Linux Endpoint Management
Secure, accessible, and centralized management for all your Linux distros and devices.
Integrated Management and Security for Linux Endpoints
Secure, monitor, and manage your fleet of Linux devices and endpoints with unified policies and without the need for custom code and configurations. Deliver seamless experiences for your users and admins with frictionless authentication, remote-enabled management, and automated workflows. Advanced security features ensure ongoing protection for your devices, users, and organization.
Simple, Accessible Linux Management
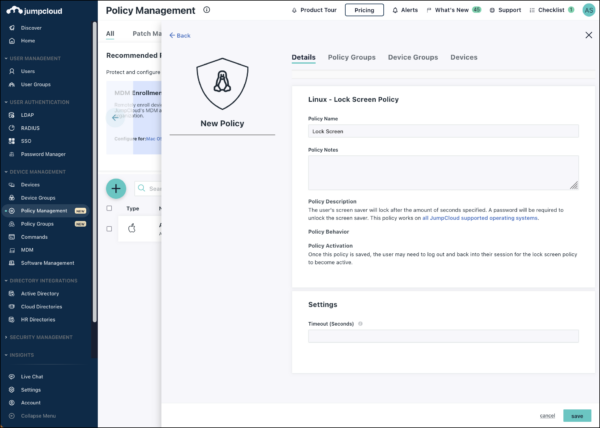
Manage Linux endpoints with the same flexibility, control, and platform as other devices, without the need for custom code and configurations. Leverage JumpCloud’s admin-friendly UI and templated policies to make Linux device management accessible to your team, get devices up and running quickly, and reduce the risk of manual errors.
Onboard new endpoints quickly, and secure and configure them as soon as they enroll.
Write out tasks in any language supported by the Linux device, or select from pre-programmed Linux policies.
Combine Linux device management with identity and access management to secure users holistically with password complexity requirements, MFA, and more.
Support Article
| Get Started With Linux Endpoint ManagementBlog Post
| How To Manage Sudo Users in Other Distributions: Guides on Similar Procedures for Different Linux Distributions

Wide-Ranging, Integrated Support
JumpCloud supports a wide variety of Linux distros, which empowers you to secure, monitor, and manage all your Linux devices and endpoints with JumpCloud. Further, JumpCloud is OS-agnostic, so you can manage your Windows, Macs, and mobile devices alongside your Linux fleet, all in the same platform. JumpCloud combines this device support with identity and access management, giving you comprehensive control over your IT ecosystem.
JumpCloud supports many popular Linux distros, as well as macOS, iOS, iPadOS, Windows, and Android devices, all in one platform.
A lightweight agent allows admins to execute policies, tasks, and commands on each device.
Some of the key Linux distros that JumpCloud supports include Amazon Linux, Debian, Fedora, RHEL, Mint, Rocky, Pop!_OS, Ubuntu and more.
Control whether your Linux devices need SSH keys, have sudo access, require MFA for step-up security, and more.
Support Article
| See All Supported Linux DistrosBlog Post
| How to Migrate CentOS 7 to AlmaLinux

Comprehensive Security
Enhance security with policies that range from device encryption to conditional access policies, passwordless authentication, and more. Draw on a unified approach to identity and device management to create and enforce robust, contextualized policies that don’t require extensive knowledge of each distro’s unique characteristics to implement.
Use preconfigured security commands (lock, restart, shutdown, erase, inactivity timeout) or create and run your own on remote devices.
Remotely access Linux devices via SSH, JumpCloud Remote Access, or command-line access, check endpoint health, and verify configuration.
Get insights into hundreds of critical data points about each Linux device through System Insights.
Support Article
| View All Linux PoliciesWebinar
| Best Practices for Securing and Managing Linux Devices

Try our Linux Endpoint Management Guided Simulation
Please rotate device
This interactive demo is best viewed in landscape mode.
Explore JumpCloud Open Directory Platform Capabilities
Identity Management
Access Management
Device Management








