Integrate an existing Identity Provider (IdP) with JumpCloud to allow users to securely authenticate using their IdP credentials to gain access to their managed resources.
Prerequisites
- You need to have a Google Cloud account with the permission to create new Google Cloud Projects .
- You need to have Admin with Billing permissions to configure an IdP.
Considerations
- Federated authentication will be applied to only specific user groups. See Routing Policies for Identity Providers to learn more.
- Creating the IdP won't automatically result in users logging in with that IdP.
- User Portal access will be available with a federated login. If you don’t want User Portal access, you can create a policy to deny this, see Get Started: Conditional Access Policies to learn more.
- In order to provision users from your Google Workspace directory to JumpCloud, see Configure the Google Cloud Directory Sync to learn more.
- If you have third party SSO for your organization turned on in Google Workspace, you'll need to turn it off for it to work with JumpCloud. See Configuring an Organization-wide Third Party SSO Profile to learn more.
Preparing your IdP to Configure with JumpCloud
To prepare your connection:
- Log in to your Google Cloud Console.
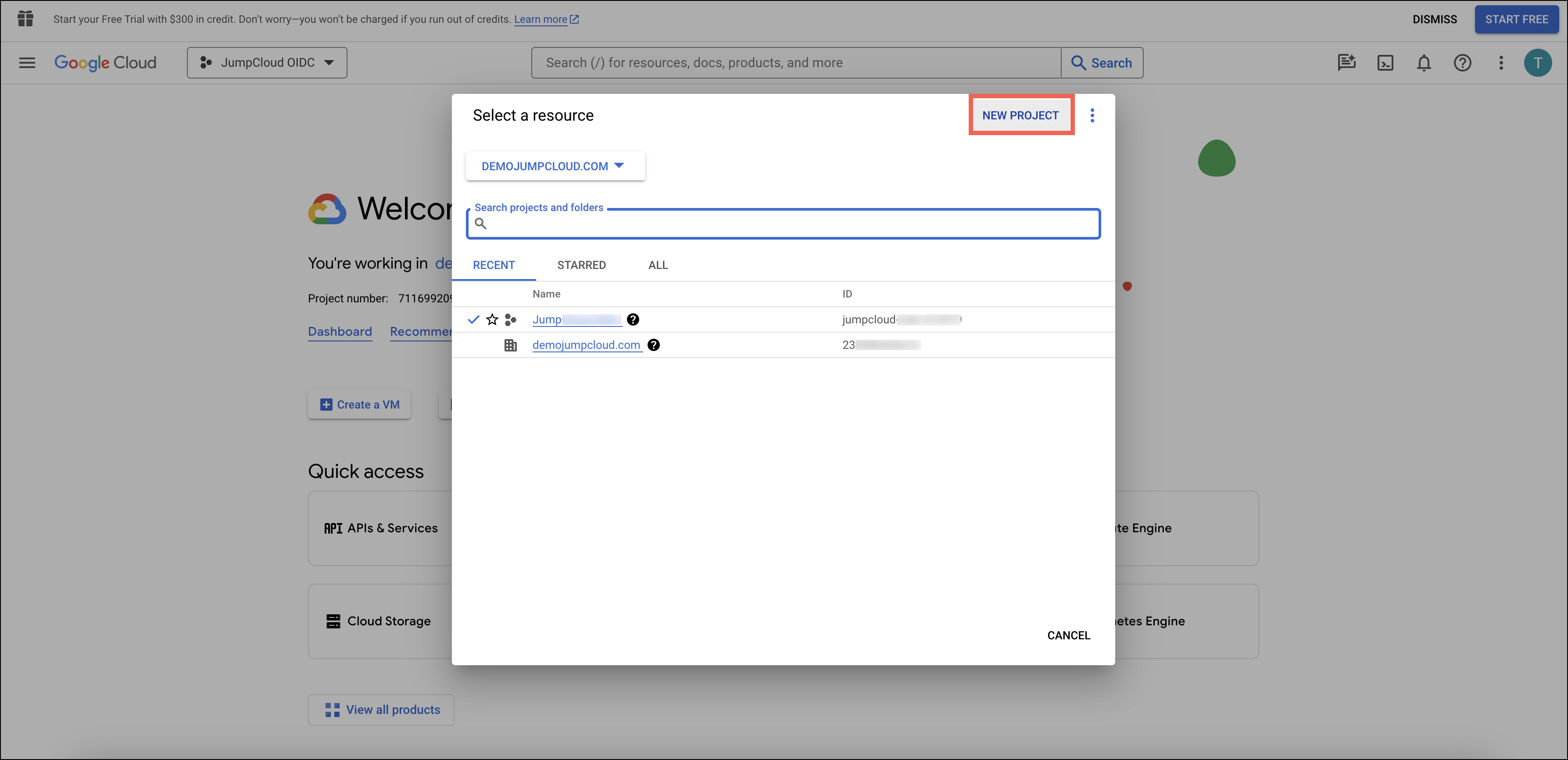
- Next to the logo in the top left corner, click the dropdown menu, then in the top right corner of the modal, click NEW PROJECT. Name it something associated with JumpCloud, like ‘JumpCloud OIDC’ and click CREATE.
