It’s the worst-kept secret in IT: small and medium-sized enterprises (SMEs) must use their budgets judiciously. The cost of network hardware, in particular, can be a major obstacle that places constraints on what IT admins can accomplish. The domainless enterprise presents a solution, minus the expensive hardware to manage your directory and access control (and especially your VPN). This makes strong perimeter security achievable at sustainable costs.
JumpCloud provides identity and access management (IAM) infrastructure through the cloud that you can configure to manage Pritunl, an open source VPN that’s based on OpenVPN. JumpCloud provides your directory of users and devices or will extend your existing directory. OpenVPN is a mature, widely used solution that’s been available for over two decades. It’s functionally the same as VPN appliances that you’d pay a reseller to obtain at high cost.
The benefits extend beyond connectivity: JumpCloud layers on additional Zero Trust security controls that are transparent to the end user beyond being prompted to authenticate themselves when they’re accessing IT resources. This solution protects your confidential information and systems while reducing the costs that are traditionally associated with remote IT access.
JumpCloud Manages and Secures
JumpCloud’s LDAP directory underpins access control and has integrated Zero Trust security features that continuously authenticates and authorizes users. The cloud directory extends to single sign-on (SAML SSO) to direct users to the JumpCloud portal for authentication. JumpCloud then layers on security features, including environment wide multi-factor authentication (MFA) and conditional access, to determine which devices may access your VPN and from where.
Other features manage and secure your devices, cross-OS, with patching and pre-built policies that act to harden systems against common security exploits. Conditional access leverages these capabilities so that only compliant devices are granted access to your VPN. This added security is accomplished without installing and maintaining additional software or hardware.
Streamlined User Lifecycle Management
The JumpCloud directory handles permissions differently than traditional on-premise solutions such as Microsoft’s Active Directory. They’re similar in that access to your VPN is determined by group membership(s), but JumpCloud’s user management is designed for the modern era. JumpCloud utilizes attribute-based access control (ABAC), which suggests membership changes when a user should (or shouldn’t) have access to IT resources. Attributes such as “manager” are actively polled to verify memberships, which saves time managing users and helps IT admins avoid potential security issues from internal and external threat actors.
This capability isn’t limited to the JumpCloud directory. Our platform integrates and extends existing directories such as Active Directory, Azure AD, or Google Workspace. JumpCloud’s platform provides vital cross-OS Zero Trust management and security that those systems lack.
Now, let’s discuss how to get started with integrating JumpCloud and Pritunl. Detailed guidance about how to install or subscribe to Pritunl managed services can be found on its website.
JumpCloud Setup
The initial step is to create a custom SSO connector for Pritunl. JumpCloud provides hundreds of free connectors as part of your subscription, and is routinely adding more, so search for it before you move ahead with this project. Continue to the next section if one isn’t available.
Create a SAML Connector
Click the SSO button in the left frame of the administrative console and hit the “plus” sign to start a new SSO connection. Select “Customer SAML App” and begin by filling in the requisite information to label your connector and choose a color scheme and logo. More context is available in JumpCloud’s SAML how-to article should you have any additional requirements.
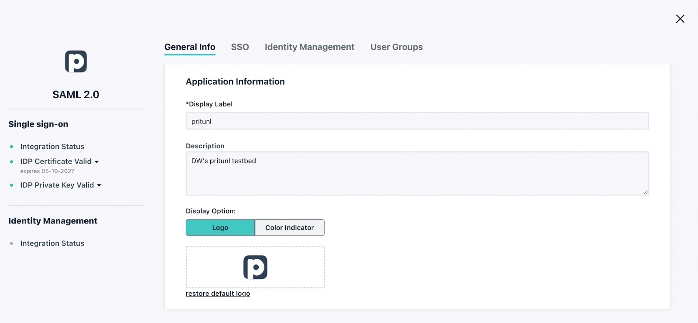
Then, navigate to the SSO tab and enter an Entity ID that’s unique to your organization’s environment. The settings on this screen are case-sensitive on both systems; any typo will result in errors and the integration will fail. Your Pritunl FQDNs and JumpCloud IDs may differ, but the fields should be formatted as outlined below:
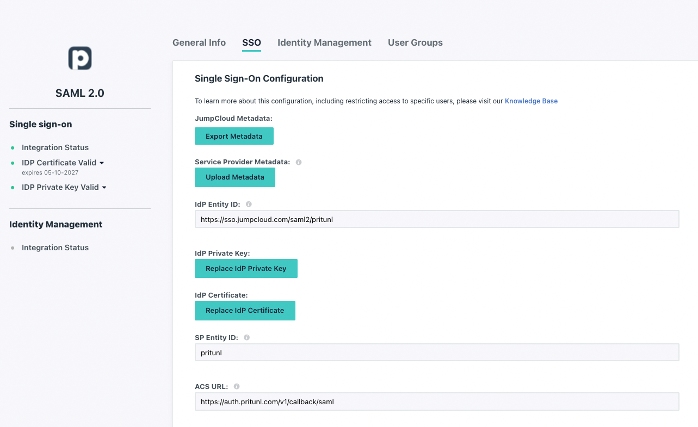
Follow the URL/URI formats precisely
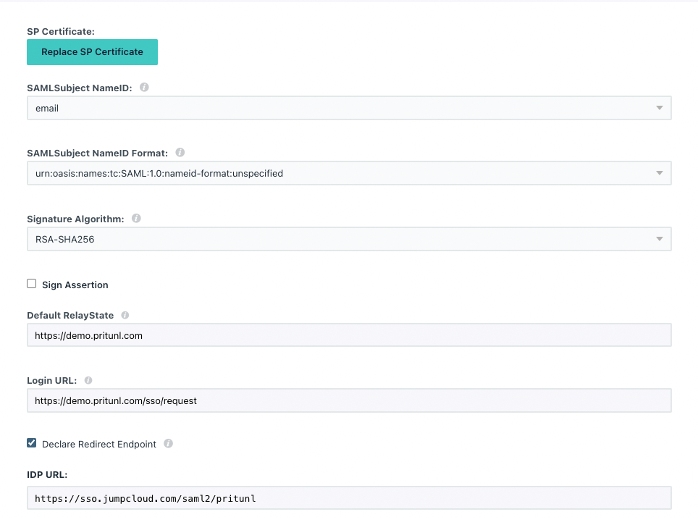
The redirect endpoint ensures that JumpCloud’s console will be used to log users into the VPN
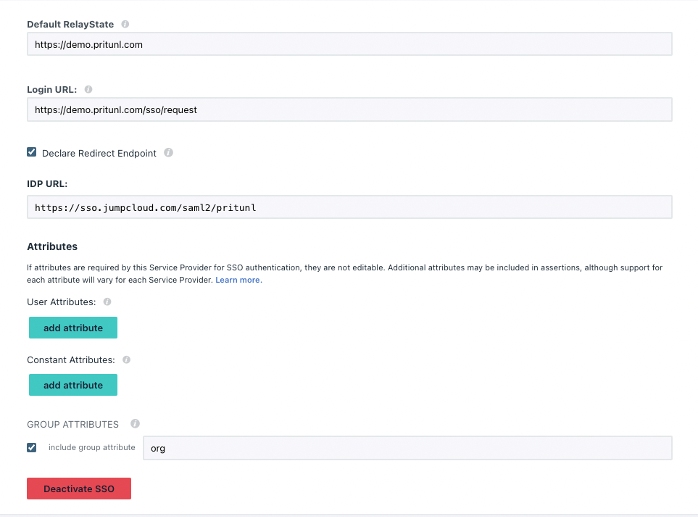
Pritunl requires the “org” attribute for group memberships
Activate the JumpCloud SSO connector once you’re finished and download the certificate. You’ll be required to copy the key into Pritunl’s GUI in a later step.
Setup Groups and Permissions
Click on the User Groups tab and add the group(s) that should have access to the VPN service. The link below is a detailed guide for admins who are unfamiliar with using JumpCloud.

