First, What Exactly is Identity Security?

Most would define identity security as the practice of ensuring that only the right people are accessing company resources; it also includes verifying users are who they say they are when they authenticate to a resource. Effective identity security usually involves having an identity and access management (IAM) solution in place that allows IT admins to centrally manage user identities and their access to IT resources. With an IAM solution, IT admins can enforce password complexity requirements, MFA, and securely provision/de-provision access throughout the network—components that are vital to any solid identity security strategy whether your network is in the clouds or on-prem.
Identity Security in the Past
Historically, identity security has been in the background of most security strategies, while the focus has been on fortifying the network perimeter. This worked okay in the past because resources only existed within the corporate network, behind firewalls, on-prem. This made it possible to keep them safely insulated from the ‘world’ (read: internet) , behind a heavily fortified perimeter. To access anything, employees would have to be physically inside the office and on its secure network, or gain access to it via VPN. Additionally, employees only needed a limited amount of IT resources to do their job, so there was a very limited number of touchpoints to keep track of.
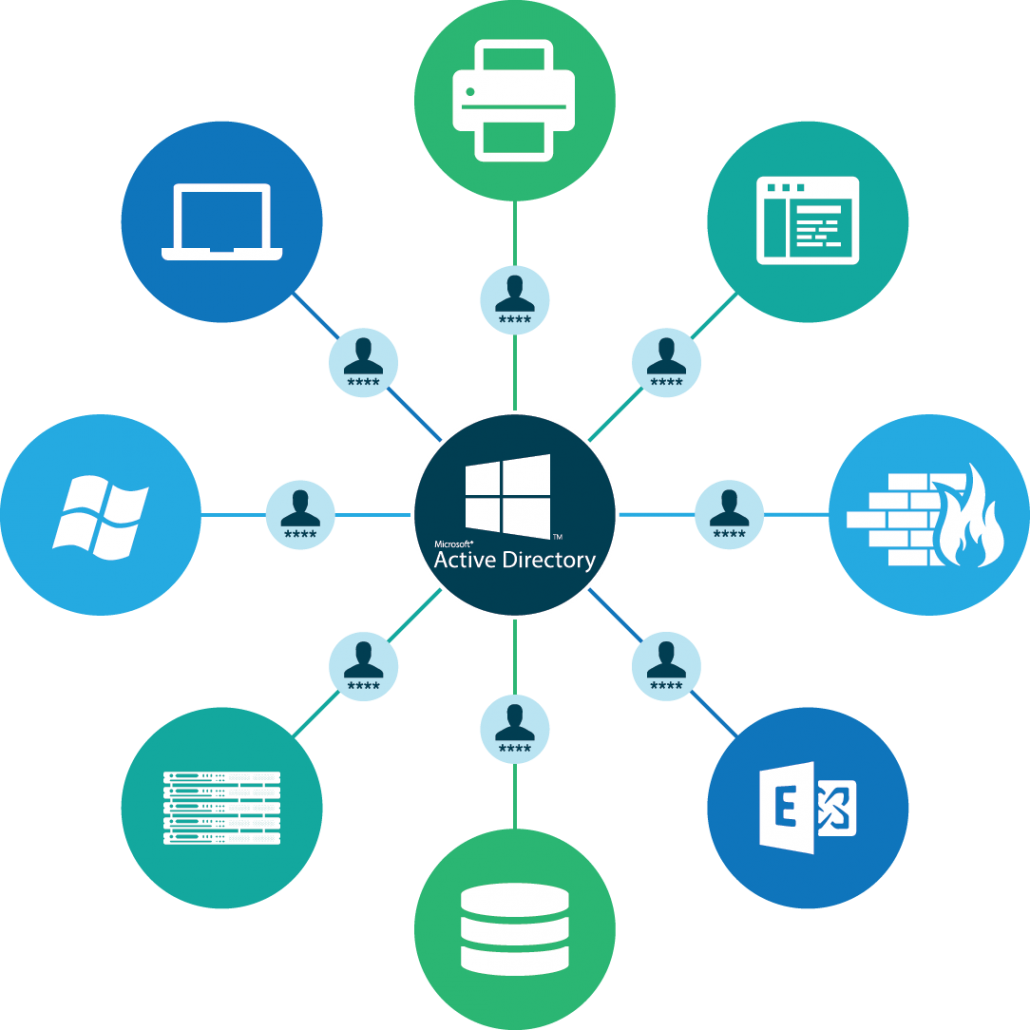
Identity security also remained a silent partner for some time because it seemed to take care of itself. This was, in large part, due to the monopoly that Microsoft® had over the IT landscape. From Windows®systems and Microsoft Office® to Active Directory® and Windows Server®, it was difficult to get through a workday without using a tool from Microsoft. Buying into this setup, though, provided organizations with secure, centralized user and resource management. When someone on the internal network accessed an IT resource, IT would depend on Active Directory to ensure only the right people were obtaining access to valuable company data.
This on-prem, Microsoft-centric environment led IT organizations to believe that they could trust the internal network communication taking place in their environment, and so that’s why they focused their efforts on protecting the network perimeter. This approach was commonly thought of as “hard on the outside, and soft on the inside”. Kind of like M&Ms®, but there are digital assets at the center instead of chocolate.
However, the IT landscape has undergone a substantial transformation over the last two decades as technologies have ‘lifted and shifted’ themselves to the cloud as subscribed-for services. This traditional on-prem approach to identity management, therefore, would show its strain and demonstrate itself as a non-viable and potentially insecure solution moving forward.
The Impact of Modern Technology on Security

