Identity management in healthcare is a critical aspect of HIPAA compliance. With more and more applications offered from the cloud, healthcare organizations need to consider some form of single sign-on (SSO) to help increase IT control while making it easier for their users to access the applications they need.
Identity management as a practice spans many of the resources organizations use on a daily basis. In this post, we’ll detail how controlling access to cloud applications, such as electronic medical and health record (EMR and EHR, respectively) software, affects HIPAA compliance.
Managing Identities in Healthcare
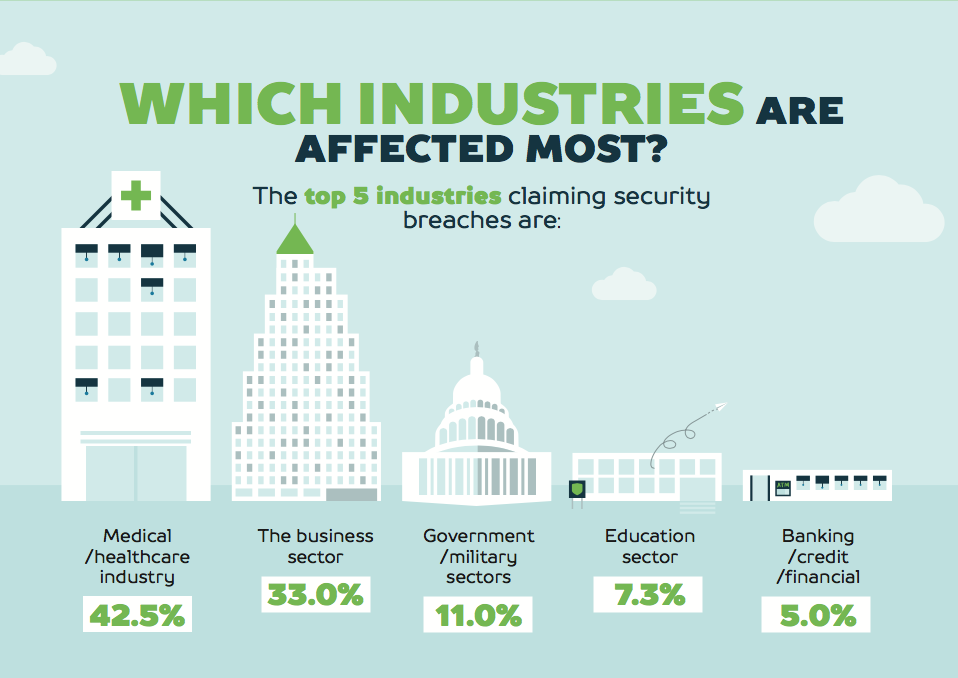
Although every industry must be vigilant about identity and access management (IAM), healthcare companies — the industry most frequently targeted by hackers — need to be the most careful of all.
Moreover, compromised identities are the number one attack vector for bad actors. These two factors illustrate just how badly healthcare organizations need strong, secure identity management.
On top of that, healthcare companies must always be conscious of HIPAA. HIPAA (Health Insurance Portability and Accountability Act of 1996) is a compliance requirement for any U.S.-based healthcare organization. As a part of its technical compliance regulations, HIPAA requires strong identity management. So, aside from the facts detailed above, healthcare organizations must have their identities tightly secured to ensure compliance.
SSO for Identity Management
Although many of the applications healthcare organizations leverage live on-prem, several of them are now leverageable from the cloud — including EMR/EHR. Traditional identity management solutions, such as Microsoft® Active Directory®, face troubles when extending their on-prem identities to cloud resources. That is why many organizations have turned to web application single sign-on solutions.
Using SSO allows end users to leverage a single identity based in their on-prem or cloud identity management tooling for all of their cloud-based applications. That means that end users have no need to write their passwords on sticky notes or make short, insecure passwords to ensure they can remember them. Some SSO providers offer multi-factor authentication (MFA) to make application identity access even more secure.
Although SSO is generally a solid move for all organizations and useful for achieving HIPAA compliance, it comes with a catch: Traditional SSO solutions are dependent upon an identity provider, like Active Directory. This addition of moving parts creates potential sources of compromise for organizations, as well as more integration work.
Beyond that, SSO solutions generally do not function as standalone identity management solutions; instead, they simply patch over AD’s inability to extend identities to the cloud. This cements identity management on-prem, which is a big step backward for organizations looking to shift to the cloud.
True SSO for Healthcare/HIPAA
What healthcare organizations need for their identity management is True Single Sign-On™. The concept behind True SSO is to provide a single identity for access to virtually all IT assets and resources. Backed by strong password management practices and MFA, True SSO is one of the best ways to secure identity management.
JumpCloud® Directory-as-a-Service® is focused on True Single Sign-On for a variety of IT resources including systems, applications, files, and networks all from one cloud-based platform. With JumpCloud, healthcare organizations can securely connect all of their users to virtually all assets and resources through a single set of credentials.
For healthcare organizations that are deeply rooted in AD infrastructure, JumpCloud features a complete AD Integration, which leverages AD as the identity source of truth while extending its identities to almost any resource that exists outside of the on-prem, Windows domain, such as cloud apps. Admins can also use JumpCloud to apply MFA to system, application, and network access, among other areas.
Independent auditor CoalFire Systems evaluated JumpCloud to see how its Directory-as-a-Service fared against HIPAA regulations. You can read more in their whitepaper on the topic.
Ultimately, with JumpCloud’s True Single Sign-On, IT organizations are granted more control over everything that people need to access. With JumpCloud, healthcare organizations can securely leverage innovative solutions from the cloud without sacrificing security.
Learn More
If you are interested in True Single Sign-On for HIPAA compliance and more, consider JumpCloud Directory-as-a-Service as your one-size-fits-all solution. You can try JumpCloud for free for your first 10 users and systems just by signing up for an account. Contact us to learn more.


