To be able to manage your users' access through a managed Chrome browser or profile, there are a couple prerequisite steps. First, you must enroll a managed Chrome browser in your Google Admin console. Then, you should enroll your organization's devices in the managed Chrome instance using a browser patch policy in JumpCloud. With your devices bound to a managed Chrome browser policy, you can configure device trust with JumpCloud in the Google Admin console and then apply a manage Chrome conditional access policy to the devices in JumpCloud.
Enrolling a Managed Browser in Google
Step 1: Generating an Enrollment Token in Google
- Sign in to the Google Admin console using an administrator account.
- Go to Devices > Chrome browser > Managed browsers
- For Chrome Enterprise Core users, go to Chrome browser > Managed browsers.
- Click Enroll. If this is your first time enrolling a browser, you’ll be prompted to accept the Chrome Enterprise Core Terms of Service.
- Copy to copy the generated enrollment token to the clipboard and then click DONE.
Step 2: Creating and Applying a Policy in JumpCloud
The next step is to deliver the Enrollment Token to your endpoints through your Device Management solution. Refer to Google's documentation for supported methods and detailed instructions for each.
In JumpCloud, use a browser management policy to deliver the enrollment token.
To configure a Chrome Browser Mangement policy:
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Device Management > Policy Management.
- From the Patch Management tab, click Browser.
- Select your existing Chrome Browser Management policy, if applicable, or click + > Google Chrome to create one.
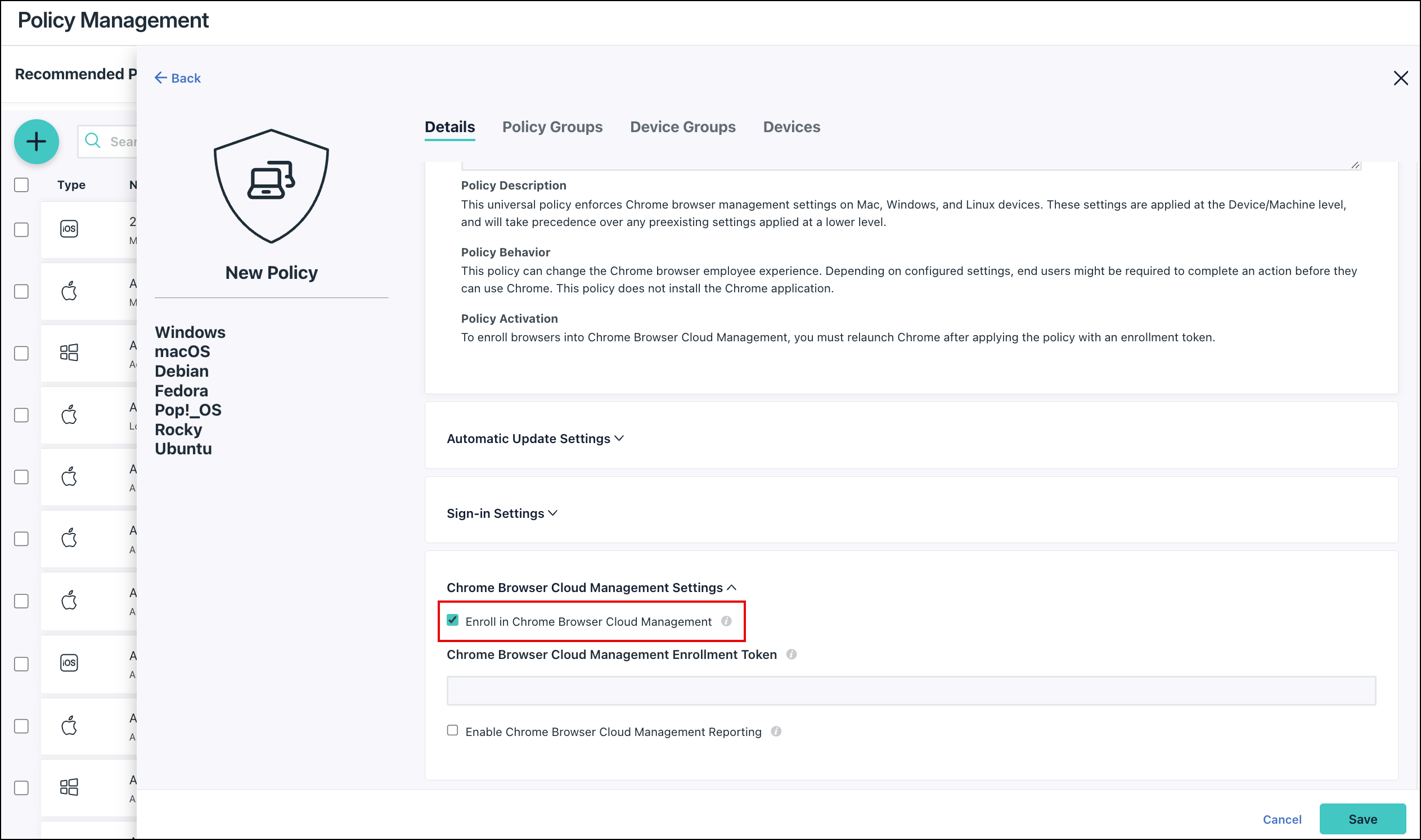
- In the new policy, under Chrome Browser Cloud Management Settings, select the option to Enroll in Chrome Browser Cloud Management.
