Updated on February 9, 2023
The world’s workforce has turned to remote work, resulting in employees accessing corporate resources from home and public networks. To Make (Remote) Work Happen, IT admins need a way to provide their employees with secure access to the resources they need to do their jobs without disrupting their day (perceived or otherwise) on whatever service they’re accessing.
Passwords alone are not enough to secure these resources and prevent unauthorized access, as they can be easily compromised by brute force, phishing, and other techniques, potentially resulting in monetary losses for organizations. IT administrators have to introduce additional security measures to protect their organization’s resources.
Multi-factor authentication (MFA) provides such a measure that safeguards organizational resources and reduces the risk (and cost) associated with password compromise. It’s a foundational security control for identity and access management (IAM) that can combine with conditional access to ensure that unmanaged devices from unauthorized locations won’t be granted access to vital IT resources.
The inclusion of MFA to IAM configurations adhere to the cybersecurity requirements that are issued by international standards bodies such as ISACA, ISO/IEC, NIST, and PCI SSC. These mature standards exist to safeguard confidential and private information from bad actors.
MFA Doesn’t Have to Be Difficult
However, implementing MFA can be a difficult proposition, for both technical and political reasons. On the technical side, there are many options to choose from, both free and paid, which can be difficult to implement and may only cover a subset of IT resources depending upon their specific requirements and capabilities. In addition, end users may be resistant to adopt MFA, especially if the process to verify additional factors is cumbersome, unreliable, or persistent.
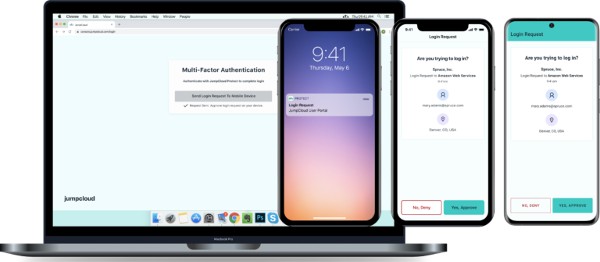
MFA combats the growing challenges associated with mitigating cyberattacks, as well as those associated with rolling out Zero Trust security tools to end users who may be resistant to the increased requirements to access their resources. IT admins can use JumpCloud Protect as an MFA solution to implement biometric authentication (Touch ID), mobile push notifications, and time-based, one-time passwords (TOTPs). It’s available as an iOS and Android mobile app, and natively backed by JumpCloud’s Directory Platform.
JumpCloud Protect: Biometric, Push, and TOTP Authentication
IT admins can leverage JumpCloud Protect to extend MFA beyond cloud applications and secure all endpoints and resources, including on-premise applications, Mac, Windows, and Linux desktops, VPN and wireless networks, and servers.
With JumpCloud Protect, IT admins can achieve:
- Improved endpoint security: JumpCloud Protect adds a secondary security layer to prevent unauthorized access to an organization’s network, customer data, tools, and more, giving IT admins and organizations peace of mind.
- Higher security for network devices: JumpCloud Protect integrates with JumpCloud’s RADIUS services to safeguard the network perimeter such as administrative access to firewalls or employee access to VPNs.
- IT unification: Use MFA to secure access to your core stack, gaining visibility for compliance purposes, improved security, and streamlining the overall IT infrastructure.
- Protection from phishing: JumpCloud generates applets for IT resources within its user console, making it more difficult for cybercriminals to spoof login pages to steal credentials.
- Financial cost savings: JumpCloud Protect is included with all bundle packages and the cloud MFA a la carte offering at no extra cost, eliminating the need to pay for additional licensing for this kind of functionality. This includes all customers of the JumpCloud Free package as well.
- Vendor consolidation: Admins will no longer have to manage third-party MFA or authenticator apps. JumpCloud Protect is natively combined with the JumpCloud Directory Platform.
- Enhanced conditional access authentication policies: For customers of JumpCloud’s Platform Plus package, JumpCloud Protect adds an extra layer of security by providing an integrated MFA solution with the package’s Conditional Access policies, triggering verification of an identity based upon a variety of parameters, such as device trust, location, network trust, and application-specific step-up challenges.
- A simplified end user experience: Standard MFA methods are often viewed as cumbersome for end users, such as the insertion of six-digit token numbers into authentication fields or combined with passwords. JumpCloud Protect provides a one-touch authentication method to support employee convenience when challenged with verifying their identity.
- Integrated visibility to validate compliance requirements: IT admins can audit JumpCloud Protect enrollment and authentication events using Directory Insights to validate compliance status against their corporate security policies and external and regulatory compliance frameworks.
How Do End Users Use JumpCloud Protect for MFA?
JumpCloud’s admins and end users can download JumpCloud Protect from the Apple App Store and Google Play Store.

JumpCloud uses clear, accessible language
End users can self-enroll and activate their device through JumpCloud’s User Portal, and they have two options they can select as a second factor: Biometric, Push, and TOTP.
- If a user selects Biometric as the MFA method during the login process, the user’s device will receive approval requests in the form of notifications which the user can use their fingerprint to approve or deny.
- If a user selects Push as the MFA method during the login process, the user’s device will receive approval requests in the form of push notifications which the user can approve or deny. The process is consistent across RADIUS and single sign-on (SSO).
