Identity and access management has quietly become a crisis for IT. The proliferation of disparate resources (SaaS, IaaS, Mac®, Linux®, etc.) has decentralized core identity management operations. While the cloud has been part of the problem, we believe that it also contains the solution.
From the crisis of decentralized IAM, the vision of JumpCloud® arose. We usually explain JumpCloud in terms of its features, be it cloud LDAP, or cloud RADIUS, or our System Agent, but here, we want to look at it from a different angle. Below we’ll explain how modern identity management was disrupted and our vision for unifying IAM again with cloud directory services.
Origins of IAM
You may (or may not) recall the brick-and-mortar environment your network and all the connectivity your company’s resources operated from back in 2000.
Remember walking into that facility, sitting down in front of your desktop, and running Windows® XP® or Windows 2000? (And by desktop, I mean an immobile, truly-tethered-to-your-desk desktop, of course). Most of the machines were physically tethered together through Ethernet wiring and switches/hubs and managed through a server somewhere around the corner in the same building in a closet or data center. This was called the LAN – the local area network. With the addition of remote sites and the Internet, the term WAN – wide area network – was introduced.
The LAN of yesteryear was brought to you almost exclusively by Microsoft Windows and its associated components. Through the magic of Kerberos for authentication, Active Directory® (AD) domain services, and Windows Server, Microsoft® was working behind the scenes and quietly running the network.
All the machines tethered to this Active Directory domain worked together. Your one set of credentials granted you access to basically everything:
- The System (Windows Desktop)
- Servers (Windows Server)
- The Network (Windows domain controller)
- Files (Windows Server and Sharepoint®)
- Your Email (Microsoft Exchange®)
- Productivity Software (Microsoft Office®)
- And more.
But this couldn’t last forever.
Directory Services, Disrupted
Microsoft was beginning to establish a vision for managing a more mobile, operative workforce, but they still kept one foot firmly rooted in the on-prem world of the past. Laptops loaded with Virtual Private Network (VPN) software enabled you to be authenticated to Active Directory, and connect to the corporate network outside of the office, but the technological climate began changing faster than Microsoft could keep up with. Their pristine model of a domain-bound network was being stretched thin by new devices and progressive applications. The sunlight of the infrastructure Active Directory had been providing was beginning to cast a shadow around something called the cloud. But, where was the cloud coming from?
Software-as-a-Service (SaaS) Takes Hold
Companies like Salesforce® were among the first to take advantage of the benefits of cloud computing. Founded in 1999, Salesforce introduced a cloud-based Customer Relationship Marketing (CRM) system that flew in the face of traditional business software – and traditional IT management.
For IT admins, this came as a bit of a shock. Suddenly, their complete control over user data and IT systems – their “domain” – was being disrupted by independent solutions outside of their control (and walls). New user accounts and credentials were flowing in from rogue sales and/or marketing teams who were subscribing to services with credit cards. In the process, users were completely bypassing normal IT purchasing models and methods.
This problem got a name (“Shadow IT”) and a host of new solutions sprung up to try to solve it. We started to see the first tethers of Active Directory branching up towards the cloud through web application single sign-on solutions, using protocols like SAML. These SSO solutions allowed IT administrators to return to management as usual (albeit managing multiple IT management systems), but only for the time being. The dam of Active Directory had sprung a leak.
The central question only became more pressing: “How can IT securely manage and authenticate all of these various identity streams?”
By the late 2000s, the pattern of tethering cloud-based utilities to Active Directory had spread to solutions like G Suite™ (formerly known as Google Apps), which had in many cases replaced Exchange as an email mechanism and productivity platform. But this required still more utilities, like Google Apps Directory Sync® (GADS), now called Google Cloud Directory Sync (GCDS), in order to do so. The spectre of Shadow IT continued to spread as new cloud-based mechanisms and devices emerged with one-off utilities to tether them back down to Active Directory.
