The JumpCloud Google Workspace Single Sign-On (SSO) integration empowers you to centralize user access and enhance security. By enabling SSO, you simplify access for your end-users, allowing them to securely log in to Google Workspace using their JumpCloud credentials. This integration also allows you to enforce critical security controls, including JumpCloud's Multi-Factor Authentication (MFA) and Conditional Access Policies.
Pairing this with the Google Workspace Cloud Directory Integration provides full identity provisioning and synchronization, streamlining IT user management.
Read this article to learn how to set up Google Workspace SSO.
Prerequisites
- A JumpCloud administrator account
- JumpCloud SSO Package or higher or SSO à la carte option
- In order to successfully complete the integration between JumpCloud and Google, you must have administrative rights to access configuration in your Google Workspace account
- Google Workspace subscription for Enterprise, Business, or Education
Important Considerations
Read the SAML Configuration Notes before you start configuring this connector.
- Non-profit or Standard (Free legacy) editions do not support SAML
- When a Google Super Admin tries to sign in to an SSO-enabled domain via admin.google.com, they will not be redirected to JumpCloud for authentication, but rather will be prompted for their full Google email address and associated password:
- Read Google’s full documentation on SSO-enabled domain redirects for Super Admins
Creating a new JumpCloud Application Integration
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Access > SSO Applications.
- Click + Add New Application.
- Type Google Workspace in the Search field and select it.
- Click Next.
- In the Display Label, type your name for the application. Optionally, you can enter a Description, and choose to hide or Show in User Portal.
- Optionally, expand Advanced Settings to specify a value for the SSO IdP URL. If no value is entered, it will default to https://sso.jumpcloud.com/saml2/<application display label>.
The SSO IdP URL is not editable after the application is created. You will have to delete and recreate the connector if you need to edit this field at a later time.
- Click Save Application.
- If successful, click:
- Configure Application and go to the next section
- Close to configure your new application at a later time
Configuring a SAML SSO Integration
To configure JumpCloud Part 1
If you are continuing from the Add New Application flow above, skip to step 3.
- Create a new application or select it from the Configured Applications list.
- Select the SSO tab.
- Replace YOURDOMAIN with your Google Workspace domain name in the IdP Entity ID and Default Relay State fields.
- Skip updating the SP Entity ID and ACS URL, those will be updated after you configure Google.
- Add any additional attributes.
- Click Save.
- Leave the configuration open, so you can copy values to the Google Workspace configuration
Download the certificate
- If you closed the application, find it in the Configured Applications list and click anywhere in the row to reopen its configuration window.
- Click Actions > Download Certificate.
The certificate.pem will download to your local Downloads folder.
To configure Google
Google Workspace gives you the flexibility to enforce SSO for your entire organization, an organizational unit (OU), specific groups or users.
Google supports up to 1000 different Individual Third Party SSO profiles.
- Log in to the Google Admin Console.
- Navigate to Security > Authentication > SSO with third party IP.
- Select Add SAML Profile and enter the SSO profile name.
- Select Send email address in the URL as the login_hint parameter
- Enter the following information:
- IDP entity ID - copy and paste the JumpCloud IdP Entity ID
- Sign-in page URL - copy and paste the JumpCloud IDP URL
- Sign-out page URL - enter https://console.jumpcloud.com
- Upload certificate - browse to and select the certificate downloaded in the previous section
- Click Save.
- Leave this configuration open, so you can copy values to the JumpCloud configuration.
To configure JumpCloud Part 2
- Update the following information in the JumpCloud Configuration:
- SP Entity ID- copy and paste the Entity ID from the SP details in the Google configuration.
- ACS URLs - copy and paste the ACS URL from the SP details in the Google configuration.
- Default Relay State - (optional) change the URL if you want your users to land on a different page than their Gmail inbox when logging in to Google Workspace.
- Click Save.
