This article outlines common issues and resolutions that occur when installing or configuring the JumpCloud Agent.
All OSes
Symptoms
The agent does not start, starts then stops, or changes made to a device do not synchronize after waiting more than two minutes. Changes can include, but not limited to:
- Account provisioning/takeover.
- Password changes.
- User details or privilege level.
- MFA Settings.
Cause
- Time is not synchronized.
- The agent is not up to date.
- The agent is not running.
- The device is inactive (red) in the console.
- The user is not active (green) in the console.
- The changes are not valid.
- Usernames are not case matched.
- MFA Tokens have not been validated.
- Other management software reverts changes to the device.
Resolution
- Verify the device time is synchronized to ntp.org or similar reliable time source.
- If the agent was installed from a saved file or device image, update the agent with the most recent version available. If necessary, delete the device record from the Admin Portal, uninstall the agent manually, and reinstall.
- Make sure the agent is running. If so, restart it. See Stop, Start, or Restart the Agent.
- Verify the agent is active (green) in the console. See Agent does not register or a device stops reporting.
- If the user status is not active (green), then hover over the status indicator to obtain the cause and take the necessary corrective action.
- Certain changes are not valid and will cause a notification alert. When this happens, it's possible the synchronization will partially work, or not work at all. See Understand Alerts.
- Usernames are case sensitive, even on Windows. A case mismatch between the JumpCloud directory and the local device account will result in a variety of sync issues. See Naming Conventions for Users to verify existing device usernames.
- Devices will not prompt for MFA until the user has confirmed their TOTP token, see Enable TOTP MFA for Devices.
- Some configuration software such as Puppet may be configured to manage files that JumpCloud manages. This will cause a conflict. See Agent Compatibility, System Requirements, and Impacts for a detailed list of files the JumpCloud agent manages.
There may be other conditions that cause the agent to fail to either start or synchronize changes. Verify the above resolution steps, then gather the following information and submit a Support Request.
- A description of specifically what fails to synchronize, including affected username(s)
- The device ID(s)
- OS Version/build number
- Agent version, found in
- MAC | LINUX: /opt/jc/version.txt
- WINDOWS: C:\Program Files\JumpCloud\plugins\contrib\version.txt
- The agent log, found in
- MAC | LINUX: /var/log/jcagent.log
- WINDOWS: C:\Windows\Temp\jcagent.log
- Your timezone, and the time when the change was made in the Admin Portal
Symptoms
- A newly installed agent does not show up as a new device record in the Admin Portal.
- A newly installed agent shows up in the Admin Portal, then goes inactive (red) within 10 minutes.
- A previously reporting device has gone inactive (red) in the console.
Common Causes
- Agent Installation Issues: Incomplete or failed installation of the JumpCloud agent can result in communication problems.
- Agent Configuration Problems:
- Any leftover files from a previous installation might interfere during reinstallation causing the device to not appear in the Admin Portal.
- Devices are deployed from an image that has not been configured correctly with a preinstalled agent.
- Full Disk Access has not been granted to the JumpCloud agent.
- Device Connectivity Problems:
- There is a network issue.
- The JumpCloud agent is not running, not running properly, or won't start.
Troubleshooting Steps
1. Ensure the JumpCloud Agent service is running:
- Check that the service is running. If it is not, start it and verify the service stays running. See Stop, Start, or Restart the Agent.
- If the agent does not start or stay running, follow the Agent does not start or synchronize changes.
2. Verify Agent requirements:
- Verify both the device and network comply with Agent and Port Requirements. If your security configuration is preventing the JumpCloud agent from running, Create an Allow List for JumpCloud Services.
- Verify that the device complies with JumpCloud Agent Compatibility and System Requirements.
- On macOS devices, verify that Full Disk Access has been granted for the JumpCloud agent. See Grant Full Disk Access to the Agent for macOS - JumpCloud
- If deploying from an image, DO NOT start the agent after deleting the the specified files. When the agent starts, it recreates the files and also creates a unique device record in your organization. Deploying from an image in this state will result in duplicate device records where only the most recent to check in will show active.
3. Contact Support
If the device record is still not created in the Admin Portal, collect the following information and submit a Support Request.