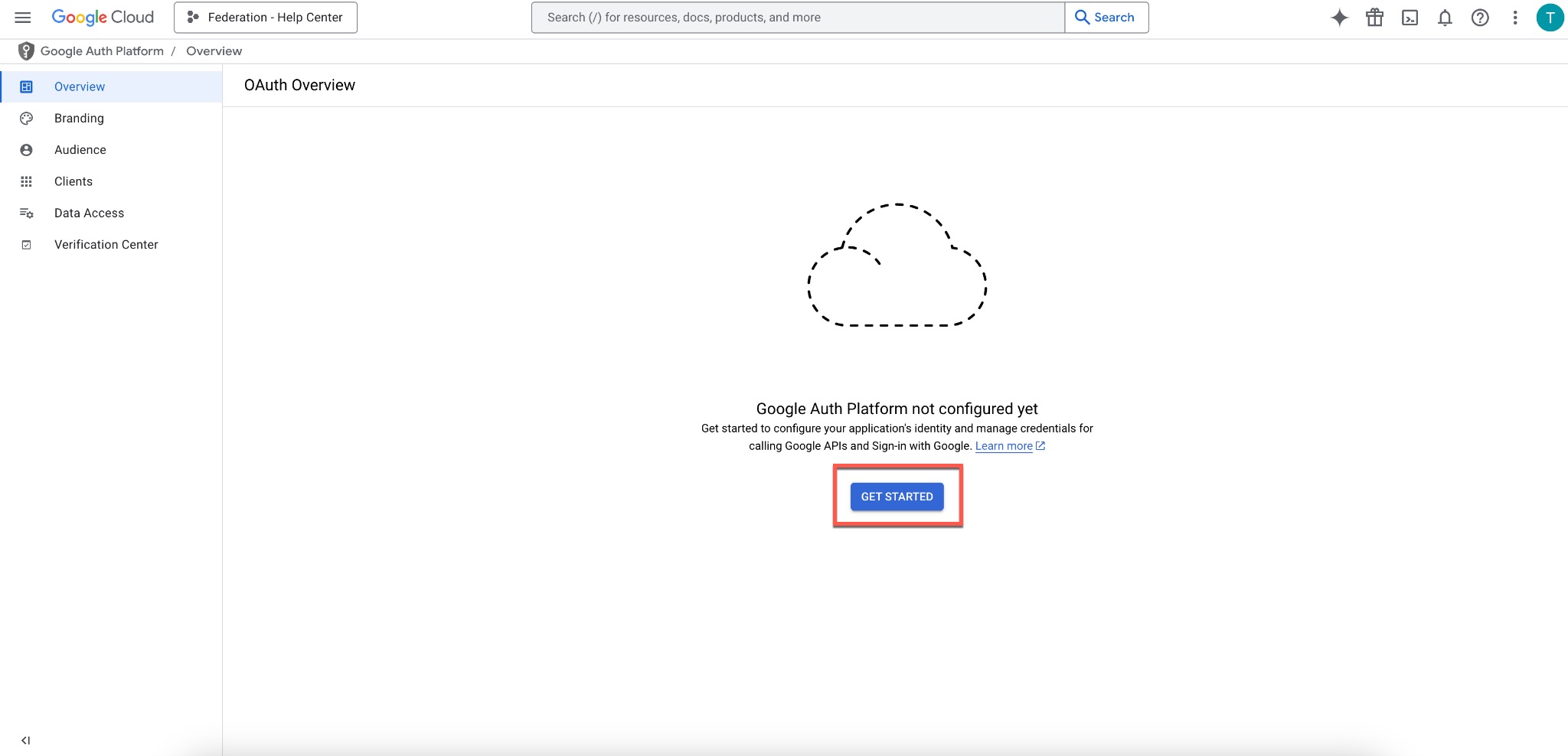
- In the left menu, go to OAuth consent form.
- Click Get Started to configure Google Auth Platform.
