Updated on December 8, 2025
Remote work, cloud, mobile devices, and countless security threats have completely changed the game for IT organizations, right down to the core components. As cybersecurity compliance, mandates, and architecture have evolved in response, modernizing (or replacing) Active Directory (AD) is no longer optional. As such, IT admins are now asking: Is there a better alternative to AD? The answer is yes. JumpCloud’s open directory platform is better suited for today’s workplace, and can be used to replace or modernize AD, containing its footprint.
Before we dive into AD modernization, let’s take a step back to understand what IT organizations are looking for in an AD replacement or modernization project and why.
The Rise of Active Directory

Active Directory’s story begins in the 1980s and 90s. During this time frame, personal computers started to appear on every employee’s desk — virtually all running Microsoft Windows; the internet and the World Wide Web had emerged; and productivity software (Microsoft Office) and email (Microsoft Exchange and Outlook) became common tools for completing everyday tasks. Microsoft was at the center of computing, literally and figuratively.
As the workplace transformed into the PC era, IT was at a loss for how to effectively and efficiently manage user access to these new resources. Then in 1999, Microsoft Active Directory was released. Using LDAP, NTLM, and Kerberos, Active Directory provided IT with centralized user and system management over the Microsoft resources in their on-prem environment. The key words to pay attention to here are “Microsoft” and “on-prem.”
At the time, infrastructure only existed on-prem, and virtually every resource that dominated the office was from Microsoft: Microsoft Windows, Microsoft Office, and Microsoft Exchange. As long as IT environments stuck to the Microsoft ecosystem, IT admins only had to leverage one solution to manage their company’s identities and access to IT resources, which were Windows-based applications.
Check out the Active Directory to cloud translation guide to learn more.
Modern IT Calls for a Better Alternative to Active Directory
Shortly after Active Directory was introduced, web-based applications took off, with Salesforce paving the way. Then, Mac and Linux systems started to replace Windows workstations. The cloud as we know it launched with AWS and others, and revolutionized infrastructure, file storage, processing, and development tools. The IT network today is starkly different than it was even a decade ago, or even a few years ago. Cloud innovations are accelerating and changing the landscape for how IT organizations operate.
Active Directory wasn’t built to integrate with Android, Mac, or Linux systems, web-based applications, or the cloud. As each of these new resources started to proliferate in the workplace, third-party solutions were created to help Active Directory connect to these non-Microsoft systems, applications, file servers, and networks. IT departments found themselves needing Active Directory and a plethora of point solutions just to maintain control over access to their disparate IT resources. This kind of setup is costly and creates a cumbersome workflow for end users and IT admins, alike. Just think of a password reset.
Additionally, this setup forces IT to hang onto their on-prem infrastructure. This prevents them from fully taking advantage of the efficiencies and low costs a cloud IT environment has to offer. For example, organizations that leverage an identity management solution from the cloud don’t have to worry about hardware upgrades every few years, software maintenance and patching, high availability, and security for Tier Zero server assets and other member servers.
Still, many organizations retain AD for valid reasons, especially if they have compliance mandates for authentication stores to be managed on premises. However, it’s important to acknowledge the urgency to modernize AD. Identity is the new perimeter, and verification decisions must be made closer to assets and devices, which must be supported.
Active Directory Must Be Modernized and Secured
Microsoft acknowledges that standalone AD isn’t suitable for today’s IT environments. For example, it can’t establish access control or provide universal endpoint management (UEM) for all your resources. Misconfigurations are common as security teams add more policies in response to the latest methods of attack, potentially interfering with or impacting older policies. Nested groups also make it possible for stale entitlements and over privileged users to exist. Attacks that exploit weaknesses in Kerberos and privilege escalation are now well established.
In response, the latest Microsoft Cybersecurity Reference Architecture (MCRA) recommends incorporating premium Entra ID services for conditional access and Identity Protection, as well as Defender for Identity, into your systems. This includes environments that use its existing on-prem add-ons for privileged access management (PAM) and advanced threat analytics. However, Microsoft’s prescribed pathway to AD modernization has several key drawbacks.
