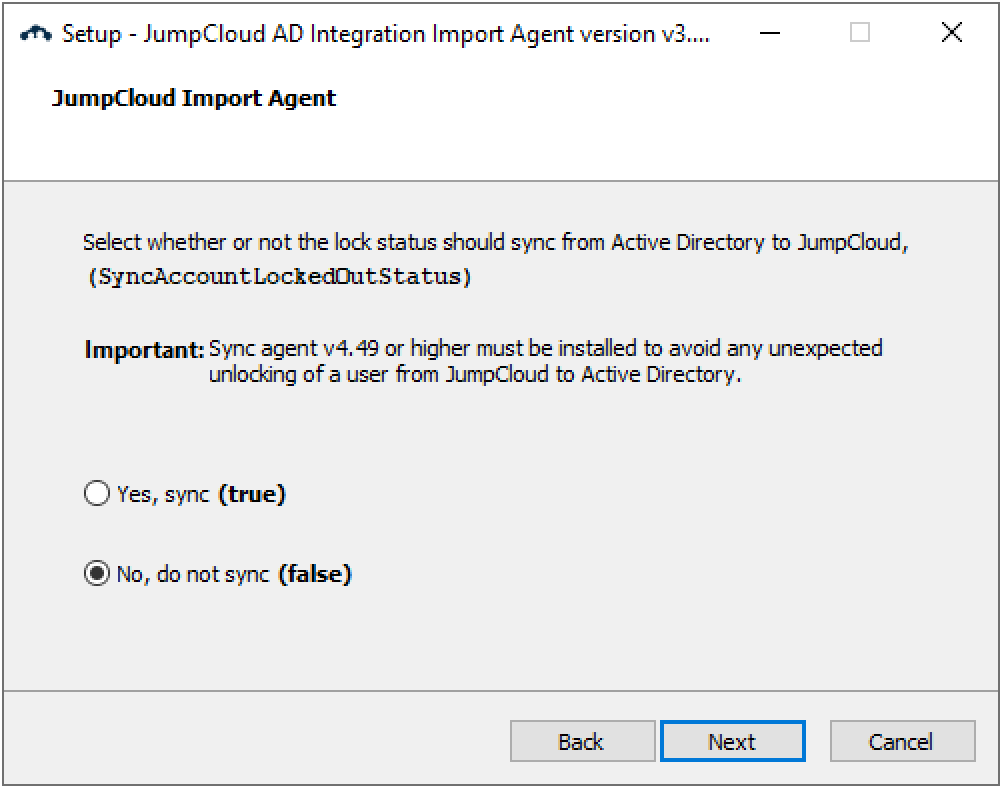
- If you answered no, you will see
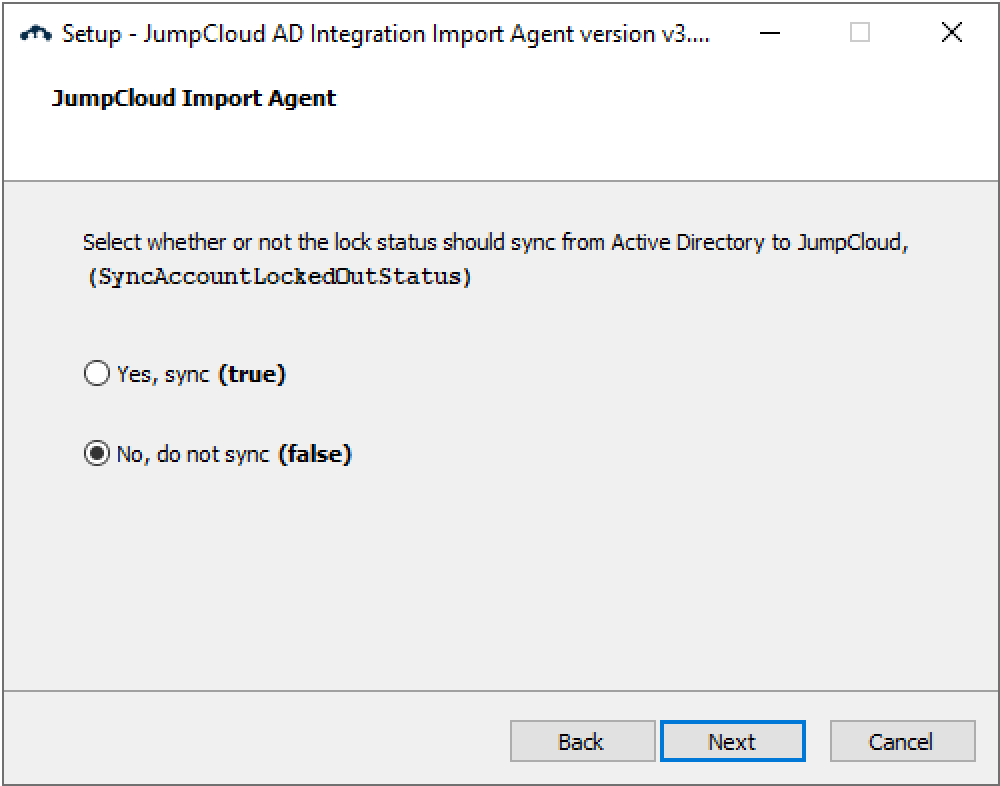
- Select whether your want to sync the additional attributes. Choose "Yes, sync (true)" if you want to sync the additional attributes.
- Select the installation directory

- Click Install. The import agent will take about 1 to 2 minutes to install.

- Select Yes, restart the computer now. If Google Workspace Password Sync (GSPS) is installed or further changes are needed, select No, I will restart the computer later.
- Click Finish.

You must reboot your AD servers to complete the AD Import Agent installation!
Adjust LSA Notification Packages for GSPS Compatibility
If Google Workspace Password Sync (GSPS) is installed on your AD server, you must adjust a registry setting to ensure its continued operation after the JumpCloud ADI import agent installation.
Incorrect registry modifications can lead to system instability. Proceed with care.
- Open Registry Editor:
- Press Win + R, type regedit, and press Enter.
- Navigate to LSA Key:
- Go to the following path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
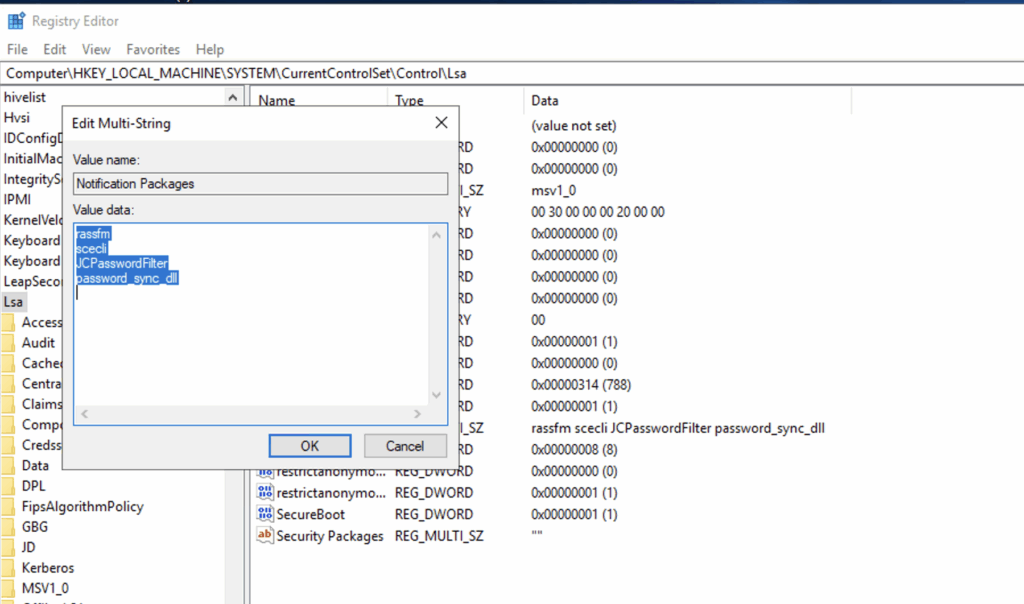
- Modify Notification Packages:
- In the right pane, double-click the Notification Packages value.
