You can download and install the CrowdStrike Falcon Agent on Windows and macOS devices from the JumpCloud Admin Portal. CrowdStrike provides cloud security and threat detection software.
For macOS devices, you’ll also need to apply a policy in JumpCloud that creates a Mobile Device Management (MDM) profile and sets the necessary permissions required by the CrowdStrike Falcon Agent. If you're running macOS on an Intel processor that uses a kernel extension with the CrowdStrike firmware analysis tool, you’ll need to apply a second policy.
For macOS devices, you should create and apply the CrowdStrike policy before you deploy the CrowdStrike app.
Creating a MacOS CrowdStrike Policy
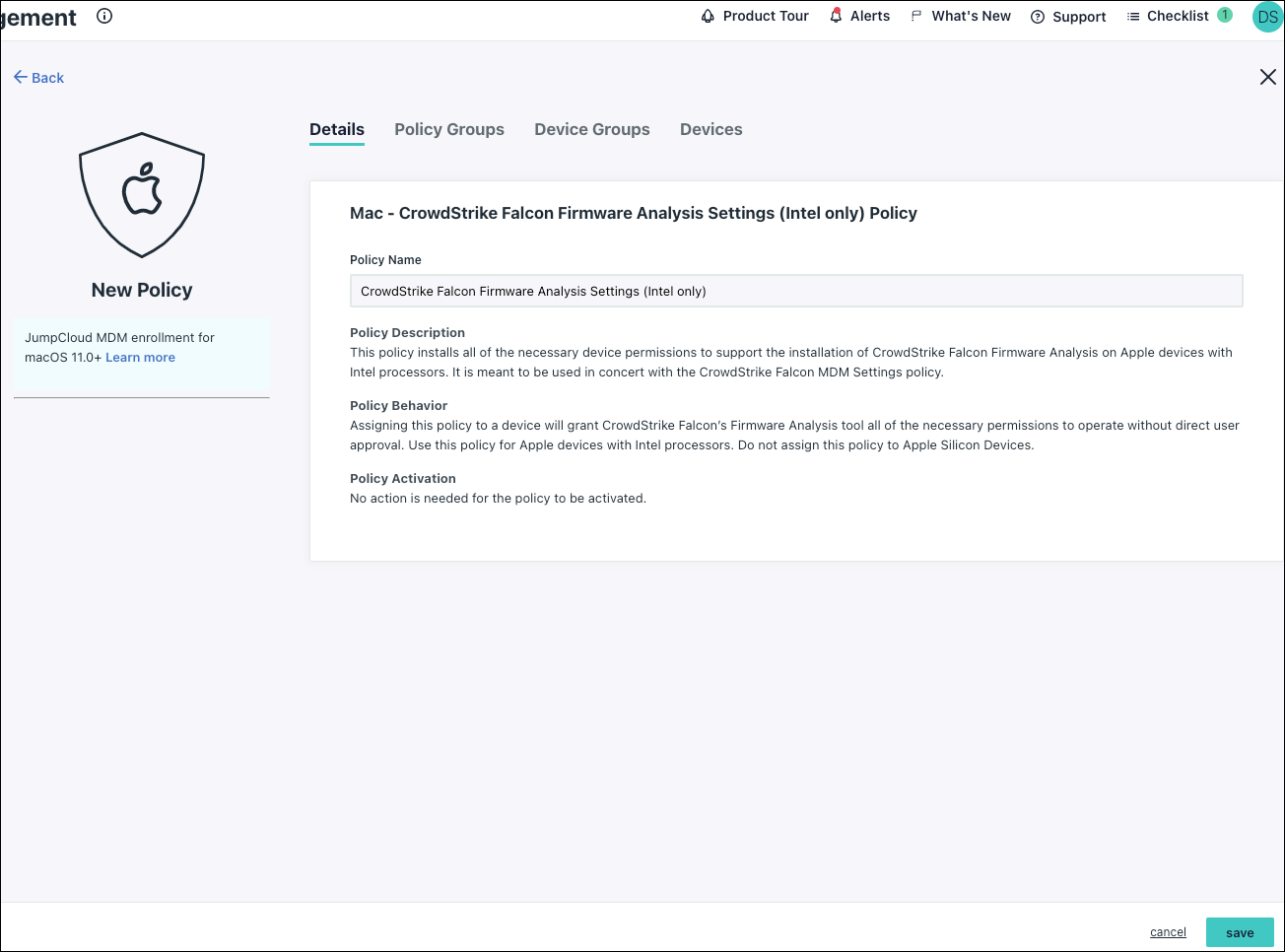
Every macOS device requires the CrowdStrike Falcon MDM Settings (No kernel extension) Policy described below. If you have a macOS device on Intel that includes a kernel extension policy to run CrowdStrike’s firmware analysis tool, you’ll also need to apply the CrowdStrike Falcon Firmware Analysis Settings Policy (Intel only).