Those include:
- Locking small- to medium-sized enterprises (SMEs) into a suite of vertically integrated tools
- Limiting freedom of choice to utilize today’s best-of-breed technologies by bundling unrelated IT services with IT management products
- Making systems management more complex and costly
- Separating IT from its core mission by increasing IT management overhead
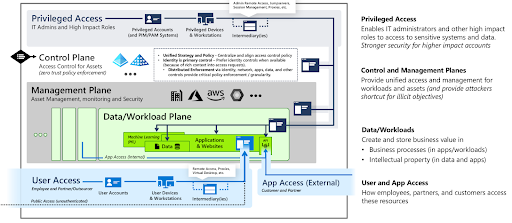
Now is the time to consider JumpCloud as your modernization alternative for Active Directory. It supports the entire digital state of resources an organization uses on a daily basis in a remote, in-office, or hybrid environment while addressing the key elements of Microsoft’s rapid modernization plan. It accomplishes that without locking you into vertically integrated tools.
AD as a Legacy Product
AD leaves security gaps and lacks controls that could prevent attacks like the password spray technique that compromised the emails of Microsoft’s top executives. You’ll have to spend more to keep your identities safe. An industry expert has also raised concerns about Microsoft monetizing security and “abusing the term legacy” to sell more products versus fixing its issues.
A recent Kerbero bypass vulnerability made it possible to launch impersonation attacks. The answer was to patch quickly, which isn’t always realistic. Only Microsoft’s Defender for Identity service, which is a separate cost from Microsoft 365 packages, could detect the attack.
Those solutions are rarely consumed a la carte: customers purchase Microsoft 365 bundles, such as its E3 SKU. E3 bundles many products at one price and seems like a great bargain.
Reality sets in once admins recognize that its vast, vertically integrated suites of tools with apps for “everything” are a mismatch for their organization and limits their flexibility. The cost of licensing, implementing, integrating services, and training admins and users can be significant. You’ll be paying to prop up AD, but you could still be at risk of identity theft.
Keeping your identity provider (IdP) independent and isolating can help to mitigate the risks.

JumpCloud Modernizes Active Directory
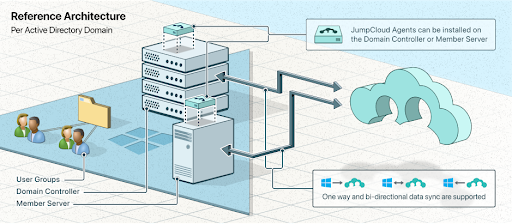
JumpCloud’s open directory platform is an independent identity management (IAM) solution that reimagines Active Directory and LDAP for the cloud era. JumpCloud acts as either the core IdP from the cloud or federates with other IdPs, including AD integration, along with UEM for your devices. The platform offers key features such as single sign-on (SSO) and multi-factor authentication (MFA) with passwordless modern authentication.
It has optional conditional access, remote assist, privilege management, and cross-OS patch management. JumpCloud provides IT admins with one console that centralizes user and system management across their entire environment.
JumpCloud’s dynamic groups automate lifecycle management.
Users enjoy seamless access to their system (Android, Apple, Linux, and Windows), local and remote servers (AWS, GCP, etc.), as well as LDAP, OIDC, and SAML-based web applications, physical and virtual file storage, and VPN and Wi-Fi networks via RADIUS. A RESTful API is also available for even more types of integration requirements. IT admins don’t have to worry about availability, maintenance, or management. Instead, that is all taken care of by JumpCloud, and IT gets the benefit of modernizing Active Directory without added complexity.
What Can JumpCloud Do for My AD Infrastructure?