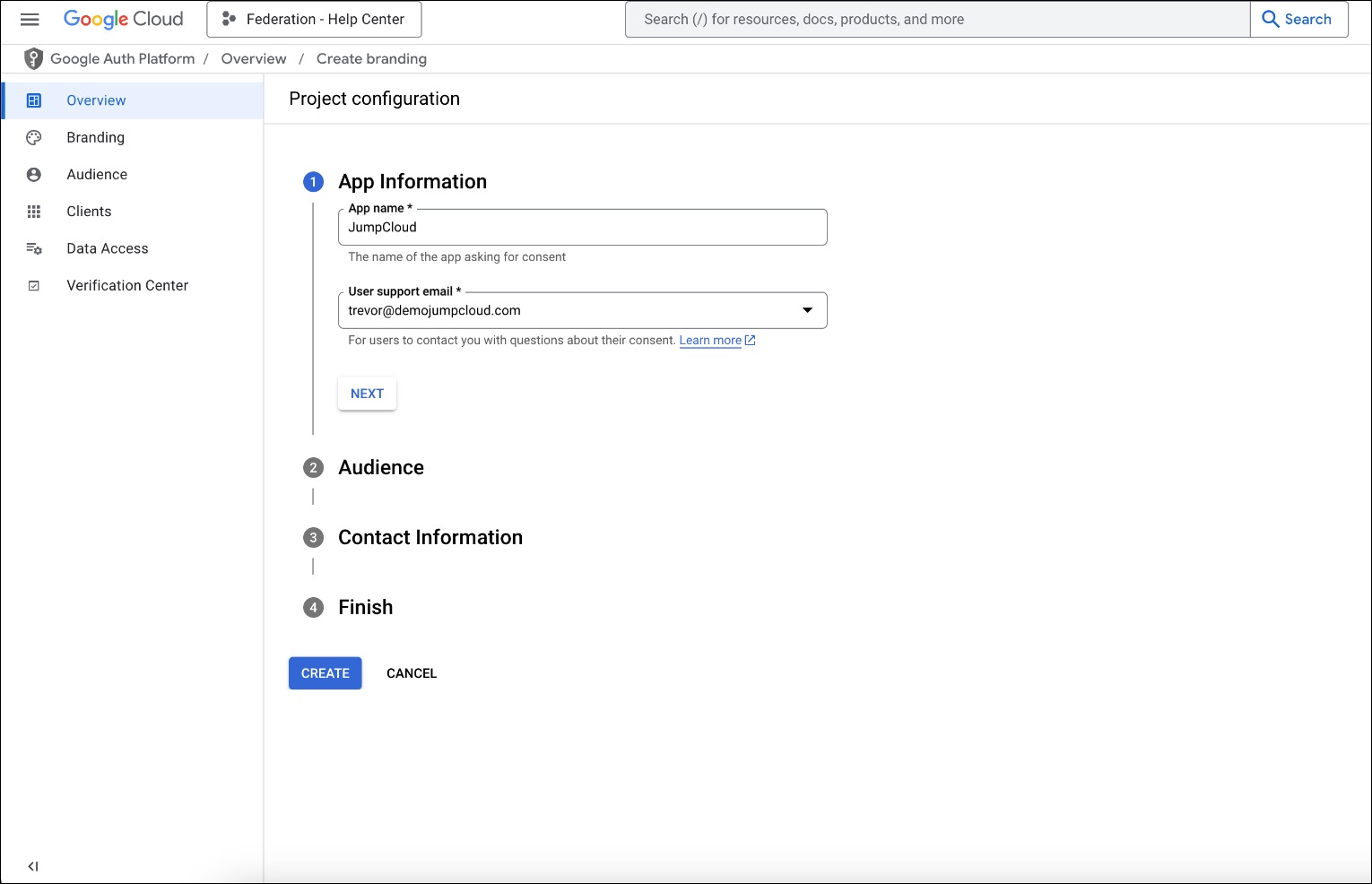
- On the App Information page, enter an App name*, something associated with JumpCloud, like ‘JumpCloud’.
- In the next dropdown menu, select a User support email*.
- Click NEXT.
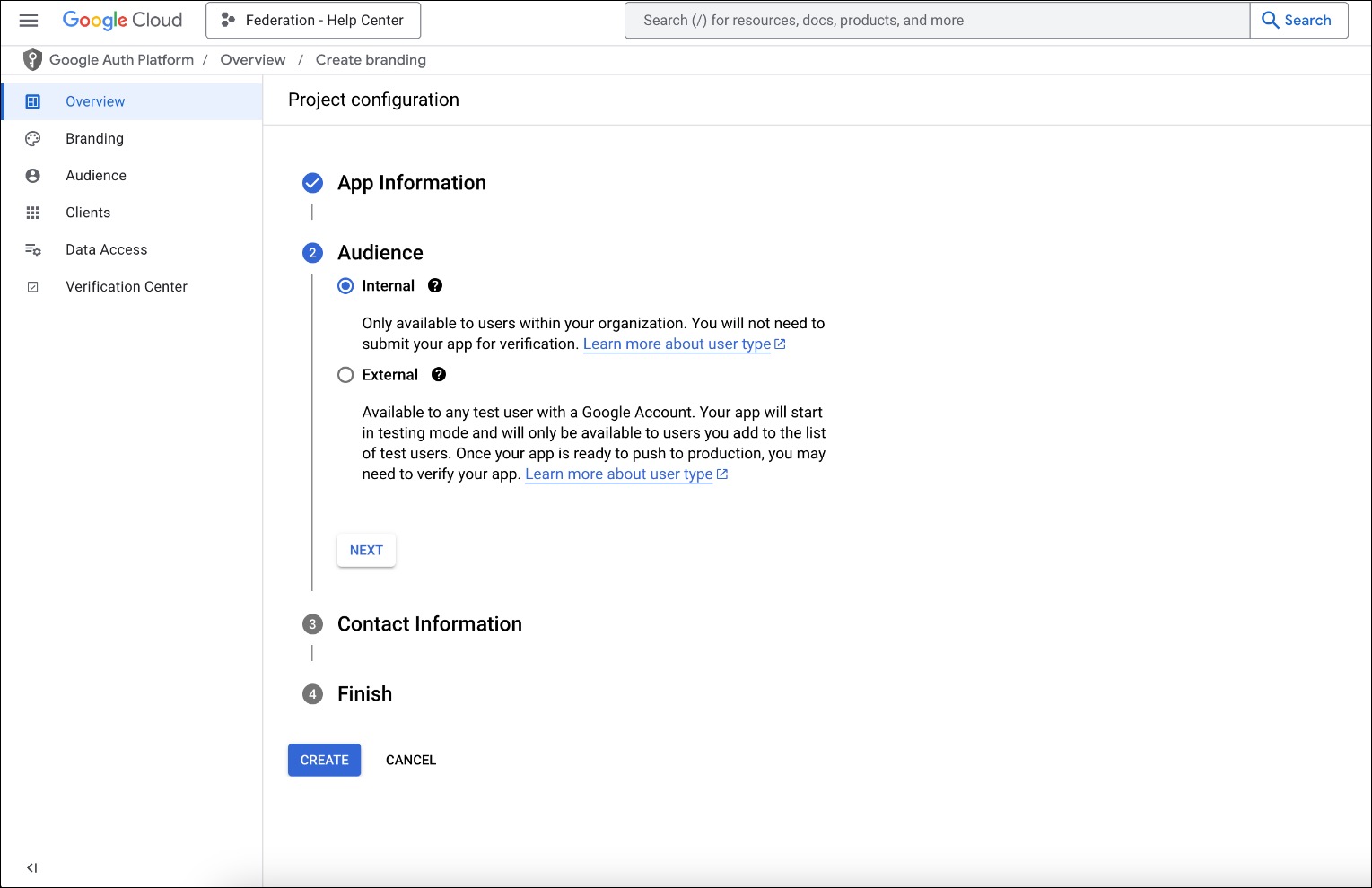
- Under Audience, select Internal, then click NEXT.
