Extending Active Directory (AD) to the Cloud is even simpler using the delegated authentication capabilities of the JumpCloud Active Directory Integration (ADI).
What is Delegated Authentication?
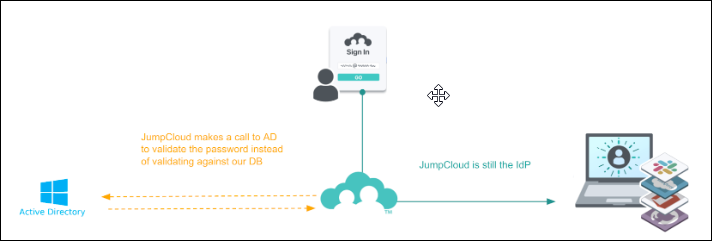
Delegated Authentication uses an external source, like AD, to verify a user’s password. Delegated authentication is different from federated user authentication in 2 key ways:
- JumpCloud is the Identity Provider (IdP). The external source is used for password validation only.
- The user is not redirected to the external source. Instead, they remain in the JumpCloud login flow and the verification is happening behind the scenes.
Why Delegate User Authentication to AD?
There are several use cases for which delegated user authentication is required or preferred:
- Easier integration deployment - Install the import agent on a small number of member servers not on all domain controllers (DCs) while still keeping and managing passwords only in AD.
- Compliance - Keep the password behind the AD firewall and still extend AD to the cloud using JumpCloud.
- Seamless onboarding of existing users to the Cloud - End users log in to JumpCloud for the first time using their existing corporate email address and AD password. No need to reset passwords.
- SSO without ADFS - Allow users to use a single secure identity to access their on-premise and Cloud resources without having to use Active Directory Federation Services (ADFS).
Important Considerations
- Delegated authentication to AD is supported by JumpCloud AD Import Agent v3.0 and higher and the import agent is installed on all AD Domain Controllers (DCs) or on AD member server(s).
- The ADI delegated authentication setting, Delegate Password Validation, must be enabled and active.
- When the delegated authentication setting, Delegated Password Validation, is enabled and Pending for the ADI configuration and the user's Delegated Authority is Active Directory, the user will not be able to log in. An AD import agent, version 3.0 or higher, must be installed and active to change the status of Delegated Password Validation from Pending to Active.
- All installed import agents should be the same version to avoid unexpected behavior or the potential for users not being able to log in if the primary agent is switched.
When upgrading the AD import agent to version 3.0, existing users connected to the domain will not have their log in delegated to AD unless the Delegated Authority is manually set to Active Directory for those existing users.
- User portal and SSO logins are delegated to AD when the following are true:
- The Delegate Password Validation setting is enabled and active for the ADI configuration.
- User has access to the delegation-enabled AD domain and their Delegated Authority is set to Active Directory on their user record.
- Users will NOT be able to log in if their Delegated Authority is Active Directory and the Delegate Password Validation setting is pending or disabled in the ADI configuration, all import agent(s) have been deleted, or the ADI integration has been deleted.
- Users will NOT be able to log in to the JumpCloud User Portal or SSO apps if they are connected (bound) to multiple delegation-enabled AD domains.
- Device password reset flow is delegated to AD when the following are true:
- The device is managed by JumpCloud.
- The Delegate Password Validation setting is enabled and active for the ADI configuration.
- User has access to the delegation-enabled AD domain, and their Delegated Authority is set to Active Directory on their user record.
- Self-Service Account Provisioning is enabled and Default Password Sync is disabled in Devices > Settings.
On devices with the configuration above, only the password used during the password reset flow is delegated to AD for validation. The user must set and use a local password or PIN for device logins. Their device login credentials will be managed separately.
- Existing AD users imported from AD to JumpCloud no longer have to reset their password in AD to log in to JumpCloud managed resources when delegation is enabled for them
- If the import agent is installed on DCs, the password is stored in JumpCloud after the initial log in. The stored password continues to be synced from AD to JumpCloud and from JumpCloud to other resources. The password can be used to log in to resources that don’t support delegated authentication to AD, such as Cloud RADIUS, Cloud LDAP, and devices.
