Microsoft Active Directory (AD) is the most common Windows-based user directory solution, and it’s baked into the IT infrastructures of many small and medium-sized enterprises (SMEs), despite being a legacy technology that struggles to support other platforms like Linux.
AD leverages LDAP under the hood, but it largely uses Kerberos as the authentication protocol for Windows machines. Because of this, Linux devices struggle to integrate with AD. Why is that important? AD serves key functions for access control: authentication, authorization, and management. If a business uses 100% Windows systems, AD accomplishes all three tasks.
However, AD starts to fail if a business uses any Android, Apple, or Linux devices; cloud infrastructure or applications, or non-Windows infrastructure that aren’t supported without modernization. Unmanaged devices and identities mean that resources aren’t being protected.
The good news is that you don’t have to replace AD altogether to solve this problem. It’s possible to modernize your existing infrastructure. This article shares several options that enable SMEs to manage their Linux devices/users, including enhancing AD with JumpCloud.
If AD Fails, How Are Businesses Managing Directories?
There are several ways that organizations can connect their Linux devices to Active Directory. The easiest is by using LDAP via the PAM module that’s built into Linux. Organizations can also use Kerberos under this model.
However, each of these approaches creates extra work and could add security issues (through increased attack surface area), instead of completely rectifying the issues where AD fails.
IT will also have to implement a dedicated authentication tool. This often requires heavy IT intervention and physical servers and exists independent of current identity practices and infrastructure.
It’s worth calling out that Microsoft’s enterprise access model supersedes and replaces AD’s tier model. The revised model spans AD installations, is multicloud, and includes users from several identity providers (IdPs) as opposed to a logical separation of AD assets in one domain. This approach fails to meet the requirements of that new reference architecture for AD.
Open Source Solutions
Another method is to leverage Samba and Winbind. This requires setting up Samba, which is no easy feat, and may require changes to the network perimeter. This approach relies heavily on VPNs, which can increase your attack surface area, and are an entrypoint into your network.
Winbind is used to resolve user and group information from Windows Server. PAM will provide authentication services.
It’s also possible to use OpenLDAP’s proxy service for integration with Active Directory. This isn’t a trivial setup and likewise increases IT management overhead and infrastructure.
Azure Active Directory and Intune
Microsoft recently added support for Linux to its Intune endpoint management service. Using Intune will obligate you to configure a hybrid server infrastructure that syncs AD with Entra ID (formerly Azure AD, or AAD). This can be significant work, and AAD is often bundled with Microsoft 365 and could obligate you to adopt a vertically integrated suite of Microsoft tools.
Additional Intune subscriptions may be necessary to manage your devices. Intune setup can be complex and Microsoft’s support for Linux is limited at this time. It imposes restrictions on which browser you may use, with Microsoft Edge as the sole option available to access your resources.
The Best Approach to Modernize AD for Linux
JumpCloud is an open directory platform that unifies identity, access, and device management capabilities, regardless of the underlying authentication method or device ecosystem.
JumpCloud’s open directory platform provides an alternative approach to connecting Android, Linux, or Mac devices to Active Directory. It also has unified endpoint management.
This cloud directory platform acts as an “extension” to AD, solidly fixing the areas where AD falls apart. It authenticates, authorizes, and manages all Android, Linux, Mac, and Windows devices. How? Active Directory Integration (ADI) is the key to making all it work.
How AD Integration and Modernization Works
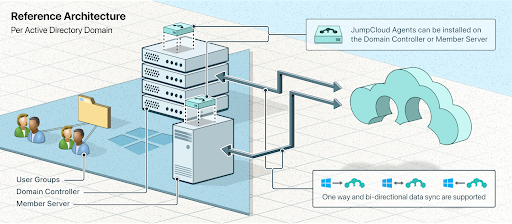
JumpCloud’s AD Integration helps SMEs to reestablish strong access control.
Linux and Mac devices connect to JumpCloud’s cloud-based directory platform via their native authentication mechanisms (and through an agent or mobile device management).
Users are added to JumpCloud’s virtual identity provider either via our Active Directory Integration, or manually.
If Active Directory is connected through the JumpCloud AD Integration feature, then any updates in AD are automatically replicated to JumpCloud and, by consequence, to all Linux devices in the directory, too.
For example, a new user can be added in AD and as a result given access to all of their Linux cloud servers hosted at AWS®. The reverse is also true where a user terminated in AD is automatically deleted from the AWS servers. This is accomplished by an active sync process between AD and JumpCloud.
Linux devices can be easily connected to Microsoft AD through JumpCloud’s hosted directory service. This eliminates the headaches associated with manual management or workaround solutions with Chef or Puppet.
JumpCloud also supports multiple Linux distros, giving you the choice to work how you want to. This allows you to utilize the speed, stability, and security of Linux-based systems, without losing sight of what’s happening in the other operating systems your organization supports.
Other practical benefits include:
- Eliminating the need for multiple passwords and siloed management
- Reducing administrative or technical overhead
- Reducing authentication friction and improving the end-user experience
Compliance and Security
JumpCloud provides a collection of pre-built policies for Linux such as full-disk encryption. These policies help organizations to manage and secure their deployed Linux endpoints more efficiently while improving their overall security posture. Additional policies include:
- Check partition and mount options: Directories that are used for system-wide functions can be further protected by placing them on separate partitions.
- Check disk encryption: This policy will check a Linux machine for full-disk or home-directory encryption and report the status.
- Disable USB storage: This policy prevents USB mass storage devices, such as flash drives and USB hard drives, from being used on the system.
- Lock screen policy: The user’s screen saver will lock after the amount of seconds specified. A password will be required to unlock the screen saver.
- File ownership and permissions: Secure system files for Linux systems.
- Network parameters: Enhance a system’s network security by setting kernel parameters for IP forwarding, packet routing, Internet Control Message Protocol (ICMP) requests, path filtering, and Transmission Control Protocol Sync (TCP SYN) cookies.
- Disable unused filesystems: Prevent an unauthorized user from introducing data into or extracting data from a system. An admin can now determine if a filesystem type isn’t necessary and disable it.
The open directory platform is also a great directory choice for organizations that don’t use AD but would like to manage their Linux devices in a similar way.
Learn More About Connecting Linux Devices to Active Directory
Sign up for a free trial of JumpCloud’s integrated IAM and UEM platform. If any questions come up or if you would like to learn more, drop us a note.
JumpCloud also provides a decentralized password manager and vault for Linux.