- Locate passwordsync_dll within the "Value data" box.
- Carefully cut passwordsync_dll from its current position and paste it at the very end of the list. Each item should remain on its own line.
- Click OK.
- Restart your AD server for the changes to take effect.
Verify the JumpCloud AD Import Agent Service Started After Reboot
Once your DC has restarted
- Open services.msc.
- Locate the "JumpCloud AD Integration Import Agent" service.
- Verify that its status is "Running". The service name is "JCADImportAgent".
If the service does not start, consult the agent logs for troubleshooting information at C:\Program Files\JumpCloud\AD Integration\JumpCloud_AD_Import.log.

Configure AD Import Agent
There are several configuration options that you should implement post-installation of the AD import agent. The recommended configuration updates are:
- Modify the UserTakeoverAction setting to retain.
- Modify the UserDisableAction setting to unbind
- Modify the UserDissociateAction setting to unbind
You can further customize the import process and define behaviors in JumpCloud based on actions in AD by adjusting other advanced configuration settings. See Advanced Configurations for Active Directory Integration for more information.
Modify the settings
- Search for a text file editor (e.g., Notepad)
- Right-click and select “Run as administrator”
- Select File>Open
- Navigate to the location of the jcadimportagent.config.json file (The default location is C:\Program Files\JumpCloud\AD Integration\JumpCloud AD Import)
- Select Open
- Change the UserTakeoverAction value to retain
- Change UserDisableAction value to unbind
- Change UserDissociateAction value to unbind
- Change any other settings to customize the import behaviors
Save the configuration changes and restart the AD import agent service
You do not need to restart the DC only restart the service to apply configuration changes.
Once all configuration changes have been made save them and restart the service.
- Save the jcadimportagent.config.json file.
- Restart the JumpCloud AD Import Agent service using the Windows Service Manager.
Install the ADI Sync Agent on Your AD Servers
When upgrading the sync agent, you must use the same AD admin account used to initially install the agent, or the sync agent service won't start due to a credential error. If you don't know which account was used, do the following:
- Select Yes to the "Would you like to review your existing configuration settings" prompt
- Select Next until you get to the LDAP Credentials screen
- Enter the agent account credentials
- Click Next
- You do not need to re-enter a Connect Key in this flow
If you are installing the AD sync agent on DCs, do not install the AD Sync Agent on Read-Only DCs (RODCs).
Now you are ready to install the JumpCloud Sync Agent on one or more member servers or your Primary DC and any DC within the domain that could experience replication delays.
- Browse to where you saved the AD Integration Sync installer file on your DC.
- Right-click the file, then select Run as administrator.
- Once the Installer Wizard appears, click Next.
- On the Destination Folder screen, click Next.
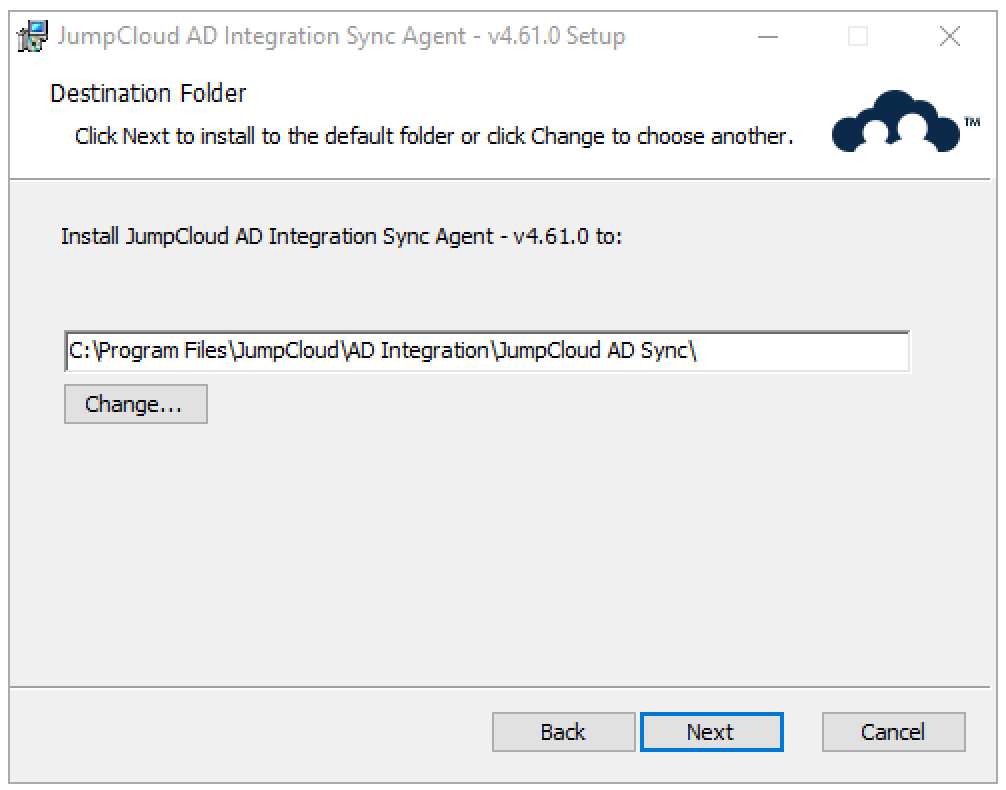
- Select the type of server on which you are installing the agent, DC or non-DC member server, then click Next.