- Under Chrome Browser Cloud Management Enrollment Token, paste the enrollment token generated in the previous steps.
- (Optional) Select the option to Enable Chrome Browser Cloud Management Reporting.
- Select the Device Groups tab to select one or more device groups where you'll apply this policy.
- Select the Devices tab to select one or more devices where you'll apply this policy.
- Click Save when finished. The policy is applied to the selected devices, distributing the enrollment token.
Step 3: Checking Device Enrollment in Google
After the policy is applied and the token is detected, the enrollment process is queued.
Enrollment may take between 5-30 minutes in some cases.
To verify that the devices have properly enrolled:
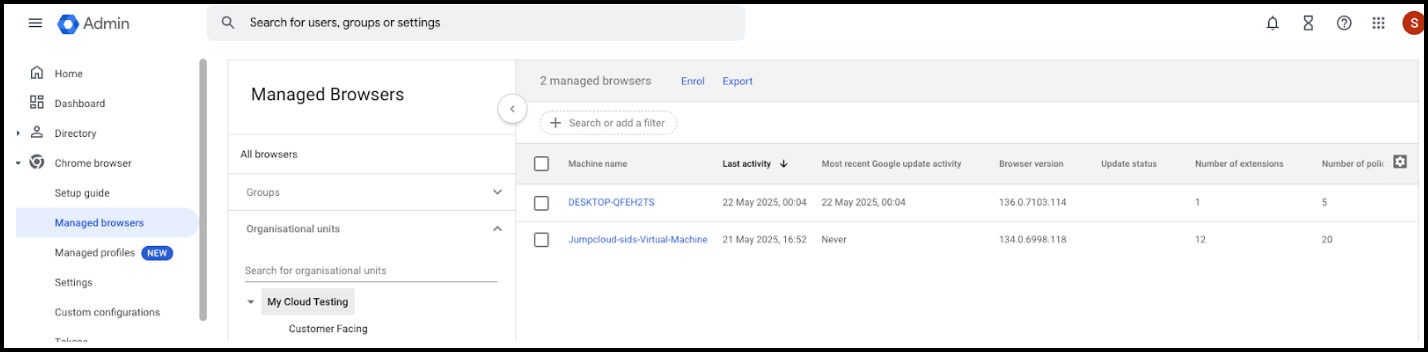
- Sign in to the Google Admin console using an administrator account.
- Go to Devices > Chrome browser > Managed browsers
- For Chrome Enterprise Core users, go to Chrome browser > Managed browsers.
- Devices are listed, along with browser information if Enable Chrome Browser Management Reported was selected in the previous configuration.
Users can view details about the managed Chrome browser on their devices by typing chrome://policy in into the address bar.
