Work from anywhere isn’t restricted to employees at small to medium-sized enterprises (SMEs). Many IT teams and managed service providers (MSPs) work in distributed teams, which necessitates securing access to network infrastructure and timely user lifecycle management. However, these foundational security controls are too often disregarded when internal budgets, or asking a client to spend more for remote access, fail to address the potential security risks.
This article is the first in a series of how-tos that demonstrate how to use JumpCloud’s capabilities to achieve better security with minimal costs using a centralized platform that includes everything required to secure access to your appliance. It has the added bonus of providing single sign-on (SSO) beyond this scenario, delivering identity and access management (IAM) for every service your organization may use, and eliminating managing passwords everywhere.
Fortinet is the maker of some of the most popular next-generation firewalls (NGFW), and its devices have interfaces to either use its security products or to configure external providers. The prerequisites to secure Fortinet NGFW access with JumpCloud’s services are:
- JumpCloud’s RADIUS services
- JumpCloud’s MFA services
- An authenticator app that supports Time-based One-time Password (TOTP)
- JumpCloud’s cloud directory groups
Three Pillars for Better Access Control
JumpCloud makes it possible for a RADIUS challenge to incorporate TOTP tokens from JumpCloud Protect™ multi-factor authentication (MFA). User passwords are amended to include a token every time a user logs into the appliance. Users are managed from within JumpCloud’s directory groups, which are bound with a RADIUS configuration that’s specific to your NGFW. The directory determines that every group within that group must be enrolled with MFA services to log into any service that JumpCloud connects them to, including your firewall appliance. A service account on the Fortinet device determines what level of admin rights are assigned.
Setting Up JumpCloud RADIUS, MFA
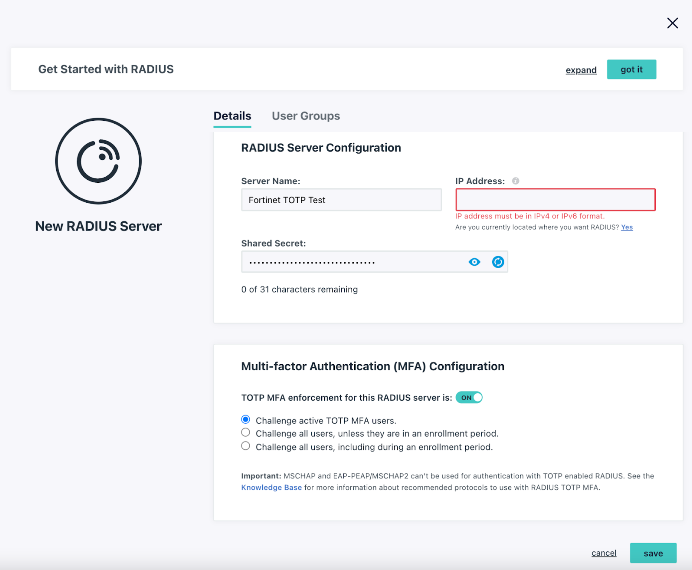
Every JumpCloud account includes RADIUS services, which are configured using the following steps.
To configure RADIUS MFA for a new server:
- Log in to the JumpCloud Admin Portal: https://console.jumpcloud.com/login.
- Go to User Authentication > RADIUS.
- Click ( + ). The New RADIUS server panel appears.
- Configure the RADIUS server:
- Enter a name for the server. This value is arbitrary.
- Enter a public IP address from which your organization’s traffic will originate.
- You must use the external IP for your Fortinet device.
- Provide a shared secret. This value is shared with the device or service endpoint you’re pairing with the RADIUS server.
- Configure TOTP multi-factor authentication for the RADIUS server:
- Toggle the TOTP MFA Enforcement for this RADIUS server option to “On” to enable MFA for this server. This option is “Off” by default.
- Select “Challenge active TOTP users” to require all JumpCloud users with MFA active for their account to provide a TOTP code when they connect to this server.
