Domain controllers (DC) have been the workhorse of Microsoft-centric networks for over 20 years, but the IT landscape has shifted as technologies and how we work have evolved. Cloud-based alternatives to domain controllers and Active Directory® became available to solve modern IT challenges by positioning devices, not the network, as the gateway to resources. Microsoft offers a virtual infrastructure of services through its Azure platform, but still has dependencies on Windows Server roles to provide authentication and authorization into every IT resource. Azure also introduced a complicated licensing scheme that cordons off key features.
JumpCloud is another option that takes a different approach via its open directory platform that eliminates the need for many on-prem systems. Its open directory consumes external identities and has workflow-based pricing. This article overviews how each of these cloud platforms makes it possible to reduce or eliminate dependence on DCs for a domainless enterprise.
Domain Controllers at Large
Domain controllers were predicated on the concept of a network serving as the perimeter. Microsoft’s approach was to create a “domain” where all of an organization’s IT assets would live. These would all be Microsoft assets, and would all be located on-prem as well.
This enclosed area or “domain” was thought to be more secure than the more open network alternative. Plus, once a user was within the domain, a directory service such as Active Directory® could control what a user had access to. This approach made it simple to appoint one central identity management platform as the control point for user access.
The IT landscape has changed with the inclusion of non-Windows resources and remote work. The original concept of the domain no longer satisfies requirements for many small and medium-sized enterprises (SMEs). Microsoft originally provided add-ons for DCs, such as AD FS, to include single-sign on (SSO) for web applications. It’s since embraced the new normal that Android, Apple, Linux, and Windows devices are all being used to perform work beyond traditional network boundaries. Organizations that use DCs require an assortment of AD add-on solutions such as identity bridges, web app SSO platforms, multi-factor authentication (MFA) solutions, and more. All of this increases IT management overhead and network expenses.
However, it’s now possible to utilize a combination of Azure Active Directory (AAD), Entra, and Intune to manage identities and devices that aren’t part of the Microsoft stack. Let’s explore those options in more detail, because usage is dependent upon a gated licensing model.
Microsoft’s Cloud Domain Solutions
Azure Active Directory Domain Services, coupled with Intune for device management and Entra to manage external identities, is the Microsoft-centric answer to cloud domain controllers. Azure was built with the enterprise in mind with complex, but extensive, deployment options. It spawned an ecosystem of consultants and add-on services for compliance, security, and more. It continues to build out its cloud offerings. For instance: Microsoft has shipped Azure AD certificate-based authentication (CBA), which eliminates the need to run AD FS for CBA. However, many of the services that a DC once provided for free are now being monetized.
Azure AD’s Role
AAD is a cloud-based identity and access management service that was originally created to ferry users into Office 365. Its capabilities are heavily dependent upon which licensing tier you’re paying for. Microsoft gates off features into three tiers: free, Premium 1, and Premium 2. The tier that’s available to you is dependent upon which Microsoft 365 package you’ve purchased, but it’s also possible to add Premium tiers to your Office 365 services at an additional cost per head. Every AAD tier obligates paying more to govern and authenticate external identities with Entra. In addition, only AAD licensing that’s Premium 1 and above will permit you to work with it.
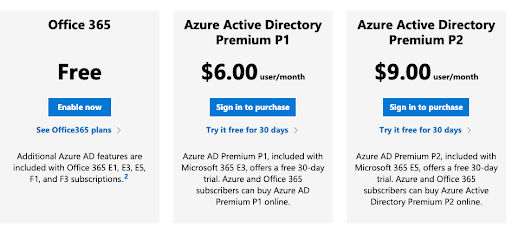
AAD Subscription Levels
Free: AAD’s free tier provides SSO for SaaS applications using your Microsoft identities with MFA. It offers basic reporting on their substrate identity management solution as well as security and usage reports. It leaves out group assignments, omits custom conditional access rules, limits how users can be provisioned, and won’t work with Intune. This leaves its subscribers without device management for endpoint security posture. The Free edition won’t work with Microsoft Sentinel, the Azure security information and event management (SIEM) platform.