Macs, Linux, and the Heterogeneous System Environment
Then, Apple pulled a Steve Jobs and changed their whole image with the iPhone® and iMac®, reinventing the consumer wheel in the process. Suddenly, admins saw people walking into the office with these sleek devices, totally unmanaged, but nevertheless accessing corporate networks and data. One recent survey on the matter found that 75% of users today prefer Mac over Windows. Simultaneously, Linux increased in popularity, especially among developers and engineers as Linux now runs 90% of the public cloud workload.
So, the massive ecosystem of vendors expanded rapidly, yet again, and system admins were reaching a breaking point. Bring your own device (BYOD) programs emerged as the influx of employees’ personal devices became too much of a security risk too ignore. But these BYOD programs required IT organizations to manage all types of disparate systems, and made environments difficult to secure. Some system admins opted instead for policies requiring their users to stick with Windows and Microsoft exclusively. Others migrated to Mac, while many embraced Linux.
IAM in Disarray
What they all had in common is a need to securely tether all pathways to a centralized identity store. But they didn’t have that. Instead, they had a convoluted knot of siloed identity management systems.
As a key aspect of these IAM silos, protocols were flying in from all sides to support specific devices and specific applications and specific networks, causing IT admins to lose sleep and probably lose hair as well. Updating and adapting IAM solutions to this multi-protocol environment was a nightmare:
- LDAP, Linux, technical applications, and more
- Kerberos mostly for Windows
- RADIUS for VPNs
- SAML for some web applications
- OAuth for other cloud applications
- SSH and MFA, while technically not protocols, for server access and increased security
- At least 30+ more
Ramifications for Active Directory
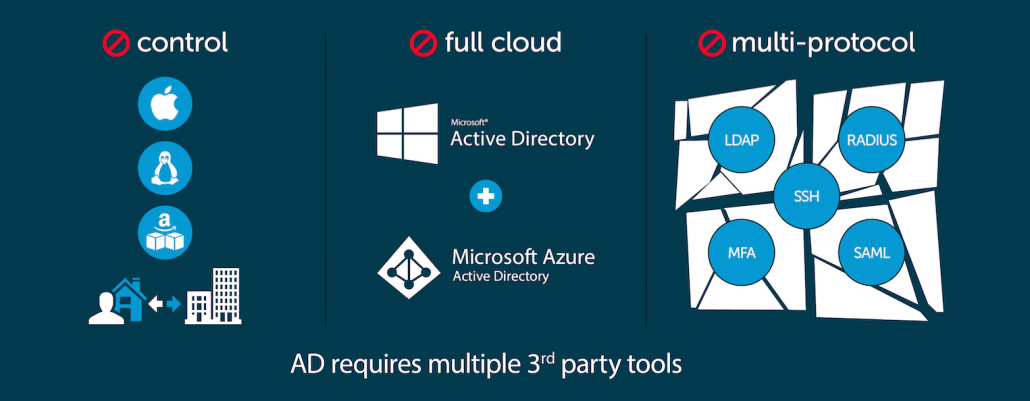
The result of all this diversification? Security gaps. Inefficiencies. Broken onboarding/offboarding processes for scaling enterprises. Wasted time and resources. IT admins at their wits’ ends.
With Active Directory at the center, IT organizations were weighed down by all they had to manage, and were struggling to stay above water. As the disarray mounted, the IT landscape reached a breaking point. Whether patchy security or disparate resources or simply the mounting stress on IT admins, organizations at large were on the verge of being pulled apart.
From this chaos, the vision of JumpCloud was formed.
Cloud Directory Services and The Return of The Unified Identity
JumpCloud emerged out of a need that was being felt industry-wide. This was simply the need to help people access resources for work, and enable them to be productive.
While SSO solutions, identity bridges, and privileged identity management encourage layering point solution add-ons on top of flawed, legacy directory services, JumpCloud felt the mounting disarray and started there—at the core of the problem.
