Your organization’s strategy for password expiration dictates how long JumpCloud user account passwords are valid and when users need to change their password. This allows your organization to implement security policies that meet your compliance standards.
JumpCloud’s password expiration options let you:
- Set a password lifespan for your organization.
- Require new users to change their temporary password the next time they log in.
- Immediately expire individual user passwords.
Configuring the Password Aging Settings for Expiration
JumpCloud’s Password Aging settings for expiration apply globally for your entire organization. Access and manage these settings from Settings > Security > Password Settings. Learn more in Manage Password and Security Settings.
Considerations:
- Individual users can be exempted from password expiration. See Get Started: Users.
- If a password expires, users will remain logged in as long as they are active. Once they become inactive, such as when the device goes to sleep, the user will be locked out of their account and will need to change their expired password to log in. Learn more in Unlock User Accounts.
- Alternatively, you can configure the actions taken when a user's password expires for Google Workspace, RADIUS, LDAP and M365/Entra ID via the JumpCloud API.
- Settings don’t apply to the JumpCloud Menu Bar App.
- You can’t modify the password expiration notice on the JumpCloud Menu Bar App/Windows App. Users on JumpCloud-managed Mac and Windows devices are encouraged to update their passwords in the JumpCloud Menu Bar App to keep their passwords in sync with Keychain, FileVault and other apps.
- For MacOS, see Manage MacOS Passwords.
- For Windows, see Manage Passwords Using the JumpCloud Windows App.
To manage Password Aging settings:
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Settings > Security.
- In the Password Settings section, set appropriate Password Aging options for your org
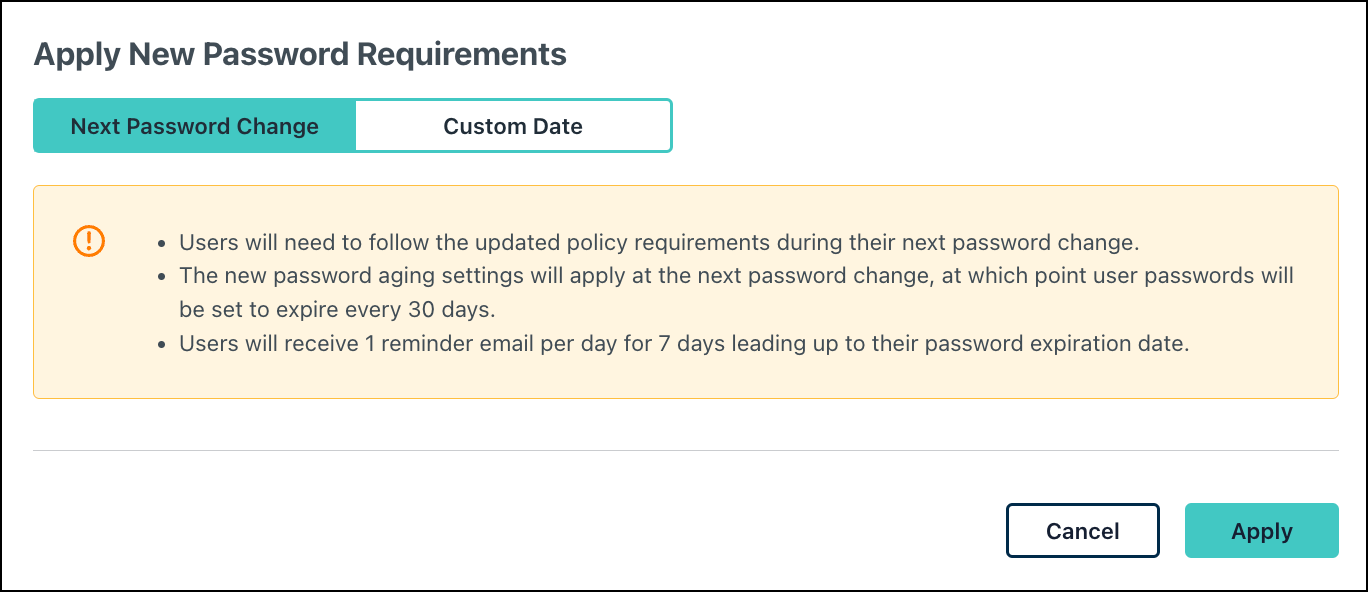
- Click Save to implement your changes. A confirmation modal appears.