Configuring and Applying Google Enterprise Device Trust
Prerequisites:
- Google Workspace subscription (any edition that includes core management features)
- Chrome Enterprise Core subscription or higher is enabled for your domain within the Google Admin console, accessible through Billing > Subscriptions
- Administrator account access to Google Admin console
To configure the device trust connector:
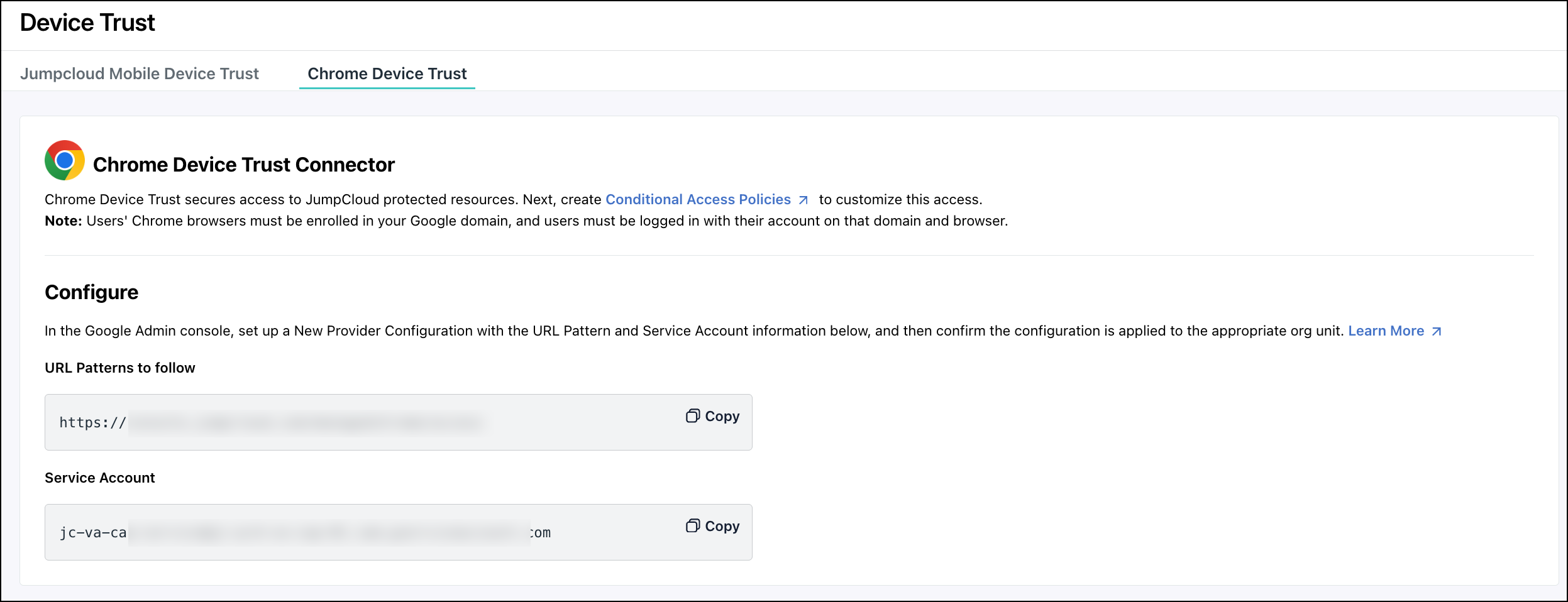