- If the import agent is installed on AD member servers, the password is never stored in JumpCloud.
- Cloud RADIUS and Cloud LDAP resource logins cannot be delegated to AD. A user must have a password in JumpCloud to be able to access these resources.
- The Delegate Password Validation setting is enabled by default for the Manage users and passwords in Active Directory ADI configuration and cannot be disabled.
- The Delegate Password Validation setting is disabled by default but can be enabled for the Manage users and passwords in JumpCloud, AD or both configuration.
- When the JumpCloud AD import agent is installed on DCs, the AD passwords sync to JumpCloud. This means that the password will be saved in both AD and JumpCloud. This applies to both ADI configurations: Manage users and passwords in Active Directory and Manage users and passwords in JumpCloud, AD or both.
- When the JumpCloud AD import agent is installed on member servers, the AD password does not sync to JumpCloud.
- In the Manage users and passwords in Active Directory configuration, this means the password will only be in AD. In this configuration, the user's Password Authority should also be set to Active Directory to prevent a password from being entered in JumpCloud by either a JumpCloud Admin or the end user.
- In the Manage users and passwords in JumpCloud, AD or both configuration, this means users imported from AD will not have their AD password stored on their initial login to JumpCloud nor will the password sync from AD to JumpCloud. Any user connected to a delegation-enabled AD domain, ones created in AD and ones created in JumpCloud, with their Password Authority set to None (JumpCloud) can have a password set and managed in JumpCloud, and their password will be synced from JumpCloud to AD. This configuration is used when user passwords are managed in JumpCloud.
- Avoid users not being able to log in to JumpCloud managed resources when changing the delegated authentication settings.
Do the following before disabling the ADI delegated authentication setting, Delegate Password Validation, or disconnecting a user from a delegation-enabled AD domain in the JumpCloud Admin Portal:
- Verify the user's Password Authority is set to None (JumpCloud)
- Either send the user an activation email or set a password for the user from the user record in admin portal
- A warning modal is shown with options to either automatically update the Delegated Authority for every connected (bound) user or not when the following actions are taken:
- on save after delegated authentication is enabled or disabled in the ADI configuration.
- an ADI AD domain is deleted.
- a user is directly connected to (bound) or disconnected from (unbound) a delegation-enabled AD domain.
- a user is connected to (bound) or disconnected from (unbound) a user group connected (bound) to a delegation-enabled AD domain.
- when a user group is connected (bound) or disconnected (unbound) from a delegation-enabled AD domain.
- The Delegated Authority setting can be updated for multiple users at once from the Users page.
- A user login to the User Portal and for SSO is always delegated to AD, even if they have a password in JumpCloud, as long as all of following criterion are true:
- Delegated Authority is set to Active Directory.
- They are connected to a delegation-enabled AD domain.
- The status of the Delegate Password Validation setting in enabled and active for the AD domain.
- Delegated authentication can be enabled or disabled on a per user basis from the user details page even if they are not connected to a delegation-enabled AD domain.
- If an import agent is paused, delegated authentication will still occur. Only the import from AD to JC will be paused.
Configuration Steps Overview
To configure delegated authentication to AD, the main steps you will take are outlined below:
- Select your ADI deployment configuration:
- If not already selected, check the option for Delegated Password Validation.
- Download and install the latest JumpCloud AD Import Agent from the JumpCloud Admin Portal.
- Give users access to ADI.
Enable Delegated Authentication for a New AD Domain
The setting for delegated authentication on the ADI configuration is labeled Delegated Password Validation.
To enable delegated authentication for the Manage users and passwords in Active Directory configuration
- No action is required:
- Delegated Password Validation is enabled by default for this configuration and cannot be disabled.
All new users imported from AD to JumpCloud will automatically have their Delegated Authority set to Active Directory.
Users imported prior to the release of Import Agent v3.0 will continue to use the password stored in JumpCloud, unless the Delegated Authority is manually set to Active Directory. If the import agent is installed on a DC, the password will continue to sync to JumpCloud.
