Updated on December 20, 2024
There’s a small universe of identity and authentication protocols/standards, each with its own benefits and differences. This article explores how SAML and OpenID Connect (OIDC) compare, the scenarios where either protocol would be beneficial for your organization, and how each contributes to identity and access management (IAM).
Each approach will enable single sign-on (SSO), but there are distinct technical and ideological differences to assess before you begin your project: SAML is more specialized toward securely granting website access across domains while OIDC provides additional context for mobile and web applications.
SAML vs. OpenID (OIDC)
An in depth comparison of these two protocols starts with a comparison between Security Assertion Markup Language (SAML 2.0) and OAuth (Open Authorization).
OAuth is the foundation for OIDC, but OIDC extends the former with an identity layer to authenticate your existing user accounts using a decentralized service that’s operated by the not-for-profit OpenID Foundation. The open-source community initiated OpenID’s development in 2005 with the objective that identities should be decentralized and not owned by a third party. There’s now over one billion OpenID-enabled user accounts from over 50,000 websites, according to the foundation. It’s the steward of the infrastructure that supports OIDC authentication, its community, and any legal or governance operations.
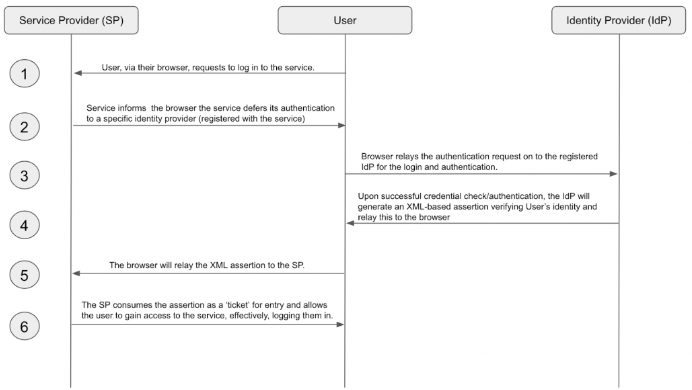
SAML 2.0, on the other hand, is an open standard that has provided authentication and authorization between commercial and private identity providers (IdP) and service providers (SP) since 2003. It began as a way to implement SSO using an XML-based framework to allow identity providers and services to exist separately from one another, with centralized user management. Let’s begin by examining how SAML works, exploring it component by component.
Similarities Between SAML and OIDC
When it comes to enabling single sign-on and streamlining authentication processes, both SAML and OIDC share common ground in terms of their core objectives. These frameworks serve as robust identity protocols that facilitate SSO, allowing users to authenticate via an identity provider and gain access to various applications that trust the IdP.
There are several similarities between SAML and OIDC that contribute to their widespread adoption and success:
- Both SAML and OIDC are secure, well-documented, and mature identity protocols that enable seamless SSO.
- These frameworks allow users to authenticate once with an IdP and access multiple connected applications without repeated logins, streamlining the user experience.
- This user-first design enhances usability and boosts productivity by reducing friction in the login process.
- While both protocols share similarities, they also have distinct nuances and advantages tailored to different organizational needs.
- Understanding these differences is key to making informed decisions that align with your organization’s requirements.
- In both frameworks, users authenticate through an IdP, which is trusted by other applications. Some Zero Trust models, however, may require re-authentication at various stages to continuously verify access.
- From the end user’s perspective, the login experience is nearly identical, as the technical distinctions occur entirely behind the scenes.
Differences Between SAML and OIDC
When it comes to identity and authentication protocols, it’s essential to understand the differences between SAML and OIDC. While both frameworks serve the purpose of user authentication, they have distinct characteristics that impact their implementation and functionality. For example:
- Many developers find OpenID Connect easier to implement due to the absence of XML handling.
- OpenID focuses primarily on identity assertion and lacks user authorization data, such as permissions. In contrast, SAML provides a more feature-rich approach to identity data exchange.
- OpenID uses a decentralized authentication model.
- SAML relies on assertions, while OpenID and OAuth utilize an ID token-based architecture.
- OIDC is specifically designed for API workloads, making it an effective solution for securing APIs.
SAML Use Cases
SAML plays a pivotal role in enabling secure and seamless authentication across various scenarios. Here are three key use cases:
Enterprise Single Sign-On for Legacy Applications
SAML is a cornerstone for implementing SSO in enterprise settings, allowing users to log in once and access multiple legacy or browser-based applications without repeated authentication prompts. For example, an employee logs in through an identity provider (e.g., Microsoft Active Directory Federation Services) and gains effortless access to tools like SharePoint, Salesforce, or SAP.