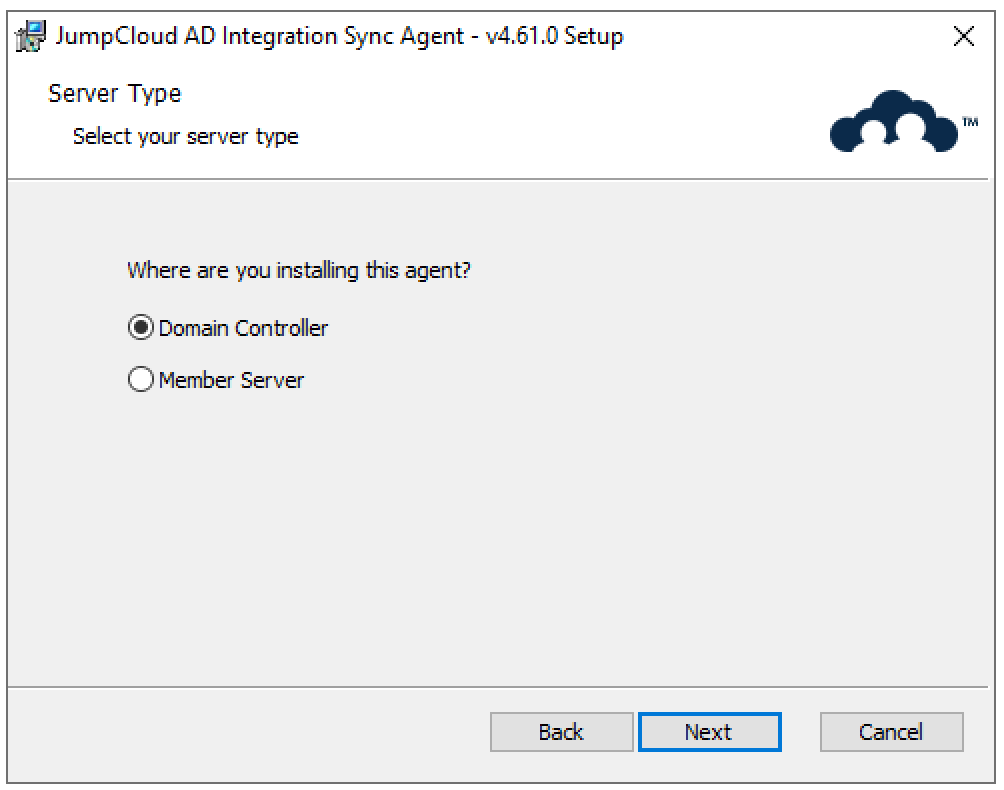
- If you chose Domain Controller, skip to step 10.
- If you chose Member Server as your server type, enter the information for the DC to which the member server should connect to sync data from JumpCloud to AD. We recommend using the FQDN for your DC.
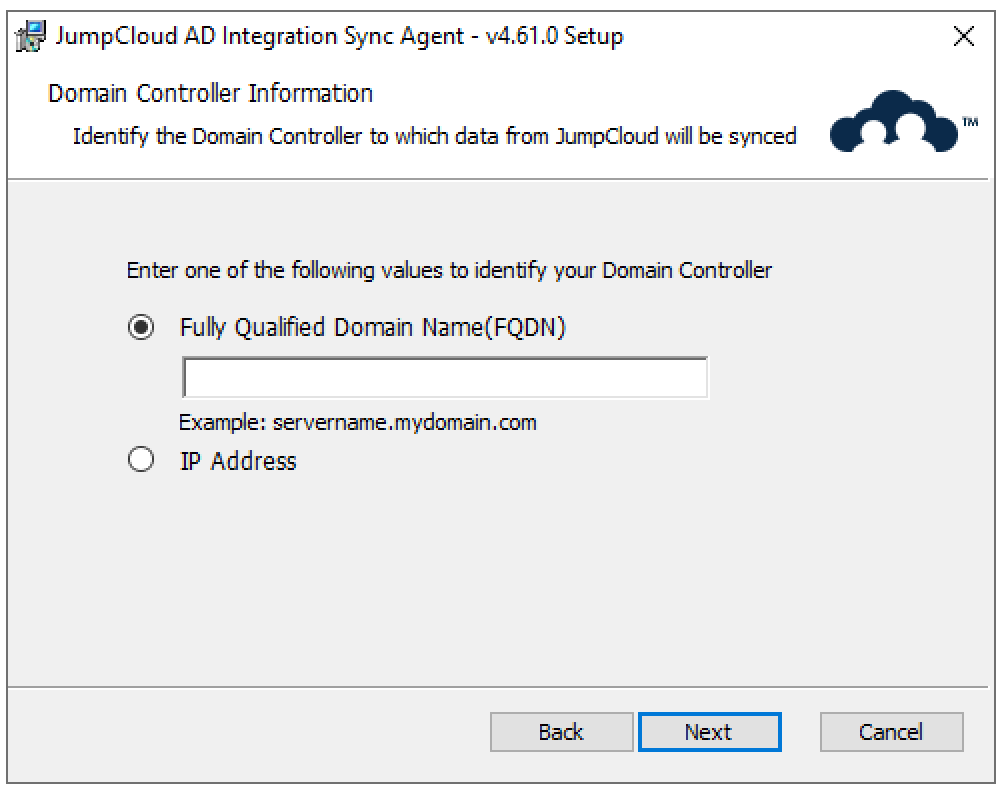
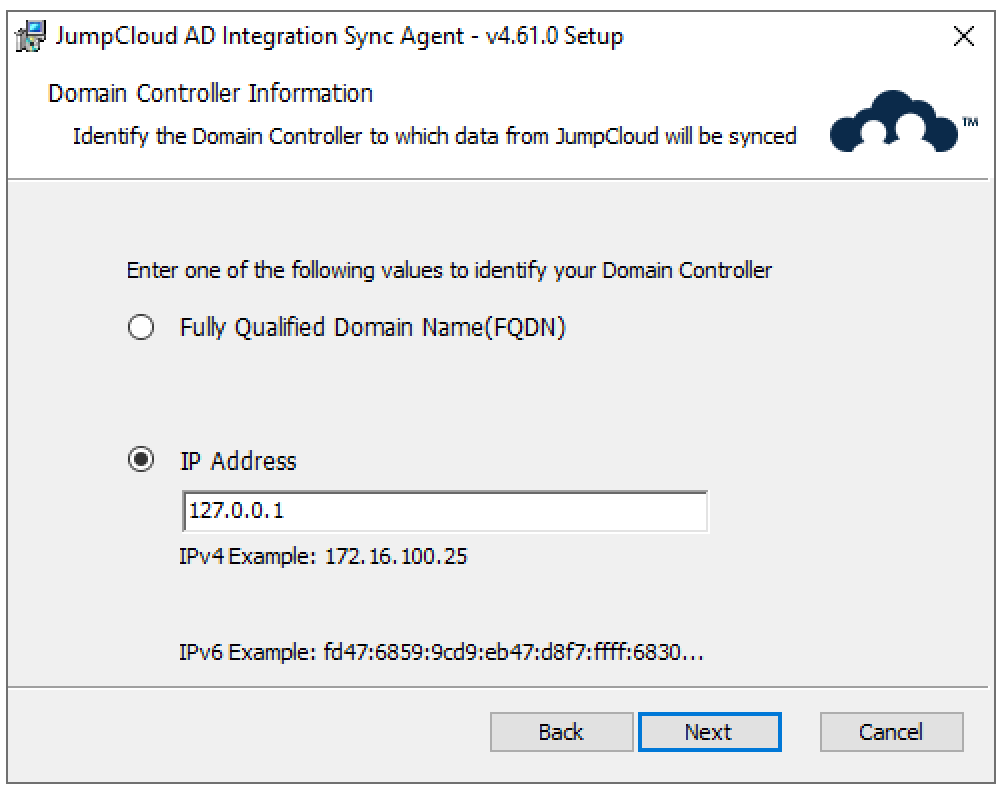
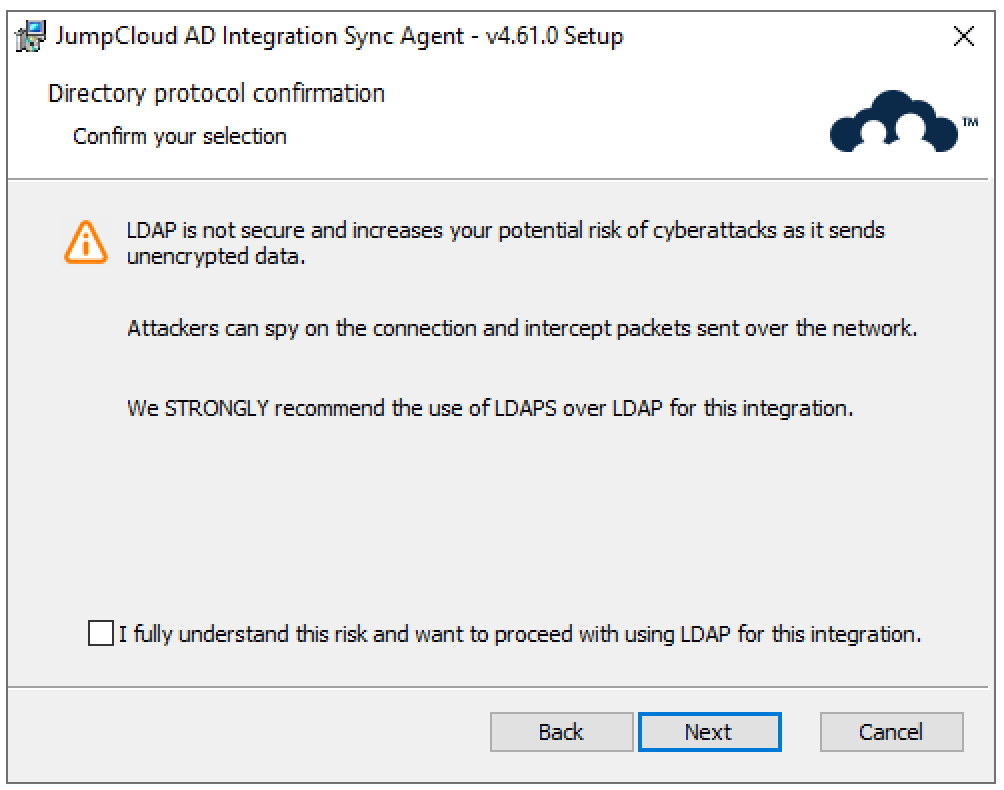
- Confirm your LDAP connection type and decide if you want to allow the use of LDAP if the connection using secure LDAP fails.
We STRONGLY recommend against allowing the use of LDAP if the connection using secure LDAP fails. LDAP is not secure and increases your potential risk of cyberattacks as it sends unencrypted data. Attackers can spy on the connection and intercept packets sent over the network.