- Users will need to comply with the updated aging setting on their next password change. Click Apply to confirm.
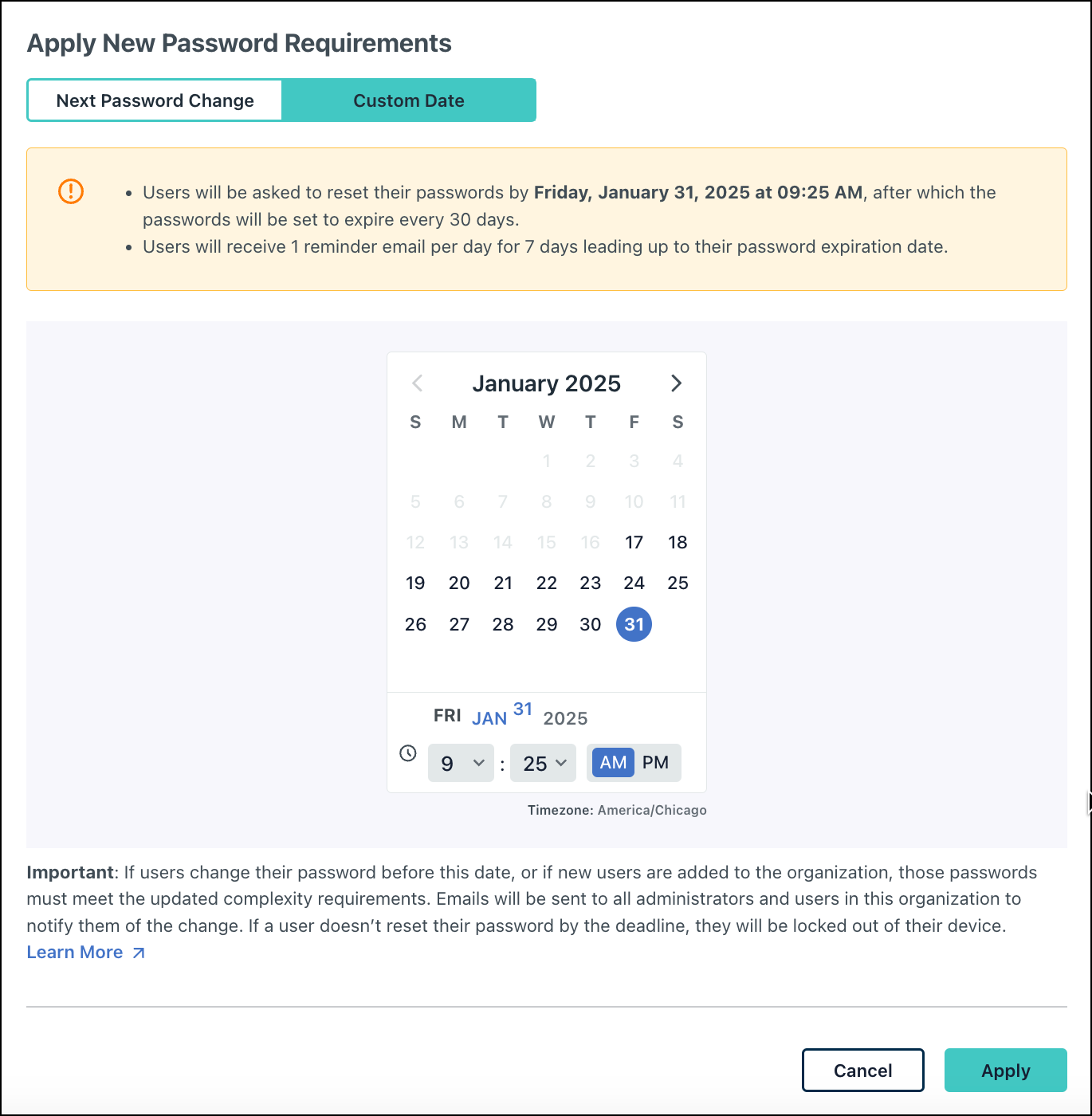
- If you prefer to set a custom date by which this setting will take place, click Custom Date and select the target date from the calendar.