- OS Version/build number
- Agent version, found in
- MAC | LINUX: /opt/jc/version.txt
- WINDOWS: C:\Program Files\JumpCloud\Plugins\Contrib\version.txt
- The agent log, found in
- MAC | LINUX: /var/log/jcagent.log
- WINDOWS: C:\Windows\Temp\jcagent.log
When ICMP type 3 code 4 (Fragmentation Needed) packets are filtered on your network, you may experience failures of the JumpCloud agent to complete its registration. Enabling this on your network may correct the registration issue. See Path MTU Discovery for more details.
Symptoms
A device has been offline for more than 30 days during the certificate renewal period and it creates a new device entry after reconnecting.
Resolution
The JumpCloud Agent certificate used to authenticate and secure device communications has a one-year lifespan. The agent will renew this certificate during a window beginning 30 days prior to the expiration date.
When a device is offline for more than 30 days overlapping this renewal window, the certificate will no longer be valid when the when the device comes back online. This causes the device object to remain offline in the Admin Portal.
You can verify this by inspecting the expiration date of the agent certificate directly on the device with the following commands:
macOS & Linux
sudo openssl x509 -in /opt/jc/client.crt -noout -text | grep -i not
Windows PowerShell
$path = 'c:\Program Files\JumpCloud\Plugins\Contrib\client.crt' $cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2($path) $cert.NotAfter
Interpreting the Results
Command Line:
Inspect the results of the command and look at the certificate expiration date (the Not After date). The certificate renewal period would begin 30 days prior to. In this example, June 20, 2023 would be the earliest the certificate renewal date.
When the device comes online next, it will attempt to re-seal to JumpCloud, generating a new client certificate, SystemID, and Device entry in the Admin Portal. The former device object will be abandoned and remain in an offline state.
JumpCloud Agent Log:
The JumpCloud Agent also details this process within the agent log. The following example details these events:
time=2023-04-03 15:05:10.42-06:00 PID=93988 level=info msg=REGISTRATION: Certificates have expired, resealing as a new system in JumpCloud
time=2023-04-03 15:05:10.42-06:00 PID=93988 level=info msg=REGISTRATION: No existing valid certificate found, initializing it
time=2023-04-03 15:05:10.42-06:00 PID=93988 level=info msg=REGISTRATION: Creating client certificates
Search for resealing when exploring agent logs. This generally confirms it was a certificate renewal miss that caused the new device object in JumpCloud.
For devices offline more than 30 days that don't create a new device entry upon reconnection, you might need to reinstall the agent. If this fails, you may need to fully uninstall and reinstall the agent.
Although JumpCloud doesn’t recommend or officially support dual boot/multi-boot devices, we understand this might be a necessity for your org.
Configuring your devices in this way can cause discrepancies within the Admin Portal, potentially leading to various errors. JumpCloud does not guarantee full functionality with dual boot/multi-boot devices.
Overview of agent configuration on a dual boot device:
- You completely understand the risks this involves as mentioned in the legend above.
- JumpCloud Agent Compatibility, System Requirements, and Impacts are still the same for this configuration, please choose a compatible OS to avoid further issues.
- Install the JumpCloud Agent on both operating systems using the respective installer for the OS you are using.
- Once installed, there will be two registries in the Admin Portal for the same device but with different operating systems. This is unavoidable, as the underlying hardware information is the same for both, given they are on the same device.
Devices managed by JumpCloud that remain offline for an extended period can face challenges such as expired certificates, outdated policies, and delayed commands.
The device’s service enrollment certificate has a lifespan of one year, and the agent will attempt to renew it beginning 30 days prior to the anniversary date.
Before bringing an offline device back online, check the device health, back up important data, and ensure network access.
Follow these steps to bring an offline device back online and ensure it updates properly:
- Connect to the Internet: Ensure the device is connected to a stable network (WiFi or Ethernet).
- The agent should automatically start when the device boots up and perform its initial checks.
- Verify Agent Status. See Stop, Start, or Restart the JumpCloud Agent for more details.
- Check the certificate status:
- macOS & Linux:
sudo openssl x509 -in /opt/jc/client.crt -noout -text | grep -i not - Windows:
$path = 'c:\Program Files\JumpCloud\Plugins\Contrib\client.crt'
$cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2($path)
$cert.NotAfter
- macOS & Linux:
- Update Device Policies
- Once the device is online, policies and configurations should automatically apply. You can verify this by checking the device status in the JumpCloud Admin Portal. If the policies do not update on the device, you can try reapplying them by unbinding and then rebinding the device to the desired policies.