First, many IT resources have moved to the cloud, and now most environments are utilizing web-based applications, cloud servers, cloud file storage solutions, and more. Second, the number of providers and platforms that organizations depend on has increased dramatically with the shift to the cloud. In turn, this has multiplied the number of touchpoints that IT and information security teams have to keep track of.
Fortunately, security methods have adapted accordingly in response to this explosion of diversity, and a new network security model was presented in 2009 that has redefined the relationship between IT organizations, users, and their data. It’s called Zero Trust Architecture or Zero Trust Security, and this updated network security model has been widely adopted since it burst on the scene, blueprinting how system resources and digital assets can be fortified with security from the inside out. The idea is relatively simple—by necessity, all network traffic and network users can’t be trusted. When implemented correctly, cybercrime can then be spotlighted and eradicated before it ever grows out of control.
Zero Trust Security is predicated on three core concepts to help redesign security throughout a network8. Networks must be:
- Easily managed and segmented for security and compliance
- Domain-less effectively (the concept of a centralized network won’t exist)
- Centrally managed from a single console
The last concept, central management for all networking elements, was further described as the “key to creating the network of the future.”8 However, organizations have found it difficult to create a centralized management system for all of their networking elements, and subsequently, they have lost their control over identity security as well. So, why is this a challenge?
Identity Security, Decentralized
The most ubiquitous directory service (Active Directory) was built to support on-prem, Microsoft-based IT resources, so IT admins have had to resort to a patchwork of independent vendors to assist with the secure management and ‘binding’ to Active Directory. These have included utilities to manage privileged user access to non-Microsoft servers; deploying SAML and other identity federation technologies to secure web based applications; specialized MDM solutions to control non-Windows systems; and more.
Sadly, these options have only ended up creating cumbersome workflows, introducing complex vendor relationships, and ultimately, increasing costs. Given this, it’s understandable why a good number of organizations have been slow to pour more resources into identity security solutions like identity and access management.
Yet, continuing to remain complacent about identity security will only increase your chances of getting breached, and here’s why: “The average company currently uses 1,083 cloud services in total.” If that’s not alarming, consider that only 108 of these are known services—meaning 975 unknown services on average per company.9
In other words:
- 10% Environment Under IT’s Control
- 90% Environment Outside IT’s Control
Further, the subscription-based, credit card model most applications leverage has made it too easy for entire departments of companies to bypass IT altogether to get the applications they want to use for their job. This has resulted in the proliferation of shadow IT where confidential streams of data exist outside of the walls of an IT organization’s governance, and therefore, outside of IT admins control. In today’s world, this is a nightmare for two reasons. One, company data is being accessed on upwards of 975 services that have little protection and oversight. Two, the little protection they do have is under the control of end users. What’s wrong with this?
The Human Factor
Human Factor 1: The Desire for Convenience
As a reminder from the introduction, 61% of users reuse passwords despite 91% knowing the security risks;4 the top two passwords for 2018 were 123456 and Password.5
Why do users have such a hard time with passwords? Well, a study from the Old Dominion University discovered a couple of things that may explain why users have trouble with this component to their credentials. The study found that,
“Users choose strong passwords only if they are willing to sacrifice convenience; it is not sufficient for them to simply understand it is important…10“

