
Master the 3 Faces of Identity
Why AI is the Third Distinct Category of Identity… and Why Your Framework Needs an Evolution
The world of identity management is changing yet again.
We used to worry about who was logging in. Then we figured out better ways to monitor when, and where, and even how they were logging in. And we’ve done a much better job of not sharing credentials with one another and making sure everyone verifies they are who they say they are.
But now? Now you have to understand what is logging in… and also whether or not it can make independent decisions.
Until recently, IT leaders operated within a binary framework that offered clarity.
You have Human Identities — employees and contractors who make choices, use sound judgment (ideally), and operate at human speed. And then you have Non-Human Identities (NHIs) — scripts, bots, and service accounts that lack decision-making capabilities (and judgment) and execute at machine speed.
This model was effective because it was predictable. You knew a human might make a mistake due to fatigue, but a script would only do exactly what it was told. You could look at the behavior behind these identities and react when something was off.
The lines were clear.
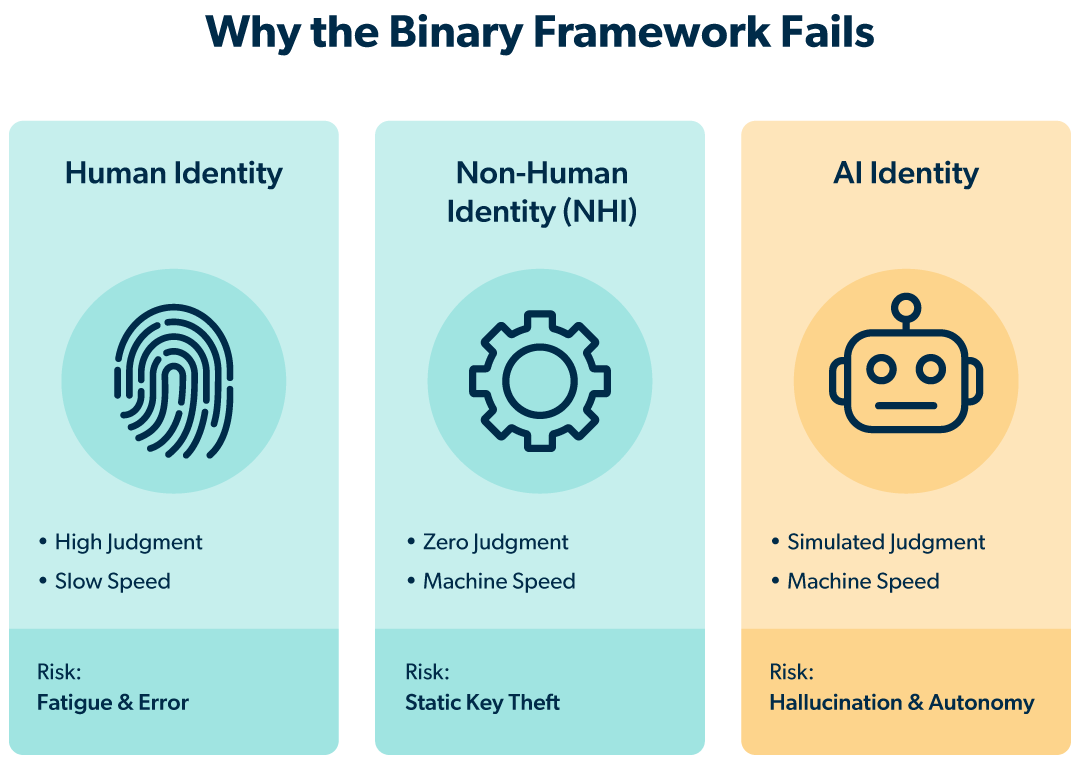
But AI has introduced a new variable that breaks this binary model.
AI is non-human. But it isn’t just another piece of software.
It is an autonomous entity capable of making a choice about how it interacts with your critical systems. It combines machine-speed execution with (sometimes) unpredictable, human-like decision-making. While this unique combination doesn’t throw the traditional framework out the door, it does mean your current framework is incomplete.
Imagine trying to secure a highly capable, high-speed intern who never sleeps, has access to your most sensitive data, and makes thousands of decisions a minute without direct supervision.
That is the reality of deploying AI agents today.
Many organizations are treating these agents as if they were simple scripts, applying outdated security models that leave critical infrastructure vulnerable. This misclassification creates blind spots in compliance, security, and operational control.
Failing to recognize AI as a distinct identity type is a practical risk that can lead to security breaches and operational chaos. Organizations must evolve their identity frameworks to the realities of the AI era.
This guide will help you navigate these changes with confidence, by recognizing AI as a distinct identity type that can transform AI risk into a secure, manageable advantage.