Premium 1 (P1): P1 adds the ability to configure Intune, provisioning for Windows devices, more advanced MFA configurations, conditional access policies, end-user self-service, advanced group management, and more thorough alerts and reporting. Azure AD Password Protection is also fully enabled versus limited in the Free edition. Other features are intended to enable hybrid scenarios for on-premises DCs that aren’t possible through the free edition.
Microsoft obligates its customer to adopt its Edge browser in order for its conditional access policies to work.
Premium 2 (P2): P2 includes all of the features of P1 but adds identity governance features including risk-based conditional access policies, conditional access based on device state or location and group, privileged identity protection, Windows Defender for Cloud Apps, and more. Privileged Access Management (PIM) to manage, control, and monitor access administrative roles is only available in this SKU.
Security and Compliance reporting is more extensive, to audit sign-ins, use risk, and activity. It’s possible to integrate with SIEMs, perform access certifications and reviews, and investigate risk events. Lifecycle Workflows, a beta lifecycle management service, is also included.
P2 is an enterprise-grade solution that could contain more extensive capabilities than an SME requires or has the capacity to fully implement and use. The breadth of P2 is significant.
AAD’s Features and Limitations
Operating without a domain controller will obligate you to license Azure Active Directory Domain Services (Azure AD DS) to use managed domain services to migrate legacy on-premises applications. Other solutions, including Microsoft Identity Manager for lifecycle management, require a DC to be installed on-premises. Lifecycle Workflows is being previewed for Azure, which will require either standalone P2 subscriptions or purchasing a higher M365 service tier.
Best practices: There are many steps necessary to configure AAD to be safer from phishing and other credential harvesting attacks. Microsoft has prescribed best practices to secure identities, but reserves several key features for its most premium subscriptions levels.
Devices: AAD lacks cross-OS device management, unless Intune is included within your license tier. Intune is a separate cost from AAD, but requires P1 or P2. Microsoft Autopatch, which includes Windows Update for Business, also has dependencies on Premium licensing. Microsoft has partitioned remote assist off as a premium add-on to Intune.
Interoperability: A domain controller and server running the Network Policy Server (NPS) role is required to utilize common network protocols including RADIUS and LDAP. You’ll also have to install and configure sync tools to connect AAD with your on-premise directory. AD DS also includes LDAP, but that’s also an additional charge beyond your regular AAD subscription.
Intune and AutoPatch for Devices
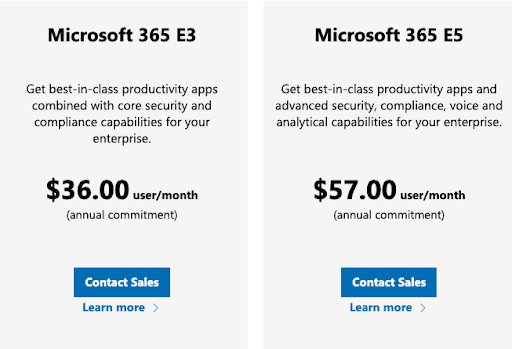
Device management is charged separately from AAD, but it’s dependent on Azure AD Premium subscriptions to function. Standalone licenses (AAD Premium, Intune) or Microsoft 365 E3/E5, Business Premium, or Enterprise Mobility and Security licensing is required. Intune uses ADMX and ADML templates for policy deployment, which may be a familiar approach for AD admins.
Windows Autopatch is available as a system to update the Microsoft stack on Windows, exclusively. Windows Update for Business has been folded into that offering. It requires enterprise-level Windows licensing, AAD Premium, and Intune in order to function.
Difficulties with Intune
Microsoft admins have experienced some difficulty getting Intune to work for them, such as:
- Unpredictable time spent importing device provisioning, assigning profiles, and deploying apps.
- Simple mistakes can cause actions to fail, such as a Registry key requirement rule filtering out devices.
