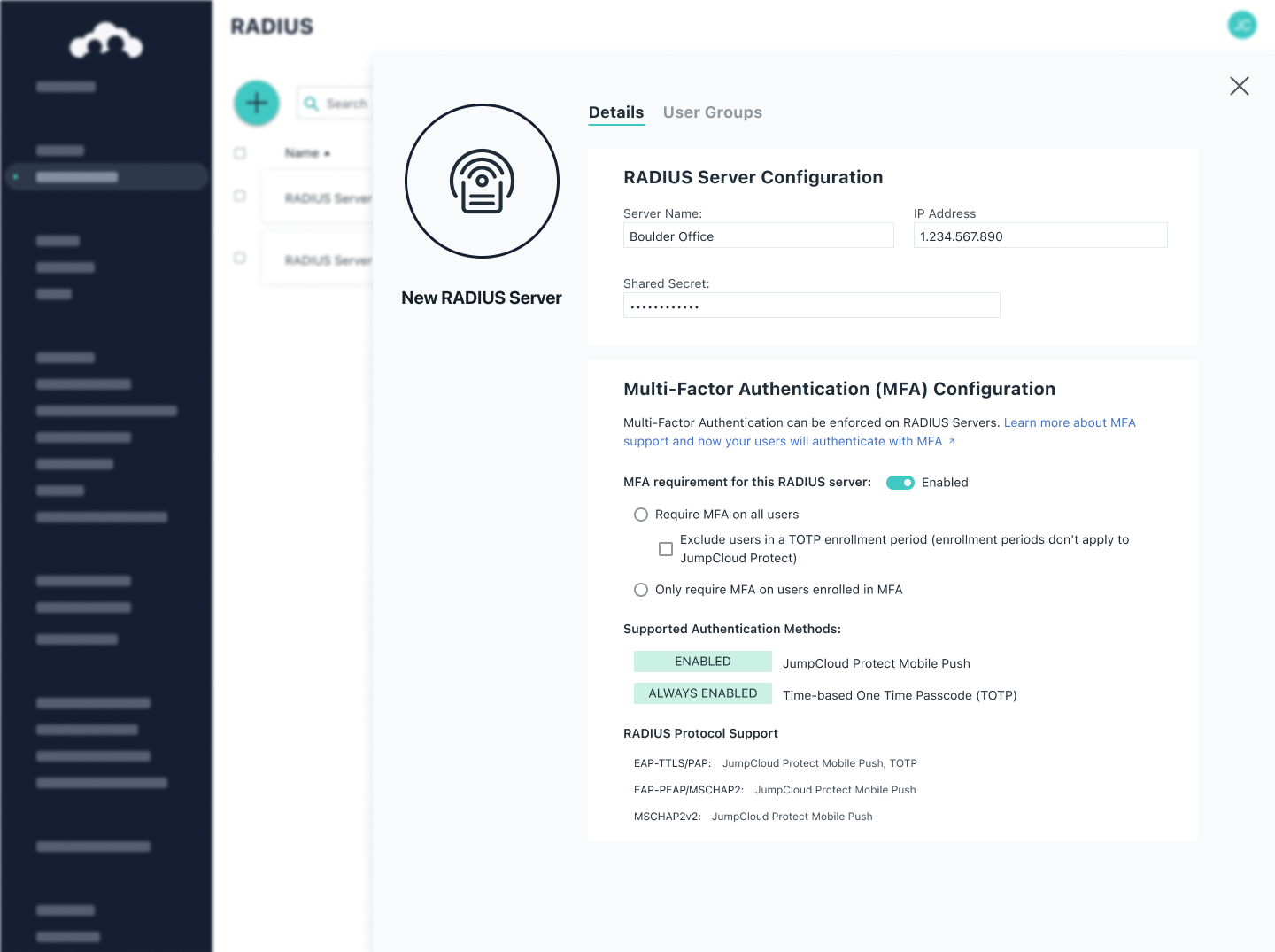
Multi-Factor Authentication (MFA)
Secure identities and manage access to all of your digital resources with MFA to prevent unauthorized logins.
Streamlined and Secure Access with MFA
With so many looming digital security threats out there, many organizations know they need improved security, but do not know where to start. With JumpCloud MFA and JumpCloud Protect™, you can secure user access to applications, devices, networks, and other resources while fostering a seamless end-user experience that greatly increases your security posture.
Flexible Authentication
Use JumpCloud Protect — our free authenticator app — or integrate your own provider, and choose from push-based, time-based one time passwords (TOTP), JumpCloud Go, hardware keys, biometric, certificates, or other methods to ensure secure access to resources as a standard user or user with administrator roles.
Course
| Enabling MFABlog Post
| One-Touch, Frictionless MFA Using JumpCloud ProtectSupport Article
| JumpCloud MFA GuideBlog Post
| Why Admin Portal Security is Crucial and How JumpCloud Keeps You Protected
Contextual Access
There is a tight balance between security and frictionless access. Level up your access security with contextual and risk-based access policies that dynamically adjust MFA enforcement based on situational or business needs.
Blog Post
| Examples of Conditional Access PoliciesSupport Article
| Conditional Access Policy Considerations

Easy Enrollment
Quickly and easily implement MFA by activating it in the JumpCloud Admin Portal. User-friendly self-enrollment enables you to provision users to your multi-factor authentication solution quickly and allows them to sign up and enroll their own devices.

Try our MFA Guided Simulation
Please rotate device
This interactive demo is best viewed in landscape mode.
Explore JumpCloud Open Directory Platform Capabilities
Identity Management
Access Management
Device Management








