Blast-RADIUS is a vulnerability inherent in the RADIUS authentication protocols PAP and MS-CHAP that can compromise the security of your network. This vulnerability exploits unencrypted, non-TLS-based protocols such as PAP and MS-CHAPv2 which are vulnerable to brute force and man-in-the-middle (MiTM) cyberattacks.
Unless you are configuring RADIUS MFA for VPN, JumpCloud discourages using using non-TLS-based RADIUS protocols and instead recommends using TLS-based authentication protocols (PEAPv0/MS-CHAPv2, EAP-TTLS/PAP, and EAP-TLS).
Identifying Insecure Protocols
- Log in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Insights > Directory Insights.
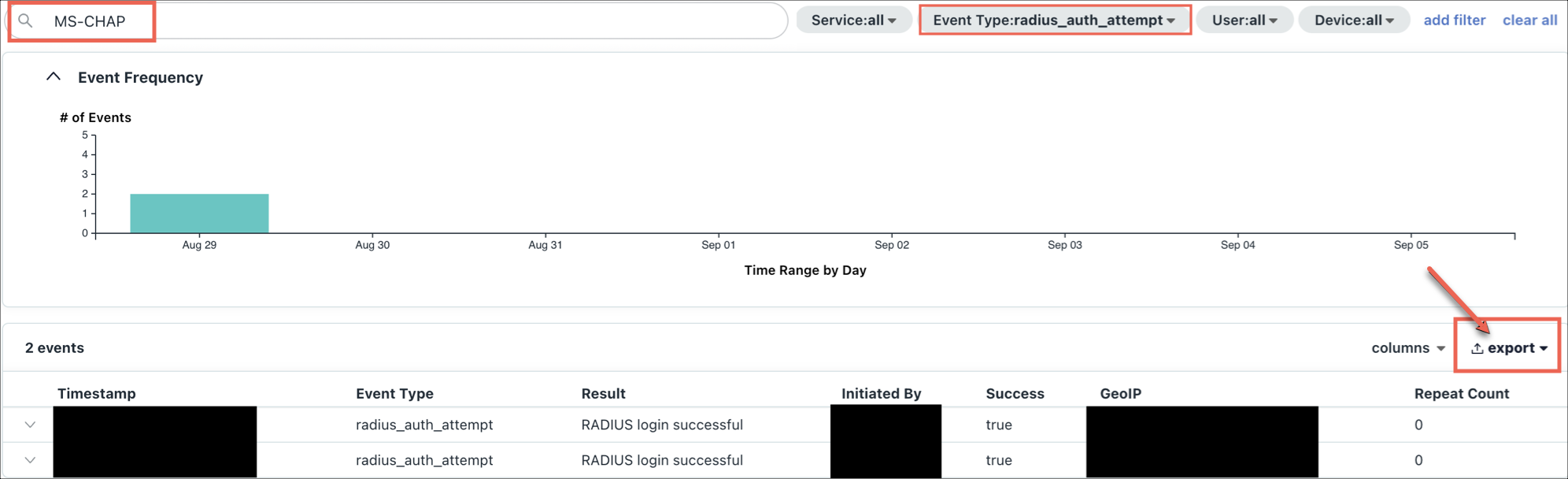
- In the Event Type filter, select radius_auth_attempt.
