It’s Cybersecurity Awareness Month! In honor of the theme — Do Your Part. #BeCyberSmart — we’re doing our part by educating IT teams and organizations on protecting themselves. Throughout October, the JumpCloud blog will focus on top cybersecurity issues, from IT admin best practices to CISO responsibilities. Tune back in throughout the month for new cybersecurity content or check out our archive of existing security articles for cybersecurity insights written specifically for the IT professional.
According to IBM, the average cost of a data breach is $4.24 million per incident. They also identified a few trends: remote work has a negative impact on this, healthcare breach costs have surged, compromised credentials are one of the most common causes of breaches, and modern approaches to cybersecurity reduce overall costs. In today’s modern IT environment, proper cybersecurity practices are essential for keeping users, devices, and information safe. What’s more, modern single sign-on (SSO) solutions are popular safeguards to put in place to improve cybersecurity and compliance simultaneously.
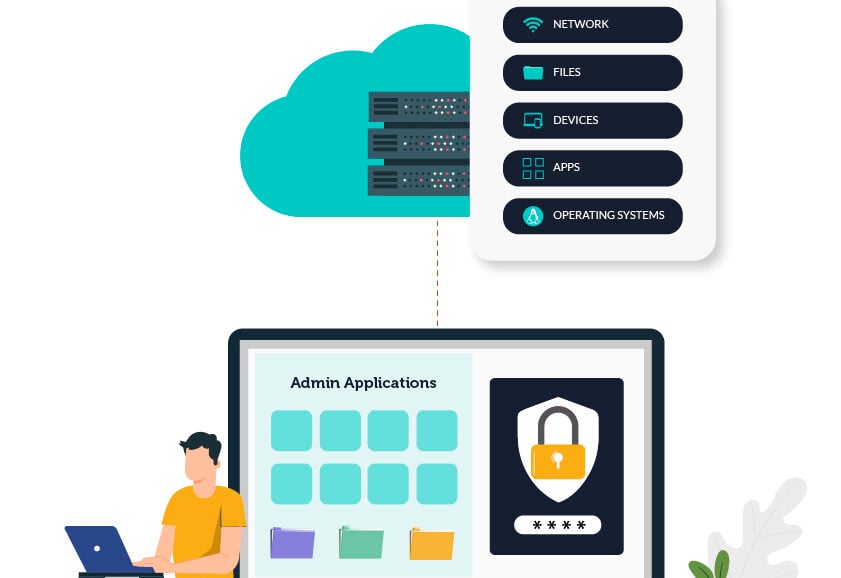
The sheer number of tasks we do online grows every year as we create and discover new opportunities to digitize our world. This is true within the workplace as well, but as we find more processes to automate using cloud-based technology and new apps to improve efficiency, we add more risk to the organization. Each tool added to the technology toolbelt, each interface users enter a password on, each app that we connect to via different networks and devices — they all add to our existing attack surface and present bad actors with seemingly unlimited avenues to cause harm if left unchecked.
This is where a secure, single sign-on solution comes into play — using one reinforced set of credentials to access all of these tools and resources provides quite a few different benefits to modern organizations. One major SSO benefit is that reduces the number of attack vectors your organization has, and SSO layered with multi-factor authentication (MFA) creates useful security and compliance controls. So, how do you find a solution that provides these capabilities and more? The answer is simple — look for an integrated, holistic directory platform that focuses on security and productivity.
Implementing an integrated directory solution provides organizations with a single source of truth for identity management and user authentication while providing built-in SSO and MFA capabilities and more. This is an important step to take to mitigate the risk that is inherent when users have to create and input different credentials across a wide variety of tools and resources, thus creating many unnecessary new attack vectors ripe for the taking.
What a Comprehensive SSO Solution Includes
Traditionally, single sign-on solutions were reduced to web applications only, with specific, limited features to support security controls around this approach. This is no longer the case; a comprehensive SSO solution can now include:
- Single sign-on capabilities to virtually all IT resources (all apps, networks, devices, file servers, and more)
- Multi-factor authentication with an integrated authenticator app that supports multiple factors like TOTP and push notifications
- Password complexity requirements
- Password reset capabilities on-device rather than through an online web portal (to prevent phishing)
- Conditional access policies regarding known devices and networks
SSO Reduces the Number of Attack Vectors That Exist
Adding a comprehensive single sign-on solution into your organization’s IT environment reduces your overarching attack surface in a few different ways:
- It reduces the total number of credentials end users need in order to access their resources, limiting the potential for them to be phished
- It also reduces the chances that credentials which were stolen in a separate breach (but related to your end users) can be used against you
- It can be layered with MFA to make it nearly impossible for phished credentials to be used against you
In addition, if you are using the right SSO solution, you can ensure:
- Credentials can be updated on devices rather than on websites or apps
- Conditional access policies can prevent users from authenticating to company resources on unknown devices/networks, creating an important layer of security
By preventing users from separately logging into each resource they need, you substantially reduce the number of attack vectors across your organization. SSO, when used properly — and especially with an SSO password manager, also results in fewer passwords being created and used in general, with one secure primary password as the main point of entry into your organization’s resources.
This also eliminates a couple common themes we see across users: password reuse and password fatigue. Plus, forcing password changes on devices rather than online makes passwords essentially impossible to phish, creating a distinct barrier between your IT resources and bad actors.
SSO and MFA are Important Compliance Controls
A comprehensive single sign-on security solution is not only important for reducing your attack surface; it’s also a widely used control for meeting a variety of compliance standards. A couple examples are SOC 2 and HIPAA. Compliance regulations like SOC often require that controls be put in place around data protection, and SSO is a great example of a security control that keeps data safe from external parties. On top of that, HIPAA requires effective authentication controls be put in place regarding users who access electronic records — so implementing SSO and MFA together ensures that the user’s identity is both verifiable and secure.
The best solution for implementing holistic compliance controls involves implementing an integrated cloud directory platform, because this provides your organization with a complete identity and access management (IAM) solution with single sign-on capabilities where you can centrally control user access to virtually all IT resources.
How an Integrated Directory Solution Solves the Problem
The issue with implementing anything less than an integrated directory solution with built-in SSO security capabilities, is that you’ll need to purchase and use multiple disparate tools to get security coverage that still doesn’t rival a holistic solution. Plus, the fewer number of tools in your IT environment, the better in terms of your attack surface and the potential for gaps in your security controls.
Integrated directory solutions check all of the boxes listed above regarding a comprehensive SSO solution, plus much more. A modern cloud directory platform will include SSO, MFA, password complexity requirements, password changes enforced on devices rather than online, and conditional access policies.
On top of that, an integrated platform will allow for quick provisioning and deprovisioning of access, which improves internal security and helps prove compliance with data protection standards. Further, if a threat is discovered in relation to a user’s identity, the user can be locked out of their account immediately until the threat is resolved, keeping IT resources safe.
Try JumpCloud’s Solution Free
The JumpCloud Directory Platform is an integrated cloud directory solution that offers IAM, SSO, and many other features that improve organizational security and user productivity. Test out JumpCloud’s modern, simplified IAM solution with True SSO, and see if it’s right for your organization! Create a JumpCloud Free account to access the entirety of the platform for free, up to 10 users and 10 devices. Along with that, enjoy 24×7 in-app support — free for the first 10 days!