- New users added before this date must adhere to the updated password aging settings. If existing users reset their password before this date, their updated password must adhere to the new settings.
- New users added before this date must adhere to the updated password aging settings. If existing users reset their password before this date, their updated password must adhere to the new settings.
You can set the following settings for password expiration:
- most recent passwords cannot match each other (limit historical reuse): Specifies the number of unique passwords a user has to create before they can reuse a previous password. Enter a number between 1-24.
- N daysuntil password expiration: Specify the lifespan (in days) of passwords for your organization. If you don’t choose to expire passwords, they’re valid indefinitely. After the lifespan expires, users must change their password.
- N days prior to password expiration, require password reset at login: If you choose to expire passwords, you can require users to reset their password for a certain number of days before their password expires. This option helps ensure that access to password protected resources isn’t interrupted by requiring users to change their password before it expires.
- Allow password change after expiration: You can allow users with expired passwords to change their password from their JumpCloud-managed device, alleviating the need for admins to manually reset user passwords. There are some considerations before enabling this, however:
- After you expire a user’s password, it’s immediately invalid; the user is logged out of their device and connected resources, and is required to change their password from their JumpCloud-managed device the next time they log in.
- If you’ve required MFA for the User Portal, your users will need to verify their identities using one of the configured methods.
- If you haven’t enabled the Allow password change after expiration setting for your organization and attempt to expire a user’s password, you can either enable the setting for your org or cancel the password expiration. If you enable the setting for your org, all users with expired passwords are able to reset their password from their JumpCloud-managed devices.
Managing Password Expiration for New Users with Temporary Passwords
When you create new users, you can give them a temporary password. To make sure users change their password to a private, secure password quickly, you can require that they change their password the next time they log in to their JumpCloud-managed device.
Read considerations for Allow password change after expiration.
To require a new user to change their temporary password:
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to User Management > Users.
- Click ( + ), then select Manual user entry. Learn about creating users: Get Started: Users.
- On the New User panel’s Details tab in the User Security Settings and Permissions section, first, select the Specify initial password, then enter a temporary password for the user.
- Next, select the User must change password at next login option. If you haven’t enabled the Allow password change after expiration setting for your org, you’re notified on the Force Password Change modal. You can choose to enable setting for your org by clicking force change, or choose not to by clicking cancel. If you enable the setting for your org, all users with expired passwords are able to reset their password.
Managing Password Expiration for Existing Users
You can manually expire passwords for individual users from the User panel.
Read considerations for Allow password change after expiration.
To immediately expire a user’s password and force them to change their password:
- Go to User Management > Users.
- On the Users page, select a user to view their details.
- Click the user’s password status, then select Force Password Change.

- If you haven’t enabled the Allow password change after expiration setting for your org, you’re notified on the Force Password Change modal. You can choose to enable this setting for your org by clicking force change, or choose not to by clicking cancel. If you enable the setting for your org, all users with expired passwords are able to reset their password.
Managing Password Expiration for Multiple Existing Users
You can manually expire passwords for multiple users from the Users list.
Read considerations for Allow password change after expiration.
To immediately expire multiple users' passwords and force them to change their password:
- Go to User Management > Users.
- Select the users whose password you want to expire.
- Click Actions, then select Force Password Change. If you haven’t enabled the Allow password change after expiration setting for your org, you’re notified on the Force Password Change modal. You can choose to enable the setting for your org by clicking force change, or choose not to by clicking cancel. If you enable the setting for your org, all users with expired passwords are able to reset their password.