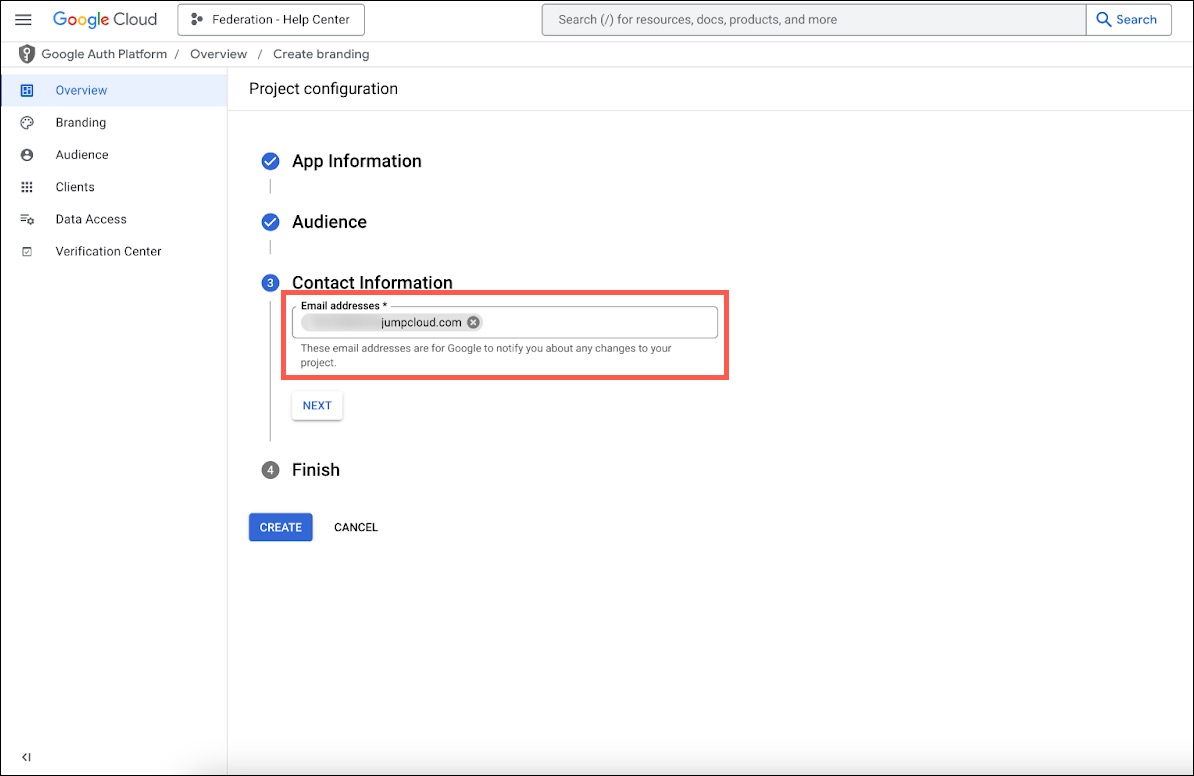
- Under Contact Information, enter a contact email address, then click NEXT.