- From the JumpCloud Admin Portal, go to Security > Device Trust > Chrome Device Trust.
- Collect the URL Pattern to follow and Service Account. You will use these values to configure the device trust connector in the Google Admin console.
- Log in to the Google Admin console.
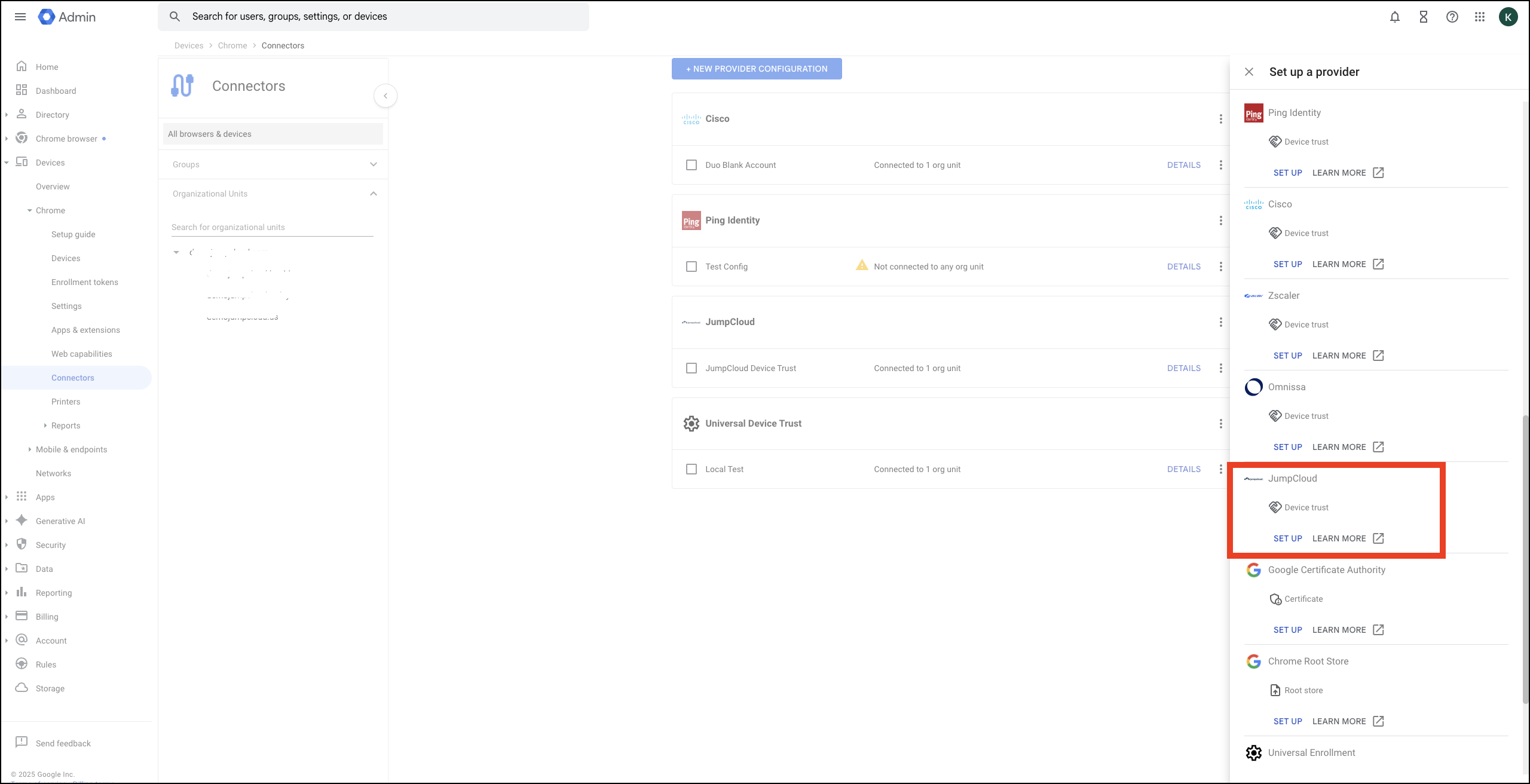
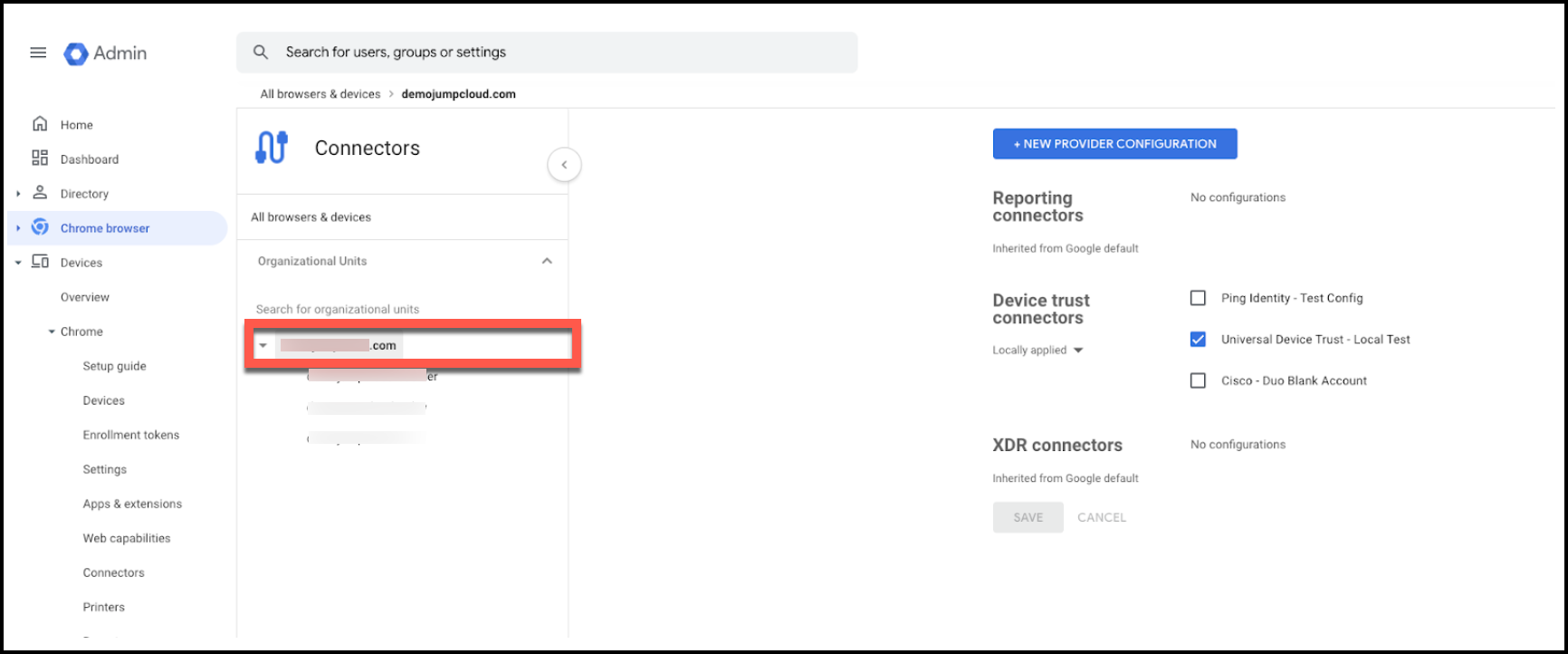
- Go to Devices > Chrome > Connectors and click New provider configuration.