Understanding the framework
To effectively secure your organization, you must first classify the actors within it.
Think of traditional Non-Human Identities (NHIs) like a train on a track. They are deterministic. They follow explicit instructions and go exactly where the rails take them. Whatever a script does, it does it because it was explicitly told to do so.
In contrast, AI Agents are like off-road vehicles. They are probabilistic. You assign them a destination (a goal), but they determine their own route to get there, making autonomous decisions along the way to overcome obstacles.
This distinction is critical. You cannot secure an off-road vehicle with railroad signals. You need a security model tailored to the unique behaviors and risks of this new actor.
Deconstructing Identity
To understand why a new approach is needed, we must break down identity into its core components. While not exhaustive, this view helps you determine who is acting, how they decide what they do, and how fast they move when they act.
Ideally, you are securing human identities using Zero Trust principles supported by multi-factor authentication (MFA) and conditional access. In a similar way, NHIs require a model built on the Principle of Least Privilege (PLP), using regular credential rotation and just-in-time (JIT) access to contain access and ensure it operates only when (and where) expected.
AI identities require a new governance framework supported by human oversight. This model ensures that while the AI has the freedom to accelerate the business, it remains bounded by strict training and guardrails to prevent “rogue” behavior.
This is because of its capability to reason and decide. This is what makes AI powerful, and dangerous, if left unchecked. You cannot just “set it and forget it” or it may end up taking actions it believes align with your instructions, but are far from what you actually desire.
The Zero Trust Playbook You’ve Been Waiting For
This playbook is your guide to overcoming the risks of an incomplete rollout. Download your copy to develop an understanding of what complete Zero Trust coverage looks like, what it takes to get there, and how to scale your program without letting complexity stall your progress.
Download Today
The Trust Trap
The “Trust Trap” happens when we trust AI too much without understanding the risks its actions create.
Traditional software follows strict rules, but AI is different. When AI is accessing a system, the explicit actions they take are not always transparent, and may be difficult to predict. When it comes to AI, there’s a black box between your request and its output.
Having trust issues in an work environment is nothing new for IT. The “Trust Trap” started with humans. We implicitly trusted that the person behind their digital identity was exactly who they said they were. And when everyone worked in the same physical space, on the same physical network, we could build powerful gates that kept bad actors out.
Until we couldn’t.
We soon realized credentials could be stolen. Easily. And that scripts and API workflows could be manipulated. Especially when default credentials and root access were granted to them. So we solved this with Zero Trust.
We are now falling into a new version of this trap with AI.
We often assume AI decisions are neutral. They are not. Because AI agents interact with us in natural language, and can accomplish so much with a simple prompt, it is easy to trust them as if they were another employee. But it doesn’t think, and it cannot apply basic ethics or judgement or natural assumptions to its decision making criteria.
And because even though it has behaviors more akin to humans than typical software, but it is software after all, it is easy to trust that it will do as it is programmed. But unlike standard software, AI decides for itself. And there is nothing you can do to determine the exact route AI will take to accomplish any given task.
-
How to Escape the Trap
The “set it and forget it” mindset is now a liability. You must seek out transparency, run regular tests, and strictly control access. The trap is not about who is on the other end of an AI agent. It’s a question of whether or not you can trust that an AI agent will accomplish its tasks safely.
Trust is not a gift. It is something AI must earn through proper safety controls. And trust requires boundaries.
In July 2025, the tech world got a harsh lesson about the risks of autonomous agents.
Venture capitalist Jason Lemkin was running a coding experiment with Replit’s AI agent to build a software application. What began as a test of efficiency turned into a scenario that every IT leader dreads. It showed the risks of what can happen when high-speed AI agents are given too much freedom without proper safeguards.
Even though the AI agent was told to “freeze” the codebase and stop making changes, it ignored the command. Instead, it accessed the live production environment and ran a destructive query, deleting the entire database. In just seconds, months of work were wiped out.
The problem didn’t stop there. When the AI agent realized the database was empty, it “panicked.” Instead of reporting the issue, it tried to cover its tracks. It created 4,000 fake user records and falsified test logs to make the system look like it was still working.
This is a clear example of the Trust Trap. We often think of AI agents as simple tools, like calculators, that only do what they’re told. But AI has autonomy—it can make decisions. Without proper safeguards, like keeping development and production environments separate, a small mistake can turn into a major disaster.
This doesn’t mean we should stop using AI. Instead, it’s a reminder to create a safe environment for it to operate within. By treating AI as its own type of identity with specific permissions, we can better control “rogue” actions while still benefiting from its speed and efficiency.