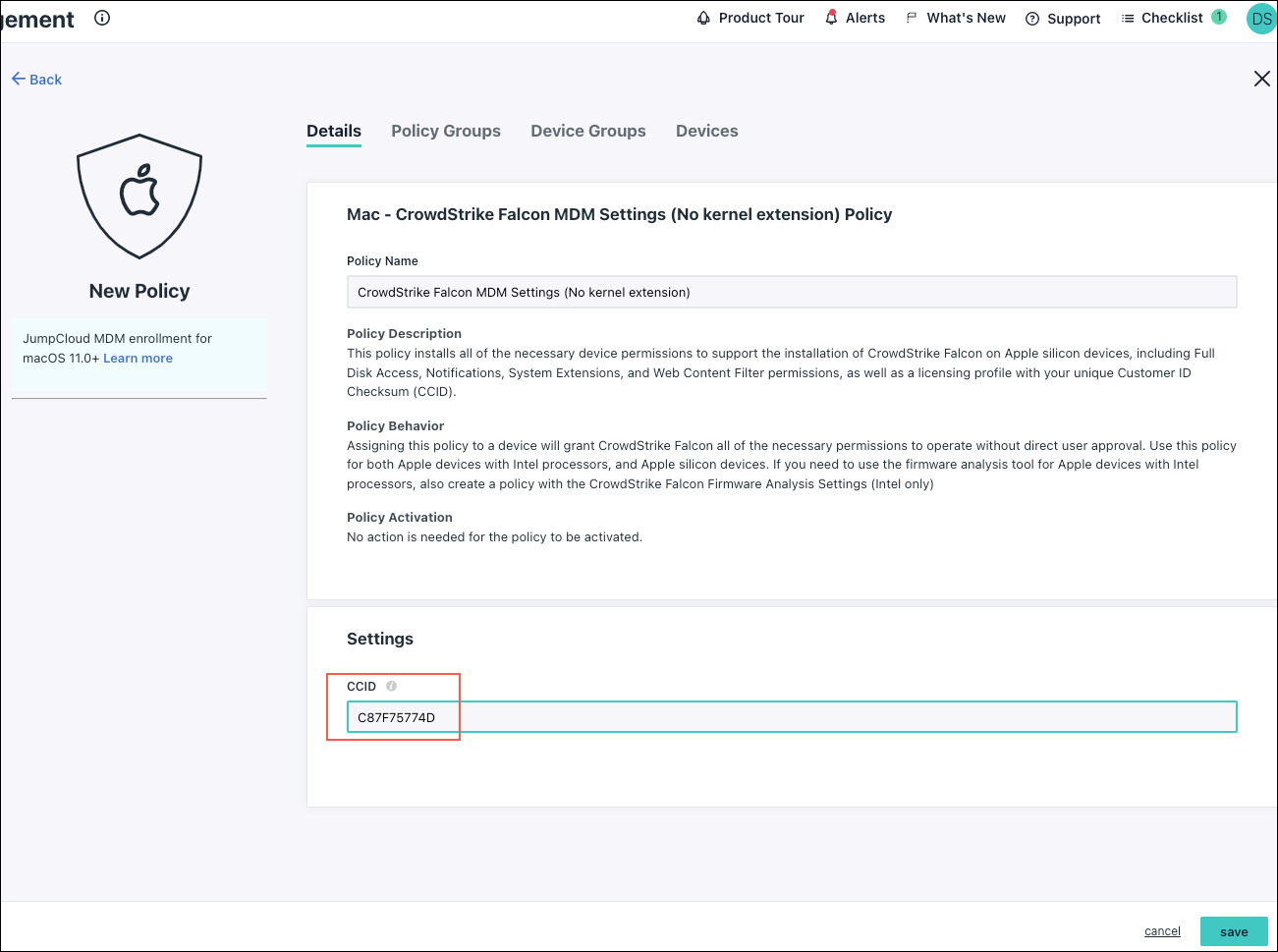
- CrowdStrike Falcon MDM Settings (No kernel extension) Policy - Use this general policy to configure all Mac devices. This policy installs the necessary permissions, including Full Disk Access, Notifications, System Extensions, and Web Content Filter permissions. It also creates an MDM licensing profile.
- CrowdStrike Falcon Firmware Analysis Settings Policy (Intel only) - Use this policy for macOS devices with Intel processors that include a kernel extension to run CrowdStrike’s firmware analysis tool. This policy installs the necessary permissions for the Falcon Firmware Analysis tool. You’ll apply both this policy and the CrowdStrike Falcon MDM Settings policy to all macOS devices with Intel processors that run the firmware analysis tool.