SAML, being an open standard, makes it easy to provide authentication (and authorization, if required) to facilitate SSO access to web applications through identity federation. SAML relays user credentials from an IdP that owns and maintains identities to verify access rights and SPs. Service providers require authentication prior to granting users access to the resource. Each user (or group) has attributes that outline profile information and assert what exactly they’re authorized to access.
Federated Identity Management for B2B and B2C
SAML enables federated identity management, allowing organizations to rely on trusted third-party identity providers for efficient and secure authentication. For example, a vendor’s employees can use their own organization’s credentials to securely access your company’s applications, such as a supplier portal, without the need for separate login credentials.
SAML uses extensible markup language (XML) metadata documents (SAML tokens) for an assertion process to verify a user’s identity and access privileges.
Secure Authentication in Regulated Industries
Industries with strict compliance requirements, such as finance, healthcare, or government, rely on SAML for standardized and robust authentication. For example, a healthcare provider uses a centralized identity provider to authenticate staff accessing electronic medical records (EMR) systems, ensuring compliance with regulations like HIPAA.
Developers use SAML plugins within apps or resources for an SSO login experience that assures security practices are being followed and credentials/assertions determine who can access an application. Additionally, SAML can be used to control what resources an identity can access in an application.
OIDC Use Cases
OIDC’s strengths lie in modern application development, API security, and cloud-native environments. Here are three use cases for how OIDC is often used:
Authentication for Modern Web and Mobile Applications
OIDC is widely used to authenticate users in web and mobile applications, especially in cloud-native environments. It integrates easily with OAuth 2.0 to provide a seamless and secure user experience. For example, users log in to a mobile app or a modern web app (e.g., a social media app or online shopping platform) using their Google or Facebook credentials via OIDC.
API Authentication and Authorization in Microservices Architectures
OIDC is commonly used for authentication and authorization in API-driven, microservices-based environments, where services need to verify user identity and authorize access to resources. For example, a user accesses a service that calls multiple microservices (e.g., order processing, payment gateways) using an OIDC token to authenticate and authorize each service call.
Single Sign-On for Cloud Applications
OIDC is ideal for cloud-based SSO, where users authenticate once and gain access to multiple cloud applications, particularly in SaaS (Software-as-a-Service) environments. Users authenticate through an identity provider (e.g., Azure AD or Okta) to access a suite of cloud applications like Office 365, Salesforce, and Slack.
How SAML Works
SAML is an open standard for authentication (and optionally authorization) that enables SSO access to web applications through identity federation. It relays user credentials from an IdP to verify access rights with SPs, which require authentication before granting access. Each user (or group) has attributes that define their profile and access permissions.
SAML uses XML metadata documents (SAML tokens) to assert and verify a user’s identity and access rights. Developers integrate SAML plugins into apps or resources to provide secure SSO login experiences, ensuring credentials determine who can access an application. It can also restrict what resources a user can access within an app.
SAML relies on key components like the IdP, client, attributes, and SP to exchange user information and manage access control.
Identity Provider (IdP)
An IdP is a service that maintains and manages digital identities to verify user credentials throughout applications, networks, and web services. Its primary role is to safeguard the integrity of user credentials and federate user identity where SSO logins are desired.
Client
Clients are your users who will authenticate into a service using the credentials that are being managed by an IdP. For example, your employer may use SAML for SSO access into the services that you need to work, using your company email address and password.
Attribute
SAML transfers messages, called assertions, from an IdP to a service provider. These assertions set all relevant security requirements for the transaction by authenticating, authorizing, and determining the level of permissions a client will receive. Attributes such as “dept,” “email,” and “role,” are used to enforce access management and access control. Sometimes, custom attributes are used so that SAML can be extended for use with custom software.
Service Provider (SP)
Service providers are a resource that users authenticate into using SAML SSO, usually a private website or application. They receive, accept, or deny assertions from IdPs for each client profile prior to granting users access. SPs send requests to IdPs to begin the authentication process, and the client’s assertion is received in response. The process is sometimes reversed when an IdP initiates the sign-in flow to assert user identity. It can be initiated either way.
