Active Directory’s (AD) trust relationship flows are a familiar concept to many IT admins who are charged with mapping out which authenticated users can access which network resources across domains. Configurations can be complex and trust extends beyond AD to the entire IT infrastructure, your counterparts at the other organizations, and ultimately all of its users.
Modernizing AD means adopting cloud services that have more of a flat organizational structure. Users from other organizations are segmented into groups where external users are granted the appropriate entitlements, their devices are managed by unified endpoint management (UEM), and identity and access management (IAM) enforce memberships. Continuous evaluation takes the place of AD domain and forest trust relationships.
This article provides an overview of how legacy trust relationships are managed through lifecycle automation and IAM security controls in cloud directories, modernizing AD while reducing risks and infrastructure costs. In turn, identities and devices of all kinds can be challenged before access, aka “trust,” is granted. It also compares Entra with JumpCloud’s open directory and how they’re used to modernize AD.
Cross-Domain Trusts
Active Directory Domain Services (AD DS) interdomain forest trust relationships provide a way for authentications to be trusted across domains. A login on one domain is trusted by another because there are “bonds” between the domains in a forest or tree. This configuration simplifies user and service access to global resources and centralizes administration and security.
There are many benefits to this hierarchical approach, and it’s understandable that admins who are well acquainted with AD would expect the same from a cloud directory. However, this approach, like AD itself, was intended for a different era in computing where networks were the only perimeter versus a cloud directory, which explicitly validates trust for all access requests.
AD doesn’t take a modern Zero Trust approach to security where you “assume breach” and “trust nothing.” Trust is generally inherent in AD domain trusts. Consider that you not only place trust in a domain, you also trust an entire infrastructure, all of the endpoints, people, and its processes. Let’s explore what AD domain “trust” actually means from a cybersecurity perspective.
Trust in IT Infrastructures
With AD, you trust a domain’s encryption, network segmentation, and threat protection at the highest level. The full scope of a domain’s network infrastructure includes numerous considerations ranging from endpoints to network configurations to physical security.
Ask yourself what you’re trusting:
- Endpoints: Are endpoints and servers being patched? Do they have Endpoint Detection and Response (EDR) deployed? Are there policies managing Windows endpoints in AD? Are non-Windows services being managed? Is data being backed up?
- Active Directory: Is Enhanced Security Admin Environment (ESAE) architecture being followed to follow a privileged access strategy for admins? Is there an appropriate focus on identity lifecycle management or identity protection to prevent lateral movement through AD in the event of a breach? Do you fully trust those configurations? Are less robust legacy authentication protocols such as NTLM being used for compatibility? Do you have full visibility into event logs and other indicators of attack?
- Networks: Is firmware on switches and firewalls being updated? Is the filtering and security adequate to detect and prevent security incidents? Is there multi-factor authentication (MFA) deployed in that infrastructure? Are solutions such as Security Information and Event Management (SIEM) being used and are those supported well enough?
- Physical security: Are server rooms and other network assets being secured? Are there procedures to log and limit access to sensitive infrastructure? Is there a disaster recovery plan to ensure business operations in the event of a catastrophe?
Trust in People
You not only trust your admin peers; you trust all of their users (and vendors). You trust their hardware and software supply chain. You trust how well insider threats are being recognized and handled as well as the organization’s level of security awareness.
No Zero Trust Controls
- AD lacks continuous access evaluation
- AD lacks native support for MFA, whether hardware or software based
- AD lacks privileged access management
- AD has no conditional access for devices and users
Ultimately, AD doesn’t meet modern IT requirements by itself. Traditional domain trusts are insufficient to meet the objectives of a Zero Trust security strategy. Microsoft recognizes this and strongly recommends that organizations that use AD for their identity security strategy also adopt its cloud security solutions including Defender for Identity and Defender for Endpoint to identify security incidents and orchestrate a response to compromised identities/devices.
Microsoft Defender for Endpoint is also recommended if you to extend monitoring to server threats, which also places Microsoft in control of your Endpoint Detection and Response (EDR).
Modernizing AD with Cloud IAM and UEM
Microsoft takes an enterprise approach to solving collaboration challenges while JumpCloud works best for small and medium-sized enterprises (SMEs) that have limited IT resources and are seeking more straightforward solutions. Microsoft extends AD with Entra ID’s premium tier of identity governance and a variety of licenses for security services. JumpCloud combines AD integration with automated lifecycle management through dynamic groups and built-in UEM, delivering a Zero Trust security strategy with identity governance and administration.
Microsoft’s Monolithic Approach
Microsoft recommends using a single Entra ID cloud tenant (when possible) for consistency in how resources are supported, managed, and governed. A common topology is to have one AD Connect sync server sync one of multiple domains from a forest to Entra. Otherwise, multiple forests must be reachable by a single server that’s placed within a DMZ or screened subnet.
Deploying multiple tenants is more complex, but supported by Entra ID’s enterprise collaboration feature where external users from trusted domains are given user objects in the directory. Access packages are used to grant entitlements, which authorizes user access to apps and groups. Device claims and MFA is trusted from other Entra ID tenants, but Entra handles the AuthN/AuthZ and clearing the B2B relationships for tenants, i.e., “domains.”
Entra’s enterprise IAM features are available for those applications and identities. Microsoft’s reference architecture then prescribes using its security services to monitor identities and AD. It’s possible to consolidate your domains’ management and security with this stack, but one price doesn’t mean “integrated.” The automations and workflows aren’t trivial, and change is constant. The preferred practice is to engage with a vendor, indefinitely, to maintain it all.