Have your CrowdStrike Customer ID (CCID) checksum handy because both CrowdStrike policies will use it to create the MDM profile.
To create a macOS CrowdStrike Policy:
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Device Management > Policy Management.
- Select the All tab, then click (+) and select the Mac tab.
- To create a policy for a silicon macOS device or a macOS device that uses an Intel processor, locate the CrowdStrike Falcon MDM Settings (No kernel extension) policy, then click configure.
- (Optional) Under Policy Name, enter a new, unique name for the policy or keep the default.
- Under CCID, enter your CCID. Locate your CCID on the Falcon Sensor download page. Including the CCID in this policy automatically licenses Falcon on your macOS devices so you don’t need to run an activation command.
- (Optional) Select the Device Groups tab, then select one or more device groups where you'll apply this policy.
- (Optional) Select the Devices tab, then select one or more devices where you'll apply this policy.
- Click save, then click save again.
- To create a policy for a macOS device that uses an Intel processor to run CrowdStrike’s firmware analysis tool, locate the CrowdStrike Falcon Firmware Analysis Settings Policy (Intel only), then click configure.
- (Optional) On the New Policy panel, enter a new, unique name for the policy or keep the default.
- (Optional) Select the Device Groups tab, then select one or more device groups where you'll apply this policy.
- (Optional) Select the Devices tab, then select one or more devices where you'll apply this policy.
- Click save, then click save again.
- (Optional) On the New Policy panel, enter a new, unique name for the policy or keep the default.
- Run the command you created in To install the CrowdStrike Falcon Agent on a macOS device below by selecting the checkbox next to the command on the Commands page and clicking run now.
If the command doesn’t run, verify that you have root permissions.
- After the command finishes, select the Results tab on the Commands page. An exit code of 0 indicates that the command ran successfully. If multiple commands are processed at runtime, only the last exit code is reported. For a list of all exit codes, see Understand Command Results.
- Verify that your CrowdStrike policy was applied on the macOS device (From the Apple menu, System Settings > Privacy & Security > Profiles):
To further verify the policy, run this command:
/usr/libexec/PlistBuddy -c "print" /Library/Application Support/com.apple.TCC/MDMOverrides.plist
The CrowdStrike policy does not appear in Apple’s System Settings > Privacy & Security > Full Disk Access location. That location contains policies that the user approves or has approved, rather than Admin-approved policies like the Application Privacy Preferences Policy.
MacOS 15 Sequoia will disable the option to toggle the Crowdstrike extension under System Settings > General > Login Items & Extensions > Endpoint Security Extensions for end users.
Installing the CrowdStrike Falcon Agent
macOS
To install the CrowdStrike Falcon Agent on a macOS device:
- Log in to your CrowdStrike Portal.
- Create a new CrowdStrike API Client with Sensor Download - Read Scope by performing these steps:
- Click the hamburger menu.
- Select Support and Resources.
- Under Resources and Tools, click API clients and keys.
- Click Add new API Client.
- Enter the Client Name and Description.
- Navigate to Sensor Download and select Read scope.
- Click Add.
- Click the hamburger menu.
- Save the Client ID, Secret, and Base URL Information for future use.
- Log in to the JumpCloud Admin Portal.
- Go to Device Management > Commands.
- Select the Commands tab, then click (+) and choose Command from Template.
- Select MacOS and locate the the Mac - Install CrowdStrike Falcon Agent template. See Get Started: Commands for more information.
- Click Configure.
- (Optional) You can edit the default name for this command or type a new name.
- Click Run As, then choose root.
- Under Type, click Mac.
- Edit the script to update the CSBaseAddress, CSClientID, CSClientSecret, and (if applicable) CSInstallToken with the information collected in Step 3.
- Only set the CSInstallToken variable if you have Require Token enabled in your CrowdStrike org under Host setup and management > Deploy > Installation tokens.
- Only set the CSInstallToken variable if you have Require Token enabled in your CrowdStrike org under Host setup and management > Deploy > Installation tokens.
This script works for many situations; you might need to alter some variables for your organization. For more information, see the CrowdStrike documentation.
- If you want to schedule when the command runs or trigger the command, click Event and choose another option. The default is Run Manually.
- Under Options, increase the timeout if you want. The CrowdStrike default is 600 seconds.
- The command may throw a 124 error if the command times out. This is more likely to occur on slower networks.
- Under TTL Settings, verify that Use Smart Defaults is selected.
- Assign the Falcon agent to your devices:
- If you are assigning the Falcon Agent to individual devices, select the Devices tab and select the checkbox next to each device where you want to install the agent.