To enable delegated authentication for the Manage users and passwords in JumpCloud, AD or both configuration
- When creating a new AD domain in the JumpCloud Admin Portal:
- Check Delegated Password Validation checkbox in the Configuration Summary section of the Setup step.
- Download and install the Import and Sync agents.
- Click Configure ADI.
- Check Delegated Password Validation checkbox in the Configuration Summary section of the Setup step.
- When updating the configuration for an existing AD domain in the JumpCloud Admin Portal:
- Go to User Management > Active Directories.
- Click the domain to which you want to enable delegated password validation.
- Check Delegated Password Validation checkbox in the Integration Details section.
- Make other configuration changes, if needed.
- Click Save.
- Review the confirmation message.
- Select the update option.
- Click Continue.
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
- When adding an ADI for a new AD domain using the JumpCloud v2 API:
curl --request POST \
--url https://console.jumpcloud.com/api/v2/activedirectories \
--header 'content-type: application/json' \
--header 'x-api-key: REPLACE_KEY_VALUE' \
--header 'x-org-id: REPLACE_ORG_VALUE' \
--data '{"delegationState":"ENABLED","domain":"string","groupsEnabled":true,"useCase":"TWOWAYSYNC"}'
- When updating an existing ADI configuration using the JumpCloud v2 API:
Users may not be able to log in after this change is made. Changing the delegated authentication setting via the API does not automatically update the Delegated Authority for users connected to the ADI AD domain. You must update that setting manually for each connected (bound) user.
Replace {id} with the ID of your ADI instance.
curl --request PATCH \
--url https://console.jumpcloud.com/api/v2/activedirectories/{id} \
--header 'content-type: application/json' \
--header 'x-api-key: REPLACE_KEY_VALUE' \
--header 'x-org-id: REPLACE_ORG_VALUE' \
--data '{"delegationState":"ENABLED","domain":"string","groupsEnabled":true,"useCase":"TWOWAYSYNC"}'
Enable delegated authentication for users
These steps are intended for users who are already connected (bound) to a delegation-enabled AD domain but do not have their Delegated Authority set to Active Directory.
Users will NOT be able to log in to the JumpCloud User Portal or SSO apps if any of the following are true when their Delegation Authority is set to Active Directory:
- they are connected (bound) to multiple delegation-enabled AD domains.
- the status of the ADI delegated authentication setting, Delegated Password Validation, is NOT enabled and active.
- they are NOT connected to a delegation-enabled AD domain.
- all import agents that support delegation have been deleted.
Considerations
- Users must manage their passwords in AD once delegated authentication has been enabled.
Prerequisites
- Verify ADI delegated authentication setting, Delegated Password Validation, is enabled and active on the AD domain to which you will be connecting (binding) the user or to which the user is already connected (bound).
- Verify users are not already connected (bound) to a delegation-enabled AD domain.
- Verify users do not need access to JumpCloud LDAP integrations and JumpCloud Cloud RADIUS WiFi Networks.
- Remind users they will need to log in with their AD login credentials.
To enable delegated authentication for a single user in Admin Portal
- Log in to JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to User Management > Users.
- Click the user for whom you want to delegate password validation.
- Verify the user is connected to a delegation-enabled domain:
- Click the Directories tab and see if there is a check next to an ADI domain with the delegation enabled label (Delegation ENABLED).
- Select the User Groups tab.
- Expand each user group of which the user is a member (bound).
- Verify the group gives access to the delegation enabled AD domain.
- Click the Directories tab and see if there is a check next to an ADI domain with the delegation enabled label (Delegation ENABLED).
- Select the Details tab.
- Expand User Security Settings and Permissions.
- From the Delegated Authority dropdown, select Active Directory.
- Review the confirmation message.
- Click Update Setting.
- Click Save User.
To enable delegated authentication for multiple users in Admin Portal:
- In the JumpCloud portal, go to User Management > Users.
- Select the users for whom you want to delegate authentication to AD.
- Click the Actions dropdown menu.
- Click Set Delegated Authority.
