In the world of identity and access management (IAM), single sign-on (SSO) continues to be one of the most popular tools used by organizations all over the world. There are approximately 15,000 SaaS companies in the United States alone — with thousands more in other countries (Statista). Based on this, it’s safe to say there are more web-based applications available than IT admins and users know what to do with. It also explains the interest in SSO and identity management.
However, it’s important to know the differences between SSO and IAM. SSO is one important subset of IAM, but it does not make for a complete IAM strategy on its own. Yet, many organizations only use single sign-on to connect end users to web applications in their IT environment and call it an identity management strategy, which is incorrect. If anything, it’s a fragmented identity management strategy, and every resource aside from web applications is left unmanaged (or managed with different, unconnected solutions). Whereas, a complete IAM strategy involves understanding, controlling, and managing user identities and access to all IT resources holistically.
In this article, we’ll discuss what SSO and identity management are and how SSO became a part of IAM. We’ll also dive into what questions to pose to make an informed decision on whether your organization only needs SSO or if a more comprehensive IAM solution is needed, as well as what a modern, cloud-based IAM solution looks like.

What is SSO, Really?
Single sign-on is popular, and for good reason, but it doesn’t quite live up to its name. Single sign-on sounds like a tool that enables a user to access every resource they need via a single (successful) sign-on attempt. But this isn’t actually the case — the first generation of single sign-on providers created SSO solutions that simply extended identities from a separate directory (typically Active Directory (AD), but could be any core directory service) to web applications. Therefore, we more aptly refer to these tools specifically as web app SSO tools, which describes exactly what they are.
Web app SSO is also seen as the equivalent of first generation Identity-as-a-Service (IDaaS) solutions, which is another misnomer because these solutions don’t own identities. Rather, the core directory that the web app SSO solution is layered on top of is what actually houses and manages identities. And, since web app SSO tools are typically layered on top of a directory, it means you’ll need to purchase and manage multiple tools to make a solution like this work.
What is Identity Management?
Identity management, or the more comprehensive term identity and access management, ensures that users have access to only the IT resources that they need, and only after first being verified and authorized to do so.
It is too easy for bad actors to breach a user’s identity, especially when it isn’t managed well. Proper identity and access management is the key here, because it builds in security, oversight, and management of both identities and access.
You essentially have two options when it comes to IAM solutions:
Option 1: Manage a variety of tools that are layered on top of one another to handle each aspect of IAM. Keep in mind that this traditional approach often gets costly and out of hand if too many tools are added into the mix. These disparate tools can include:
- A directory
- A directory extension
- Web app SSO
- Privileged account management (PAM)
- Password manager SSO
- Multi-factor authentication (MFA)
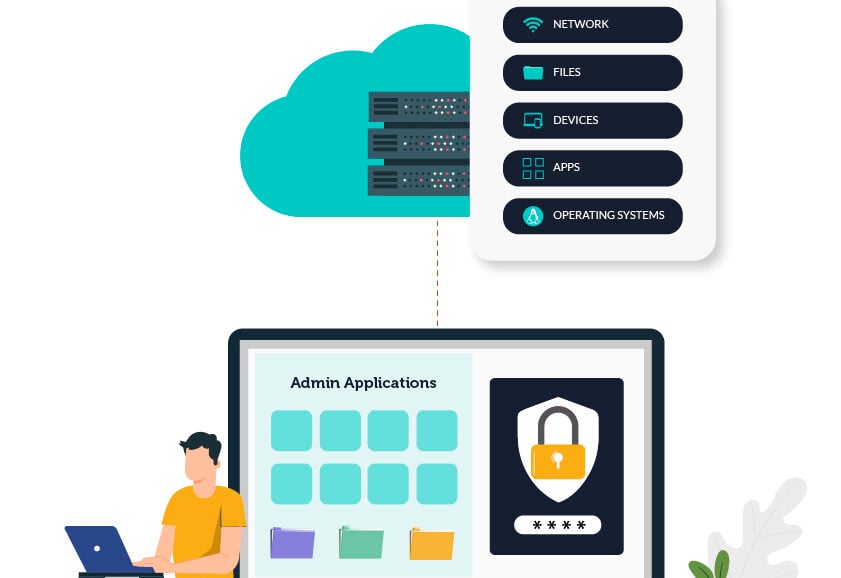
Option 2: Manage a single comprehensive cloud directory platform that functions as a complete cloud IAM solution. Use it to house and manage identities and access while implementing SSO to virtually all IT resources such as devices, networks, cloud infrastructure, legacy and web apps, physical and virtual file servers, and more! On top of that, enjoy MFA, PAM, conditional access policies, and much more, all included in the same modern platform.