- Problems with assigning available licenses to new users.
- Configuration changes take a long time to go into effect.
- Debugging events and sync logs requiring additional third-party tooling.
- Loss of internet connectivity causing Windows Autopilot to fail.
Testing any feature takes days to weeks because I go ‘hmm what does this do? changes setting 3 hours later huh, still no change…’
Reddit User
JumpCloud strategically combines many of the features found in Premium AAD and Microsoft ‘s Intune, in a manner that’s easier for SMEs to implement and deploy. It can extend existing domain controllers or offer Office 365 subscribers the economy to select less expensive licensing while receiving the benefits of advanced lifecycle management, and device management. It’s even possible to opt for Google Workspace while maintaining your existing Microsoft identities. This next section outlines JumpCloud as a cloud alternative to your DCs.
JumpCloud’s Cloud Domain Controller Alternative
JumpCloud’s open directory platform unifies identity, access, and device management capabilities, regardless of the underlying authentication method or device ecosystem. It can extend both AD and the free tier of AAD to accomplish more, with a lower TCO. JumpCloud authenticates users whether they use biometrics, digital certificates, passwords, or SSH keys. JumpCloud ensures that every resource has a “best method” to connect to it, including LDAP, OIDC, RADIUS, and SAML. Like the original concept of a DC, users can employ a single set of credentials to access systems, applications, networks, file servers, and cloud apps. Essential reporting on directory, SSO, and system-level events is built into the JumpCloud platform.
Identity as the Perimeter
Environment-wide MFA with optional conditional rules for privileged users secures access to your resources. For instance, an unmanaged device wouldn’t be able to log into sensitive resources such as protected customer data. JumpCloud also offers a decentralized password manager for non-SSO applications. This holistic approach to identity and access management (IAM) enables SMEs to deliver secure, frictionless access, from managed devices running any platform. This helps SMEs to adopt a Zero Trust security strategy without great difficulty.
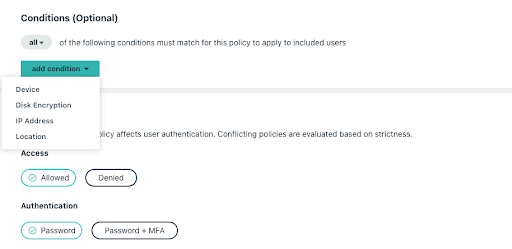
JumpCloud also delivers advanced lifecycle management by integrating with popular HR systems and attribute-based groups that automate entitlements management, either entirely, or making helpful suggestions for admins to review and act on. These features reduce the likelihood of introducing human error or stale credentials compromising security. JumpCloud doesn’t charge extra for group-based access control or advanced entitlements management.

Devices as a Gateway
Unified device management (aka mobile device management, or MDM) makes it possible to position every device as a gateway to your resources through user identities. JumpCloud will manage Apple devices, Android, Linux, and Windows. Pre-built policies, including policy templates, are available to quickly establish default device postures, and root-level command terminals make it possible to centralize other admin tasks. Remote assist is standard.
Provisioning is made simple via Windows Out of Box Experience (OOBE) that is arriving soon. JumpCloud supports Apple’s Volume Purchase Program (VPP) for corporate-owned devices. Unlimited remote assistance is included and cross-OS patch management, with coverage for web browsers, is available if you need it.
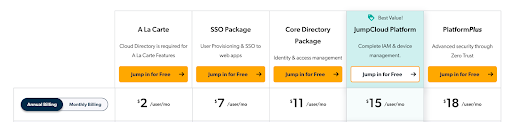
There are no licensing hurdles to obtain device management or consume external identities within your directory. JumpCloud produces value lock-in versus vendor lock-in with workflow-based pricing versus features being gated off to compel a deeper customer commitment.
Learn More
If you would like to learn more about the future of domain controllers, drop us a note. Alternatively, sign up for a JumpCloud free trial and see what the open directory platform could do for you.