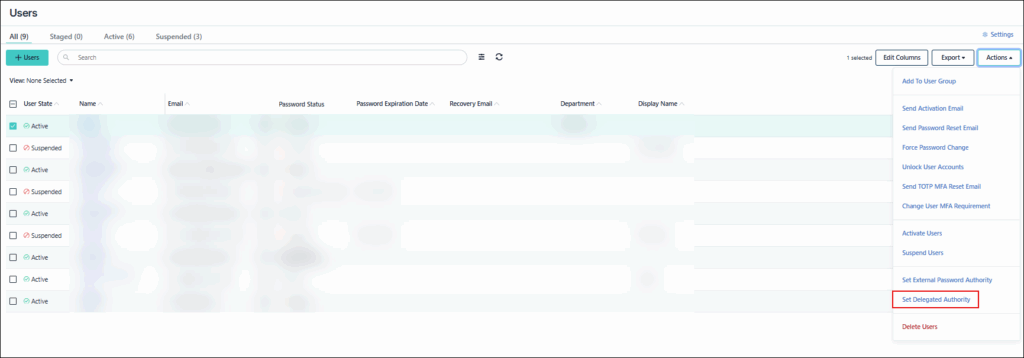
- Select Active Directory.
- Click Save.
To enable delegated authentication for a single user through the API:
- Generate an API key if you do not already have one.
- Example curl request:
curl --location --request PUT 'https://console.jumpcloud.com/api/systemusers/{UserID}' \
--header 'Accept: application/json' \
--header 'Content-Type: application/json' \
--header 'x-api-key: {API_KEY}' \
--data '{"delegatedAuthority":{"id": "string","name": "ActiveDirectory"}}'
- Example PowerShell request:
'https://console.jumpcloud.com/api/systemusers/{id}?fullValidationDetails=SOME_STRING_VALUE' -Method PUT -Headers $headers -ContentType 'application/json' -Body '{"delegatedAuthority":{"id": "string","name": "ActiveDirectory"}'
Replace {id} with the ID of your ADI instance.
To enable delegated authentication for multiple users through the API
- Generate an API key if you do not already have one.
- Example curl request:
curl --request PATCH \
--url 'https://console.jumpcloud.com/api/v2/bulk/users?suppressEmail=SOME_BOOLEAN_VALUE' \
--header 'content-type: application/json' \
--header 'x-api-key: REPLACE_KEY_VALUE' \
--header 'x-org-id: REPLACE_ORG_VALUE' \
--data '[{
"id":{ID},
"delegatedAuthority":{"id": "string","name": "ActiveDirectory"}
}]'
- Example PowerShell request:
'https://console.jumpcloud.com/api/systemusers/{id}?fullValidationDetails=SOME_STRING_VALUE' -Method PUT -Headers $headers -ContentType 'application/json' -Body '[{"id":{ID},"delegatedAuthority":{"id": "string","name": "ActiveDirectory"}}]'
Replace {id} with the ID of your ADI instance.
Grant Users Access to Delegation-enabled AD Domains
These steps are for giving users who are not already connected to a delegation-enabled AD domain access to that AD domain.
To grant user direct access to a delegation-enabled AD domain
From the ADI configuration:
- In the JumpCloud Admin Portal, go to User Management > Active Directories.
- Select your AD domain.
- Select the Users tab.
- Select the user(s) to whom you want to give access.
- Click Save.
- Read the warning message:
- Select the update option you prefer.
We recommend automatically updating the settings for the user.
- Click Continue
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
From the user details page:
- In the JumpCloud Admin portal, go to User Management > Users.
- Click the user for whom you want to enable delegated authentication.
- Select the Directories tab.
- Select the AD domain with delegation authentication enabled label (Delegation ENABLED).
Make sure only one AD domain with delegation enabled is selected. Otherwise, users won’t be able to log in.
- Click Save.
- Read the warning message.
- Select the update option you prefer.
We recommend automatically updating the settings for the user.
- Click Continue.
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
To give user access to a delegation-enabled AD domain through a user group
Dynamic Group Members
Users who gain access to the delegation-enabled AD domain via dynamic groups will need to have their Delegated Authority setting manually changed to Active Directory to enable delegated authentication.