- Select “Challenge all users,” unless they are in active an enrollment period, to require all JumpCloud users that aren’t in an MFA enrollment period to provide a TOTP code when they connect to this server.
- Select “Challenge all users, including during an enrollment period” to require all JumpCloud users, even those in MFA enrollment periods, to provide a TOTP code when they connect to this server.
- To grant access to the RADIUS server, click the User Groups tab, then select the appropriate groups of users you want to connect to the server.
Note that we recommend using EAP-TTLS/PAP, but Fortinet doesn’t support it at this time.
This article details how to manage users and groups within JumpCloud.
Configuring Fortinet
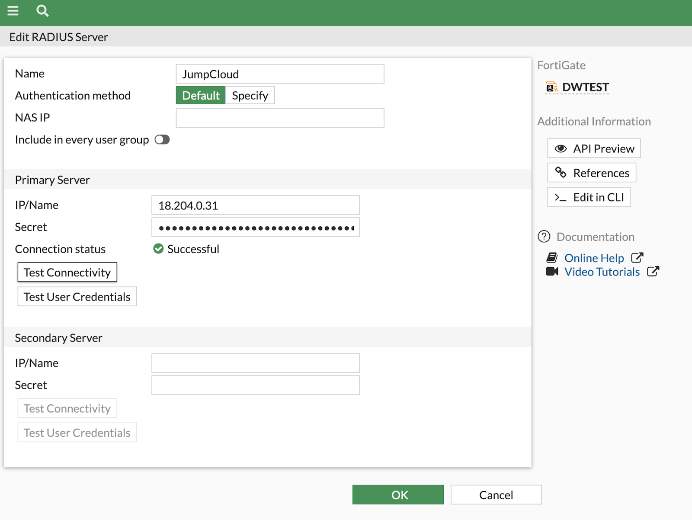
You’ll use the information contained in JumpCloud’s RADIUS interface to create a new RADIUS server entry within your Fortinet appliance, here:
You’ll then enter an arbitrary name for the RADIUS server, one of JumpCloud’s RADIUS IPs, and paste the shared secret where it’s indicated. Importantly, ensure that the PAP protocol is selected as the Authentication Method in order to engage the RADIUS challenge. A TOTP token from JumpCloud MFA, which you can add as an account in an authentication app, is the “response” to the challenge that will validate your users.
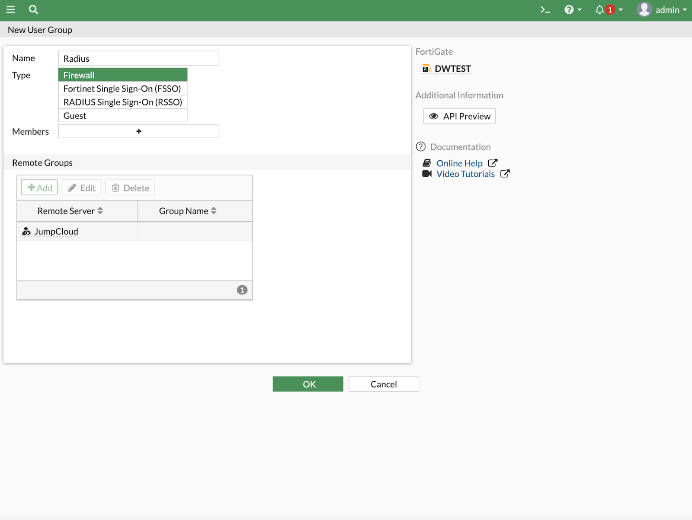
You will then proceed to create a user group for your remote admins within Fortinet.
- Click on User & Devices – User Groups.
