JumpCloud leverages a service account to ensure that JumpCloud-managed users on macOS devices can unlock FileVault encryption. Before JumpCloud can provide FileVault access to JumpCloud-managed users, the JumpCloud Service Account must be created to provide its crucial function of granting new users secure tokens. This service account is created during the JumpCloud's agent installation process, or may be automatically installed at user login.
Understanding Secure Tokens
Apple File Systems (APFS) in macOS 10.13 changed the way Apple manages FileVault encryption keys. To secure and provide access to encryption keys, which are required for FileVault decryption, Apple introduced secure tokens.
Secure tokens are granted to the macOS users who create a local account using Apple's Setup Assistant for the first administrative user, and then subsequently through Apple's Users & Groups pane in System Settings. Apple's Deployment Reference for Mac describes additional methods in which a system account may be granted a secure token. Users with a secure token may enable and manage FileVault on a macOS system, and users created by these users are also given secure tokens via a chain of trust methodology.
Using the JumpCloud Service Account
The JumpCloud Service Account is installed as a system account whose sole purpose is the management of secure tokens for JumpCloud-managed accounts. As a service account, its context is to provide security-level services to other user accounts managed by JumpCloud, and it can't be logged in to by other users — the JumpCloud Service Account doesn't have an accessible password or valid home directory.
The JumpCloud Service Account is configured through the JumpCloud Service Account Utility. The JumpCloud Service Account Utility will launch automatically after MDM-driven enrollments, and can also be launched manually from the /Applications folder on the user’s device. The app will only successfully open if it doesn’t detect a service account on the device. If the user tries to launch it while a service account is present, the JumpCloud Service Account Utility will not launch.
This service account is also used to rotate the FileVault Recovery Key when using FileVault 2. See Create a Mac FileVault 2 Policy. Additionally, JumpCloud provides Recovery Key escrow through MDM.
Expected Behavior
- The service account appears in the list of users on the FileVault login screen on boot.
- The service account doesn't appear on the main login window or show in the list of users in User Management > Users.
- New users will need to log in to be added to FileVault and allowed to decrypt the system.
- Existing users that JumpCloud has taken over who don't have secure token enabled need to log out and log back in to be added to FileVault and allowed to decrypt the system.
- Password reset behavior for JumpCloud-managed users is the same as other versions of macOS with FileVault enabled.
- When the JumpCloud agent is uninstalled, the JumpCloud Service Account is removed.
Installing the JumpCloud Service Account
The Service Account can be installed automatically by JumpCloud or manually by administrators.
Installing Automatically
JumpCloud automatically installs a service account when an administrator-level user logs in to the Mac device. During login, the JumpCloud Agent silently verifies that a service account exists. If one does, no action is taken. If not, the JumpCloud Agent uses the credentials of the logged-in user to instantiate it. These credentials are not stored anywhere on the device in plain text. They are securely captured during the login process and passed directly to the agent.
For JumpCloud to be able to automatically install the service account at login, the following is required:
- The device must be macOS 10.15 and later.
- The user that logs in must be a JumpCloud-managed administrative user on the Mac system.
Installing Manually Using the Service Account Utility
If the service account can't be installed automatically, the Service Account Utility will launch and prompt for admin account credentials to complete the creation of the JumpCloud Service Account. See Resolving a Service Account Prompt below.
- If the user is a secure token-enabled user: When installing the agent using the package installer, if the current user is a secure token-enabled user, the installation window prompts the current user to enter their password to install the JumpCloud Service Account. If the user clicks Exit, the service account isn't installed, the agent isn't installed, and the system won't be bound to JumpCloud.
- If the user isn't a secure token-enabled user: When installing the agent using the package installer, if the current user isn't a secure token-enabled user, the installation window asks the user to enter a secure token-enabled username and password. If the user clicks Exit, the service account isn't installed. Because the agent isn't installed, JumpCloud can't manage FileVault on that system.
- If the password is entered incorrectly: When installing the agent using the package installer, if the secure token administrator's username is entered, but the password is entered incorrectly, the user is required to enter the correct password to bind the system to JumpCloud. If the user clicks Exit, the system isn't bound to JumpCloud in any way, and the installer shows a failure message.
For JumpCloud to manage users on systems, the following must be true:
- MacOS 10.15 and later
- Users are FileVault-enabled
When installing the agent using the package installer, it's necessary to provide credentials for a natively created administrator account with secure token enabled. A secure token is granted to the first user to log in to a system created by the Setup Assistant. To check the secure token status of this user, run the following command in Terminal:
# sysadminctl interactive -secureTokenStatus SECURETOKEN_ADMIN_USERNAME
# SecureToken is ENABLED for user SECURETOKEN USER
This command can be run using the JumpCloud agent and it's available for import using the JumpCloud PowerShell Module.