Premium licenses are required for access reviews, and your team (and potentially dedicated new hires) must be qualified to use it all. Entra’s enterprise features are robust, but aren’t easily understood. Admins must understand how to use access packages, which premium licenses to use, and how to configure the appropriate RBAC roles for guests, or be comfortable with using privileged admins to make approval decisions to support your cross tenant ID workflows.
A new cross-tennant synchronization feature is in preview.
Note: Privileged access in hybrid AD environments means subscribing to Azure ID Identity Protection, a premium tier feature. Defender for Identity is a separate subscription recommended to check for signals of compromise in on-premises AD. Otherwise, it’s possible for attackers to move laterally through the Microsoft stack to your domain controllers.
JumpCloud’s Open Directory Platform
JumpCloud is an open directory platform that manages identities as a standalone identity provider (IdP) and through federation with other IdPs. It includes unified endpoint management (UEM) to secure access from every device from Android to Apple products to Linux and Windows, using either agents or mobile device management (MDM). JumpCloud supports web authentication and common network protocols, and API provisioning, all from the cloud.
Supported protocols include:
- SAML and OIDC
- LDAP and RADIUS
- Pre-built integrations with popular HR systems
- JumpCloud also offers a secure decentralized password manager with business collaboration features and management for when SSO isn’t an option
Authentication and authorization features:
- JumpCloud Go, a phishing resistant hardware-bound credential that delivers passwordless modern authentication
- Easy to use conditional access policies for privileged access control
- Certificate-based authentication for RADIUS
- Platform-wide push MFA and TOTP
- WebAuthn
- SCIM provisioning
Cross-OS system and browser patch management is also available as an add-on.
JumpCloud can be used as part of your identity security strategy to modernize AD while keeping your IdP independent. Crucially, its approach reduces complexity for the admins who implement and support your systems. JumpCloud makes it possible for a smaller team to accomplish more out of the box without having to enlist outside vendors and consultants to implement it.
Read about how JumpCloud compares to Entra ID and Intune.
JumpCloud’s Active Directory Integration (ADI) integrates AD with the open directory platform. There are several options for configuring AD and JumpCloud, depending on your company’s needs and objectives. Recent enhancements include a more scalable deployment model that’s deployed on a member server within your domain to configure syncing. It’s also now possible to sync multiple domains to JumpCloud at once. Delegated authentication (similar to passthrough authentication) leverages existing credentials from AD without forcing password resets.
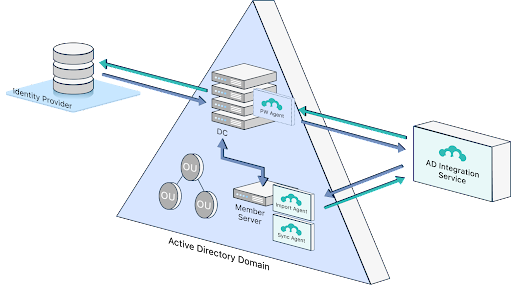
How Is JumpCloud Different from Microsoft?
JumpCloud utilizes dynamic groups to scale how admins manage users and devices from a single pane of glass. Entra has dynamic groups, but expressions must be created by admins and Intune’s device management is a separate product. JumpCloud’s rules-based automation is pre-built and foundational. Dynamic groups use attributes from your AD (or HR systems) to improve your security while optimizing IT management. Ultimately, admins can spend less time working on onboarding and lifecycle management tasks and more time on higher priorities.
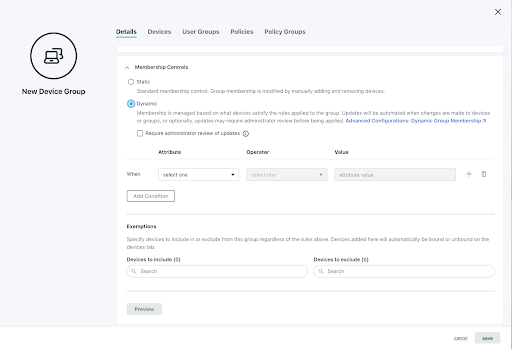
Dynamic groups provide for automated “access reviews” without premium pricing or having to reskill your team to use enterprise identity governance solutions from Microsoft. This governance is applied to your domains as you integrate them with JumpCloud’s open directory. AD will be modernized without starting over and ripping out everything that you’ve built. Authentication is also stronger than Kerberos, and is separate from Microsoft’s security stack.
The combination of dynamic groups and JumpCloud Go, with unified IAM/UEM and broad support for common authentication protocols, makes modern authentication more practical to deploy. Many organizations are breached when MFA solutions aren’t fully utilized and gaps exist in coverage. Most organizations deploy more than Windows devices, but Windows Hello, Microsoft’s modern authentication solution, won’t integrate at the device-user login level beyond Windows. Management costs and security risks increase when non-Microsoft products and solutions such as Google Workspace and MacOS devices exist in siloed authentication flows.
JumpCloud’s unified IAM/UEM platform breaks down silos for defensive security uplift against cyber threats. It unifies disparate source domains when it’s used for AuthN/AuthZ to your resources; you gain visibility into the activities that occur across multiple domains and what resources users are logged into. Integrating your preferred security tools with JumpCloud can leverage those events to identify incidents and orchestrate a response.
To be clear, JumpCloud isn’t an SIEM but it features built-in reports as well as integrated tools called Directory Insights and System Insights for event logging and compliance.
Ultimately, JumpCloud makes many of the “premium” features found in Entra and Intune more accessible while preserving flexibility, provides the choice to use best-of-breed solutions without compromising on Microsoft monoculture, and gives you greater control over your identities.
Schedule a JumpCloud Demo
Schedule a demo to discuss how JumpCloud modernizes AD and to learn more about our options for implementation assistance, migration services, custom scripting, and more.
Having one price doesn’t mean that it’s integrated. Find out more about the costs and risks of adopting Microsoft 365.