- Choose Universal Device Trust from the provider list and click SET UP.
- In the configuration details, enter the following:
[image]- Enter an identifiable Configuration name, such as JumpCloud Device Trust.
- URL patterns to allow, one per line: Paste the URL Pattern you collected from the JumpCloud Admin Portal
- Service accounts, one per line: Paste the Service Account you collected from the JumpCloud Admin Portal
- For Enforcement level, ensure Managed browsers and profiles is selected.
- Click Add Configuration when done.
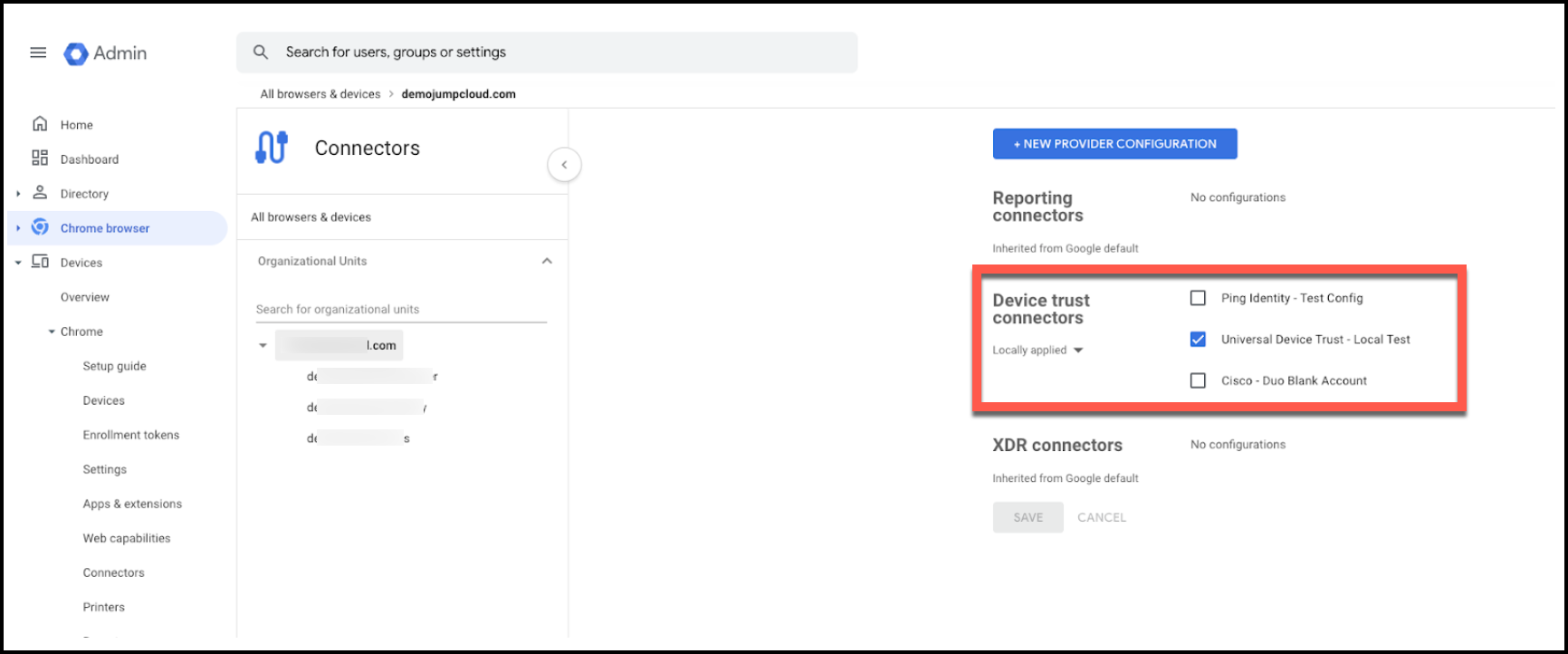
- On the Connectors page, select the organizational unit to apply the configuration.