Refer to the To give user direct access to a delegation-enabled AD domain section for the manual change instructions .
From the ADI configuration:
- In the JumpCloud Admin portal, go to User Management > Active Directories.
- Select your AD domain.
- Select the User Groups tab.
- Select the group(s) to which you want to give access.
- Click Save.
- Read the warning message.
- Select the update option you prefer.
We recommend automatically updating the settings for the user.
- Click Continue.
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
From the user groups detail page
- In the JumpCloud Admin portal, go to the User Management >User Groups.
- Select the user group to which you want to give access to your delegation-enabled AD domain.
- Select the Directories tab.
- Select the AD domain with delegation authentication enabled label (Delegation ENABLED).
Make sure only one AD domain with delegation enabled is selected. Otherwise, users won’t be able to log in.
- Click Save.
- Read the warning message.
- Select the update option you prefer.
We recommend automatically updating the settings for the user.
- Click Continue.
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
Remove User Access to Delegation-enabled AD Domains
To remove access for users with a direct connection to a delegation-enabled AD domain:
From the ADI configuration:
- In the JumpCloud Admin portal, go to User Management > Active Directories.
- Select your AD domain.
- Select the Users tab.
- Deselect the user(s) from whom you want to remove access.
- Click Save.
- Read the warning message.
- Select the update option you prefer.
We recommend automatically updating the settings for the user.
- Click Continue
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the number of users deselected.
From the user details page:
- In the JumpCloud admin portal, go to User Management > Users.
- Click the user for whom you want to disable delegated authentication
- Select the Directories tab.
- Deselect the AD domain with delegation authentication enabled label (Delegation ENABLED).
Make sure only one AD domain with delegation enabled is selected. Otherwise, users won’t be able to log in.
- Click Save.
- Read the warning message.
- Click Continue.
To remove access users connected to a delegation-enabled AD domain through a user group
From the User Groups tab of the User page:
- In the JumpCloud admin portal, go to User Management > Users.
- Click the user for whom you want to disable delegated authentication.
- Select the User Groups tab.
- Deselect the group that is connecting the user the delegation-enabled AD domain.
- Click Save.
- Read the warning message.
- Select the update option you prefer
We recommend automatically updating the settings for the user.
- Click Continue
If the group from which you removed the user is a dynamic group, you will be prompted to add the user to the exclude list for that group.
From the Users tab of the User Group page:
- In the JumpCloud admin portal, go to User Management > User Groups.
- Click the user group that is connecting the user the delegation-enabled AD domain.
- Select the Users tab.
- Deselect the user(s).
- Click Save.
- Read the warning message.
- Select the update option you prefer.
We recommend automatically updating the settings for the user.
- Click Continue
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
Dynamic Groups Consideration
If the group is a dynamic group and the user still meets the conditions for being a member of that group , you will need to add the user(s) to the exclude list.
To remove access for user groups connected to a delegation-enabled AD domain
For dynamic groups, users who no longer meet the conditions set on the group will automatically lose access to the delegation-enabled AD. You must manually set the Delegated Authority to None (JumpCloud) for these users.
Follow the instructions in section To remove access for users with direct access to a delegation-enabled AD domain for manually disabling delegated authentication to Active Directory for these users.
From the ADI configuration:
- In the JumpCloud admin portal, go to User Management > Active Directories.
- Select your AD domain.
- Select the User Groups tab.
- Deselect the group(s) from which you want to remove access.
- Click Save.
- Read the warning message.
- Select the update option you prefer.
We recommend automatically updating the settings for the user.
- Click Continue
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
From the user groups detail page:
- In the JumpCloud admin portal, go to User Management > User Groups.
- Select the user group to which you want to give access to your delegation-enabled AD domain.
- Select the Directories tab.
- Deselect the AD domain with delegation authentication enabled label (Delegation ENABLED).
- Click Save.
- Read the warning message.
- Select the update option you prefer.
We recommend automatically updating the settings for the user.
- Click Continue
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
Disabling Delegated Authentication for Users
These steps are intended for users who are already connected (bound) to a delegation-enabled AD domain and have their Delegated Authority set to Active Directory.