Allowing a Password Change After Expiration
The following flows assume the Allow password change after expiration setting is enabled for an organization.
Require a New User to Change their Temporary Password
The following flow applies when admins select to require a new user to change their temporary password:
- An administrator creates a new user, gives the user a temporary password, and selects User must change password at next login.
- The user must change their password the next time they log in to their device:
- If JumpCloud detects the user is on a Mac or Windows device, they’re asked to update their password on their device login screen. If you've required MFA for the User Portal, users are required to verify their identity when they change their password.
- If JumpCloud detects the user is on a Linux device, they can log in to their User Portal using expired credentials and are shown a password change prompt. This prompt can’t be dismissed. If you've required MFA for the User Portal, users are required to verify their identity when they change their password.
An Existing User’s Password Expires
The following flow applies when a user’s password lifespan expires:
- The user’s password lifespan is reached and the password expires.
- The user is logged out of their device and all JumpCloud-managed resources.
- The user must change their password the next time they log in to their device:
- If JumpCloud detects the user is on a Mac or Windows device, they’re asked to update their password on their device login screen. If you've required MFA for the User Portal, users are required to verify their identity when they change their password.
- If JumpCloud detects the user is on a Linux device, they can log in to their User Portal using expired credentials and are shown a password change prompt. This prompt can’t be dismissed. If you've required MFA for the User Portal, users are required to verify their identity when they change their password.
Expire an Existing User’s Password
The password for a Samba user, which is the Samba Service Account, cannot be expired.
The following flow applies when an admin expires an existing user’s password, unless the user is the Samba user:
- An administrator selects to view an existing user’s details.
- The administrator clicks the user’s password status, then selects Force Password Change.
- The password is immediately expired and the user is logged out of their device and all JumpCloud-managed resources.
- The user must change their password the next time they log in to their device:
- If JumpCloud detects the user is on a Mac or Windows device, they’re asked to update their password on their device login screen. If you've required MFA for the User Portal, users are required to verify their identity when they change their password.
- If JumpCloud detects the user is on a Linux device, they can log in to their User Portal using expired credentials and are shown a password change prompt. This prompt can’t be dismissed. If you've required MFA for the User Portal, users are required to verify their identity when they change their password.
Implementing a Rolling Password Expiration Policy
This section describes legacy behavior for password expiration. See Manage Password and Security Settings
When enabling password expiration for a JumpCloud organization, the default behavior is to set the password expiration date to the same date and time for all users of a JumpCloud organization. To limit the number of accounts that are set to expire on a given date and time, admins can create a phased, rolling password expiration policy for their organization.
This can be done by enabling the Password Never Expires setting for all users in an organization before enabling password expiration for an organization and then disabling the setting for batches of users at a time.
Need to install the JumpCloud PowerShell module to automate this task? See Install the JumpCloud PowerShell Module.
For organizations that already have password expiration in place, the steps can also be implemented, but doing so will update all users' existing password expiration dates.
Only once the Password Never Expires setting is disabled per user will the global password expiration setting apply to the user's account.
Examples from the JumpCloud PowerShell Module example library are used to modify users and implement a rolling password expiration policy:
- Step 1: Enable the Password Never Expires setting for all users in the organization.
- Step 2: Enable a password expiration policy in the Admin Portal.
- Step 3: Disable the Password Never Expires setting for users in batches.
When the setting Password Never Expires setting is disabled for a user, the user’s account will be set to expire at the current time plus the number of days configured for expiration. As an administrator, you can choose the duration between batches of users you disable the expire setting for in your organization.
Forcing an Org-Wide Password Reset
Organizations may want, or sometimes have an immediate need, to have their entire user base reset passwords. There are many ways to facilitate this with the JumpCloud. There are advantages and disadvantages for each option, ways to initiate the reset flows, and variations in user experience that result.
See Force an Organization-Wide Password Reset to learn more.