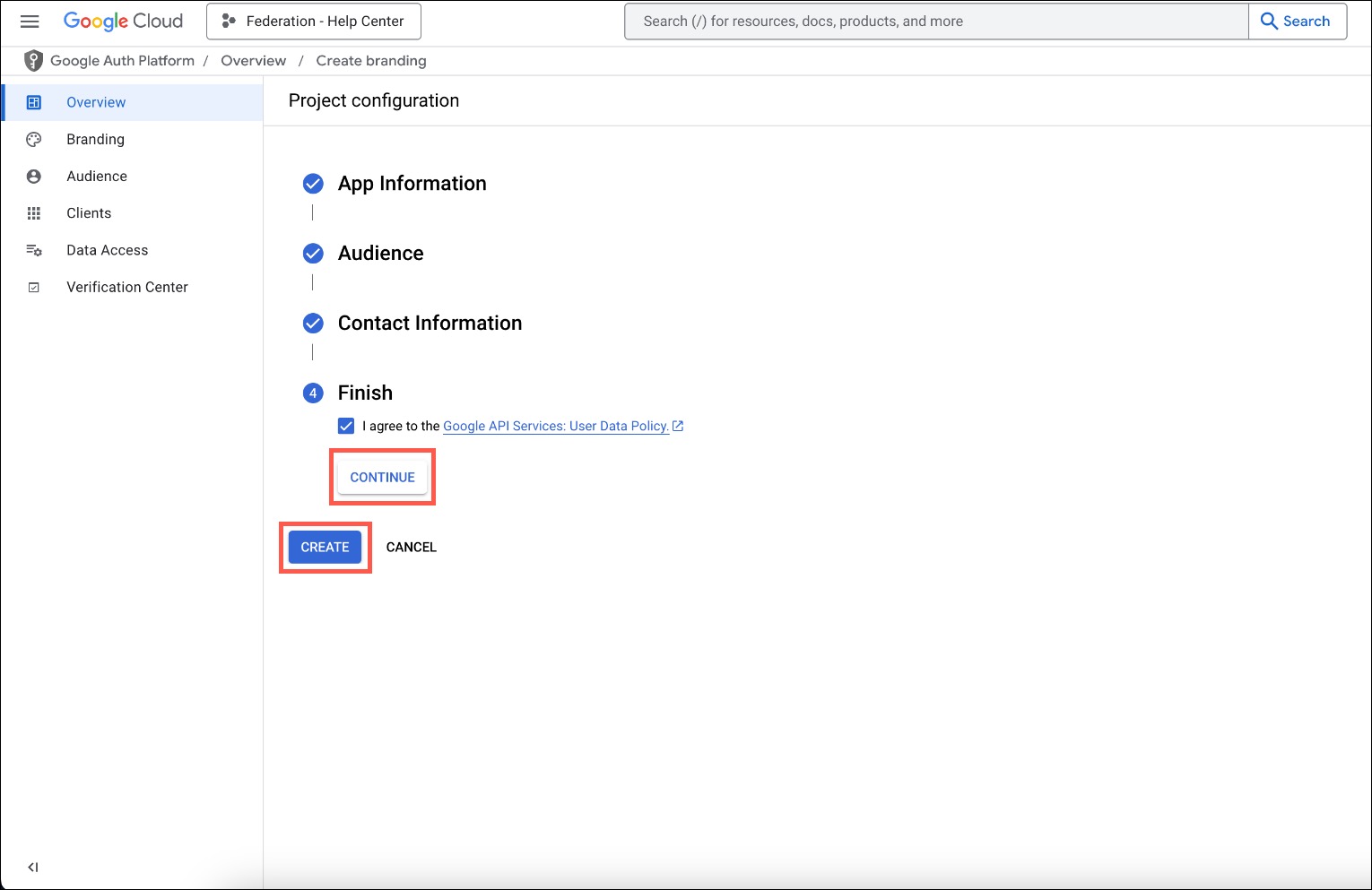
- Under Finish, select to agree to the policy and click CONTINUE, then CREATE.
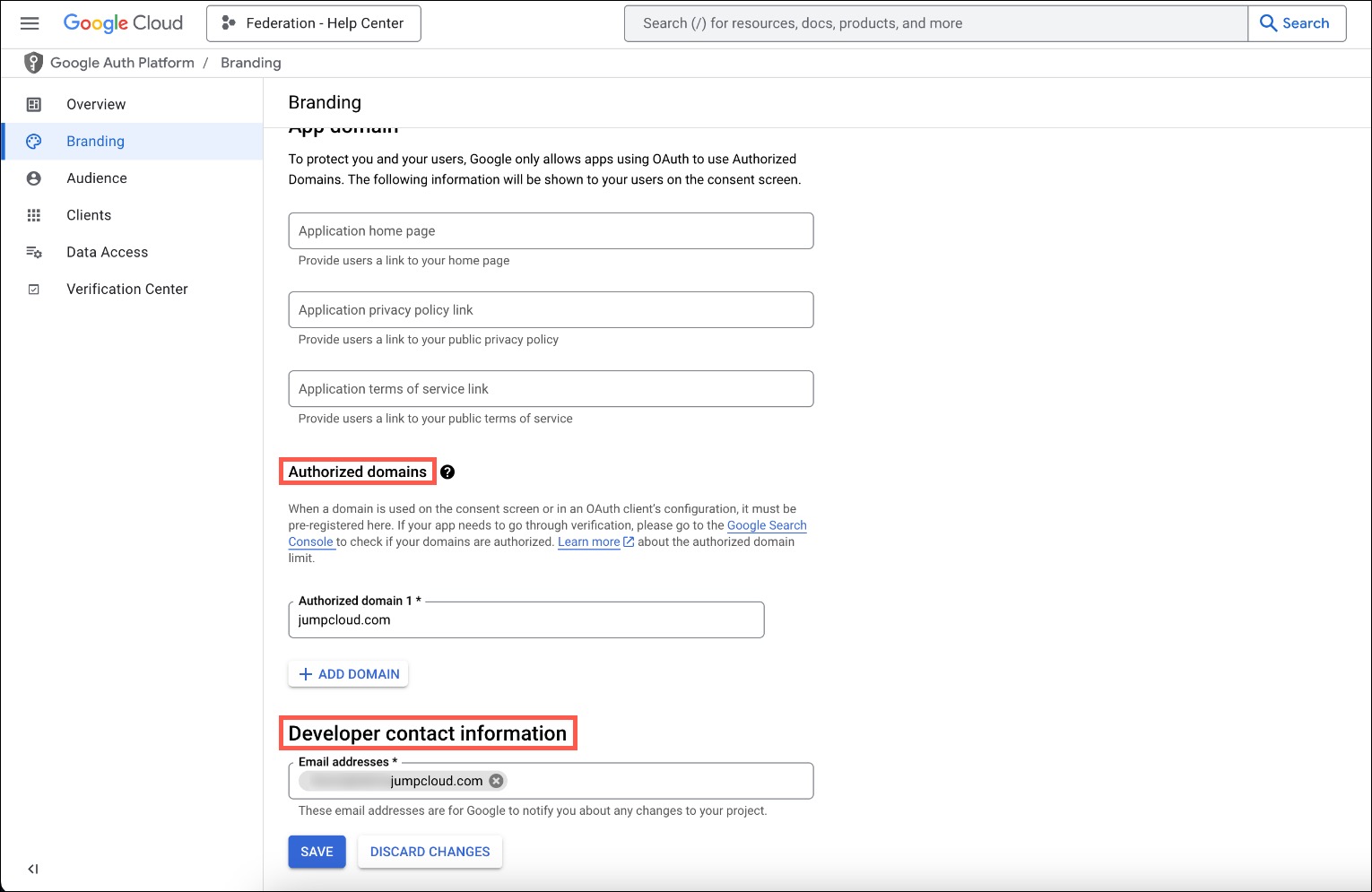
- In the left menu, go to Branding. Scroll down to Authorized domains, under Authorized domain 1*, enter
