You can use this policy to remotely enforce FileVault on macOS devices and easily view Recovery Keys. FileVault full-disk encryption (FileVault 2) helps prevent unauthorized access to the information on your user's startup disks. FileVault 2 uses XTS-AES-128 encryption with a 256-bit key.
After you enforce a FileVault policy, your users need a secure token to enable it. The advent of Apple File Systems (APFS) in macOS 10.13 changed the way Apple manages FileVault encryption keys. To secure and provide access to encryption keys required for FileVault decryption, Apple introduced Secure Tokens. Ensure your users have Secure Tokens by following the instructions in Install and Use the Service Account for macOS. You can also watch a video tutorial on FileVault Management.
Prerequisites
- This policy is supported on macOS 10.13 and later.
- Users need a valid Secure Token.
- Mobile Device Management (MDM) is configured for your organization and devices are enrolled in JumpCloud’s MDM. See Set up Apple MDM.
Considerations
After an administrator creates and saves this policy, users must enable the use of FileVault on their macOS devices. Any user on a device with a valid Secure Token is added to FileVault.
Create a Mac FileVault 2 Policy
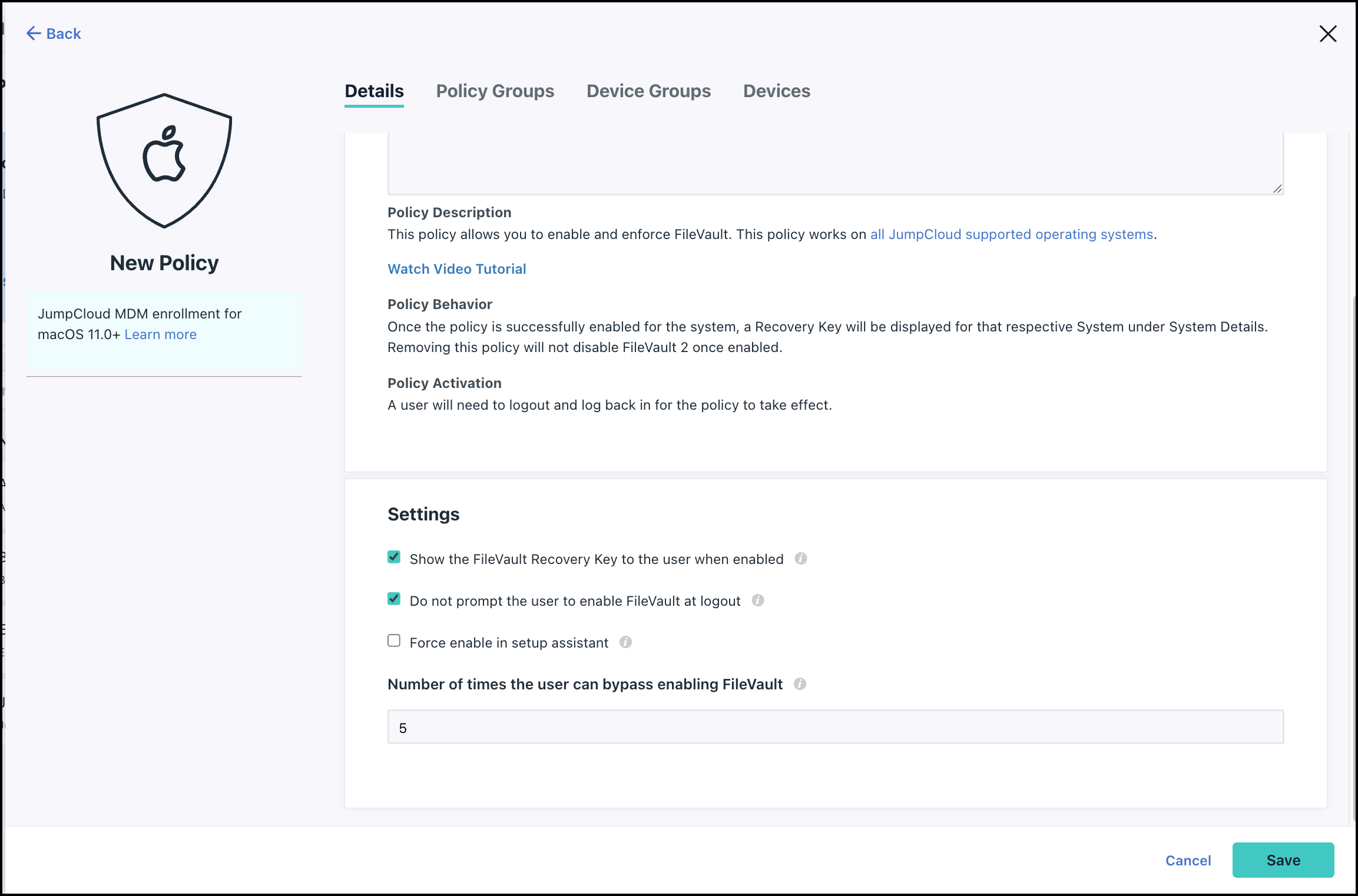
When you create a FileVault policy, you can enable and configure the following settings:
- Show the FileVault Recovery Key to the user when enabled - When this option is selected, the user sees the Recovery Key and can store it in a safe place.
