In this article, we’ll take a closer look at Zero Trust Network Access (ZTNA): a combination of technologies that facilitates secure remote access between users, devices, and applications via defined access control policies.
We’ve all heard the phrase: innocent until proven guilty.
But what does it mean?
Say your neighbor accuses you of stealing his bike… because you often wear black hoodies at night (he doesn’t realize you’re just a programmer). He recently installed some M820 Saint Shimano brakes, among other upgrades, and is distraught.
Though your neighbor may start giving you the side eye, you can breathe a sigh of relief knowing the U.S. legal system has your back. Unless he can prove guilt “beyond all reasonable doubt,” the law assumes your innocence.
Sometimes it makes sense to give our fellow humans the benefit of the doubt. Unfortunately, that’s never a good idea when it comes to cybersecurity.
As data breaches continue to rise — by at least 17% from 2020 to 2021— adopting a ”trust no one” mentality has never been more crucial. This is where Zero Trust Network Access (ZTNA) comes into play.
What Is Zero Trust Network Access (ZTNA)?

ZTNA refers to the technology necessary for implementing a Zero Trust security model. Sometimes called “zero trust network architecture,” Zero Trust models always assume that threats exist both inside and outside of networks every moment.
Unlike virtual private networks (VPNs), which provide access to LANs by default, ZTNA solutions only permit access to applications, services, and data to users as necessary.
For example, the marketing department won’t have access to the same resources as the accounting department within a given organization. Also referred to as the principle of least privilege (PoLP), this security measure helps mitigate potential cyberattacks to smaller sets of resources than might otherwise be compromised.
Fun fact: 73% of hackers say traditional perimeter firewalls and antivirus protection are “irrelevant and obsolete.” Furthermore, IT administrators can use ZTNA tools such as multi-factor authentication (MFA), single sign-on (SSO), and directory services to further reduce security risks.
How Is ZTNA Different from Traditional Perimeters?
Until recently, most IT teams placed layered security rings around digital assets residing in on-prem networks. This “defense in depth” security framework operated under the assumption that attackers would have to break through layers of applications, networks, hosts, and data to access an organization’s most crucial digital assets.
This security method was adequate until cloud infrastructures went mainstream during the mid-2000s. It’s not an understatement to say Google Cloud Platform, Microsoft Azure, and Amazon Web Services (AWS) changed everything.
Suddenly, employees began relying upon cloud-based software subscriptions, public Wi-Fi connections, and coffee shops. Translation: no longer was proprietary data delegated to software-defined perimeters (SDPs)!
According to the 2021 Forrester report “A Practical Guide to a Zero Trust Implementation,” ZTNA perimeters were a natural evolution from traditional setups:
“The perimeter did not disappear: our perception of the network perimeter has just evolved. The perimeter is now ‘the edge’ of your network, whereby users touch or connect to the enterprise.”
This means IT admins must re-create segmentation boundaries around network hosts, peers, and services; authorize access to said boundaries; and monitor activity within each segmentation. For example, say an application tier can exchange information with middleware; middleware can talk to databases, but the application tier cannot access the database tier directly.
With that said, the ultimate aim of ZTNA and SDP is the same: prevent users from interacting with applications, services, and information they don’t have permission to use.
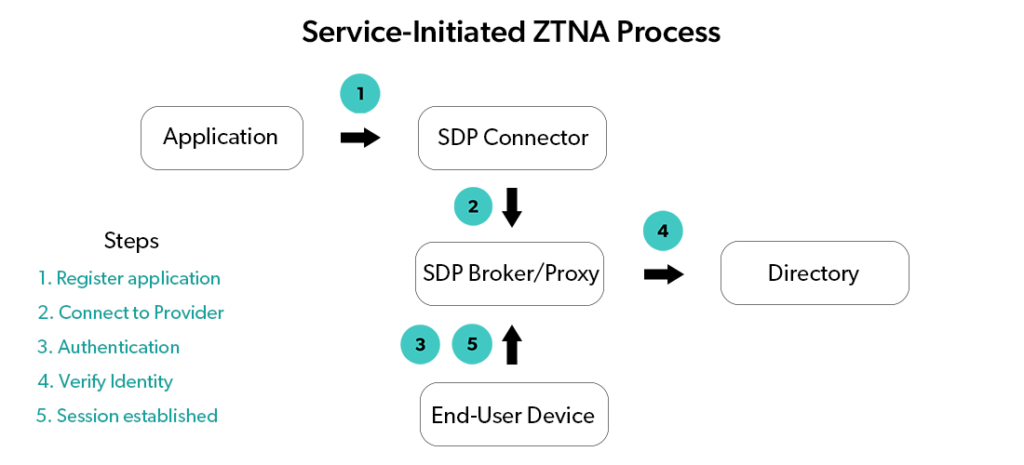
How Does ZTNA Work?

