Updated on December 8, 2025
Today’s employees use multiple applications every day and don’t have the time or mental space to memorize hundreds of passwords. They’re also using many device types and are probably bringing their own device(s) to work. You may think these are unrelated topics, but they aren’t.
Enter: Single sign-on (SSO). Single sign-on models enable users to connect to web apps, file sharing systems, and cloud servers with just one set of credentials, reducing their mental load and speeding up the login process. SSO is ideal for admins, too, increasing their visibility and control and shrinking their queue of help tickets. Yes, SSO can also help to manage devices.
But when organizations start thinking about implementing SSO, they’re likely to come across two methods: identity-initiated (IdP) SSO and service provider-initiated (SP) SSO. It’s not all or nothing, because an IdP can wear both hats. That makes it possible for your team to consume services like device management from another platform if your primary IdP doesn’t offer it.
To ensure you pick the right SSO approach for your company, we’ll explain what each of those terms means, their pros and cons, and how they differ. We’ll also cover identity federation, which makes it possible to access services seamlessly by using your home IdP.
What Is IdP-Initiated SSO?
In plain terms, identity provider-initiated single sign-on uses an identity-as-a-service provider (IdP) to validate an authenticated user’s access to an application.
Organizations use identity providers to store user credentials and authenticate users who attempt to access the company’s network. Many identity providers are OpenLDAP or Microsoft Active Directory implementations, or a cloud-based IdP like JumpCloud.
In IdP-initiated SSO, users navigate to the company’s identity provider and click on the application they want to access.
In the background, the identity provider sends a SAML authentication request to the service provider to ensure the end user has the appropriate access privileges. If the provider accepts the SAML response, the user can log into the application and start their session.
What Is SP-Initiated SSO?
Service provider-initiated SSO flips this scenario — a service provider requests authentication from an identity provider to validate an authenticated user’s access to an application.
When a user wants to log into an application, the application redirects the request to the company’s identity provider. The identity provider confirms the user’s identity and access level and sends a SAML response and assertion to the service provider, allowing the user to log in.
What’s the Difference Between IdP-Initiated SSO and SP-Initiated SSO?
The main difference between IdP-initiated SSO and SP-initiated SSO is where users start the login process. IdP-initiated login requests start in the identity provider, whereas SP-initiated login requests start in the application users want to access.
An IdP-initiated login looks something like this:
- A user logs into the identity provider.
- The user clicks on the application they want to access in the IP catalog.
- The identity provider packages the user’s identity, pertinent information, and what the user can access into an XML-based SAML assertion.
- The identity provider sends a secure reference to the SAML assertion to the service provider or through the user’s browser.
- The service provider reviews the assertion and accepts the assertion as valid.
- The user is logged into the application and can begin their work.
An SP-initiated login looks something like this:
- An unauthenticated user goes to the login page of the application they want to use.
- The service provider redirects the user to the identity provider.
- The identity provider creates a SAML assertion and sends it to the service provider.
- The service provider accepts the assertion.
- The user is logged into the application and can begin their work.
There are pros and cons to both methods of SSO initiation.
Pros and Cons of IdP-Initiated SSO
Pros
- IdP is highly flexible, so IT teams can configure it to fit their specific use cases.
- Some service providers can’t issue SAML requests, making IdP a necessary solution.
Cons
- IdP-initiated SSO is susceptible to man-in-the-middle attacks where the attacker either intercepts or steals the SAML assertion.
- Sometimes, IdP-initiated SSO can overwrite existing sessions within a service provider.
Pros and Cons of SP-Initiated SSO
Pros
- Users can initiate their login straight from the application they want to use, rather than having to log into an identity provider first.
- Since the service provider redirects the request, SP-initiated SSO doesn’t typically cause session overwriting.
Cons
- Some service providers can’t issue SAML requests.
- SP-initiated SSO may be more challenging to troubleshoot if there is an error on the service provider’s end.