jumpcloud.com - Under Developer contact information, enter an Email address*.
- Click SAVE.
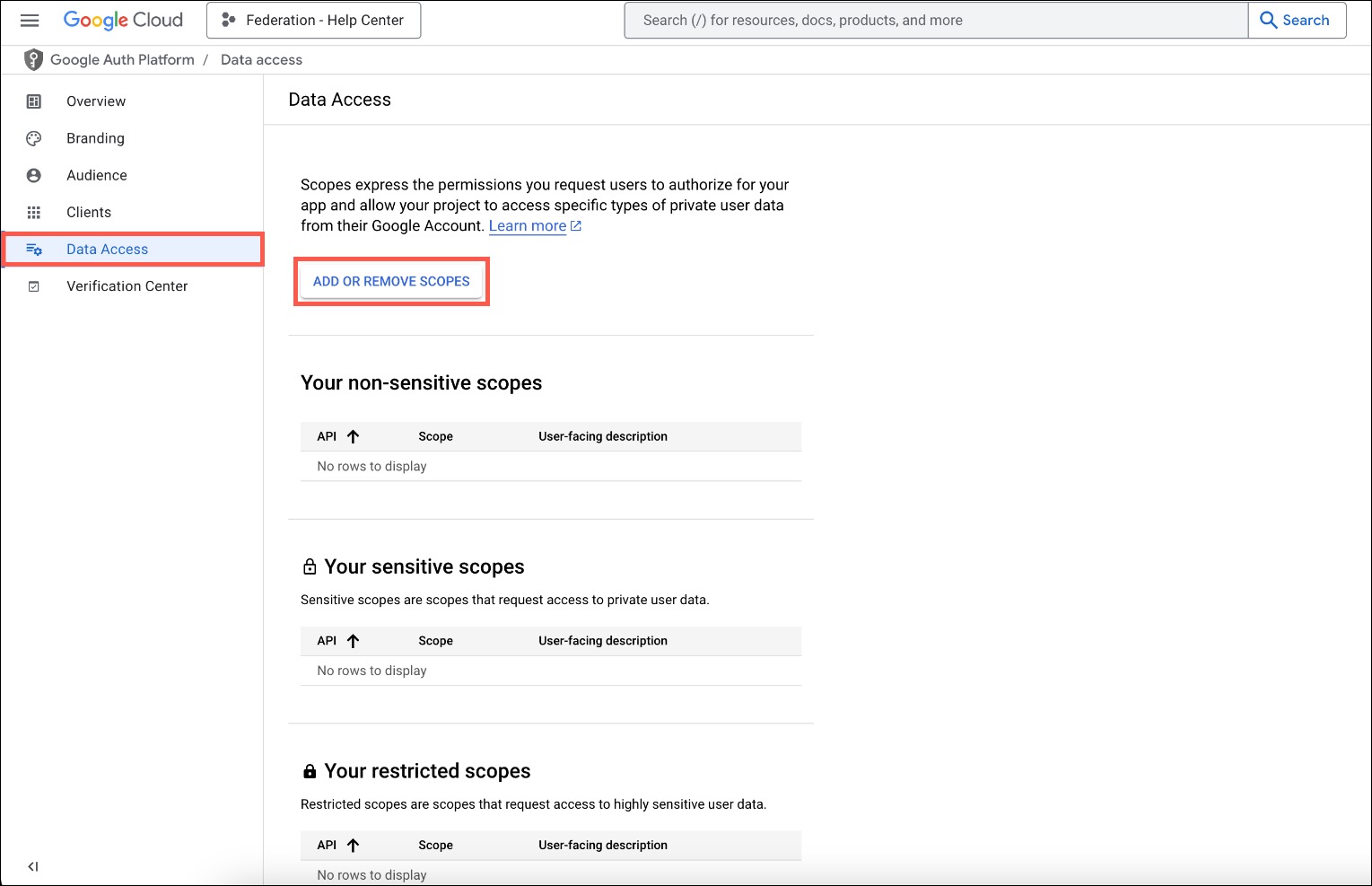
- In the left menu, go to Data Access to manage the scopes. Click ADD OR REMOVE SCOPES.