Picture an Olympic-sized swimming pool.
Think of the various IT aspects under your care as swim lanes. Each aspect — users, devices, transport, apps, and data — is a swimmer with its own security policies.
One swimmer cannot interact with another until they prove their identities. In other words, every organizational device, user, and service must prove its authenticity through an encrypted tunnel before it can exchange data with another lane.
What happens when a lane becomes compromised? Its communication with other data sources is immediately and automatically blocked. As part of ZTNA, administrators may also employ identity and access management (IAM) mechanisms like mutual TLS, MFA, and SAML to support trustworthy end-to-end communication.
Want to learn more about creating Zero Trust “lanes?” Check out this video with Don Bowman, Agilicus cybersecurity expert.
What Are the Elements of ZTNA?
Of course, the specific technologies admins employ in Zero Trust Network Access frameworks varies depending on unique organizational needs. However, most ZTNA programs incorporate the following security measures:
- Identity and access management (IAM): The quickest way for hackers to access a company’s digital assets is via stolen credentials. Modern IAM solutions, like the JumpCloud Directory Platform, mitigate this risk by giving IT admins centralized control over devices, applications, files, networks, and login credentials. Admins configure an identity for each unique user, allowing controlled access to the tools they need (e.g., Wi-Fi, company servers, specific apps), while restricting access to the digital assets they don’t need.
- Tighter device security: Admins analyze network traffic to and from devices via agent-based or service-based ZTNA software. As remote work continues to grow in popularity, so does the use of mobile devices and their accompanying business-related apps. Unfortunately, tablets and smartphones pose huge security risks if hacked, lost, or stolen. Thus, mobile device management (MDM) security measures are now a crucial aspect of ZTNA.
- TLS encryptions: IT admins rely on small, encrypted, TLS tunnels that link users and applications. This is a significant contrast to traditional perimeters built on private MPLS-based connections.
- Secure authentication measures: Another essential component of ZTNA are sophisticated authentication controls like multi-factor authentication (MFA), single sign-on (SSO), and conditional access safeguards that follow if/then policies. SSO platforms are particularly powerful because they allow users to access all approved network applications with one username and password, thus removing the risks associated with maintaining multiple logins.
- Enhanced risk factors: Security systems evaluate risks based on user identities, roles, locations, timing, request frequency, and more. Admins can then pair granular risk factors with conditional access policies to either heighten or reduce authentication restrictions.
- Hidden IP addresses: They don’t reveal IP addresses to the network at large.
- Individual application access: Once connected to a network, devices can only access approved applications and services.
As mentioned above, there is no “one-size-fits-all” plan when it comes to ZTNA. Organizations should customize their approach to meet their unique security needs.
Benefits of Zero Trust Network Access

Of course, the most obvious benefit of running ZTNA is superior data protection. But let’s take a deeper look at what that means along with the other advantages provided by Zero Trust security implementations.
1. Greater Security Than VPNs
As previously mentioned, VPNs are becoming unnecessary to effective cloud-based security. Zero Trust security networks, supported by tactics like SSO verification and MFA, reduce the likelihood of malware gaining unauthorized access to large network data segments.
Once malware breaches a firewall, hackers can locate proprietary data within minutes, if not seconds! VPNs on their own may not be sufficient to prevent lateral movement once a legitimate device has been compromised.
Alternatively, Zero Trust requires authentication at every access transaction, which prevents them from laterally attacking data infrastructures during a breach.
Cloud directory platforms support authentication protocols — SAML, SCIM, OAuth, WebAuthn, and LDAP — to connect users to resources directly as opposed to making all resources available upon authentication to the network.
Alternatively, VPN security measures may allow cybercriminals to freely navigate systems undetected once inside the underlying network.
With ZTNA, limited and time-bound access settings reduce the likelihood of cybercriminals locating such data in the first place. Not only are traditional VPN architectures much slower, but they are also more expensive in terms of bandwidth fees.
2. Streamlined IT Management
Privileged access management (PAM) systems automatically evaluate login requests based on predetermined criteria. This means IT administrators don’t have to waste time monitoring logins throughout the day.
Their ZTNA system will alert them upon identifying suspicious activity based on pre-identified parameters. Cloud-based directories like JumpCloud allow admins to maintain a bird’s-eye view of activity across IT environments. With JumpCloud, IT managers can quickly retrieve the time, locations, and applications involved within approving and/or denying access requests.
Obviously, the less time admins spend analyzing logins, the more time they can devote to product development, process improvement, or other high-value activities!
3. Streamlined User Access
One less frequently discussed benefit of ZTNA is its positive impact on employee productivity. With SSO, users can access the entirety of resources they need with one set of credentials. The user will either enter one username and password repeatedly or they will log into all necessary applications with one click.