Option 2 eliminates the need for on-prem infrastructure and a variety of point solutions while providing your organization with all of the capabilities you need with much more flexibility. It also has the advantage of eliminating the need for directory extensions (given the holistic, open nature of the platform to support multiple protocols, access requests, and resources) and password managers (given the fact that end users have a single set of credentials that consolidates access to virtually all IT resources, not just web applications).
What’s the Difference Between SSO and IAM?
Recent trends like certain IPOs, acquisitions, and announcements in the IAM/SSO industry have made it clear that major players care about this market, and that there’s an active transition away from point solutions like web app SSO to comprehensive IAM solutions happening. This is primarily because single sign-on, especially web app SSO, isn’t a complete IAM solution; it’s only one part of the greater strategy. A true IAM tool contains complete single sign-on capabilities, plus much more.
How Did IAM and SSO Come Together?
The disconnect between IAM and SSO happened in the same way that we’ve seen over and over again, in pretty much every industry:
- A problem arose: Web applications emerged in the early/mid 2000s, which created a large contingency of IT resources living outside of the domain.
- An initial solution was created: Web app point solutions emerged which were layered on top of AD, the reigning directory solution of the time, to bring management of these resources back under the control of the domain.
- As time went on, the initial solution stopped solving the overall problem: More IT resources transitioned to the cloud, new technology was adopted that changed how and where employees worked, and there was an acceleration away from all-Windows-based, on-prem IT environments. This highlighted a much broader need for comprehensive identity and access management, of which web app SSO is only one small part of.
Why Identity Management Is More Than Web App Single Sign-On
Web app SSO allows users to authenticate to web applications with one set of credentials, but they don’t take into account access management regarding other important IT resources. You don’t just log in to web apps at work — everyone has to sign-on to their device(s) and network(s) to just get started. Past that, they might log in to legacy on-prem apps, physical or virtual file servers, and other cloud infrastructure. Now the coverage of web app SSO seems pretty narrow in the grand scheme of things, right?
This is where a modern identity management tool comes into play. A comprehensive IAM platform allows IT to control identities and access levels from one central place. This means using one platform to provision and deprovision user access to virtually all relevant IT resources (not just web apps) regardless of protocol, store credentials, and to ultimately own identities. Putting in place a complete IAM solution eliminates the need for separate web app SSO tools altogether, providing you with more functionality and control within a single pane of glass.
Credential Storage
One big issue with using a web app SSO point solution is the storage and synchronization of credentials. It’s important to consider where these SSO providers pull credentials from. If they house them, how do those credentials sync with what end users are using on-prem? Specifically, what credentials do they use when they access their laptop or desktop, internal WiFi network, internally hosted web applications, or their own servers? If they aren’t in control of the user’s credentials, as is the case with most web app SSO implementations, then they are reliant on a third party solution. That means integration, availability risk, and, of course, increased security risks.
Protocol Usage
Today’s web app SSO solutions are largely based on SAML — one of the standard protocols for web authentication and authorization. However, most internal resources are based on different protocols such as LDAP, Kerberos, and RADIUS, which adds complexity to the lives of IT admins who want to securely and easily connect users to a wider variety of IT resources. A complete IAM platform should be able to handle and support a wide variety of protocols to ensure that users can successfully authenticate to whatever resource they need, regardless of protocol.
Web App SSO Providers Don’t Own Identities
Lastly, the way most web application SSO implementations work is that they sit on top of a directory and federate credentials to web applications. So, they can extend a user’s credentials to web apps, but web app SSO providers don’t necessarily own an identity. This is one reason why web app SSO solutions don’t often act as core identity providers, and it’s also the reason why SSO providers can’t offer the same control and core identity management that a modern cloud IAM platform can.
The solution to all of this? Since the market itself is transitioning away from add-on web app SSO solutions to comprehensive IAM platforms, you should consider following suit within your organization. Doing so will improve security, productivity, and your bottom line when you cut out the hidden costs that come with managing multiple systems, like a directory and separate, third-party SSO solution. A complete cloud IAM solution includes True Single Sign-OnTM capabilities, along with a variety of other features that improve organizational efficiency while simultaneously reducing risk.
What’s the Difference Between Web App Single Sign-On and Modern True Single Sign-On?