- Select the first three scopes; email, openID, and profile.
- Click UPDATE then SAVE.
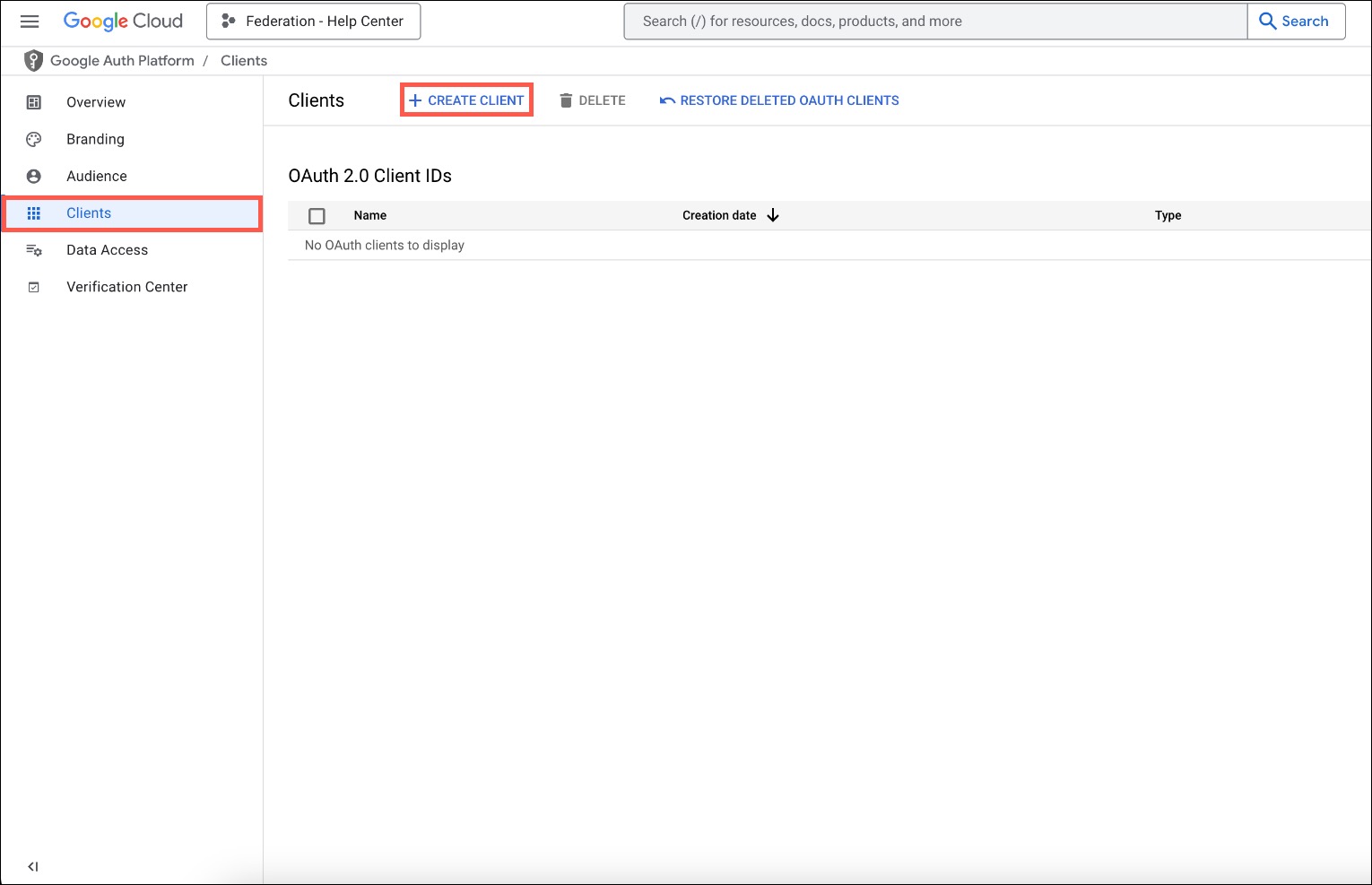
- In the left menu, go to Clients. In the top menu, click + CREATE CLIENT.