- Ensure the Device trust connector configuration you just created is Locally applied:
Creating a Managed Chrome Conditional Access Policy in JumpCloud
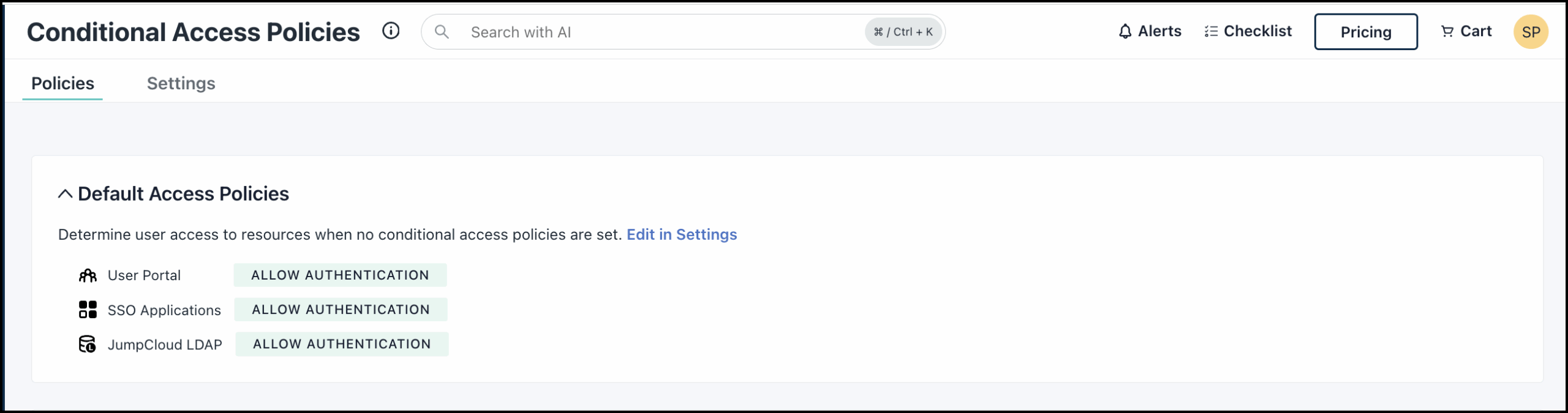
Default access policy settings dictate the behavior of access rules when no conditional access policies are applied. When default settings are configured to Allow Authentication, you can configure specific deny rules through conditional access policies. See Set a Default Access Policy for more.
JumpCloud offers conditions for managed Chrome browsers and managed Chrome profiles.
- A Google Chrome managed browser is a version of the Chrome browser that is centrally controlled by an organization using enterprise management tools such as the Google Admin console and third-party MDM or identity platforms like JumpCloud.
- A Google Chrome managed profile is a Chrome user profile that is signed in with a work (Google Workspace) account, and enrolled under organizational management policies.
- See Google's What's the difference between a managed profile and a managed browser? for more information.
Supported Platforms: Windows, macOS
Prerequisites :
First verify your Default Access Policy settings as follows:
- When no Conditional Access Policies are applied, Default Access Policy settings will determine the behavior of all access rules.
- If it is set to Allow Authentication, you will need to write a Deny conditional access policy rule.
- If it is set to Deny Access, you will need to write an Allow conditional access policy rule.
- See Set a Default Access Policy to learn more.
What is an enrollment domain in JumpCloud Conditional Access Policies for Chrome ?
This is your primary Google Workspace domain. By default, all user accounts in your org are created with a username at this domain. You can manage this domain and others in the Google Admin Console under Account > Domains > Manage Domains.
Follow the initial steps to create a new conditional access policy in Configure a Conditional Access Policy. Review the steps below to configure a condition for your particular use case.
On managed devices, users can only access sensitive applications (such as GitHub or SFDC) through a Chrome browser or profile logged in with their work domain. Any attempt to access these critical applications from another browser will be denied.
Consideration:
Default Access Policies rule under Settings is set to Allow Authentication.