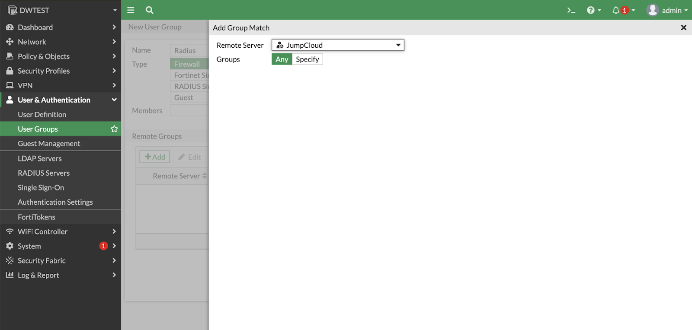
- Hit the “plus” icon to create a new group with the name “RADIUS,” selecting “firewall” as the “type.” Ensure that you add a Remote Server instead of a group.
- Add a “Group Match” by selecting the Remote Server you’ve previously created.
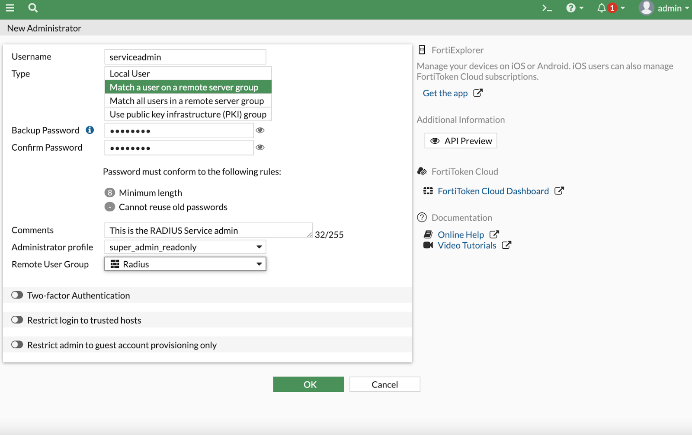
The final step is to create a new administrator that will be a service account for users within the JumpCloud admins group. Begin by selecting “administrators” within the left console panel, and select “Create New.”
- Type in any user name.
- Enter a backup password to use in the event that RADIUS services are inaccessible.
- Determine which Fortigate administrator profile is appropriate for your users.
- Select “Create Remote User Group” under “Type” and hit “OK” after highlighting the RADIUS group you previously created.
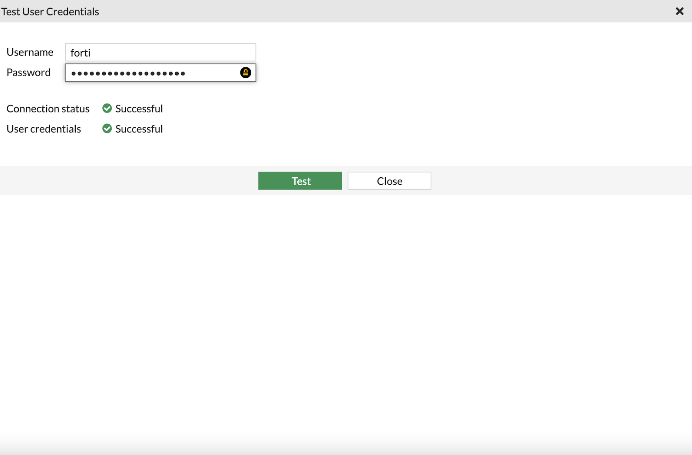
You may test connectivity with JumpCloud RADIUS services in the prior “Radius Servers” panel using the “Test User Credentials” field. This approach will only work when you append a TOTP token, following a comma, with your password. For example, “password123” becomes “password123,tokenstring”. Your logins are now MFA enabled, and Fortinet admin users will now be centrally managed from within JumpCloud’s cloud directory.
Recommended Security Steps
PAP (password authentication protocol) transmits passwords in cleartext. Adding MFA to the authentication process increases security, but we strongly recommend the following steps:
- Connect through a VPN using a secure tunnel (SSL or IPSEC)
- Consider isolating this traffic through its own VLAN and segment your network away from end-user traffic
- Use the strong shared secret that JumpCloud generates for RADIUS and treat it as you would a password.
Try JumpCloud
The JumpCloud platform connects you to more things and is available as a free 30 Day Trial.