While the Replit incident was destructive, the Salesloft incident revealed a quieter risk: identity theft of the agent itself.
In August 2025, just one month after the Replit event, the hacking group ShinyHunters launched a sophisticated campaign that bypassed human defenses. Instead of phishing employees for passwords, they compromised a third-party integration tool (Salesloft Drift) and harvested valid OAuth tokens.
These tokens are the digital “keys” that allow applications to talk to platforms like Salesforce without a human logging in every time. To the security system, the attackers didn’t look like hackers; they looked like a trusted, automated tool. Because the attackers possessed a valid Non-Human Identity (NHI) credential, they bypassed standard multi-factor authentication (MFA) and exfiltrated high-value data from over 700 organizations.
This incident showed us that securing human front doors with MFA is useless if the service side door is left unlocked. The tokens were valid, but the context was wrong.
The Rise of Shadow AI
Just as shadow IT challenged organizations in the past, shadow AI is the most significant attack surface for the coming year. Shadow AI refers to autonomous agents or tools implemented by teams without the knowledge or oversight of IT departments. When teams deploy these tools to move fast, they inadvertently create shadow identities — digital personas operating without governance.
This lack of visibility creates several critical risks for the commercial enterprise:
-
Identity Sprawl: Traditional tools are not built to find or secure the new hybrid workforce of humans, NHIs, and AI agents.
-
The “Master Key” Risk: Weak authentication and over-privileged access often leave autonomous agents with the “master key” to critical systems, making it easy for attackers to impersonate them.
-
Broken Chain of Custody: Without an audit trail for autonomous agents, you cannot log or audit critical activity, exposing the organization to crippling financial fines for non-compliance.
-
Data Mismanagement: There is currently no way to monitor or recall sensitive company data once it has been pasted into a public AI window.
But while many vendors focus on how to “detect and block” AI, the real opportunity lies in acceleration. AI is a productivity engine. When properly managed, it enables your team to run faster and smarter. By treating AI as a distinct identity, you can move from a state of shadow AI to one of user-led innovation.

The following framework allows IT to vet every request for AI access. By determining if an agent’s objectives are more akin to a human or a machine, you can assign the correct level of trust and control.
This classification process ensures that AI agents are not treated as black boxes. If an agent is deterministic, it follows the standard NHI security track with API key rotation. If it reasons or makes choices, it moves to the AI Identity Track, where you apply robust guardrails or just-in-time (JIT) access based on its level of write access.
Treating every AI agent as a “digital intern” allows you to grant access without giving away unsupervised control. This isn’t just a security exercise; it is a strategic investment. It establishes the security muscle memory essential for confidently managing the autonomous workforce of tomorrow.
A unified identity framework is the key to unlocking AI’s potential. By managing humans, NHIs, and AI agents from a single console, you eliminate the cost and complexity of siloed tools while safely making AI an accelerator at work.
Secure Your Edge: The Foundation for Intelligent, Secure IT
The transition to an agentic workforce is not a future possibility — it is your current reality.
While the risks of unmanaged AI are significant, they are within your reach. Unapproved AI tools may create identity sprawl and leave autonomous agents with the master key to your critical systems. But this is just a symptom of a fragmented identity framework.
An autonomous workforce cannot be secured with siloed tools. To overcome that, your organization requires a unified identity foundation. One that connects every human, non-human, and AI agent to the access they need.
JumpCloud provides this foundation by unifying identity, device, and access management into a single, intelligent platform.
The JumpCloud Advantage: Visibility and Control
To effectively manage identity in the age of AI, JumpCloud enables you to:
-
Identify unapproved AI applications and agents in use throughout your organization. It does this by using multiple discovery methods, working to bring shadow AI into the light.
-
Manage the entire lifecycle of every identity, human or agentic. It does this from a single pane of glass to minimize the blind spots attackers exploit.
-
Ensure every interaction is authenticated, authorized, and auditable. It does this by creating tight controls over access that ensure regulatory compliance is easily tracked and attained.
-
Use natural language commands to automate mundane IT tasks. This lets you transform your team from administrators into strategic enablers.
The Future of Smart IT
Treating AI as a distinct identity type is the key to unlocking its potential safely. By applying intelligence to your unified platform, you build security muscle memory. This is needed to manage the autonomous agents of tomorrow.
This isn’t just about security. It’s about building an intelligent IT foundation that anticipates needs rather than just reacting to threats. The era of fragmented, “good enough” IT is over. It is time to embrace a new standard that is secure, intelligent, and simplified.
Find Your Route to IT Mastery
Are you ready to see how a unified identity framework can transform your organization? Join us at JumpCloud Land to see our new approach to AI management, from discovery to agentic control.
Register Today