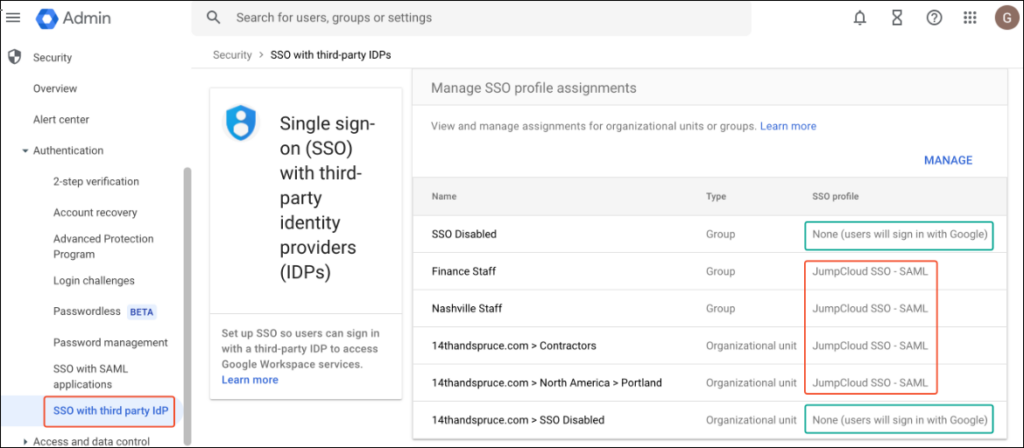
To assign Google SSO Profile(s)
Google's SSO profiles provide flexibility to include or exclude specific user groups or organizational units (OUs) from SSO through assignments within your Google Workspace environment.
- To specify which users, groups, or OUs will use this SSO profile, navigate to Security > Authentication > SSO with third Party IDP > Manage SSO profile assignments.
- Select the OU, group, or use to which you want the SSO profile to be enforced.
- Click Save.
- To remove SSO, select None from the dropdown.
Disabling Google Workspace non-Admin User Password Recovery
To ensure an appropriate user workflow for password resets, Google allows for completely disabling non-admin user password recovery through the dashboard configuration.
This will not modify the Forgot Password reset link behavior.
To disable non-admin password recovery
- Log in to Google as an administrator from your tenant.
- Go to Security > Account recovery.
- Click User account recovery.
- Deselect the Allow users and non-super admins to recover their account option.
- Click Save.
Authorizing User SSO Access
Users are implicitly denied access to applications. After you connect an application to JumpCloud, you need to authorize user access to that application. You can authorize user access from the Applications, Users List or User Groups page.
To authorize user access from the Application’s page
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Access > SSO Applications, then select the application to which you want to authorize user access.
- Select the User Groups tab. If you need to create a new group of users, see Get Started: User Groups.
- Select the check box next to the desired group of users to which you want to give access.
- Click Save.
To learn how to authorize user access from the Users or User Groups pages, see Authorize Users to an SSO Application.
Validating SSO user authentication workflow(s)
IdP-initiated user workflow
- Access the JumpCloud User Console
- Go to Applications and click an application tile to launch it
- JumpCloud asserts the user's identity to the SP and is authenticated without the user having to log in to the application
SP-initiated user workflow
- Go to the SP application login - generally, there is either a special link or an adaptive username field that detects the user is authenticated through SSO
This varies by SP.
- Login redirects the user to JumpCloud where the user enters their JumpCloud credentials
- After the user is logged in successfully, they are redirected back to the SP and automatically logged in
Removing the SSO Integration
These are steps for removing the integration in JumpCloud. Consult your SP's documentation for any additional steps needed to remove the integration in the SP. Failure to remove the integration successfully for both the SP and JumpCloud may result in users losing access to the application.
To deactivate the SSO Integration
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Access > SSO Applications.
- Search for the application that you’d like to deactivate and click to open its details panel.
- Select the SSO tab.
- Scroll to the bottom of the configuration.
- Click Deactivate SSO.