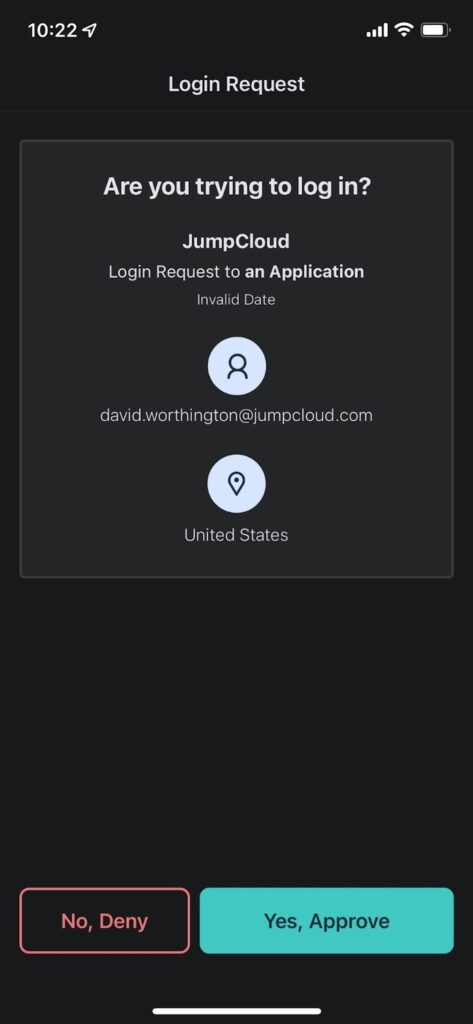
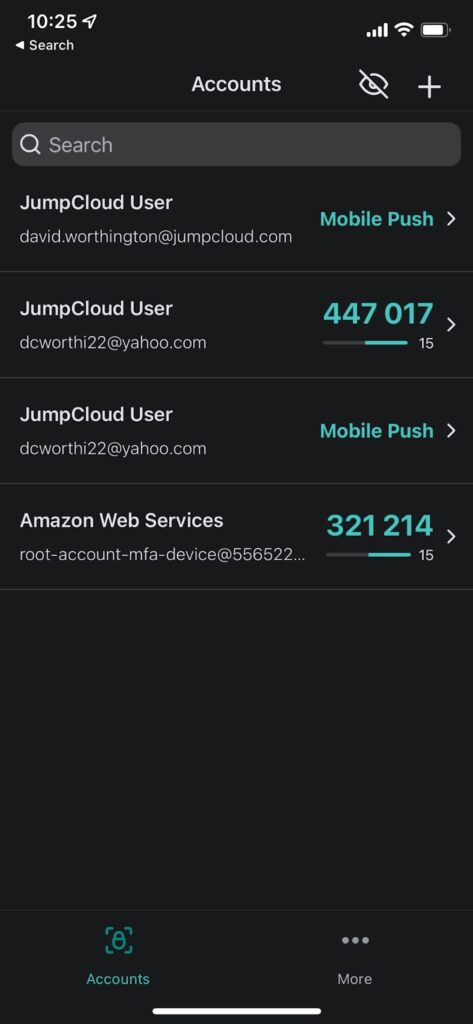
- If the user selects TOTP, the user can enter the code displayed on the mobile app for the associated account to continue the login process.
What Resources Does JumpCloud Protect Support?
End users can use JumpCloud Protect (Biometric, Push, and TOTP) as a factor for the following scenarios:
- User portal login.
- Apps using SAML SSO with both Identify Provider (IdP) and Service provider (SP) initiated flows are supported. JumpCloud also now supports SSO using OpenID Connect (OIDC). Windows, Mac, and Linux devices login.
- RADIUS and LDAP.
- Password management (change and forgot password).
- End users can use JumpCloud Protect with TOTP as a factor for the following scenarios:
- User Portal login, SSO.
- Device login (Windows and Mac) and change password from tray app (Windows) and menu app (Mac).
- RADIUS and LDAP.
Additionally, users can add JumpCloud Protect TOTP as a second factor to their personal online accounts that support this factor.
How Secure Is JumpCloud Protect?
JumpCloud Protect provides the highest level of security in terms of mobile app storage and communication.
- When a device is enrolled and activated for Push MFA, an asymmetric key pair of public and private keys are generated.
- The private key is stored securely on the device while the public key is stored on JumpCloud servers.
- The push requests and responses are signed by the key pair.
Additionally, communication and data exchanged between the mobile app and JumpCloud servers happens over a secure channel.
Why Should Customers Enable JumpCloud Protect?
JumpCloud Protect is natively integrated with JumpCloud’s Cloud Directory Platform, unlike traditional point MFA solutions that are inserted into the access transaction, adding additional overhead to integrate and maintain. Because of this, JumpCloud Protect provides a second layer of security to support device login (across Windows, macOS, and Linux), Admin portal login, RADIUS and LDAP application access.
JumpCloud Protect gives both IT and security teams a path to protection without overcomplicating their infrastructure. For employees, an intuitive, easy-to-use method with less user friction for enrollment and authentication is presented, thereby increasing the chances of adoption and limiting the need for ongoing technical support.