With less passwords to remember, workers are less likely to forget, reset, and compromise precious login information. Just how big of a problem is sign-on lockout?
According to a 2017 report from LastPass, the average business worker has nearly 200 passwords. As reported by Forbes, one study found that most employees switch between applications at least 10 times per hour. That translates up to 32 lost days of productivity per year, in some instances!
In addition, user-friendly MFA applications (like those that support push notifications), conditional access policies, and passwordless authentication further streamline the user’s login experience.
4. Remote-Work Friendly
As previously mentioned, an increasing number of organizations now rely on cloud-based applications to get work done.
Since the beginning of the COVID-19 pandemic, many companies have switched to remote and hybrid work policies out of necessity. Understandably, the office exodus introduced valid concerns around employees using personal devices over public networks.
The good news is that all it takes to handle these concerns is implementing a tool like the JumpCloud Directory Platform that is equipped to enforce conditional access policies, multi-factor authentication (MFA), and customizable security measures that safeguard organizational data regardless of location. Again, with Zero Trust security, a worker’s identity is the perimeter.
5. Enhanced Compliance
Unfortunately, audit evaluations are often fleeting moments in comparison to the time IT departments spend preparing documentation trails.
ZTNA supports stringent compliance policies by analyzing, recording, and cataloging every access request. Cloud-based directories track the time, applications, and locations involved with each request, resulting in the creation of stress-free audit trails.
Such reporting capabilities allow admins to quickly produce compliance documentation as requested by governing agencies.
Are you sold on the benefits of Zero Trust security yet? If so, keep reading for a summary of the steps your IT department should take to get started.
How to Implement Zero Trust Network Access

1. Define Surfaces & Identify Resources
The best place to begin is to take stock of what you have. Often referred to as a “protect surface,” this action allows you to differentiate between what is and isn’t valuable to the organization at large. Palo Alto Networks recommends breaking this task into the acronym DAAS: data, applications, assets, and services.
For example, say your organization is an insurance agency that handles personal claims information. The data is the client information, the applications include the software your insurance agents use to evaluate the claim, the assets are your servers and equipment that store the data, and the services are the technology relied upon to access the data (e.g., Active Directory, cloud-based directories, SSO).
Alternatively, refer to JumpCloud and Forrester’s A Practical Guide to a Zero Trust Implementation for a strategic roadmap for getting started.
2. Map Standard and Privileged Pathways
Once you’ve identified your organization’s DAAS, it’s time to map information access pathways. Who has access to which elements? How do they access these elements? When are they permitted to use them?
3. Pick Your Priorities
Prioritize protection based on what is most essential to running the business. Your most valuable assets are likely your core business operations and customer data. With this in mind, we recommend prioritizing high security measures, like:
- Core business operations.
- Customer data.
- Personal identifiable information (PII) and IP data.
- Financials.
- Users who can access the above resources.
Depending on organizational bandwidth, you may want to run a soft launch for IT admins and select user groups. As your team becomes more comfortable implementing and enforcing ZTNA elements, branch out to secure more items.
It’s worth emphasizing that ZTNA implementation, improvement, and maintenance is an ongoing commitment. With that said, determining which technologies can best mitigate your highest risks may be the most challenging part of the process.
While no single product can help you achieve Zero Trust completely, JumpCloud unifies several ZTNA functions in one platform at a scalable, low price tag.
4. Implement Zero Trust Policies
Next, create policies that add context to user requests. JumpCloud provides admins with a point-and-click method to configure machine behaviors, regardless of location. Keep track of remote workers using Mac, Linux, and Windows systems with ease.
Also, don’t underestimate simple policies like screen saver lock, password requirements, and disabling guest accounts!
5. Monitor and Maintain Parameters
With ZTNA, it’s not enough to install antivirus protection software and “check out.” Install tools like endpoint detection and response (EDR) software to significantly decrease the surface area of attack for endpoints and keep monitoring the effectiveness of the parameters and policies you have set.
Finally, no ZTNA program will be successful without stakeholder support. At JumpCloud, we run training modules quarterly to ensure team members understand the importance of following security measures. This step is especially crucial for organizations with remote workers who are capable of making common mistakes known to trigger security breaches.
Simplify Zero Trust Network Access with JumpCloud
If you haven’t already, the time to adopt Zero Trust is now. No matter the size of your organization, your IT department must always assume threats exist both inside and outside of your network at every moment.
The easiest way to implement ZTNA? Let JumpCloud’s cloud directory and identity management platform do the heavy lifting for you. With JumpCloud, you can securely authenticate users to systems, applications, and Wi-Fi networks without a VPN.
Alternatively, if you want to keep your VPN for other reasons, JumpCloud can still streamline centralized provisioning, deprovisioning, and account modification by connecting our cloud LDAP functionality or RADIUS to your VPN.
Ready to give it a whirl?
Click here to sign up for a free trial.