We STRONGLY recommend the use of LDAPS only when installing the agents on a member server.
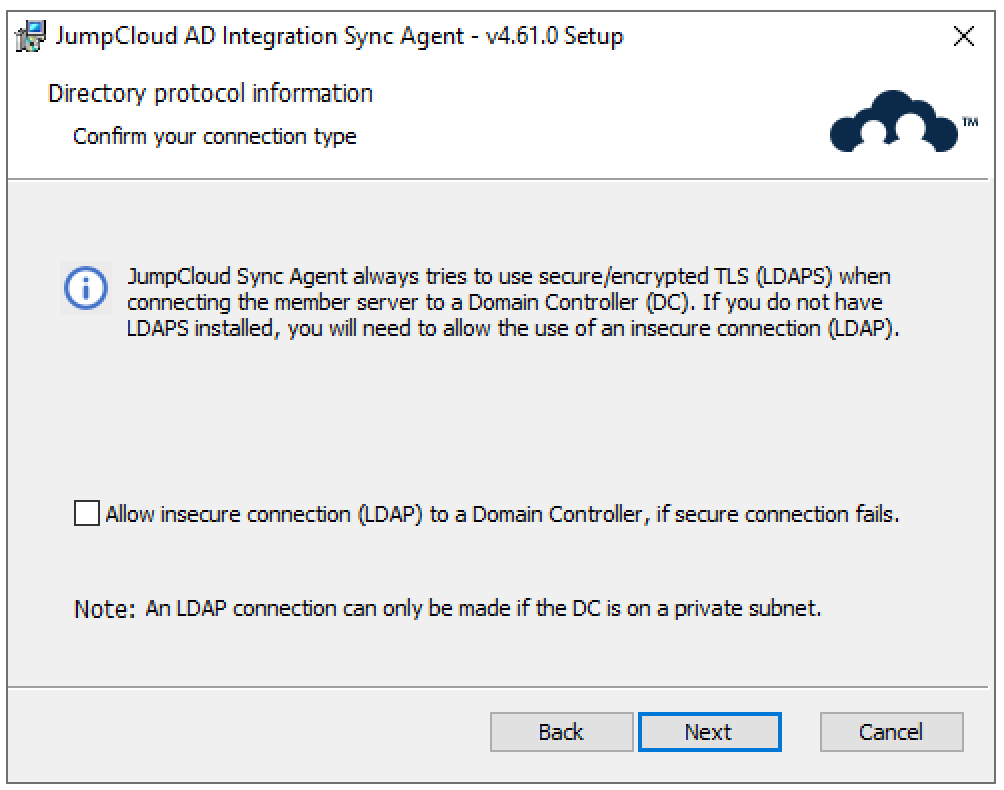
- If you checked Allow insecure connection (LDAP) to a Domain Controller, if secure connection fails, you must confirm that you understand the risk before you can proceed.
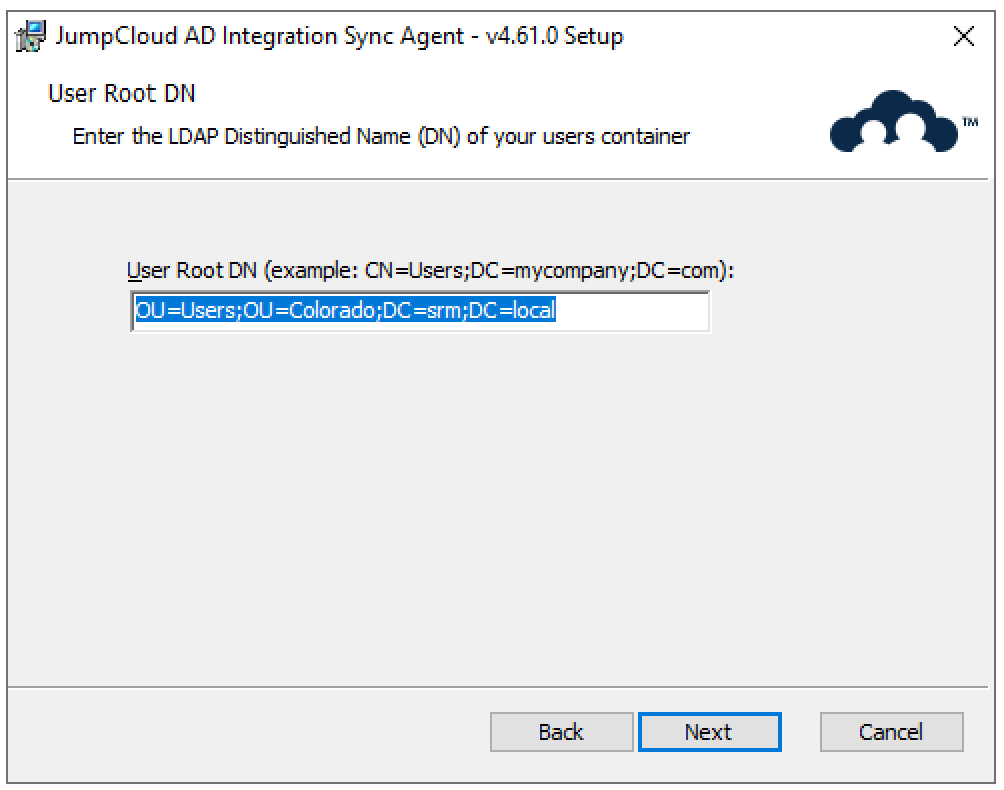
- Enter in the Root User Container you noted in the Determine the Root User Container in AD section above. If you’re using the default AD Root User Container, the value will be CN=Users;DC=company;DC=com. If you’ve chosen another Root User Container, enter the value you noted.
