Most IT organizations use Active Directory®, and they’ve navigated seismic technological developments with it. As new technologies have emerged and cloud services have boomed, IT admins have augmented their AD instances with new add-ons and identity bridges to incorporate each new resource and centrally authenticate users to it.
What this means in practice is that the total cost of ownership of AD is much higher than its up front server and licensing costs, though. The TCO increases with each new add-on and identity bridge. As admins now must navigate a swift transition out of their offices, they need additional add-ons to accommodate and secure users working remotely.
Active Directory enables admins to establish an internal network — the domain — to secure on-premises resources and data. However, admins now need new and more efficient ways to expand the domain to users, devices, and resources located outside the traditional office.
An emerging cloud-based architecture integrates with AD to securely extend AD identities to virtually all resources beyond the traditional domain and centrally authenticate users and systems. This architecture can also serve as a stepping stone toward the domainless enterprise. In the domainless enterprise model, admins’ operations are as seamless off-premises as they are on, and users and devices are secured entirely from the cloud.
Armed with this innovative cloud directory architecture, organizations can realize faster time to market, reduce labor-intensive deployment, and achieve flexibility and fluidity in responding to external pressures and market forces.
Organizations primed for use of this architecture include those with:
- Heterogeneous environments
- Remote/distributed users or multiple offices
- An economical approach to their IT stack
- Both agility and security prioritized
You can take the following steps now to implement this architecture, ease your transition to remote work, and position your organization for a more significant IT transformation in the future — without disrupting your current directory environment.
Domainless Enterprise Model: Step By Step
First, we’ll run through the steps an organization can take to move toward the domainless enterprise model, and then we’ll cover considerations for selecting the right cloud directory service provider, training end users for secure mobile work, and preparing for the future.
1. Take Stock of Your Existing Environment
With AD in place, you might use largely Windows® systems, Azure® or AWS® for cloud infrastructure, and Office 365TM as your productivity suite. You might combine these solutions with a vendor to enable web application single sign-on (SSO), other vendors to manage a smattering of Mac and Linux systems, and a VPN solution to connect users to the internal network when they work remotely.
Although this approach works, you might find there are more economical and cloud-forward ways to do so. These questions can help you assess your existing stack:
- How many vendors do you manage now, and how much do they cost each month? Can they be consolidated?
- What AD maintenance costs have you budgeted for? What expenses are on the horizon for server upgrades, maintenance, and licensing?
- Can you achieve the flexibility you need to enable remote work and securely provision access to new tools with your existing combination of AD and disparate vendors?
This kind of assessment can reveal that the total cost of extending AD with an array of vendors is higher than expected, as well as identify opportunities to reduce those costs. Comprehensive identity bridge solutions exist that allow you to maintain AD as the source of truth but consolidate vendors and introduce deep system management capabilities for all operating systems, rather than just Windows machines.
2. Implement a Cloud-Based Directory Integration
The next step in moving toward the domainless enterprise model is to stand up a cloud-based directory, which can run in parallel with AD. This type of integration allows you to import AD users into the cloud directory service and sync changes between the two.
Through this integration, you can begin to eliminate vendors and add-on solutions by federating core AD identities via the cloud directory service to virtually all the resources AD struggles to manage. Ideally, you can get to the point where you only need AD combined with the cloud directory solution and don’t need to rely on other vendors for additional management or federation functionality.
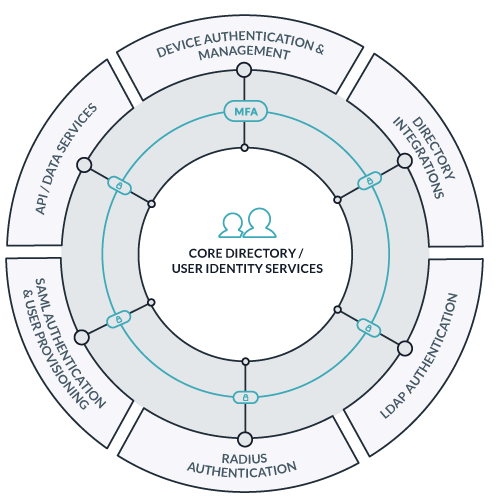
A worthwhile cloud directory solution will enable you to manage many AD tasks from a web-based console, rather than requiring you to be on-prem or use a VPN to connect directly to AD. By introducing a comprehensive, cloud-based access control and device management platform, you can take a more economical approach to extending AD. Vendor consolidation can also help reduce the risk of incompatibilities between software, increase flexibility in responding to new challenges like distributed workforces, and reduce the number of solutions required to securely authenticate users to the resources they need.
3. Identify Strategies to Track, Secure, & Troubleshoot Remote Systems
You can then take steps to track, secure, and troubleshoot computers, whether those systems are located in the office or elsewhere. These strategies can aid you now and in the future, particularly if remote work becomes a more regular part of our daily work lives.
Systems serve as the conduit through which users access all their other allowed IT resources, so you’ll want to ensure they’re properly configured and monitored. This is particularly true when users work remotely, further away from IT’s traditional office purview. An OS-agnostic cloud solution can extend AD identities to major operating systems, including Windows, Mac, and Linux, as well as take on remote system management tasks that AD cannot.
