Next-generation antivirus products aren't just relying on signature and heuristic-based detection anymore; they are using some focused artificial intelligence to identify unusual behaviors.
Because the JumpCloud Agent executes background tasks that could be flagged as unusual, this could be flagged by your antivirus vendor; however, this is how the Agent works by design, and is not malicious. Antivirus software may flag the JumpCloud Agent at any time, even if it hasn’t happened previously.
It's recommended to add the JumpCloud installation folder as well as the JumpCloud Agent application for Mac, Windows, and Linux systems to an allow list. If the JumpCloud Agent or scripts run by the Agent are flagged as suspicious after you have added the JumpCloud Agent to your allow list, we recommend contacting your antivirus vendor.
If you are using JumpCloud Remote Assist, see Understanding the Remote Assist Agent for endpoint security exclusions.
Finding the Allowlist Folder and Application
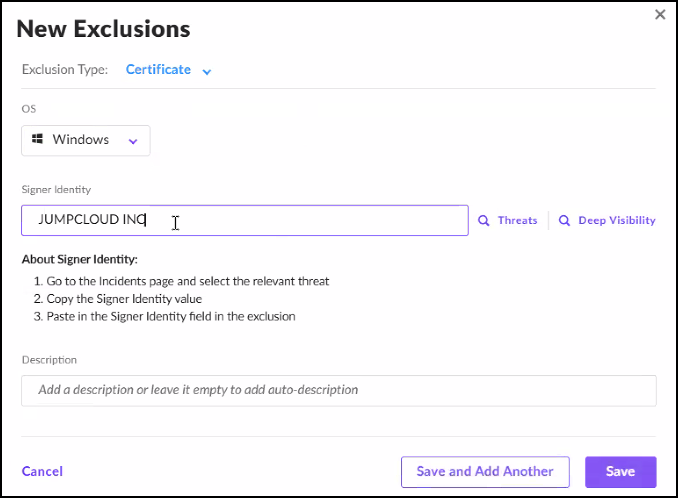
Windows
Add the following folders and their subfolders:
- C:\Program Files\JumpCloud
- C:\Program Files\JumpCloudTray
- C:\Windows\Temp
- C:\ProgramData\JumpCloud
Additionally, add an exclusion for JumpCloud's certificate signing identity, JumpCloud Inc.
Mac
- /opt/jc
- /opt/jc_user_ro
- /Library/LaunchDaemons
- com.jumpcloud.darwin-agent.plist in the above directory
- /Library/LaunchAgents
- com.jumpcloud.user-agent.plist in the above directory
Linux
- /opt/jc
- /opt/jc_user_ro
- /etc/pam.d/jcprotect
- /etc/pam.d/jcprotect-prompt
- (64-bit only) /lib/x86_64-linux-gnu/security/pam_jc_push_mfa.so
- (64-bit only) /lib/x86_64-linux-gnu/security/pam_jc_session_check.so
- (64-bit only) /lib/x86_64-linux-gnu/security/jc_localgrpc.so
- (32-bit only) /lib/i386-linux-gnu/security/pam_jc_push_mfa.so
- (32-bit only) /lib/i386-linux-gnu/security/pam_jc_session_check.so
- (32-bit only) /lib/i386-linux-gnu/security/jc_localgrpc.so
Understanding JumpCloud’s Allowlisted Login Items
With macOS 13 Ventura, end users have the ability to switch off persistent software, such as the JumpCloud Agent. Ventura also introduces the concept of allow listed Login Items, which is a list of third-party apps that users are allowed to log in to with Mobile Device Management (MDM).
JumpCloud uses an allow list so that these Login Items can use JumpCloud’s MDM:
- Apple’s code-signing identity for apps signed by our team ID. For example, N985MXSH86.
- JumpCloud Launch Daemons and Launch Agents that are labeled as com.jumpcloud. You can see what is running on your device by reviewing the /Library/LaunchDaemons directory and the /Library/LaunchAgents directory. For example:
com.jumpcloud.agent-updater.plist
com.jumpcloud.darwin-agent.plist
com.jumpcloud.macos-update-notifications.plist
com.jumpcloud.Nudge.plist
com.jumpcloud.jcagent-tray.plist
com.jumpcloud.user-agent.plist
If you are not using JumpCloud’s MDM, but you are using another MDM vendor, you can use JumpCloud’s Mac Managed Login Items Policy to add Login Items to an allow list for your macOS devices. For more detail and instructions, see Create a Mac Managed Login Items Policy.