- In this example, we’ve modified the Root User Container. The value is: OU=Corporate Users;DC=example;DC=com
The AD Domain and Root User container DN needs to be the same for both the AD import agent and AD sync agent.
Case is important when entering the User Root DN, always use capital “OU”, “CN”, and “DC”.
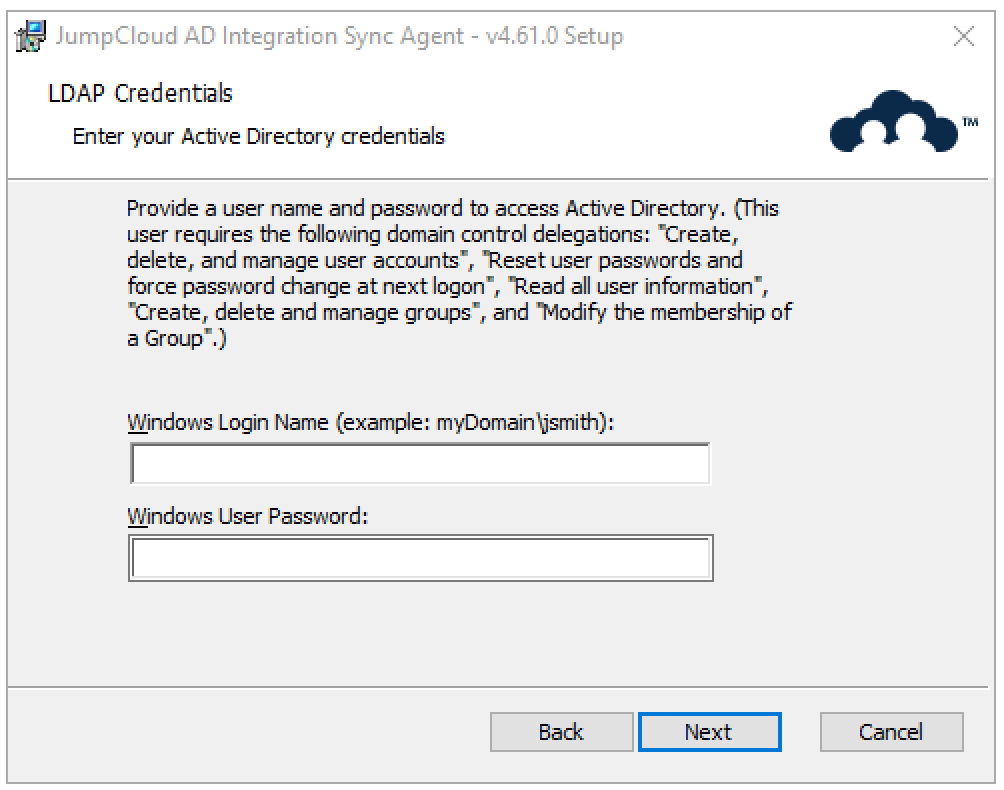
- Enter the AD Sync Agent’s Service Account you’ve created. This should be the jcsync User Account you created in the Create the AD Sync Service Account section above. Then click Next.
Case is important when entering the Windows Login Domain, use the same case that was used when creating the AD domain instance in JumpCloud.
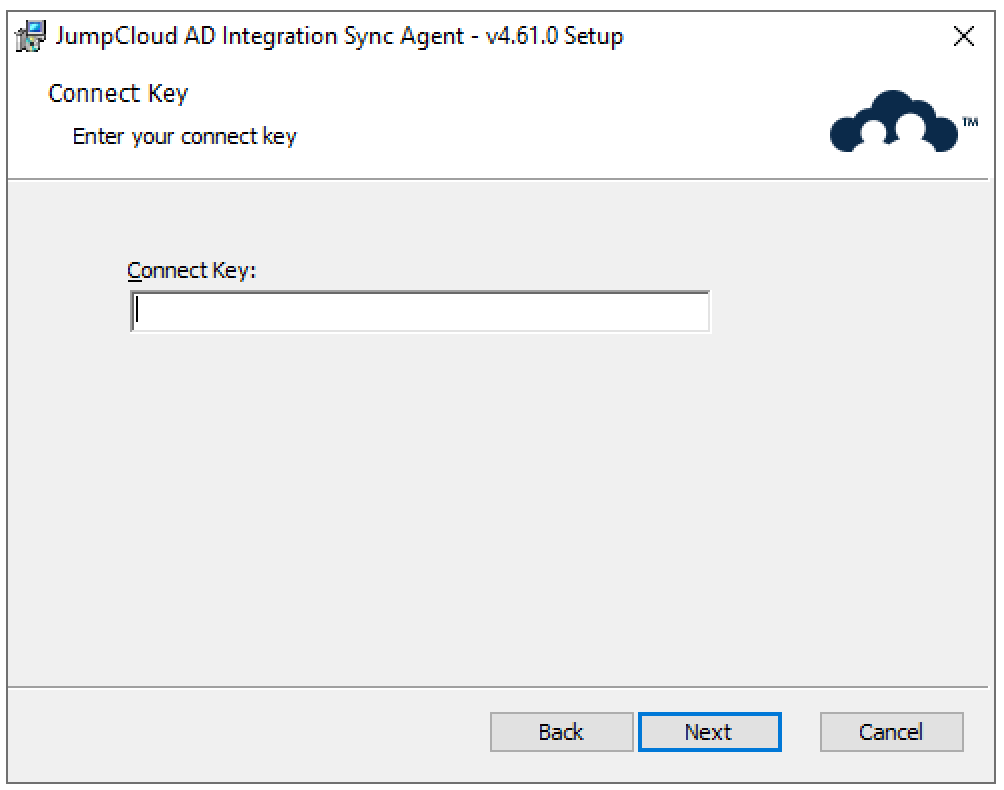
- Enter the Connect Key that was presented to you within the JumpCloud Admin Portal after downloading the AD Sync Agent. Then click Next.
The following steps allow you to select the sync agent's configuration settings, which will determine specific synchronization behaviors. Reference the Sync Agent section of Advanced Configurations for Active Directory Integration for details about each setting.
