Single Sign-On (SSO)
Secure access to all your organizational resources, from anywhere, through one, unified identity.
One Secure Identity to Access Any Resource
The more sets of credentials employees have to manage and remember for different resources, the more at-risk your organization is. With JumpCloud, implement and enforce SSO and multi-factor authentication (MFA) across all SAML and OIDC-based applications to ensure access security while simplifying the login process.
Secure Resource Access
JumpCloud SSO grants users a single, secure set of credentials to access their IT resources. Pair with JumpCloud Go™ for a hardware-protected and phishing-resistant passwordless login method for users to access web resources from managed devices.
How We Compare
| JumpCloud vs. OktaBlog Post
| How Single Sign-On (SSO) Authentication WorksSupport Article
| Started: SSO Applications
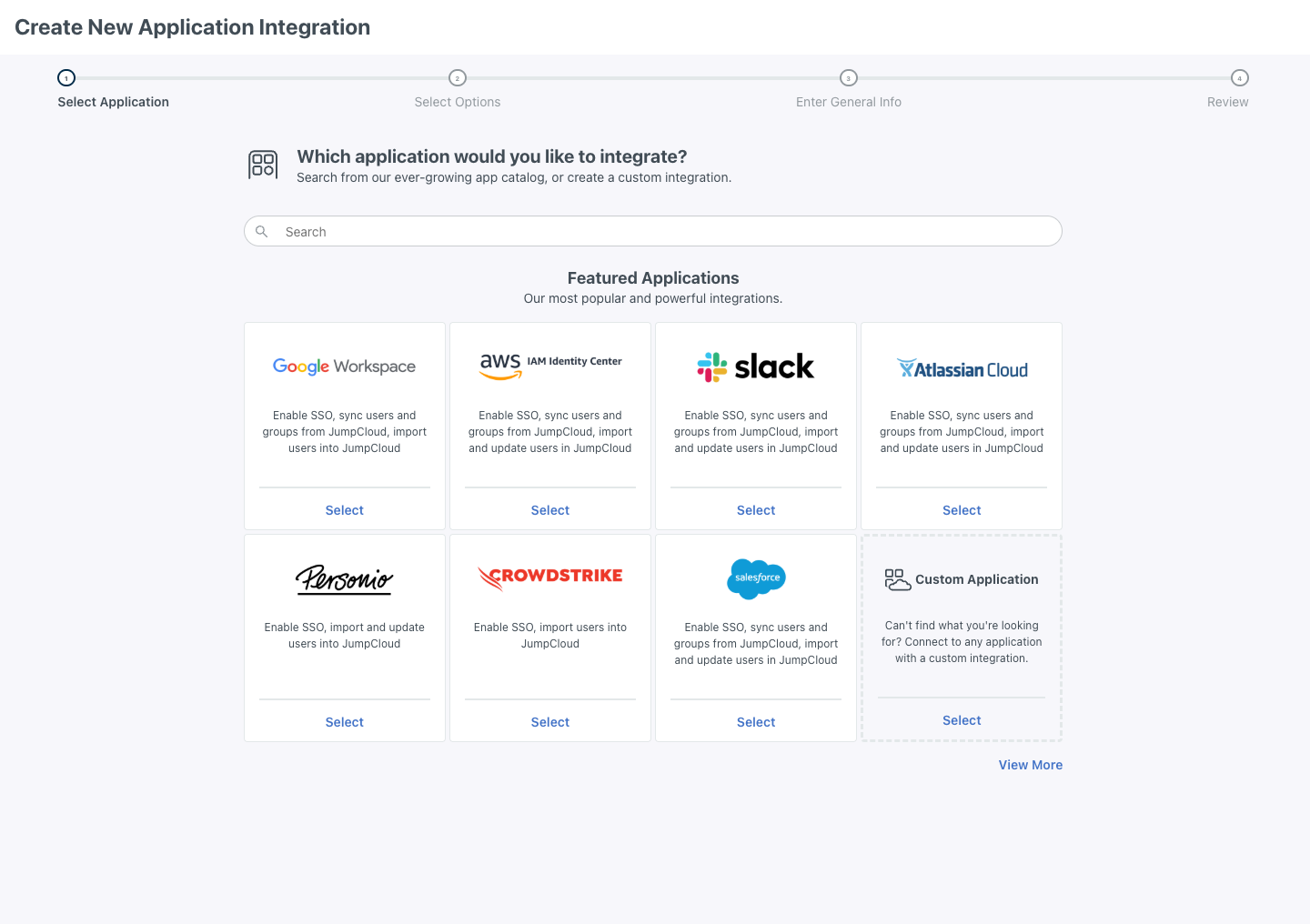
One Portal, Many Apps
Accessing apps at work shouldn’t feel like a chore for employees. Set up users to enable them to quickly access web apps from their JumpCloud User Portal. Provide access to apps via SAML 2.0 and OpenID Connect (OIDC), using a catalog of pre-configured connectors.
Blog Post
| What is Single Sign-On (SSO)?Support Article
| Connecting Apps to JumpCloud Using Pre-Built ConnectorsCourse
| Advanced SSO

Scalable User Management
Create dynamic user groups based on user attributes, then associate them to the resources they need. Onboard with automatic access provisioning to each group-connected resource. Manage access, account provisioning, and deactivation with a few clicks.

Explore JumpCloud Open Directory Platform Capabilities
Identity Management
Access Management
Device Management