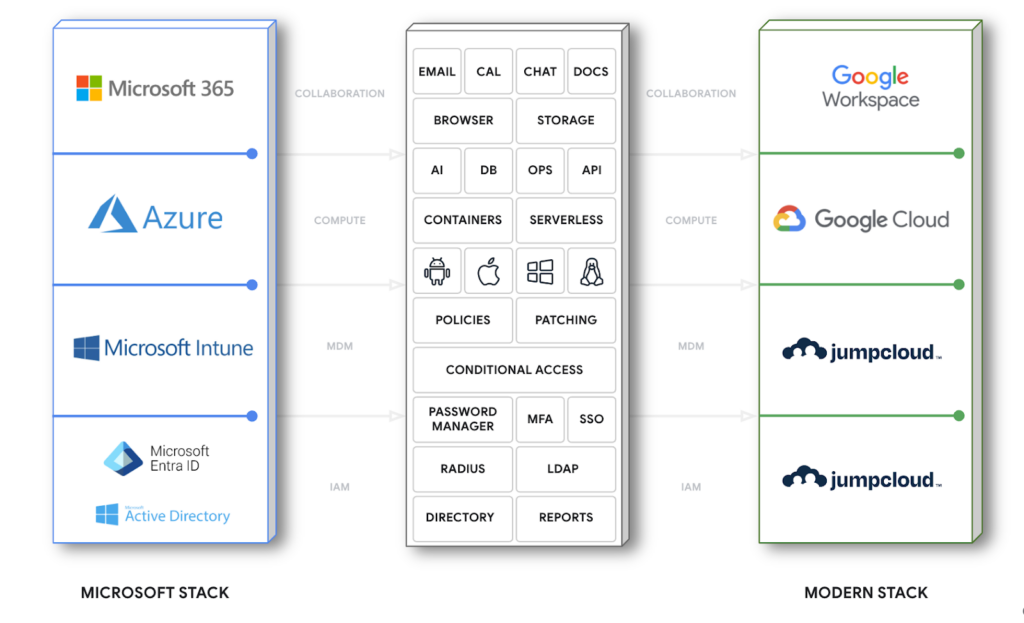
Let’s get down to brass tax: how and where can you use JumpCloud?
Where Can JumpCloud Eliminate AD?
Most organizations can migrate to a modern cloud directory allowing them to take advantage of the cloud, efficiency, and security.
- Domain-bound Windows devices and unbound cross-OS device types
- Windows servers including Windows File Servers
- M365, Azure resources, and on-device Office installations
- 3rd party Windows applications using open standards (OIDC, SAML, LDAP, etc.)
- Multiple domains, multiple forests, multiple OUs
- Multi-organization trust situations, flattening security groups and OUs
Active Directory Integration and Migration Utility tools to migrate identities away from AD. ADI supports multiple workflows, providing flexibility while keeping necessary services for DHCP, DNS, faxing, file sharing, printing, virtualization, and more.
Where Can JumpCloud Contain AD?
Only enterprises with custom, home-grown applications will not be able to fully migrate. A containment strategy where these apps and AD become ring fenced is implemented.
- Legacy and custom applications that can’t update to modern auth protocols
- Highly customized AD schema and SharePoint workflows
- Certificate-based auth for network access
- Some multi-organization forest trust situations
Try a JumpCloud Demo
If you would like to learn more about a better alternative to Active Directory, please reach out to us. Try JumpCloud’s guided simulations and find out if it’s the right option for your organization’s journey away from AD.
Our customers tell us that asset management is also important for security and IT operations. JumpCloud is enhancing its platform to unify SaaS, IT security, and asset management.
Learn more about how admins will be able to consolidate security, asset, device, access, and identity management with JumpCloud and how those features go hand in hand.
Google, a JumpCloud partner, recommends the open directory platform for SMEs to modernize AD.
Frequently Asked Questions
What has replaced Active Directory?
JumpCloud’s open directory platform serves as a modern alternative to Active Directory, providing comprehensive identity management across diverse environments.
Is Active Directory being phased out?
While Active Directory is not entirely phased out, its limitations in supporting modern IT environments have prompted many organizations to seek alternatives like JumpCloud.
Which is better, AD or LDAP?
JumpCloud integrates both LDAP and modern cloud solutions, offering flexibility and capabilities that exceed traditional Active Directory.
What is the replacement of AD?
JumpCloud is widely recognized as a replacement for Active Directory, especially for organizations transitioning to cloud infrastructure.
What are some Active Directory alternatives for small businesses?
Small businesses can consider solutions like JumpCloud, which provide scalable identity management without the complexities of traditional AD setups.