- Select your ADI deployment configuration
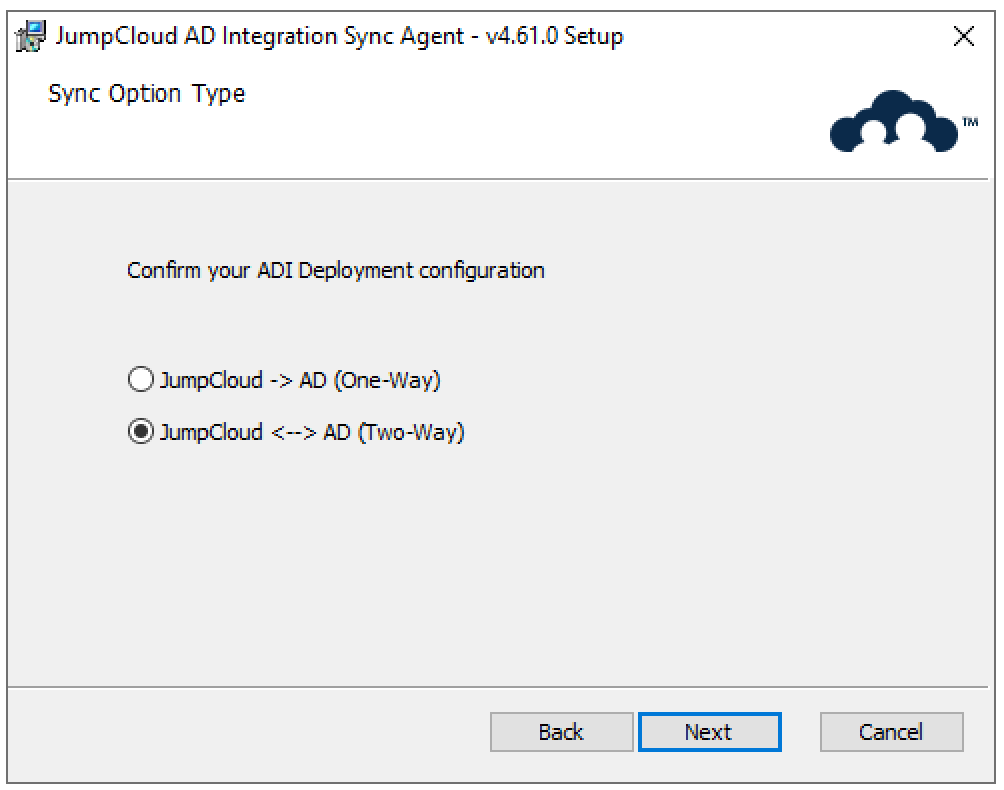
- Enter the Distinguished Name (DN) of an existing Active Directory security group (sync_group). This group will act as the parent for any new security groups that JumpCloud creates in AD, keeping them organized as sub-groups.
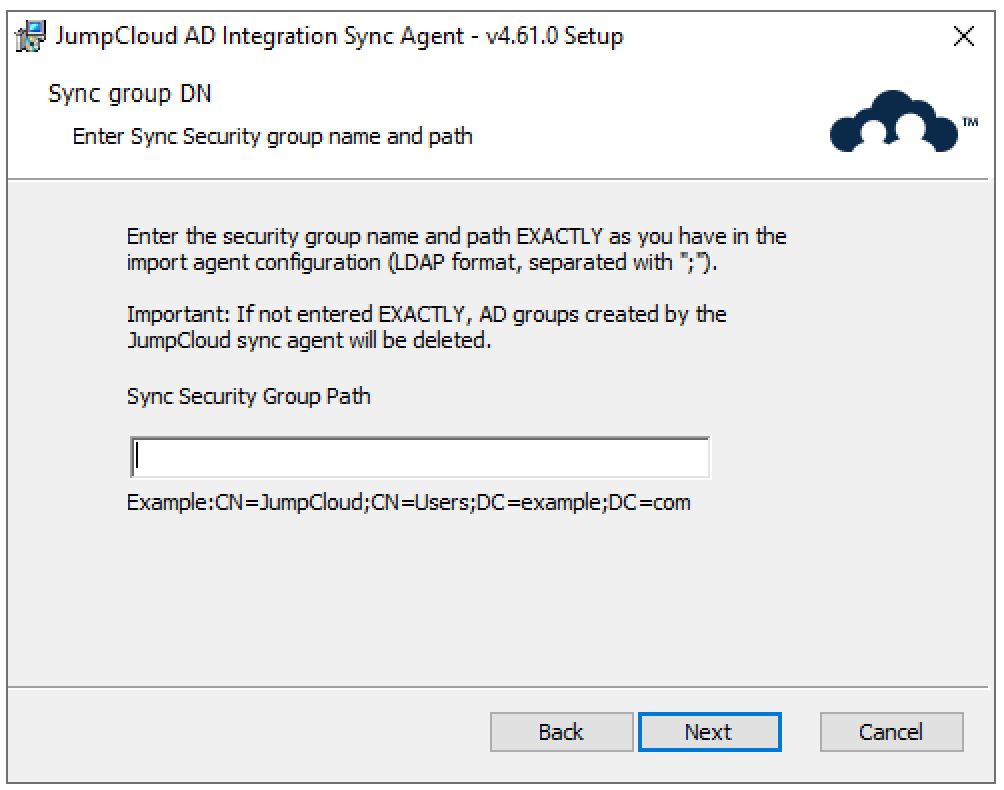
- Choose what happens to JumpCloud-managed Active Directory security groups if they are disconnected from ADI in the JumpCloud Admin Portal (group_disconnection_action).
- Remove: The security group is permanently deleted in AD.
- Retain (Default): The security group remains in AD, but JumpCloud will no longer manage it.
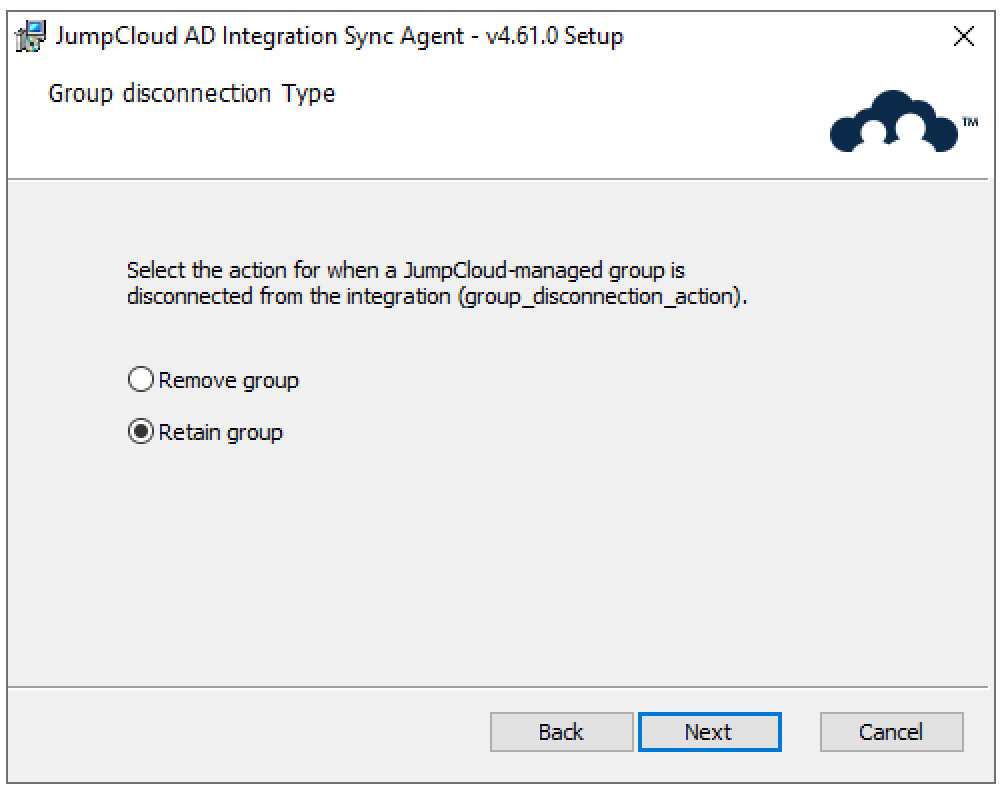
- Choose what happens to an AD user account when it's disconnected from JumpCloud's ADI (e.g., user deleted in JumpCloud while still connected to ADI or all connections removed); user_disconnection_action.
