This article describes how to use JumpCloud groups and attribute mapping to set up access control on a new FortiGate device. It’s the second half of a two-part series demonstrating RADIUS AuthN and AuthZ capabilities. The first post converted preexisting FortiGate groups into remote RADIUS users. This approach spares admins the work of having to establish local groups using ACLs on the FortiGate appliance. IT admins can set up strong network access control (NAC) with role-based access to benefit security, workflows, and compliance.
The prerequisite steps involve setting up JumpCloud RADIUS. Please refer back to this support article for those complete instructions. The initial step is to create a user group with a remote server that corresponds with JumpCloud. The group names should be identical on each side.
This example sets up a general VPN users group as well as an administrators group. Reply attributes, which will be outlined in a later step, will be used to segment entitlements for your users. It’s an example of the flexibility and utility of JumpCloud RADIUS.
RADIUS Reply Attributes
Configuring the correct RADIUS Reply Attributes within JumpCloud is the most crucial step in this tutorial. Return to your JumpCloud group and navigate to the RADIUS tab. This is where attribute mapping is defined and values (aka groups on your FortiGate device) are assigned.
Only use the attribute name: “Fortinet-Group-Name”
This example syncs the JumpCloud group with a local administrators group with the resident entitlements.
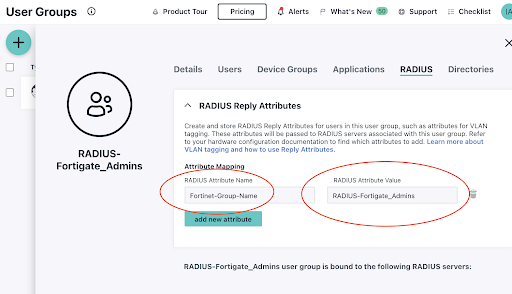
The appliance will determine the user’s level of access control when more than one group is assigned to a RADIUS server. A JumpCloud RADIUS group that has the RADIUS-Fortigate-VPN_Users attribute value will provide general VPN access and the administrators groups will authorize against FortiGate’s super admin profile.
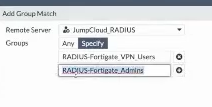
Users that belong to multiple JumpCloud RADIUS groups won’t receive multiple Reply Attributes, making it possible to have a separate administrative login. For compliance purposes, network security should vet access to the administrative group and user creation in JumpCloud. JumpCloud groups leverage attribute-based access control (ABAC), automating the identity management lifecycle by recognizing and responding to changes in employment. This adds an additional security control to your posture via a mature approach to entitlements management.
JumpCloud RADIUS also provides integrated Push and TOTP multi-factor authentication (MFA). Privileged access management is possible through optional conditional access policies. These security features make it possible to enact a Zero Trust security strategy for network hardware.
Now, let’s move on to the FortiGate setup.
FortiGate Setup
Configure your FortiGate RADIUS server for JumpCloud RADIUS. Fortinet also documents how to configure SSL VPNs and SSL VPN captive portals in its knowledge base. Refer back to its documentation for details on those steps. Proceed to the next section when you’re ready.
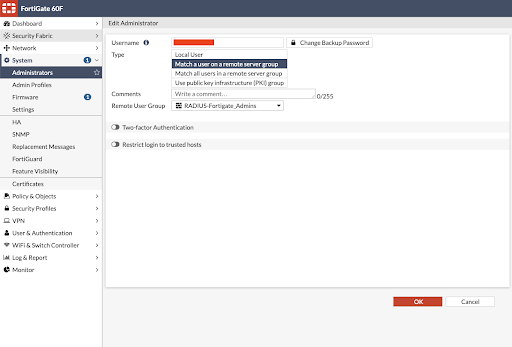
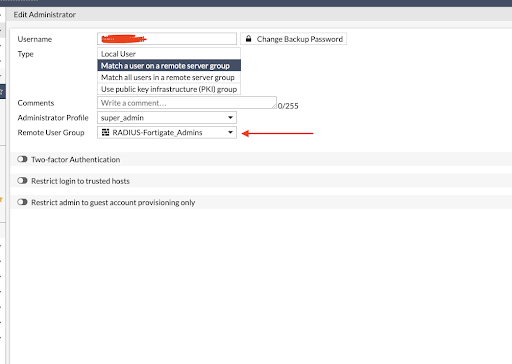
Set Up Remote User Groups
This tutorial demonstrates RADIUS authentication into two groups: one for general VPN access and another for a privileged group for administrators. Settings establish the appropriate entitlements.
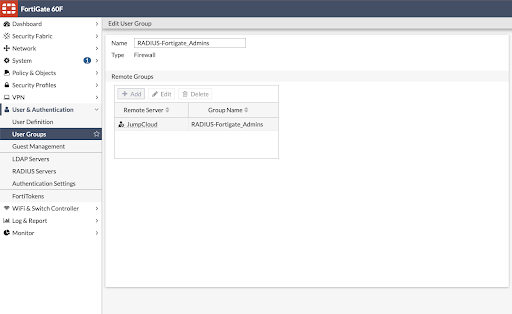
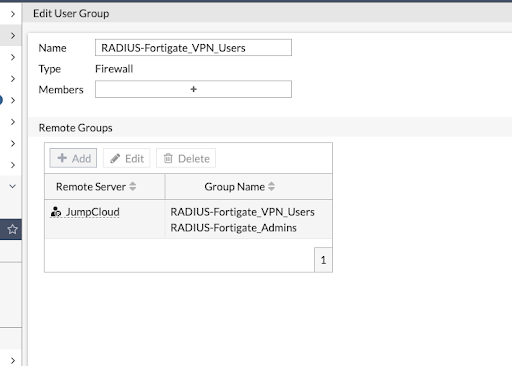
Match Users in JumpCloud and Local Groups
Add users to your groups. Fortinet provides directions on how to add and create groups. Be certain to match the user names with JumpCloud RADIUS user names, exactly.
Test your configuration by attempting to log in with active users. You may also view events in JumpCloud’s directory reporting module.
Reporting
JumpCloud’s Directory Insights captures and logs RADIUS authentications. It makes it possible to determine which user is attempting to access your resources and whether it was successful. Directory Insights is useful for debugging and testing your RADIUS configuration deployments.

Try JumpCloud RADIUS
Additional technical discussion about this topic is best reserved for the JumpCloud community. JumpCloud’s full platform is free for 10 users and devices with premium chat support for the first 10 days to get your started. The open directory platform provides SSO to everything:
- SAML
- OIDC/OAUTH
- LDAP
- RADIUS
Attribute-based group access control, mobile device management (MDM), commands, and GPO-like policies are included in the platform for advanced identity lifecycle management. JumpCloud also features integrated remote assistance, reporting, and an optional password manager and cross-OS patch management. The directory platform works across Android (soon), Apple, Linux, and Windows devices, managing identities wherever the user is.
Need a Helping Hand? Reach out to [email protected] for assistance to determine which Professional Service option might be right for you.