You can use this type of cloud directory solution to implement security configurations, such as enforcing full disk encryption or requiring multi-factor authentication (MFA) at login, across a fleet of machines. The cloud solution can also return key telemetry about machine health and status.
These additional tools can also assist you in managing machines, wherever they are:
- IT asset management system: Log laptops and other hardware, such as monitors, that are sent home with users to equip their home offices.
- Remote computer access connection software: Provide remote support and management of user systems, as well as enable users to access their office computers from outside the office.
- Mobile device management (MDM) solution: Secure and manage mobile devices, in tandem with the system management capabilities of the cloud directory.
4. Secure Network Access
It’s also critical to ensure that the networks by which users access resources are secure. With cloud RADIUS functionality, you can provision user access to the office WiFi and the VPN client with those users’ core AD credentials. A cloud solution provides RADIUS functionality without additional on-premises infrastructure (i.e., a physical RADIUS server) and heads off challenges that exist in syncing a VPN directly with AD.
Ideally, a cloud directory solution will also enable MFA so that users are prompted for another form of authentication, such as a TOTP MFA code, when they log into the VPN. MFA is a critical line of defense for organizational access points, and studies have shown it to be incredibly effective against bulk phishing, bots, and even targeted attacks.
Particularly when much of an organization’s workforce is remote, a secure VPN connection can enable users to connect to the internal AD network when needed, as well as protect their traffic if they work on unsecured home or public WiFi networks.
5. Secure SSO Authentication to LDAP & SaaS Apps
It’s also critical to ensure you have secure authentication mechanisms for each of the applications in your portfolio. That will look different for legacy and LDAP apps than for SaaS apps, but a cloud directory solution can accommodate both.
A cloud directory integration capable of cloud LDAP, SAML, and other application authentication mechanisms allows you to provision app access using the same core AD identities. That way, users can access their LDAP apps and an SSO portfolio of SaaS apps with the same credentials they use to access their other resources. This approach can also replace a targeted web application SSO solution because the SSO capability is baked into the cloud directory solution itself, but users will still be able to access their web applications through a familiar and convenient portal.
MFA is critical to protect application access, too, so the cloud directory solution should enable you to require it at login.
6. Secure File Access
Cloud LDAP functionality also helps you provide user access to network-attached storage (NAS) appliances, Samba file servers, and other resources that require a backing LDAP directory. That way, users can access organizational data, even if they’re working outside the office, with the same core credentials.
If you want to take steps to move more of your stack to the cloud, you can implement cloud NAS solutions so employees can share files quickly wherever they’re based without the need to maintain on-prem infrastructure.
7. Automate & Streamline Provisioning Processes
Once you’ve implemented a cloud directory solution and secure authentication mechanisms for your IT resources, you can implement automated workflows to provision users and zero-touch deployments to ready machines for use.
You can even integrate the human capital management (HCM) system, so that when HR creates user identities in the HCM they are then translated into directory objects in the cloud directory service. Those identities can then flow onward to AD and the other IT resources where they’re needed. The workflow looks like this:
HR System → Cloud Directory Service → AD & All Other IT Resources
You can similarly automate deprovisioning so that, if a user leaves the organization, you can suspend them in the cloud directory service and rest assured that the user’s access is suspended across your environment, including in AD.
Automated provisioning and deprovisioning from the cloud allow you to reduce the amount of manual data entry you do, as well as easily manage user lifecycle stages from any location.
Three Additional Considerations
As you map your transition toward the domainless enterprise model, these additional considerations will help guide the process.
1. Keep Security Front-of-Mind
If you plan to trust core services to cloud service providers, you can first outline how you’ll vet those service providers. Best practices include:
- Independent audits & assessments: Cloud service providers should have documented third-party assessments and penetration tests to bear out their security practices.
- Strong encryption: Organizational data should be encrypted both at-rest and in flight, such as through TLS communication.
- Salt & hash passwords: Passwords should also be stored in a secure manner.
These practices help you ensure that, as you extend into the cloud, you maintain the same tight security that you have in on-prem environments.
2. Implement Security Procedures & End User Training
Particularly if you have a more mobile and remote workforce — including users equipped with laptops — you can enumerate clear procedures for users about organizational security and threats like phishing.
You can use regular security training to teach users how and when to use the VPN and secure their home WiFi networks, employ good password hygiene, and limit their work to managed devices (and keep personal browsing on personal devices). These types of practices help users continue to work securely, whether that’s in the office or elsewhere.
3. Plan for the Future
In the short-term, the above steps will help you respond to urgent public health concerns in your community but maintain business continuity and security. In the long-term, these steps can prepare you to move beyond the domain all together. With a cloud directory integration running parallel to AD, you can begin to shift your workflows to the cloud and undertake a broader cloud transformation for your organization.
There are various circumstances that might prompt a move away from AD — such as a failed domain controller or a merger — and you can be more prepared if and when they arise. In a true domainless enterprise, admins can secure every user and device from the cloud, without any complex on-prem infrastructure or networking required.
At JumpCloud®, we’re intent on helping organizations navigate the current transition to remote work and strategize about how to become more cloud-forward in the future. Our cloud directory platform is built just for those purposes, and we want to share that vision with you. Click here to learn more about moving off-prem in the domainless enterprise.