- Remove: The user's AD account is permanently deleted.
- Retain: The user's AD account remains active in AD.
- Disable (Default): The user's AD account is disabled in AD.
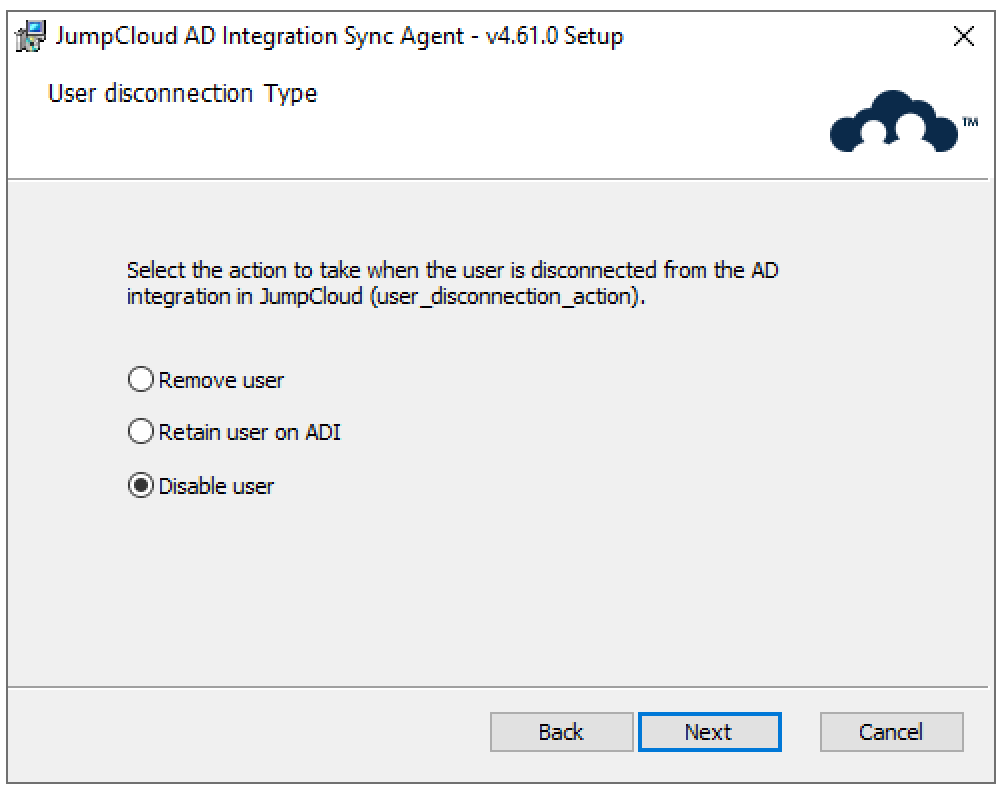
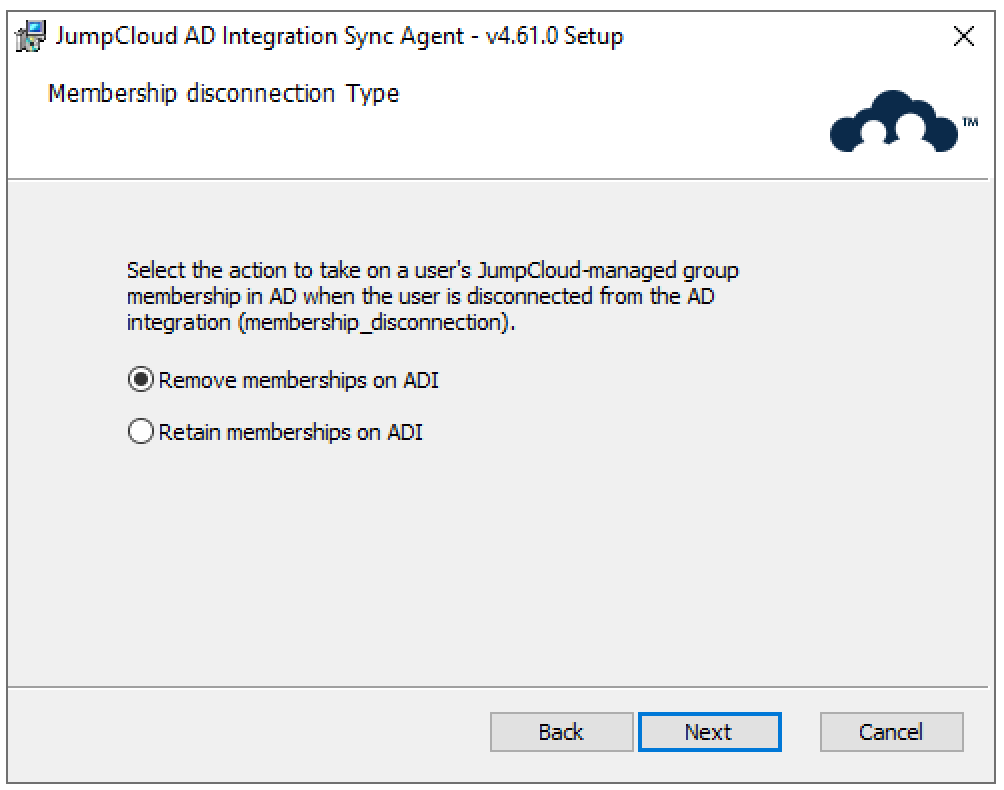
- Choose what happens to a user's memberships in JumpCloud-managed Active Directory security groups when that user is disconnected from ADI (membership_disconnection_action).
- Remove (Default): The user is removed from all JumpCloud-managed AD security groups.
- Retain: The user remains a member of these groups in AD.