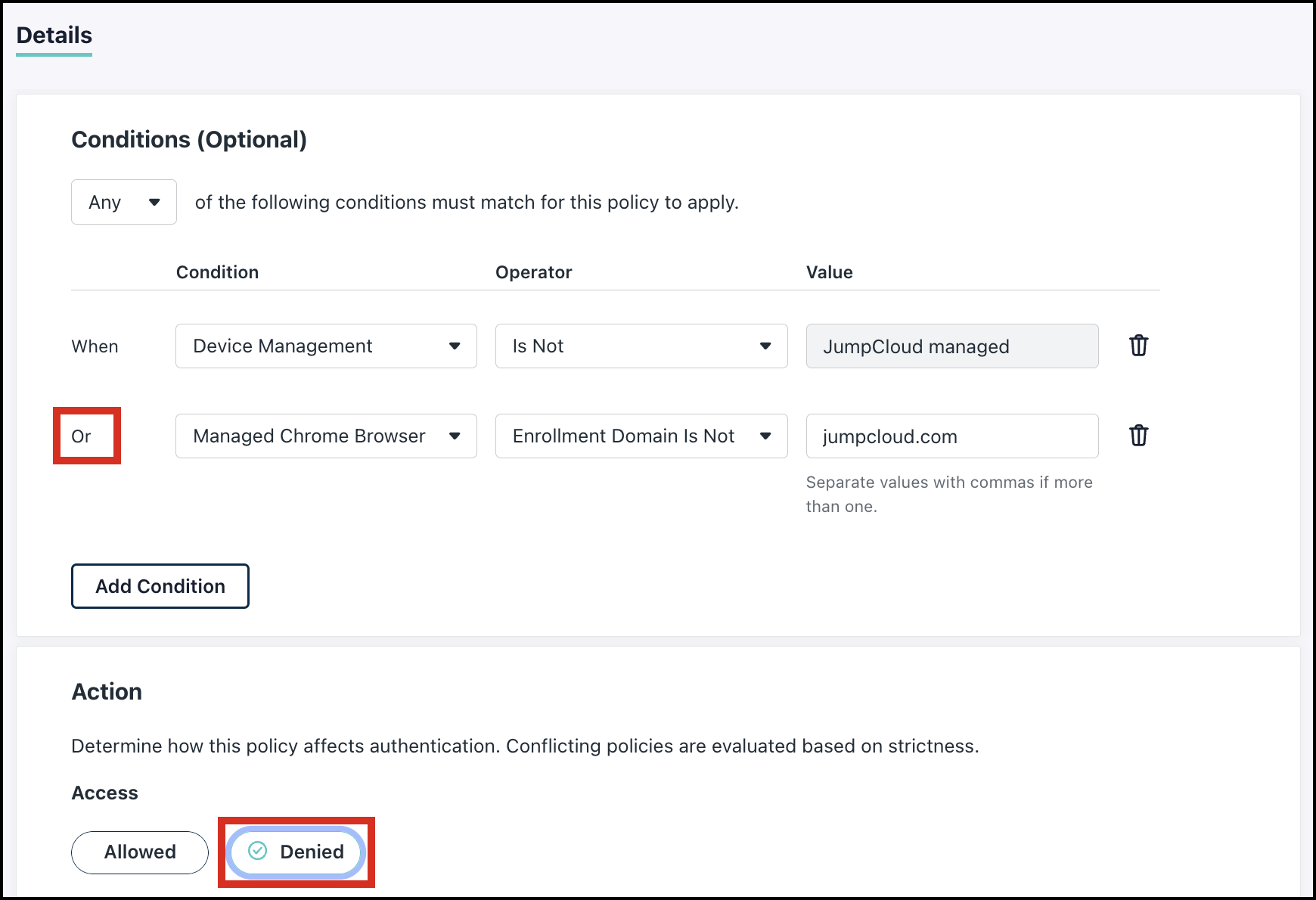
We need to create a new Conditional Access Policy to Deny access:
- From the initial drop-down, ensure Any of the conditions must match for the policy to apply.
- Select Device Management as a first Condition.
- For Operator, select Is Not.
- The Value defaults to JumpCloud managed.
- Click Add Condition (Or).
- For Condition, select Managed Chrome Browser.
- For Operator, select Enrollment Domain Is Not.
- For Value, enter the relevant domains. Include all allowed domains as comma separated values (jumpcloud.in, jumpcloud.com, etc.).
- Set the Action to Denied.
If a user is already logged into Chrome, they'll need to restart the browser and try again for this Conditional Access Policy to apply.