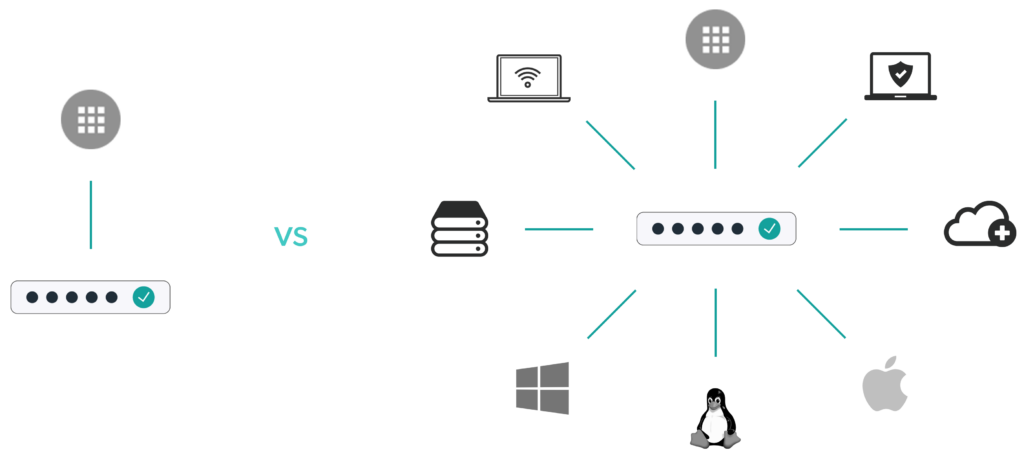
Web app single sign-on solutions connect users to just one category of IT resources: web applications, via a single set of credentials.
The modern version of single sign-on, or what we call True Single Sign-On, is the use of one set of secure credentials across virtually all IT resources such as Mac, Windows, and Linux devices; web apps; legacy apps; networks; physical and virtual file servers; cloud infrastructure; and more.
True SSOTM is included as part of the JumpCloud Directory Platform, meaning that all of the capabilities you need to establish and maintain a modern core IAM solution are contained in one cloud-driven platform. This eliminates the need for the use of multiple disparate tools to manage your IT environment, no matter what types of resources your users need to access.
Considering many organizations are still using first generation solutions like web app SSO and on-prem infrastructure like AD, we can see that there is quite clearly a disconnect between traditional web app single sign-on and full identity and access management using True SSO. It’s important that this disconnect gets addressed to help organizations move forward and modernize their IT infrastructure to mitigate security risks and user productivity concerns.
Choosing an IAM Solution That Fits Your Needs
When considering identity and access management solutions, start by asking yourself the following questions:
- What types of IT resources do I have? Take an inventory of device types, on-prem applications, cloud applications, infrastructure, networking components, etc.
- What access is most critical for me to control? Do I care about managing a user’s access to their devices, applications, networks, etc.?
- What authentication protocols do I need to support? Are all of my services SAML, or do I need LDAP, RADIUS, SSH, or others?
- Do I want to control my users’ devices to ensure that they are secure and safe? If I’m an MSP, are my customers requiring me to contractually agree to user or device management?
- Are security policies and compliance a part of my requirements? Many organizations must comply with specific regulations. If that’s true for my organization, what do the regulations I am subject to say?
These questions are a good place to start because they will help you identify your needs and requirements. For organizations that are largely focused on cloud applications and don’t care about devices or controlling users on those devices, then a web application single sign-on solution may suffice.
However, for organizations that are scaling quickly, housing sensitive data, interested in improving security, or simply planning ahead, their environment dictates a broader view of authentication and authorization. Further, those that are subject to compliance requirements will not be able to meet the standards they are held to just through web application access control — all IT resources should be monitored and managed.
These organizations are interested in controlling access to devices, physical and virtual file servers, on-prem applications, cloud infrastructure, web applications, and networks, among other things — in short, a holistic approach to identity and access management. Their IT environment generally involves a mix of platforms, applications, and locations (on-prem and cloud). In these situations, a comprehensive directory platform is an appropriate choice.

JumpCloud’s Modern IAM and SSO Platform
With the modernization of the IT environment, the traditional concept of web app SSO isn’t enough for many organizations, nor does it rival true identity and access management solutions.
The JumpCloud Directory Platform functions as a core identity provider via the cloud that has built-in True Single Sign-On capabilities that allow users to seamlessly authenticate to virtually any IT resource. While this provides a great experience for end users, it also allows IT admins to gain higher visibility into the IT environment and control identities in a way that’s secure and efficient.
Try JumpCloud’s Solution Free
Test out JumpCloud’s modern, simplified IAM solution with True SSO, and see if it’s right for your organization! Start a trial of JumpCloud to access the entirety of the platform for free.