How OIDC Works
OIDC extends the OAuth protocol so that client services (your applications) verify user identities and exchange profile information through OpenID providers via RESTful APIs that dispatch JSON web tokens (JWTs) to share information during the authentication process. The providers are essentially authentication servers.
Many developers are attracted to this approach because it’s highly scalable, flexible across platforms, and is relatively simple to implement. Its main components are a unique user ID workflow with OAuth underpinnings.

OpenID Architecture and Components
OpenID Connect (OIDC) is built on top of the OAuth 2.0 protocol and uses a set of key components to facilitate secure authentication. The primary components in OIDC include:
- End-User (the user trying to authenticate)
- Client (the application requesting authentication)
- Authorization Server (the IdP responsible for authentication)
- Resource Server (where the user’s data resides)
OIDC introduces the ID Token, a JWT (JSON web token) containing user identity information, which is issued by the Authorization Server. It also relies on access tokens for securing API access and refresh tokens to maintain long-term sessions.
OpenID Authentication Flow
OIDC follows a structured authentication flow that starts when the client application redirects the end user to the Authorization Server’s login page. These steps include:
- The user authenticates via the IdP, which then sends an Authorization Code back to the client.
- The client exchanges this code for an ID Token and an Access Token by making a request to the Authorization Server’s token endpoint.
- The ID Token provides the client with user identity information (e.g., name, email), while the Access Token is used to access protected resources.
This flow ensures that user authentication is secure and that the client can safely obtain user information without exposing sensitive credentials.
Choosing Between SAML and OpenID
Criteria for Decision Making
When choosing between SAML and OpenID Connect, consider factors like the type of application, security requirements, and system architecture.
SAML is a good choice for legacy, enterprise environments requiring robust security for web-based SSO and where XML-based communication is preferred. It’s ideal for large-scale, centralized authentication in corporate settings.
On the other hand, OIDC is better suited for modern applications, particularly in mobile and cloud-native environments. It’s easier to implement, with RESTful APIs and JSON, and integrates well with OAuth 2.0 for fine-grained access control. For organizations needing lightweight, scalable solutions with support for distributed systems, OIDC may be the preferred option.
Best Use Cases for SAML
SAML excels in enterprise environments where legacy applications require secure web-based SSO, often in large-scale, centralized setups.
It is particularly well-suited for regulated industries where strict compliance and audit requirements exist, such as healthcare, finance, and government. Examples include enterprise applications like SharePoint, Salesforce, and SAP, where secure user authentication across multiple internal systems is essential.
SAML also works well for federated identity management in B2B or B2C scenarios.
Best Use Cases for OpenID
OpenID Connect is ideal for modern, web-based, and mobile applications, especially in cloud-native and microservices environments.
It is the preferred choice when integrating with third-party identity providers like Google, Facebook, or GitHub for user authentication. OIDC works seamlessly for applications requiring fast, scalable authentication, such as SaaS applications (e.g., Slack, Salesforce, Dropbox). Additionally, it’s highly effective in API-driven environments, where microservices need secure and lightweight user authentication via tokens.
Using OIDC and SAML Together
These protocols aren’t mutually exclusive. Consider using SAML for enterprise SSO to secure access to your organization’s resources and OIDC for mobile use cases that have high scalability requirements.
When considering these technologies, you may ask yourself:
Is SAML More Secure Than OpenID Connect?
SAML and OpenID Connect are both secure, but SAML provides stronger built-in security for legacy systems, like encryption and digital signatures. OpenID Connect, based on OAuth 2.0, is lighter and better suited for modern, API-driven environments with token-based security.
Is SAML 2.0 Outdated?
No, SAML 2.0 remains widely used in enterprise and legacy systems. While newer protocols like OpenID Connect are preferred for cloud and mobile apps, SAML continues to serve organizations with established infrastructure and strict security requirements.
What’s the Difference Between SAML and OAuth?
SAML is an authentication protocol, while OAuth is an authorization framework. SAML is typically used for web-based SSO, while OAuth allows secure access to resources without exposing user credentials. OpenID Connect extends OAuth to include authentication features.
Learn More
If you’d like to learn more about how to combine the best of both worlds, using SAML and OIDC, please contact us. The JumpCloud platform utilizes user attributes to make smart group membership suggestions, and much more. You can also explore what JumpCloud has to offer by scheduling a free personalized demo.