On macOS, if the agent has run into an error condition preventing it from starting correctly (e.g. no longer has full disk access), then LaunchD may disable the service to prevent it from cycling. In these cases, reinstalling the agent over the top of the existing configuration will reset the service and should allow the agent to start.
Linux
Symptoms
Attempting to install the JumpCloud agent fails on a Linux system and logs an error noting that Your OS/architecture [ ] is not supported.
Cause
On Linux, JumpCloud uses both the architecture of your kernel (uname -m) as well as the contents of your /etc/issue or /etc/os-release file to determine the OS type of your servers. If the contents do not match JumpCloud current set of supported operating system types, you will receive this error.
See Agent Compatibility, System Requirements, and Impacts for supported Linux versions.
Resolution
Returning the /etc/issue or /etc/os-release file to its original contents can often correct this issue.
(Unsupported) Workaround
Install the agent on the unsupported distribution at your own risk.
Installing the JumpCloud agent on an unsupported version does not guarantee functionality.
You will need to edit the etc/issue, etc/os release, and/or etc/system-release files to match those of a JumpCloud-supported distribution before installing the agent.
Symptoms
After installing the JumpCloud Agent using the curl command to a Linux Amazon EC2 hosted system, the agent will fail to start and will report the following within /var/log/jcagent.log:
2016/02/02 19:11:04 [9762] Initial certificate checks failed, err='Could not seal the agent to JumpCloud, err='Could not initialize client certificate, err='Could not sign the certificate, err='CSR request failed with status=408, body='<html><body><h1>408 Request Time-out</h1>
Your browser didn't send a complete request in time.
Resolution
The problem involves improper packet splitting. When Amazon identifies an internal instance, it sets the MTU to 9001 (jumbo frames). However, outbound traffic is still set to an MTU of 1500. The default version of curl was not properly reading the correct MTU, and was thus attempting to send a 9001 size frame, but only the first 1500 chars were actually copied.
On the Linux instance run:
ifconfig <interface> mtu 1500 up
You may also make a permanent change in /etc/sysconfig/network-scripts/ifcfg-<interface> by adding MTU=1500
macOS
Symptoms
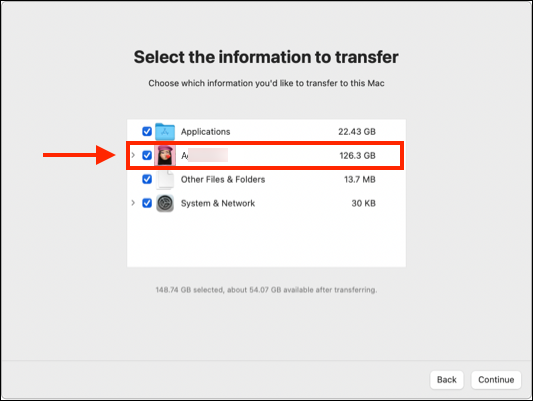
- After migrating user data from an old Mac to a new Mac using Migration Assistant, the JumpCloud Agent no longer starts or synchronizes.
- The new device becomes active under the old device records.
- The new device may show as inactive (red) or behave erratically when performing actions in the Admin Portal.
- Policies or commands fail to apply to the migrated device.
Cause
Using Migration Assistant to transfer Applications, Other Files & Folders, or System & Network Settings from a JumpCloud-managed device causes a failed state for the new device in JumpCloud. This is caused by Migration Assistant transferring device agent and MDM settings from the old device to the new device.
Resolution
You may need to delete the device record from the Admin Portal, uninstall the agent manually, and reinstall or re-enroll the device in MDM.
Use of Migration Assistant is not supported for JumpCloud-managed or MDM enrolled JumpCloud devices. We recommend using a cloud backup solution or manually copying user data to the new device.
If your environment requires using Migration Assistant, proceed at your own risk. Select only the user home directory during the Migration Assistant wizard (as highlighted in the following image). Do not migrate Applications, Other Files & Folders, or System & Network Settings and ensure these are deselected during the Migration Assistant process.