Reimagining the centralized identity management of the past, JumpCloud saw an opportunity to pull it all back together. But this time, unification would begin with the cloud.
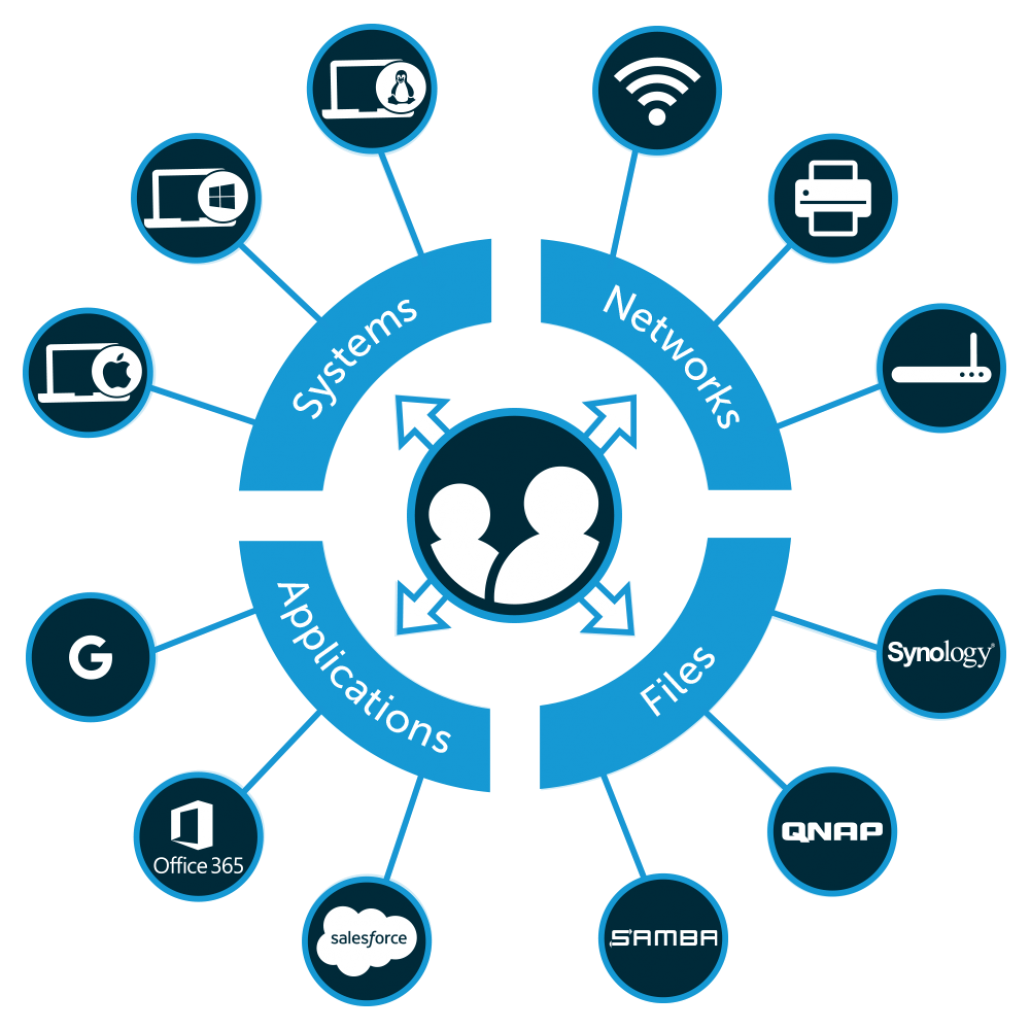
We wanted to build the world’s first, and best, 100% cloud-based directory—one capable of securely managing desktops, laptops, applications, files, WiFi networks, and more regardless of platform, protocol, provider, and location.
