The identity lifecycle management (ILM) process involves managing user identities and their access privileges from the beginning to the end of their involvement with your organization.
This process begins on an employee’s first day and continues throughout their employment, specifically when they change roles or need their access privileges altered. The process eventually ends once they have departed from your organization, all access has been revoked, and their digital identity is suspended, permanently revoked, or deleted entirely.
What Are the Phases of Identity Lifecycle Management?
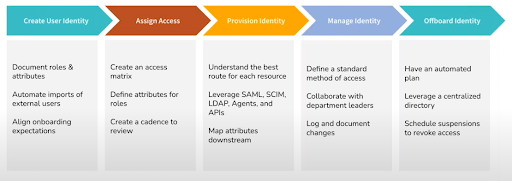
The phases within the identity lifecycle management process are:
- Identity creation.
- Onboarding.
- Monitoring, reporting, and maintenance.
- Offboarding.
1. Identity Creation
The first step in managing the identity lifecycle is to create the digital identity that will be managed moving forward. Digital identity creation usually happens shortly before or on a new employee’s first day. The first iteration of their digital identity is often created in HR’s software which is commonly referred to as an HRIS tool.
HR gathers the relevant information from the new employee, uses it to create their digital identity, and associates a role or title to that identity.
2. Onboarding
Once the new employee has an active digital identity in HR’s software, it must also be created within IT’s software.
Onboarding With Modern Tool Integrations
The easiest, fastest, and most secure way to do this is through a built-in integration between the IT and HRIS tools being used. In this scenario, the identity created in the HRIS tool is automatically imported into the IT software through the integration.
Once imported, the role associated with the identity in the HR software tells the IT tool what access needs to be provisioned. This is often done via groups that have certain access to resources provisioned to them, so when a new identity becomes associated with a group, the proper access is immediately assigned.
Onboarding Without Modern Tool Integrations
In all other scenarios without this useful integration, this phase of identity lifecycle management is much more difficult and time-consuming. In this case, HR and IT need to be in communication about when a user starts, what their role is, and what access they need. Then, come day one of their employment, HR and IT need to quickly create separate but mirrored identities in each tool.
After that, IT needs to manually provision access to each resource needed for that employee’s role while also ensuring that the principle of least privilege access is followed, but that enough access is provisioned for that employee to be productive right away. If multiple new employees are being welcomed on the same day, managing onboarding gets exponentially more difficult and tedious, significantly increasing the chances for human error to occur.
The consequences of this can be disastrous for productivity or security, depending on how little or how much access is wrongly provisioned.
Other Onboarding Management Tasks
The other primary identity lifecycle management task that needs to happen during onboarding is email creation. The new employee’s email address will be an important identifier moving forward, so it needs to follow the specific naming conventions that your organization adheres to. This email address will need to be set up in order for resource access to be granted appropriately.
While there are many other tasks that fall under the scope of onboarding, those tasks are not specific to identity lifecycle management.
3. Monitoring, Reporting, and Maintenance
The third phase of the identity lifecycle management process involves a few different but related tasks:
- Monitoring access levels to ensure no accounts are over or underprivileged as time goes on.
- Reporting on identities and access to prove that compliance has been achieved and security standards are being adhered to.
- Ongoing access maintenance during role or responsibility changes.
To fully understand how these tasks are related, think about it this way:
Constant access monitoring allows you to be aware of who has access to what and why, and to see and respond to security events in a timely manner.
Reporting on the access that you’re already aware of allows you to prove compliance and complete audits with fewer unexpected hiccups along the way.
And, staying on top of access maintenance allows you to remain secure and compliant as access needs change.
Preventing Privilege Creep
While initial access rights are given during onboarding, ongoing access monitoring and maintenance is a valuable way to prevent privilege creep. As individuals change roles and gain new or let go of certain responsibilities, the access needs of users change. It’s essential to stay on top of this maintenance to keep your org secure and compliant. Learn more about privilege creep and addressing other challenges with identity lifecycle management.
4. Offboarding
The final phase of identity lifecycle management is offboarding. Proper offboarding is essential for maintaining security across your organization, because ex-employees that retain access to any of your resources are a threat. To mitigate this potential threat, IT must revoke access and deprovision identities in a timely, complete, and secure manner.
Let’s go back to the two scenarios highlighted in the onboarding section: scenario 1 involves a smooth integration between HR and IT tools, and scenario 2 has a lack thereof.
Offboarding With Modern Tool Integrations
With a modern HR and IT tool integration, the departing employee’s digital identity is removed or suspended within the HR software. This action then prompts the connected directory to also revoke that identity, as well as all of the access provisioned to it. When HR and IT tools are connected, offboarding becomes seamless, quick, and secure.
Now, both HR and IT need to do one final check to ensure that all offboarding boxes have been checked, and nothing has been overlooked.
Offboarding Without Modern Tool Integrations
However, without a seamless connection between HR and IT software, offboarding can be an inefficient and insecure process. HR is likely the first department to find out an employee is departing, so they’ll revoke or suspend the identity when it’s appropriate. However, IT may not find out about the departure in a timely manner, which leaves departed users with access to company resources that might include sensitive information. Improper offboarding like this can pose huge security risks for your organization.
Even if IT does find out that an employee is leaving in a timely manner, it’s very time-consuming and tedious to manually remove all access from each departing identity. Plus, IT has a variety of high-priority tasks on their plate each day, so revoking access might not happen immediately, once again opening up your organization to unnecessary security threats.
The entire identity lifecycle management process benefits greatly when cross-departmental software integrates well, efficient processes are in place, and communication between teams is timely.
ILM for External and Guest Identities
Another important part of the identity lifecycle management process is the management of external and guest identities. Many organizations deal with this because they employ contractors or seasonal workers, or because they need a way to manage partner and vendor identities. These external identities often need to exist in the organization’s infrastructure to promote smooth collaboration and simplify access management across the board.
While the ILM process for external and guest identities is very similar to that of internal, long-term employees, there’s an increased need for an identity suspension functionality in the directory being used. This is because these identities are revoked and created, or re-created, far more often than those of internal employees. When IT is able to simply suspend an identity, automatically revoking access until the suspension is removed, it’s much easier to manage external and guest identities and access.
JumpCloud’s Identity Lifecycle Management Solution
JumpCloud’s open directory platform simplifies identity lifecycle management across all of your internal and external identities. Not only does it provide you with one location to remotely manage identities and access on Windows, macOS, and Linux devices, but it also integrates smoothly with your HRIS platform of choice.
Use these capabilities to easily manage identities and provision and deprovision access via SAML SSO, JIT provisioning, and SCIM. From there, use JumpCloud Insights to monitor and log events across all identities.