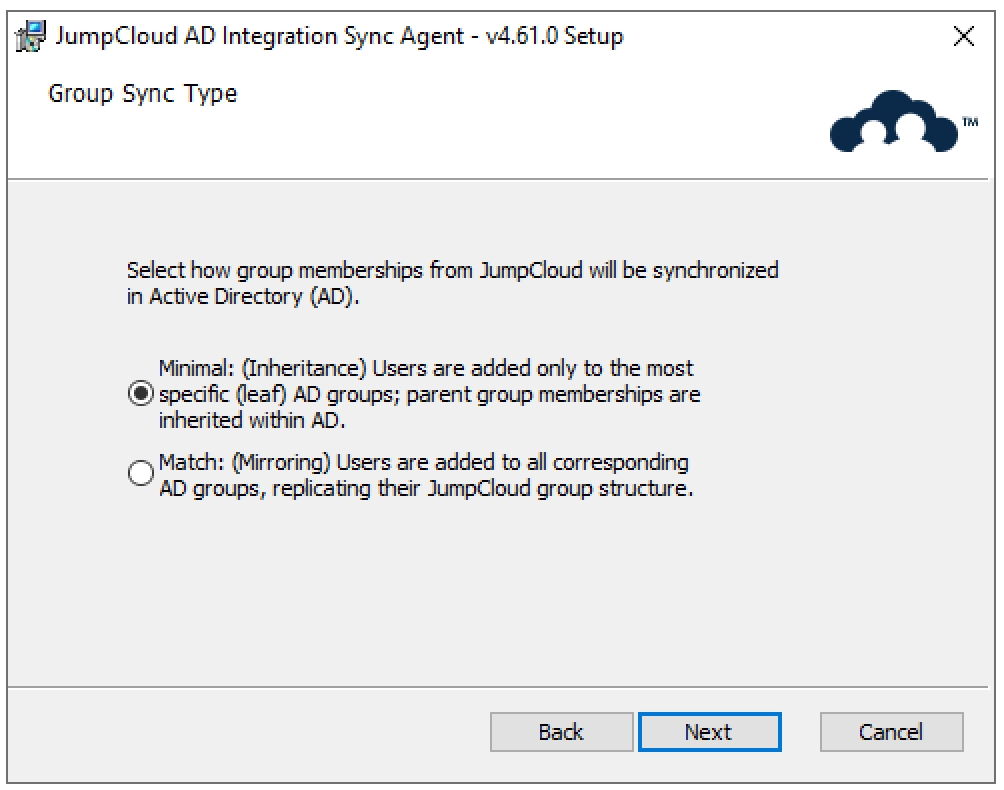
- Choose how JumpCloud manages a user's memberships within Active Directory's nested group structures (group_membership_sync_type).
- Minimal (Inheritance): Users are added only to the most specific (leaf) AD group; parent group memberships are then handled by AD's standard inheritance.
- Match (Mirroring): Users are added directly to all relevant AD groups in the nested structure, creating an exact match of their JumpCloud group memberships within AD.
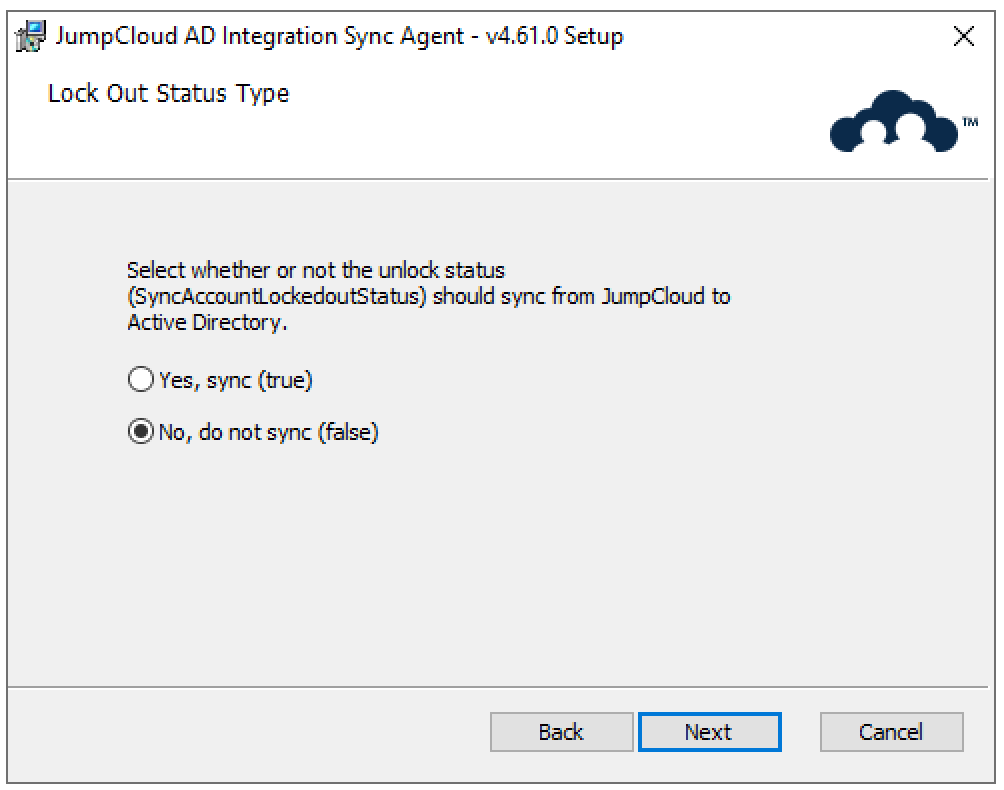
- Choose how JumpCloud controls unlocking a user's Active Directory account (SyncAccountLockedOutStatus).
- True: JumpCloud will unlock the AD account only if the JumpCloud account is specifically unlocked. (Recommended for precise control.)
- False (Default): The AD account may be unlocked by JumpCloud during any user attribute update.
- Finally, click the Install button to install the AD Sync Agent. This could take up to 3 minutes.
You DO NOT need to reboot the servers after the AD Sync Agent installation.
Congratulations! You’ve installed the AD Sync Agent. You are ready to verify that the AD Sync Agent is communicating properly.
Verify AD Import and AD Sync
Once you’ve installed the AD import and AD sync agents within your AD environment. You can easily verify that the JumpCloud AD Sync Agent is working. Please ensure the following are present and visible:
- The JumpCloud AD Sync Agent should be shown as green and active within the Admin Portal under User Management > Active Directories > Domain Integration > Domain Agents tab.
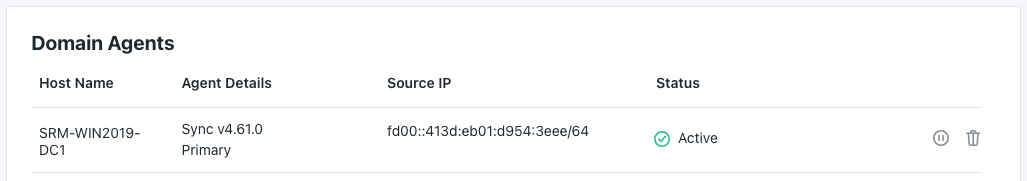
If the AD Sync Agent(s) or the AD Import Agent(s) are showing red or are in a non-connected state, please check services.msc to see if the services are running.
Additionally,
- JumpCloud User Group is now within your JumpCloud organization. The JumpCloud User Group should have a User Group icon with an AD badge in the User Group Details pane. See the example below:
- Navigate to User Management > User Groups. You should see the JumpCloud User Group with a Microsoft badge next to it. Click on the User Group to open up its details
- Navigate to User Management > User Groups. You should see the JumpCloud User Group with a Microsoft badge next to it. Click on the User Group to open up its details
- When the user group is opened, you can see that the User Group has a Microsoft Badge and is also assigned to AD on the Directories tab.

Next Steps
Please read the Using and Managing the ADI article next.
Want additional assistance from JumpCloud?
If you’re having issues with getting JumpCloud’s ADI working, try the Troubleshooting Guide. JumpCloud now offers myriad professional services offerings to assist customers with implementing and configuring JumpCloud. If you’re looking for assistance with Migrating from AD, or to integrate AD with JumpCloud, we recommend you reach out to JumpCloud’s Professional Services team on the following page: Professional Services - JumpCloud.








 Step 4
Step 4