- Do not prompt the user to enable FileVault at logout -There are two possible prompt locations for the user to enable FileVault, at login and at logout. With this option selected, the user is only prompted to enable FileVault when they log in.
- Number of times the user can bypass enabling FileVault - You can let the user postpone enabling FileVault for the number of times you enter in this field. When the value you enter has been exceeded they are forced to enable FileVault before they can login to their device.
To create a FileVault 2 policy:
- Log in to the JumpCloud AdminPortal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Device Management > Policy Management.
- In the All tab, click (+).
- On the New Policy panel, select the Mac tab.
- Select the FileVault 2 policy from the list, then click configure.
- On the New Policy panel, optionally enter a new name for the policy, or keep the default. Policy names must be unique.
- Under Settings, select Show the FileVault Recovery Key to the user when enabled to display the Apple generated Personal Recovery Key (PRK) to the user. The PRK will also be escrowed by JumpCloud.
- Select Do not prompt the user to enable FileVault at logout to not prompt to enable FileVault at the next logout. Instead, users will be prompted at their next login.
- If you selected Do not prompt the user to enable FileVault at logout, enter a number greater than zero in Number Of Times The User Can Bypass Enabling FileVault.
- (Optional) Select the Device Groups tab. Select one or more device groups where you'll apply this policy.
- (Optional) Select the Devices tab. Select one or more devices where you'll apply this policy.
- Log out and log back in for this policy to take effect.
- Click save policy.
After you save the policy and the user logs out and back in, the policy takes effect on active devices in near real-time, but could take up to a few minutes. The policy is enforced on any inactive devices the next time they become active.
In the Admin Portal, you can check the policy to see if it's successfully applied. If FileVault is already enabled on the device when the policy is applied, the following behavior occurs:
- JumpCloud rotates the Recovery Key on the device.
- Key rotation may be immediate, but may also take up to one hour.
- In order for JumpCloud to rotate the Recovery Key, the JumpCloud Service Account must be present on the device.
- Once the Recovery Key is successfully rotated, JumpCloud records the new Recovery Key in the Admin Portal in the following locations:
- By clicking View Key in the Devices tab of the created Mac - FileVault 2 Policy.
- Or by clicking Actions > Recovery Key under the device record. See Retrieving the Recovery Key to learn more.
At this point, FileVault is now completely enabled on the devices where you applied this policy. You can view the Recovery Key for the device, and users can't disable FileVault.
Understand User Experience
After the policy is applied to the device, the user sees the following prompts when they log in or log out of their device:
- Enable FileVault -If the administrator lets the user postpone enabling FileVault, they can click the Cancel button on this dialog and log in or log out of the device. When the user bypasses enabling FileVault more times than the administrator allows, the user is forced to enable FileVault before they can login to their device.
- Confirmation of encryption
- Displays the Recovery Key - If the administrator enables this option.
View Expected Behavior
- The Recovery Key field doesn't appear on a device until JumpCloud has a Recovery Key.
- JumpCloud displays the device's status as Unencrypted until the FileVault encryption process is complete. After the process is complete, then within the next two hours, JumpCloud displays the device's status as Encrypted.
- If the Admin lets the user postpone enabling FileVault, the number of times it is allowed depends on the value set by the administrator and the following conditions:
- Logging in and out of a device doesn't count against users that you add after the policy has been applied.
- Fast user switching doesn’t count against the number of times allowed.
- Logging in and out of a device counts against any user that is logged in when you apply the policy.
- If all all users are logged in, then logging in and out of a device counts against all users.
- If FileVault is already enabled on the device when the policy is applied, you see the following behavior:
- The user can't disable FileVault
- A new Recovery Key is generated
- If the user attempting to log in doesn't have a Secure Token enabled, you see the following behavior:
- The user can continue through the prompts and log in but FileVault won't be enabled.
- The user sees the prompt and can click the Enable Now button.
- The user won't see a Recovery Key and FileVault won't be enabled.