Today, we are well on our way to achieving that vision, no matter the vested industry interests in opposition to our efforts. we can say that we’ve achieved that vision. We call it Directory-as-a-Service® (DaaS). These are the principles that have guided us:
Cloud-Forward
The JumpCloud platform doesn’t require any on-prem hardware. We are built on the cloud, for the cloud and on-prem and remote IT resources—so, from the cloud, but for wherever your IT resources are. So, DaaS works seamlessly with SaaS apps, cloud server environments, and remote user management. But while we know that the future is in the cloud, we haven’t forgotten the past: JumpCloud can manage your legacy, on-prem apps and hardware too.
Platform Independent
We believe that users should have a choice in everything they use—and that admins should have control over those systems regardless of platform. By providing a vendor-agnostic identity management tool that caters to a wide variety of heterogeneous environments, everyone wins (except for the guys that want to lock you into strictly their platforms).
Multi-Protocol
This emphasis on independence extends to networks, protocols, and apps as well. Simply put, we don’t care what you want to connect to us. We use a wide variety of protocols and directly support SAML integration with hundreds of applications.
Centralized
We believe IT admins should be able to enforce security settings and take actions on groups of users and systems, in a centralized, automated fashion. Setting policies, executing commands, running scripts, and controlling systems across whole fleets of machines should be encouraged—not restricted.
System is the Gateway
The system is at the center of the user’s work life. With JumpCloud, the system is the gateway of authentication to access resources securely. When a user logs into a workstation, only that single identity can be used across everything from apps to infrastructure. Reset passwords straight from the OS through the JumpCloud Mac App. JumpCloud is where identity security meets user convenience.
Hyper-Secure
“Paranoia is not retroactive” is a common saying at JumpCloud. Once a security breach occurs, there’s no way to reverse the damage. That’s why we’re dead serious about security. By employing a private PKI infrastructure, unique key generation per agent, multi-factor authentication, and independent audits from a qualified third-party assessor three times a year, you can trust our security practices are proactive, fortified, and meticulously monitored.
We don’t do it all, and we don’t propose to. But what we do propose is through highly scalable protocols, a feature-rich platform, and the hard work of our engineering team, we’ve delivered the first true, cloud-based directory.
And that’s only just the beginning.
A Single Pane of Glass for IAM
With the rapid adoption of cloud apps, infrastructure, heterogeneous resources, and with IT services expected to grow by 4.7% in 2018 (~$44 billion dollars), it’s the dawn of a new age.
We’re at the forefront of this revolution, unifying and simplifying directory services, and we hope you see that vision with us. With JumpCloud, you’re returning to the simplicity of a secure, centralized, singular source of truth. Pick and choose what you want, leverage the protocols you need, and do it all from a single browser-based console.
In a way, we’re realizing the initial idea of unified IT management put forward by AD in the early 2000s, and taking it much further. Unlike AD, our Directory-as-a-Service is in the cloud, platform independent, hyper-secure, with no on-prem servers to configure or maintain.
Our long-term vision isn’t just to be the world’s best, most secure cloud directory. We want to be the world’s best directory—bar none.
Do You Share Our Vision for the Modern Directory?
As IT admins continue to contact us with questions on how JumpCloud can be the right fit for their environment, we understand firsthand the needs of organizations are never exactly the same. If you haven’t reached out already, we encourage you to do so to see how JumpCloud can streamline your identity management process.
A few other options are also available for getting to know the Directory-as-a-Service platform:
- Personalized Demo – Receive a demo walkthrough tailored to your needs from one of our product experts
- Free Account – Explore the features for yourself and get unlimited access for your first 10 users
- Knowledge Base – Scan through the possibilities with our database of instructional material
We hope you now have a sense for what we’re really excited about at JumpCloud as we continue to build together on the promise of comprehensive, foundational IT infrastructure for the modern era.
Discover More About JumpCloud In These Case Studies
Explore the case studies above to see how JumpCloud is improving organizations around the world. As mentioned previously, if you’d like to see the identity management platform in action for yourself, you can sign up for a free account below, or send us an email for further details.