Considerations
- Users won’t be able to log in until a password has been set in JumpCloud
- If the import agent is installed on a DC, the users will have a password in JumpCloud. The AD password is synced in this configuration
- If the import agent is installed on an AD member server, the users will not have a password in JumpCloud. Passwords are not synced from AD to JumpCloud in this configuration
Prerequisites
- Notify users they will be getting a welcome email with a link to set their password in JumpCloud
To disable delegated authentication for a single user
- In the JumpCloud admin portal, go to User Management > Users.
- Click the users for whom you want to disable delegated authentication to AD.
- Select to None from the Delegated Authority dropdown menu.
- Review the confirmation message.
- Click Update Setting
- Click Save
To disable delegated authentication for a multiple users
- In the JumpCloud admin portal, go to User Management > Users.
- Select the users for whom you want to disable delegated authentication to AD.
- Click the Actions dropdown menu.
- Click Set Delegated Authority.

- Select None.
- Click Save.
Disable Delegated Authentication for a Domain
The setting for delegated authentication on the ADI configuration is labeled Delegated Password Validation.
Considerations
- Users won’t be able to log in until a password has been set in JumpCloud
- If the import agent is installed on a DC, the users will have a password in JumpCloud. The AD password is synced in this configuration.
- If the import agent is installed on an AD member server, the users will not have a password in JumpCloud. Passwords are not synced from AD to JumpCloud in this configuration.
Prerequisites
- Notify users they will be getting a welcome email with a link to set their password in JumpCloud
To disable delegated authentication for the Manage users and passwords in Active Directory configuration
Delegated Password Validation cannot be disabled for this configuration.
To disable delegated authentication for the Manage users and passwords in JumpCloud, AD or both configuration
- In the JumpCloud admin portal, go to User Management > Active Directories.
- Click the domain to which you want to enable delegated password validation.
- Uncheck Delegated Password Validation checkbox in the Integration Details section.
- Make other configuration changes, if needed.
- Click Save.
- Review the confirmation message and select the appropriate update option.
- Click Continue.
- If update users was selected, the changes are processing in the background. Processing time is dependent on the size of the group.
Auditing and Troubleshooting
Use Directory Insights to audit and troubleshoot changes and actions related to delegated authentication. See Troubleshoot: Active Directory Integration (ADI) for detailed troubleshooting guidance.
| Event | Description | Delegated Authentication Specific Information |
|---|---|---|
| user_login_attempt | Logs every time a user tries to log in to a JumpCloud managed resources | JSON includes a new field “password_delegated_authority” in the auth_context when the user’s login is delegated to AD for authentication |
|
"auth_context": { "auth_methods": { "password": { "success": true } }, "password_delegated_authority": "ActiveDirectory"
}, |
||
| association_change | Logs every time two resources are associated (bound) or disassociated (unbound). | Logged when a user is associated (bound) or disassociated (unbound) to a delegation-enabled AD domain. |
| Logged when a user group is associated (bound) or disassociated (unbound) to a delegation-enabled AD domain. | ||
| user_delegated_authority_update | Logs when a change is made to the Delegated Authority setting on the User record. | This event is specific to the delegated authentication functionality. |
| activedirectory_domain_delegated_password_change | Logs when the delegated authentication setting Delegated Password Validation in the ADI configuration is changed | This event is specific to the delegated authentication functionality. |
Next Steps
Haven’t installed the import agent yet?
Check out the step-by-step configuration guides
- Configure ADI: Manage users, security groups, and passwords in AD
- Configure ADI: Manage users, groups and passwords in either, or both, AD and JumpCloud
Ready to use ADI?
Read the Using and Managing the ADI article next.
Want additional assistance from JumpCloud?
If you’re having issues with getting JumpCloud’s ADI working, try the Troubleshooting Guide. JumpCloud now offers myriad professional services offerings to assist customers with implementing and configuring JumpCloud. If you’re looking for assistance with Migrating from AD, or to integrate AD with JumpCloud, we recommend you reach out to JumpCloud’s Professional Services team on the following page: Professional Services - JumpCloud.