Identity Federation
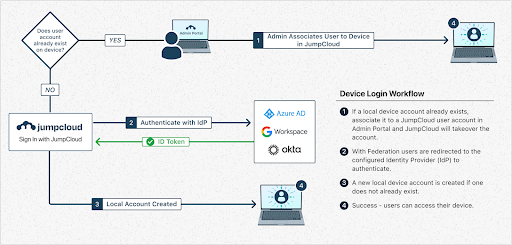
An IdP can also act as a service provider when it needs to access resources or services from another domain. If your IdP needs to access a service in another domain (e.g., for device management), it becomes the SP. Federated identity allows authorized users to access multiple applications using a single set of credentials, enhancing security and efficiency. An IdP typically handles user authentication and identity verification when this trust relationship exists.
For example, JumpCloud makes it possible to configure Google, Entra ID, or Okta as a trusted external IdP to allow users to login with these IdPs to access JumpCloud resources. Federated authentication allows you to configure a trusted, external IdP as a source of user authentication in JumpCloud. Users maintain all their group, device, and directory associations, but authenticate with a trusted IdP. It’s made possible by OAuth OIDC, an open standard.
In practice, users login into JumpCloud with the trusted IdP that they’re familiar with. This login takes place within the context of the external IdP and JumpCloud never sees the user’s password or any other secure credentials they may use during authentication.
Mitigating the Risk of SAML IdP-Initiated SSO
There are three main ways to reduce the risk of man-in-the-middle attacks with IdP-initiated SSO:
- Use minimum possible response trust length – Part of SAML assertion validation involves reviewing when packages expire and when they were issued. Therefore, IT teams should configure their IdP with the minimum length of time to trust responses to leave less time for interception.
- Leverage replay detection – Some cyberattackers attempt to reuse SAML assertions to gain access to company applications. Installing a replay detection platform can reduce the chances of unauthorized access. These tools assess whether an assertion has already been seen, preventing it from being reused.
- Follow the specification – SAML 2.0 specifications include a section regarding unsolicited responses that can safeguard companies from SAML theft. IT teams should ensure that service providers in their IdP-initiated SSO workflow do not accept unsolicited SAML responses with an InResponseTo value.
While none of these methods are sufficient when used alone, implementing all three together minimizes your attack surface.
Secure IdP-Initiated SSO with JumpCloud
It’s important to note that both methods of single sign-on involve the use of an identity provider. When storing sensitive information in a third-party authentication service, you run the risk of the IdP mishandling data or being the target of a cyberattack.
That’s why it’s critical to work with an SSO provider that can help you layer on additional security controls and IAM capabilities. JumpCloud is an IdP for the modern enterprise, securely connecting users to resources regardless of location, platform, or provider. JumpCloud supports globally used applications like Salesforce, Atlassian, and Google Workspace, file storage providers like Google Drive and Dropbox, as well as major servers like GCP and AWS.
How JumpCloud Can Help
JumpCloud protects users on the back end while providing an easy-to-use front end, giving both your IT team and employees an ideal SSO experience. It also provides a complete cross-platform device management and MDM package for federated scenarios.
Cross-OS device management is a critical technical component of a BYOD strategy. Identity federation helps to consolidate device management tools into a single console for increased operational efficiency. It has optional remote assist, privilege management, and cross-OS patch management. You can try JumpCloud for free to determine if it’s right for your organization.
You may also check out these guided simulations to see how federated identity works.
Frequently Asked Questions
What is the difference between IdP-initiated and SP-initiated SSO?
IdP-initiated SSO starts the login process at the identity provider, while SP-initiated SSO begins at the service provider, where the user tries to access an application.
How does IdP-initiated single sign-on work?
In IdP-initiated SSO, users log into the identity provider, select the application they want to access, and the IdP sends a SAML response to the service provider to log the user in.
What are the pros of using SP-initiated SSO?
SP-initiated SSO allows users to log in directly from the application, enhancing usability and reducing the likelihood of session overwriting compared to IdP-initiated SSO.
Is IdP the same as SSO?
No, an Identity Provider (IdP) is a service that authenticates users and offers access to applications, while Single Sign-On (SSO) is a user authentication process that allows users to log in once and gain access to multiple applications.
What are security implications of IdP-initiated and SP-initiated SSO?
IdP-initiated SSO can be vulnerable to man-in-the-middle attacks, whereas SP-initiated SSO may present troubleshooting challenges if issues arise on the service provider’s end.