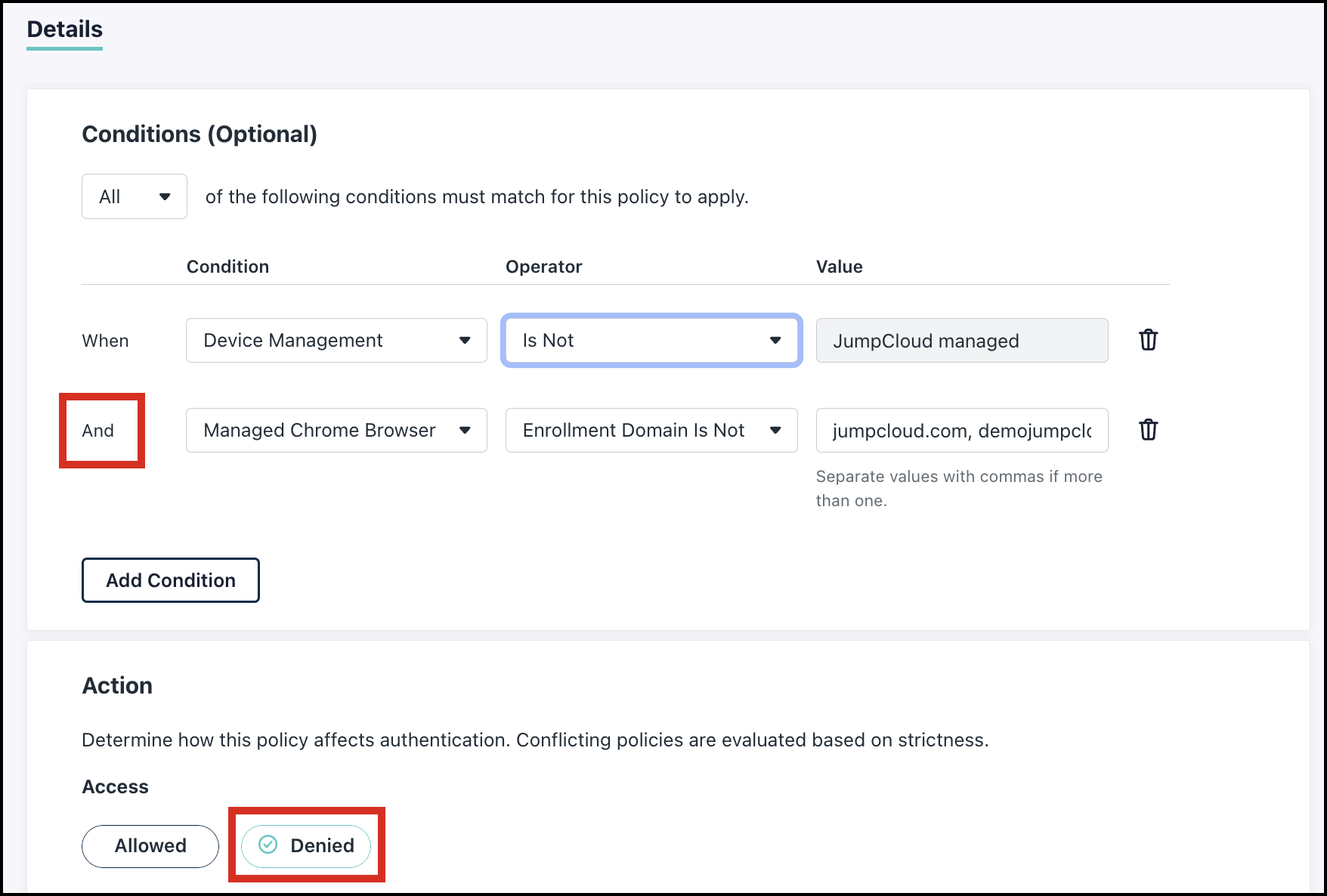
On personal or unmanaged devices, users can only access sensitive company applications through a Chrome browser or profile logged in with their work domain. Any access attempt from a guest or personal profile will be blocked.
Consideration:
Default Access Policies rule under Settings is set to Allow Authentication.
We need to create a new Conditional Access Policy to Deny access:
- From the initial drop-down, ensure All of the conditions must match for the policy to apply.
- Select Device Management as a first Condition.
- For Operator, select Is Not.
- The Value defaults to JumpCloud managed.
- Click Add Condition (And).
- For Condition, select Managed Chrome Profile.
- For Operator, select Enrollment Domain Is Not.
- For Value, enter the relevant domains. Include all allowed domains as comma separated values (jumpcloud.in, jumpcloud.com, etc.).
- Set the Action to Denied.
If a user is already logged into Chrome, they'll need to restart the browser and try again for this Conditional Access Policy to apply.