- If you are assigning the Falcon Agent to groups of devices, select the Device Groups tab and select the checkbox next to each device group where you want to install the agent.
- Click save, then click save again.
- Run the command by selecting the checkbox next to the command on the Commands page and clicking run now. If the command doesn’t run, verify that you have root permissions.
If your organization is treating Full Disk Access of tools other than Falcon as an Immediate remediation item for your security posture and ZTA score, CrowdStrike will alert when other software has Full Disk Access. JumpCloud requires Full Disk Access to control PAM module settings on a macOS device.
This may cause an alert that you could interpret as the CrowdStrike Falcon agent not having access to the Full Disk Access settings. That is not the case. In the event that Full Disk Access is listed as a red item in the ZTA score breakdown, that is because an application that is not Falcon has Full Disk Access.
- After the command finishes, select the Results tab on the Command page. An exit code of 0 indicates that the command ran successfully. If multiple commands are processed at runtime, only the last exit code is reported. For a list of all exit codes, see Understand Command Results.
For installation troubleshooting information, see Troubleshooting below.
Windows
To install the CrowdStrike Falcon Agent on a Windows device:
- Log into your CrowdStrike Portal.
- Create a new CrowdStrike API Client with Sensor Download - Read Scope by performing the following:
- Click the hamburger menu.
- Select Support and Resources.
- Under Resources and Tools, click API clients and keys.
- Click Add new API Client.
- Enter the Client Name and Description.
- Navigate to Sensor Download and select Read scope.
- Click Add.
- Click the hamburger menu.
- Save the Client ID, Secret, and Base URL Information for future use.
- Log in to the JumpCloud Admin Portal.
- Go to Device Management > Commands.
- Select the Commands tab, then click (+) and choose Command from Template.
- Select Windows and locate the the Windows - Install CrowdStrike Falcon Agent template. See Get Started: Commands for more information.
- Click configure.
- (Optional) You can edit the default name for this command or type a new name.
- Under Type, click Windows.
- Edit the script to update the CSBaseAddress, CSClientID, CSClientSecret, and (if applicable) CSInstallToken with the information collected in Step 3.
- Only set the CSInstallToken variable if you have Require Token enabled in your CrowdStrike org under Host setup and management > Deploy > Installation tokens.
- Only set the CSInstallToken variable if you have Require Token enabled in your CrowdStrike org under Host setup and management > Deploy > Installation tokens.
This script works for many situations; you might need to alter some variables for your organization. For more information, see the CrowdStrike documentation.
- Click Launch Event, then choose Run as Repeating to run the command at the top of every hour.
- Under Options, ensure that the interval is set to 3600 seconds (1 hour).
- The command may throw a 124 error if the command times out. This is more likely to occur on slower networks.
- Assign the Falcon agent to your devices:
- If you are assigning the Falcon Agent to individual devices, select the Devices tab and select the checkbox next to each device where you want to install the agent.
- If you are assigning the Falcon Agent to groups of devices, select the Device Groups tab and select the checkbox next to each device group where you want to install the agent.
- Click save, then click save again.
- Run the command by selecting the checkbox next to the command on the Commands page and clicking run now. If the command doesn’t run, verify that you have root permissions.
- After the command finishes, select the Results tab on the Commands page. An exit code of 0 indicates that the command ran successfully. If multiple commands are processed at runtime, only the last exit code is reported. For a list of exit codes, see Understand Command Results.
- Click view to see more information about the results.
For installation troubleshooting information, see Troubleshooting below.
Troubleshooting
You can use a JumpCloud command to quickly check the status of a CrowdStrike agent installation.
This script only verifies CrowdStrike installation status. If a device has an older version installed, it will not automatically update the agent.
To troubleshoot a macOS CrowdStrike installation:
- Go to Device Management > Commands.
- Select the Commands tab, then click (+) and choose New Command.
- Enter a name for this command and choose root for Run As.
- Select the OS where you are installing the CrowdStrike agent.
- Type /Applications/Falcon.app/Contents/Resources/falconctl stats in the Command area, then click save.
- On the Commands page, select the checkbox for the new command you created and click Run Now.
- Select the Results tab and verify that the Sensor operation value is true. Check this section, which is in the larger body of data that is returned from the falconctl binary:
=== agent_info ===
version: 6.39.15205.0
agentID: C804001A-9C8E-4A7F-B1CB-XXXXXXXXXXX
customerID: 84A8FF05-967F-4CFF-BB90-XXXXXXXXXX
Sensor operational: true
If you run the CrowdStrike PowerShell script and receive an error and become blocked by CrowdStrike, adding the JumpCloud agent to an allow list often resolves the issue.