Use Default Access Policies settings to determine how users access a resource when no conditional access policies apply to them. You can see the Default Access Policies statuses for each resource (User Portal, SSO Applications, and JumpCloud LDAP) from the Conditional Access Policies list:
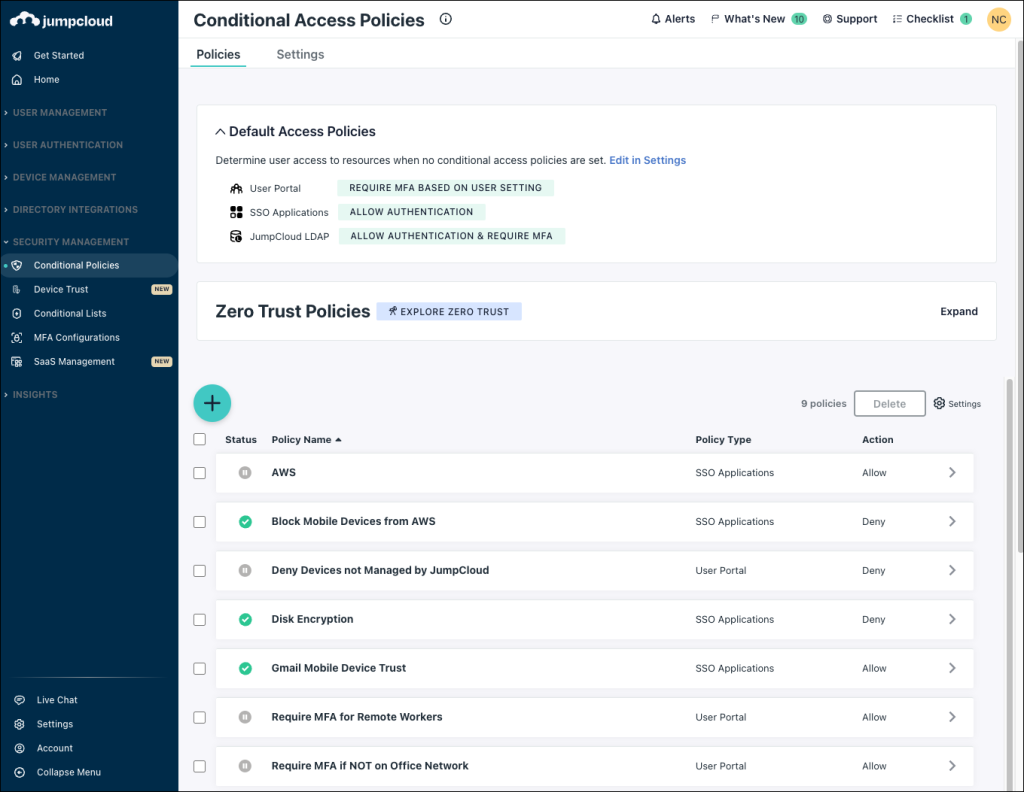
Considerations:
- Conditional access policies override a Default Access Policy.
- For the User Portal, the Default Access Policy setting defaults to Require MFA based on user setting.
- The Require Multi-factor Authentication on the User Portal option must be enabled individually in the User > Details tab to require MFA for the User Portal.
- For SSO Applications, the Default Access Policy setting defaults to Allow authentication.
- For JumpCloud LDAP, the Default Access Policy setting defaults to Allow Authentication.
- If you want to create a Default Access Policy that denies access, we recommend that you create it after you’ve configured your conditional access policies that allow access. If you first create a Default Access Policy that denies access and there are no conditional access policies that apply to users, the Default Access Policy will apply to all of your users, and they won't be able to access the User Portal or their SSO applications.
Configuring a Default Access Policy
To set up a Default Access Policy:
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Log in to the JumpCloud Admin Portal.
- Go to Security > Conditional Policies.
- Click the Settings tab.
- Expand Default Access Policy Settings.
- For a resource, decide what happens when users aren’t part of a conditional access policy:
- If you don’t want to require Multi-factor Authentication (MFA), select Allow authentication.
- If you want to require MFA, select Allow authentication & require MFA. If you select this option, only the Admin selected MFA configurations are enabled for the user in user portal.
- If you want to deny access, select Deny access.
- For the User Portal only, if you want the Require MFA setting in the User > Details tab to determine how a user accesses a resource, select Require MFA based on user setting. To find and configure this setting, jump to Requiring MFA Factor Types from User Details.
Note: If you select this option, the user can select any authentication option configured by them in the user portal.- When Require Multi-factor Authentication on the User Portal is selected on the User > Details tab, users are required to authenticate with MFA when no conditional access policies apply to them.
- When Require Multi-factor Authentication on the User Portal isn’t selected on the User > Details tab, users aren’t required to authenticate with MFA when no conditional access policies apply to them.
- Click Save Changes.
Requiring MFA Factor Types from User Details
For a Default Access Policy, you have the option to select Require MFA based on user setting. This lets the Require Multi-factor Authentication on the User Portal setting on the User > Details tab take effect when no conditional access policies apply to a user.
To configure the Require MFA setting from a User > Details tab:
- From the JumpCloud Admin Portal, go to User Management > Users.
- Edit a user or create a new user. See Get Started: Users.
- Expand the User Security Settings and Permissions section and select Require Multi-factor Authentication on the User Portal if you want users to authenticate with MFA when no policies apply to them.
- If you’re using TOTP MFA, you can enter in a number for the enrollment period, but enrollment periods will only apply if no other policy applies and if the Default Access Policy is set to Require MFA based on user setting. Without the enrollment period, users who don’t have MFA set up are required to enroll in MFA the next time they log in to the User Portal.
Users will be required to enroll for TOTP, even if they enroll for other methods such as JumpCloud Protect Push MFA.
- Click save user.