Group membership grants access rights to the VPN
Pritunl VPN will be available within the JumpCloud User Console
Pritunl SSO Setup
Pritunl has JumpCloud listed as an authentication provider. Pull down the list, select JumpCloud, and select “add provider” to start the process of filling in Identity Provider settings.
The settings will be identical to what you entered into the JumpCloud admin console. Cut and paste the certificate from a text editor when you open the certificate on your PC. This integration also requires a JumpCloud API key from your console, which will be outlined in the next section. Both of these entries are confidential and should be kept private and carefully controlled.

Your JumpCloud API key may be reviewed by clicking on your user icon at the top right of your console. Note: Generating a new key will revoke prior keys and could break prior integrations.

You’re now ready to test your configuration.
Add Zero Trust Security from JumpCloud
Strongly consider adding Zero Trust security controls with JumpCloud Conditional Access Policies. These policies extend security beyond strong passwords and MFA alone.
Policies are assigned to existing groups or you may create dedicated groups for your requirements. Different groups may have different policies (or no policies). Policies include:
- Geofencing: JumpCloud permits you to whitelist selected countries to access your VPN. Any devices that attempt to log in from locations that aren’t specified will be denied access. For instance, an employee may be attempting to access internal resources from unsecured hotel Wi-Fi while on vacation.
- Managed devices: Limit access exclusively to JumpCloud managed devices. This ensures that IAM isn’t allowing rogue devices into your network.
- Mandatory MFA: Users must prove who they say they are prior to accessing the VPN by entering a TOTP MFA code or Push MFA through the JumpCloud Protect™ application. This extends MFA beyond initial device/session logins for additional assurance, which is advisable given the current threat landscape.
Tip: Retest your connectivity prior to making changes that could adversely affect user access.
Try JumpCloud SSO with Conditional Access
Zero Trust security should be used in combination with perimeter-based security. You can save budget by using Pritunl with JumpCloud, and use JumpCloud to manage VPN access. The platform is free to use for up to 10 users/devices. Existing users should contact their JumpCloud implementation manager to begin testing conditional access.