The following applies only to devices running versions below macOS 14 Sonoma. Starting with macOS 14 Sonoma, removing the /private/var/db/.AppleSetupDone file no longer triggers Setup Assistant when a local user already exists on the device.
In rare cases, you might encounter a macOS system with no secure token-enabled user. In these instances, you can try removing the /var/db/.AppleSetupDone file on the system, then rebooting. This action causes the Apple Setup Assistant to run again on the next system startup, giving you the opportunity to create a new secure token-enabled local administrator account.
Resolving a Service Account Prompt
Beginning with JumpCloud Agent version 1.9.1, any time the agent is updated and there is no JumpCloud Service Account detected, the JumpCloud Service Account Utility will prompt the user for credentials to complete device enrollment.
The JumpCloud Service Account Utility provides an easy way to create the service account on a Mac. It prompts for an admin with a secure token and a password to create the service account. Once entered, it creates the service account. The credentials are not persisted anywhere.
The JumpCloud Service Account is required in order to grant secure tokens to new users. The Service Account is created by using the JumpCloud Service Account Utility, shown below.
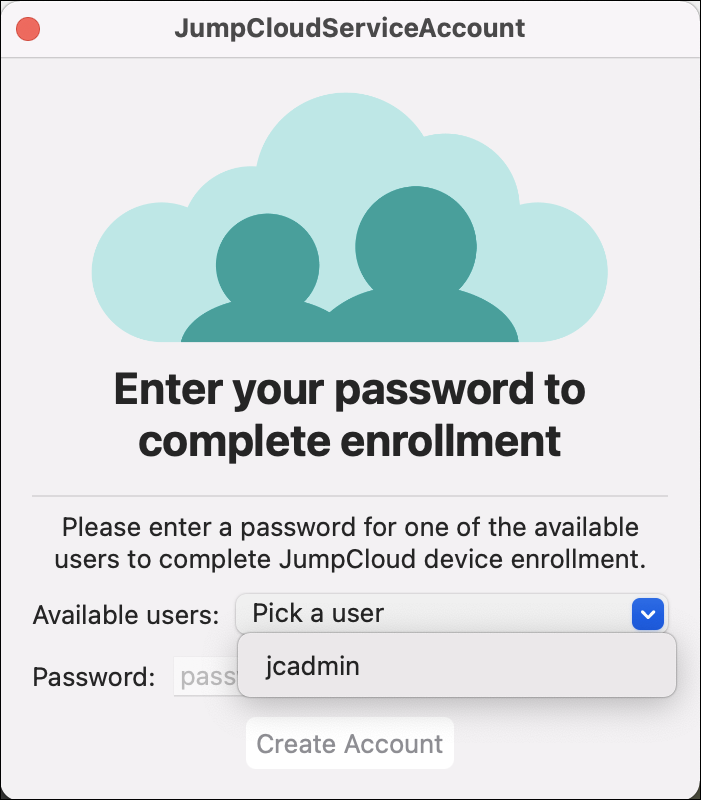
The JumpCloud Service Account Utility will launch automatically after MDM-driven enrollments, and can also be launched manually from the /Applications folder on the user’s device. The app will only successfully open if it doesn’t detect a service account on the device. If the user tries to launch it while a service account is present, the JumpCloud Service Account Utility will not launch.
To resolve the prompt, select a user and enter the local account password so that the service account can be created. Upon completion, the app will close.
Considerations:
- If the app rejects the local account password, this is likely because the admin does not have a valid secure token. If that is the case, first verify the secure token status of the admin:
sysadminctl -secureTokenStatus insert_username_here. - If the secure token is enabled: If the secure token is enabled, but you're unable to use the credentials to complete enrollment, then it’s likely the secure token is invalid. Follow the steps under "Recovering Devices That Have a User Without a Secure Token" in Troubleshooting: Service Account.
- If the secure token is disabled: The account is missing a secure token. If this is the only user account on the Mac, then the Mac is not in a state where it can provision secure tokens, and it must be wiped and macOS must be reinstalled. However, if there’s another user account on the Mac with a valid secure token, use those credentials to finish enrollment, or log in to that account and leverage the following command in Terminal to provision a secure token to the user account without a secure token:
sysadminctl -adminUser admin_user_here -adminPassword 'admin_pass' -secureTokenOn user_here -password 'user_pass'.