Full-disk encryption (FDE) is recognized as a mandatory security control, but applying it to Linux devices can be cumbersome and complex because there’s no default option for it. JumpCloud provides step-by-step guidance on how to configure FDE as well as Linux Check Disk Encryption Policy to help IT teams establish security requirements for device groups.
What Is FDE and Why Is It Important?
Theft happens, but there could be civil, legal, or reputational consequences if IT teams fail to safeguard against it. Theft in a corporate, governmental, or no-profit setting can run afoul of compliance requirements and lead to data exfiltration that compromises confidential or private information. Full-disk encryption protects your data while at rest: when your computer is off, the data is secure if it gets stolen. It’s a low-cost security control that’s simple to implement.
Distributed workforces have increased the importance of protecting your data, wherever it may reside. There are abundant media reports of thieves becoming more brazen, because there are more attractive targets in cafes and other public areas. Linux devices are no less vulnerable to theft, and it’s a best practice not to make exemptions for operating systems (OSs) that don’t integrate FDE.
The Challenges of FDE with Linux
“Simple” can be a relative term, because there’s no FDE built onto Linux distributions, which necessitates some manual configuration work. Keeping track of which systems are encrypted can also pose a challenge, because there’s scant visibility to know that it’s in place without a policy purpose-built for auditing your FDE requirements.
There are also technical constraints. Linux doesn’t have a switch to enable FDE after first install, but it is possible to encrypt single directories, including user homes, or to implement file-level encryption (should you choose to). It’s easiest to implement FDE during the initial OS installation, using LUKS (Linux Unified Key Setup on-disk format). LUKS is the de facto “standard” for FDE on desktop Linux. It offers reasonable protection by deploying the Advanced Encryption Standard (AES) cypher, which is widely accepted as the minimal strength encryption standard by cybersecurity professionals.
LUKS is very flexible and can be configured to use either a keystore or passphrase with backup key options. It protects against simple “brute force” dictionary attacks and leverages Linux’s device mapper kernel subsystem for ease of installation. It works well for all storage media, including removal disks. Please note that other options are more suitable for application servers that scale for more than eight users. LUKS can be widely deployed throughout your fleet and accommodates auditing.
JumpCloud Provides Compliance Policies
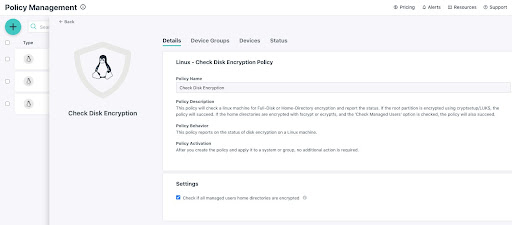
FDE should be added to your checklists for when you’re provisioning devices during the onboarding process. It must be set up before or during the OS installation. JumpCloud offers a policy to check if the system has encryption enabled, and whether it is full disk or only user home directories. JumpCloud’s open directory platform will notify IT admins if any of the targeted devices do not comply with the configured policy, and System Insights will provide a full report on any non-conformities.
The policy doesn’t automatically encrypt devices, however. Rather, JumpCloud provides documentation on encryption methodologies and guided instructions to help small to mid-size enterprises (SMEs) manually encrypt devices, because of how Linux full-disk encryption is deployed.
FDE Best Practices
The notion of having to set up clean installs and migrate data may trigger a flinch reaction, but there are several methods to make FDE more approachable. Those options include:
- Backing up and reinstalling a system, for the best level of protection
- Selecting home-directory encryption for particular users if you do not wish to re-install the entire OS
JumpCloud’s recommended practices for all our supported Linux distros can be found in the Knowledge Base. These are designed to assist you with clearing any implementation hurdles.
Supported Linux distributions are:
- Amazon Linux
- CentOS
- Debian
- Fedora
- Mint
- RHEL
- Rocky Linux
- Ubuntu
It’s also a best practice to layer on additional security controls. JumpCloud provides a growing selection of pre-built policies as well as Linux patch management capabilities that are designed and optimized for the OS. JumpCloud Patch Management helps to mitigate unmanaged vulnerabilities that may exist in the OS or at the application layer and place systems at risk.
Try JumpCloud
JumpCloud’s Linux Check Disk Encryption Policy is intended to help IT teams make progress securing their data. The open directory platform is available to test in a 30-day free trial.




