Organizations turn on multi-factor authentication (MFA) to secure access to corporate resources and increase their security posture.
IT admins like using push notifications MFA for several reasons. Since most users have smartphones in their pockets at all times, push notifications offer minimal user friction. They are also ubiquitous (admins can enable them across different kinds of resources and endpoints unlike other methods) and offer security against “man in the middle” attacks.
Recently, this trusted security measure has been facing a new kind of attack known as push bombing or MFA fatigue. Keep reading to learn more about how to reduce your risk.
What Is Push Bombing and MFA Fatigue?
When an organization uses push MFA, the user is required to approve the login or access request sent to their personal device in the form of a push notification. This is just one way (of many) to verify the user’s identity, but preferred given its UX benefits.
Push bombing is a method where an attacker uses a script or a bot to trigger multiple login attempts with stolen or leaked credentials and trigger a SPAM of multiple push notifications to the user’s mobile device.
Here’s how it works:
- An attacker repeatedly sends a user endless push notification streams with the intent to exacerbate them into accidentally approving the prompt.
- Understandably, the user feels a sense of fatigue, and it’s easy to make mistakes out of frustration. They accept the prompt.
- Unfortunately, the trick works extremely well for account take over and breaches. The attacker now has access to the account in question.
Alternatively, an attacker may also contact the user impersonating as an IT admin and convince them to approve the login attempt.
How JumpCloud Protect Helps Admins Combat Attacks
Stronger Password Policy
Push attempts are triggered after an attacker gains access to a user’s password. The weaker the password the more likely an attacker is to obtain it through brute force and social engineering techniques.
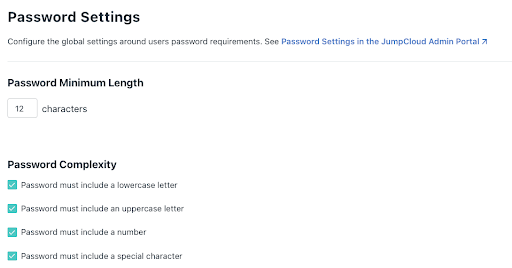
IT admins can use JumpCloud’s password settings to adopt a stronger password policy that meets the following requirements:
- Greater than or equal to12 characters in length, including alphanumeric
- Upper and lower case combinations
- Changes password every 90 days
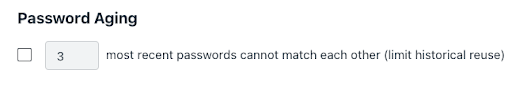
Admins should also use password aging to reduce risks due to re-use of older, leaked, or stolen credentials that a hacker may have obtained. Here’s what the Password Settings look like in the JumpCloud management portal:
Admins can also use JumpCloud’s password manager to manage their user’s passwords, which reduces the friction associated with using lengthier passwords with increased security posture. JumpCloud Password Manager eliminates the need to remember a master password thereby reducing the risks due to password leaks or breaches.
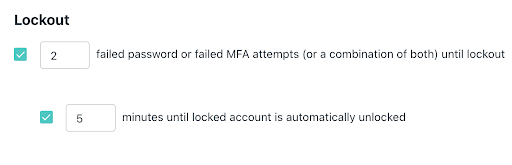
Account Lock-Out
Admins can use JumpCloud’s account lock-out settings to set a limit for password and Push MFA retries. A user’s account will be locked if the user denies a login request sent in Push notification for a specified number of consecutive attempts as determined by the settings. Admins can auto unlock the account after a certain duration to reduce user friction.