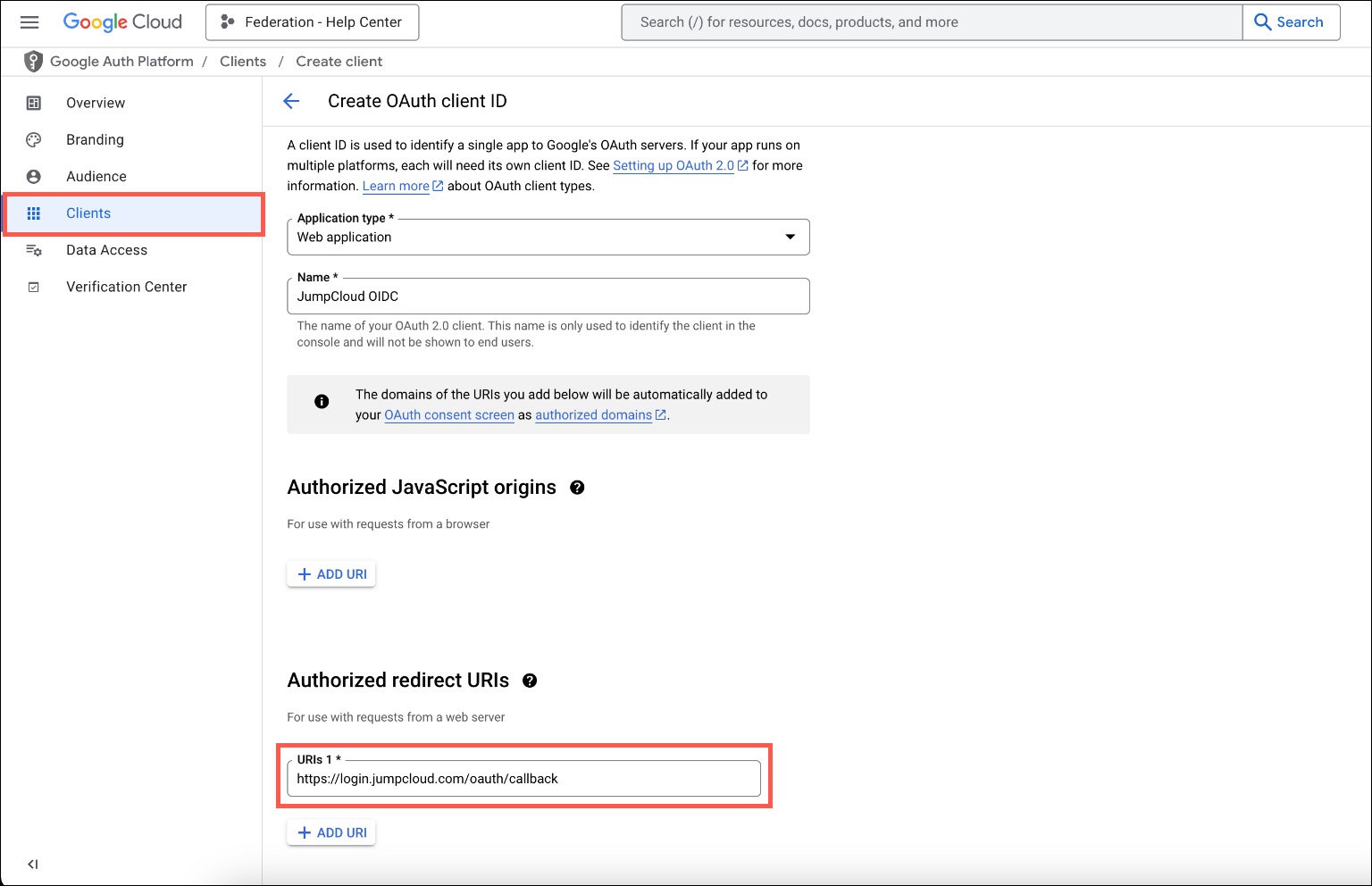
- On the next page, click the Application type* dropdown menu and select Web application.
- Then, enter a Name*, something associated with JumpCloud, like ‘JumpCloud OIDC’.
- Under Authorized redirect URIs, enter
https://login.jumpcloud.com/oauth/callback- For organizations using the EU data center, enter
https://login.eu.jumpcloud.com/oauth/callback
- For organizations using the EU data center, enter
- Click CREATE.
- You’ll get a successful OAuth client created modal with the Client ID, Client secret, Creation date, and Status.
- Copy the Client ID and Client secret to your clipboard. You’ll need these to configure Google Cloud in JumpCloud. Then click OK to exit out of the modal.
Now, you have a connection to JumpCloud in Google Cloud. Next, you’ll want to configure the connection in JumpCloud.
Configuring Google Cloud as an IdP in JumpCloud
To configure Google Cloud:
- Log in to your JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Click User Management > Identity Providers.
- Click the Add Identity Provider dropdown menu, and select Google.
- Enter an Identity Provider Name* as a display name (i.e. Google OIDC).
- Under Google IdP URL*, enter https://accounts.google.com.
- For Client ID*, paste in the first URL that you copied into your clipboard.
- For Client Secret, paste in the secret that you copied into your clipboard.
- Click Save.
Managing the IdP
To manage the IdP:
- From the JumpCloud Admin Portal, click User Management > Identity Providers.
- You can update the name, Google IdP URL, Client ID, and Client Secret.
- Under Authentication, you’ll see that Federation is applied to your users, allowing them to authenticate with an IdP.
- Under Device Account Provisioning, you can configure either Self Service Account Provisioning or Automated Device Enrollment for whichever OS you’re provisioning. The Status displays either Enabled or Disabled accordingly, click Configure to edit.
- See Provision New Users on Device Login and Automated Device Enrollment to learn more.
Deleting the IdP
To delete the IdP:
- From the JumpCloud Admin Portal, click User Management > Identity Providers.
- At the bottom of the IdP Configuration page, under Delete Identity Provider, click Delete IdP.
- You’ll be prompted to confirm your deletion, then click Yes, Delete.
Additional Resources:
Walk through a guided simulation for Configuring Google Workspace as an Identity Provider