- Search for
PAPvulnerabilities: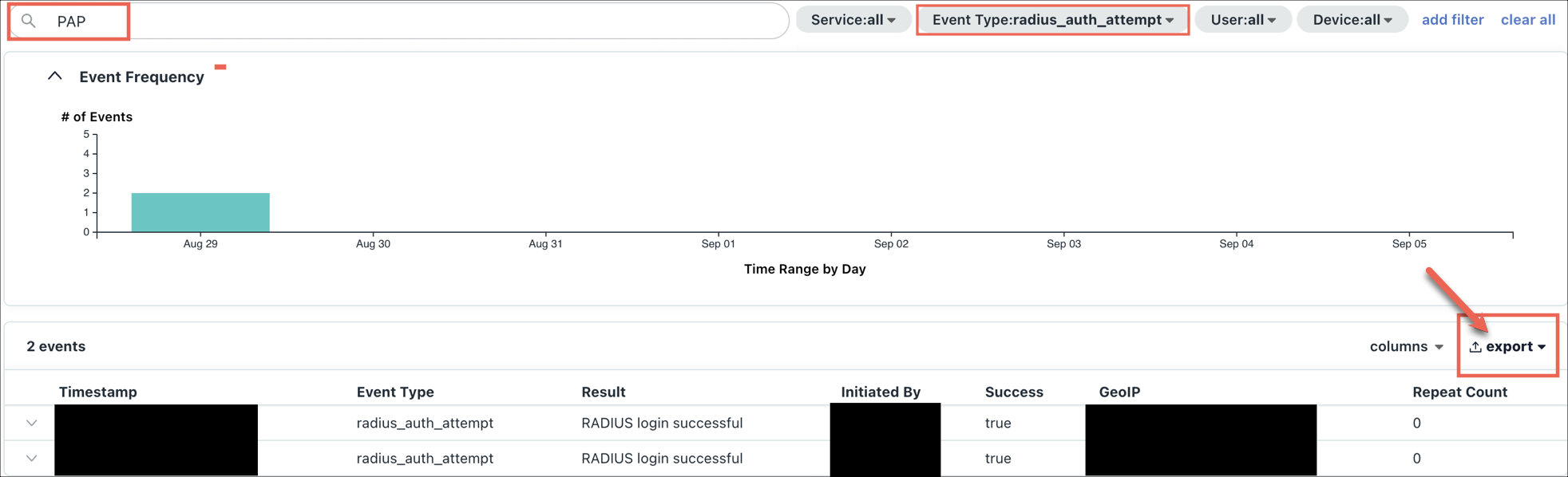
- In the Search bar, enter “
PAP” and run a report. - Click export and then export the report as a JSON file.
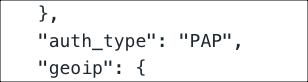
- Inspect the JSON file and search for
“auth_type”: ”PAP”.
- In the Search bar, enter “
- Search for
MS-CHAPvulnerabilities:- In the Search bar, enter “
MS-CHAP” and run a report. - Click export and then export the report as a JSON file.
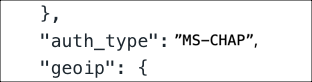
- Inspect the JSON file and search for
“auth_type”: ”MS-CHAP”.
- In the Search bar, enter “
When looking through the JSON file to find insecure protocol types, make sure you look for the auth_type, and ignore the eap_type.
- If you identify insecure protocols in your device fleet, please switch to the secure TLS-based RADIUS authentication protocols (
PEAPv0/MS-CHAPv2,EAP-TTLS/PAP, andEAP-TLS).
Any resulting non-TLS PAP or MS-CHAP authentication types are indicative of insecure protocols and should be switched to TLS-based RADIUS authentication protocols as soon as possible.
Managing Insecure Protocols
Block Insecure Protocols
You can use the JumpCloud Admin Portal to restrict insecure RADIUS authentication protocols from being used on any future network configurations.
To block insecure RADIUS protocols:
- Log in to the JumpCloud Admin Portal.
- Go to Access > RADIUS.
- Select the RADIUS network configuration you want to change. The RADIUS details tab displays.
- Click the Authentication tab.
- Select Require secure protocols to restrict the use of non-TLS-based network authentication protocols.
- Click Save.
Mitigate Risk Using Insecure Protocols
If your integration or equipment only supports insecure, non-TLS-based legacy protocols, use Directory Insights to try and mitigate your risk by monitoring RADIUS access and enforcing the following security measures for all users:
- Require multi-factor authentication (MFA) enrollment for accessing the User Portal.
- Ensure users are enrolled in MFA.
- Enable a password policy with a regular rotation interval.
JumpCloud does not recommend using MFA with RADIUS, especially for WiFi configurations. The recommendation for MFA enrollment is intended for use of non-RADIUS resources such as securing the User Portal.
For more information, see