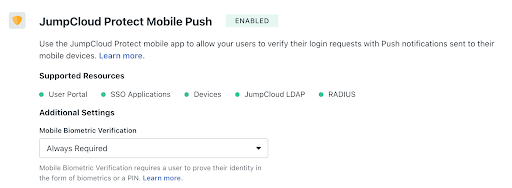
Mobile Biometric
Admins can activate mobile biometric on Push MFA, so that a user is required to use their fingerprint or face recognition as an additional factor to approve a login request. Here’s a look at what both the admin and user sees during this process:
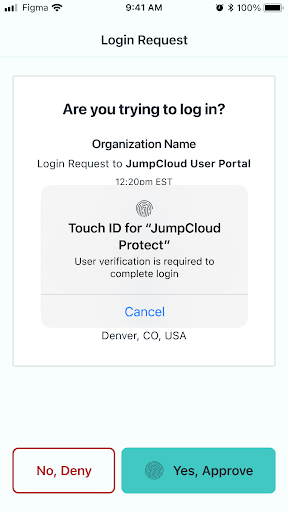
Conditional Access
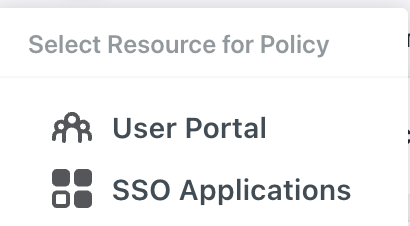
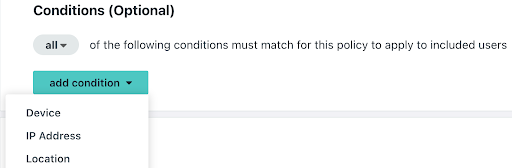
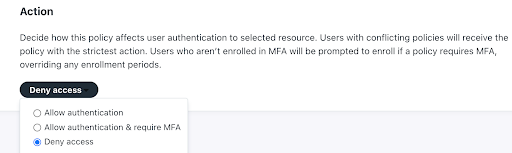
Admins can leverage JumpCloud Conditional Access policies for user portal and SSO application login attempts to restrict access from trusted devices or allow access only from the locations where an employee lives or places of travel. Simply select the Conditional Access option from the platform’s left-side navigation to open Conditional Access settings:
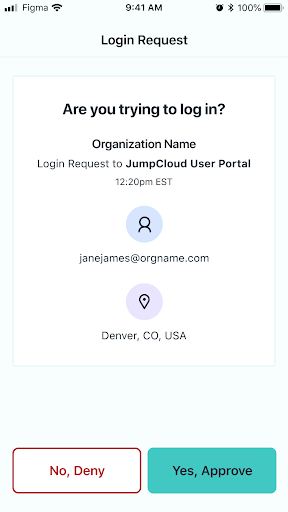
App and Location Information on Push Notifications
Admins can educate their users to check the application name for which the access request is made or the location from where the request was made before approving the request.
While application name or a granular location information may not always be available, when it is present it will help flag potentially fraudulent access requests.
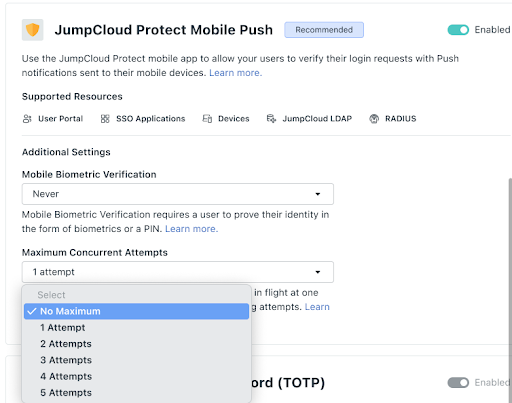
Blocking Anomalous Push Notifications
JumpCloud has added rules to restrict concurrent Push MFA attempts on web application and remote terminal logins to give admins peace of mind. This is enabled for organizations that use Protect Push as MFA, adds a protective layer to login events increasing the security posture with minimal user impact.
Note: This protective measure requires no admin action but admins has the option to balance user experience vs. security posture based on organization needs.
Avoid Account Takeovers with JumpCloud
As reported by Microsoft, requiring MFA has been shown to reduce account takeover attacks by 99%. While MFA does offer resistance to attacks, hackers have, unfortunately, found a way to circumvent them with push bombing and MFA fatigue.
So, it’s important for organizations to employ additional precautions such as adding phishing-resistant email tools and filters, educating users on stronger password practices for their personal and work accounts, and implementing stronger security practices to avoid security breaches.
JumpCloud continuously adds new features that increase the security posture of the platform to give IT admins and organizations peace of mind. IT admins can also better protect their organizations by adopting JumpCloud recommendations, starting with enforcing stronger password policies.
Ready to experience the ease of JumpCloud for your IT needs?