- Click Save.
- If successful, you will receive a confirmation message.
To delete the application
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Access > SSO Applications.
- Search for the application that you’d like to delete.
- Check the box next to the application to select it.
- Click Delete.
- Enter the number of the applications you are deleting
- Click Delete Application.
- If successful, you will see an application deletion confirmation notification.
Troubleshooting
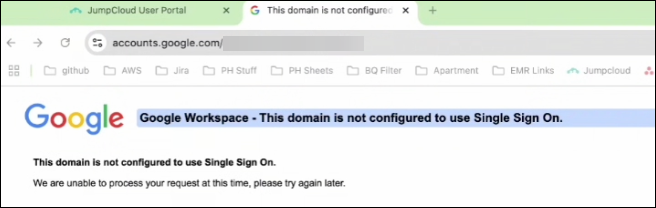
Resolution: Ensure the correct ACS URL is present in the Google Workspace SSO connector in the JumpCloud Admin Portal.
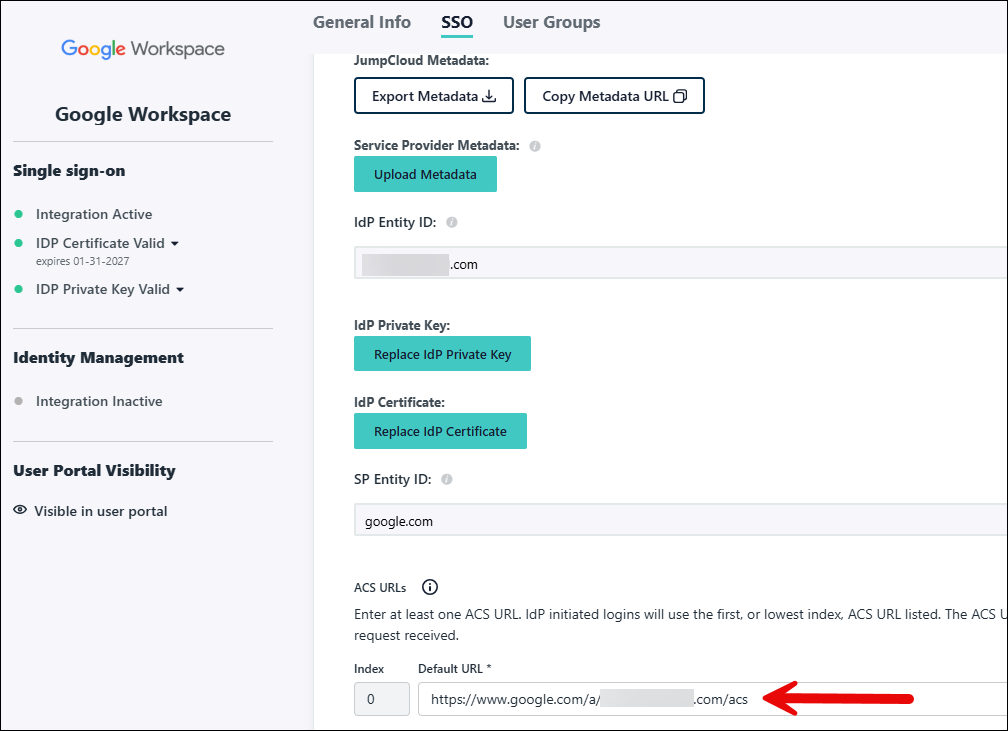
Cause: The Login URL field is populated and forcing an SP-initiated login flow.
Resolution: The URL in the Login URL field should be moved to the Default Relay State field
- Log in to the JumpCloud Admin Portal
- Navigate to Access > SSO Applications in Admin Portal
- Search for the Google Workspace app
- Click the row to open the configuration
- Click the SSO tab
- Copy the Login URL value to the new Default Relay State field
- Remove the value from the Login URL field
- Leave the Login URL field empty
- Click Save