The study was also able to determine that users are willing to sacrifice convenience for accounts, that if breached, would result in deep personal loss (e.g., bank accounts). For accounts like email, on the other hand, the study indicates that users have no interest in giving up convenience for security because when it comes down to it:
“Users are not concerned about security issues unless they feel they will be affected if the account is misused.10“
Ultimately, users engage in poor password habits because they think they won’t be impacted by the consequences.
Human Factor 2: The Effect of Information Cascade

Another human factor that weakens security is a psychological phenomenon known as information cascade.11 Information cascade is the name for when a person notices the decisions of one person and decides to make the same decisions, even if they know it’s wrong. According to a study from the University of Basel in Switzerland, people are especially prone to copying the decisions of their supervisors.
The study found that:
82% of participants agreed with the decision of their supervisor despite privately having a different opinion.12
This means if a tenured employee stores their password on a sticky note that’s attached to their monitor, other employees will notice and do the same, especially newer employees.
Human Factor 3: The Power of Curiosity
Lastly, users are still prone to falling for phishing scams, and hackers are not looking to let up on this type of attack any time soon. The The 2018 Verizon Data Breach Investigation Report found that phishing was in the top three for the kinds of attacks that resulted in a security incident/breach.1 One of the reasons users continue to fall for phishing attacks, despite security training, has to do with their curiosity. In fact, a study conducted at Friedrich-Alexander University, Germany, found the following with their participants:
- 45% fell for a phishing email even though
- 78% reported they were aware of the risks of clicking on unknown links.
When asked why they clicked on the link, the large majority of participants said that it was due to curiosity.13
Sophisticated attacks are another reason why users continue to fall for phishing scams. Verizon’s 2017 Data Breach Digest14 presents an interesting example of one organization’s experience with a phishing attack that ultimately led to fraudulent wire transfers:

“An accountant within the organization received an email from “a customer claiming to have paid a late invoice. The email instructed the accountant to click a link and provide their email domain credentials to authenticate and review the payment receipt.”
Once the attacker had gained these credentials, they used them to “log into [the accountant’s] email account and study [the organization’s] wire transfer approval process by searching through emails. The threat actor even used previously sent invoices and tax forms to create fake versions that were used to…fabricate an approval email chain that they sent to [the] Wire Transfers Department.” Sadly, in this case the attackers ended up getting what they came for, and at the time of the Data Breach Digest being released, the organization was still working with law enforcement to recover their stolen funds.
So while a user’s curiosity is certainly a weakness, it’s important to realize that hackers also employ cunning tactics that make it increasingly difficult to spot a phishing email from a real one.
Even with threat actors’ cleverness at play, these three factors illustrate who ends up guarding your company data when identity security isn’t taken seriously: users who care more about convenience than the security of your company’s data, who are too easily influenced by the behavior that‘s occurring around them, and who are up against clever hackers who exploit their curiosity. It’s no wonder that users and their credentials were the largest attack vector in 2017—they are easy pickings for hackers who understand how to leverage human psychology for their own selfish gain.
Steps for Accelerating Identity Security
So, now that there is an understanding as to why it’s time to take identity security seriously, it’s time to transition into providing a few steps that your organization can take to accelerate your identity security strategy. Since the human element is at the center of whether or not identity security is a success, the solutions discussed below will help you counter users’ curiosity and strong desire for convenience. After all, “In the big data era, insiders are exposed to increasing amounts of sensitive data, posing huge security challenges to organizations.”15 Hence, the focus is on taking steps that strengthen the weakest link, whoever that may be.
Combating Curiosity

One way IT organizations can proactively address risk associated with user curiosity is by providing information security awareness training. When conducted in-depth, security awareness training has been shown to effectively teach users how to identify phishing techniques and improve their password and browsing habits. A 2010 study found that almost all of the participants involved with the study’s security awareness training completed it with the “correct idea about phishing and the dangers it poses both to the individual and to an organization.”16
Additionally, the type of delivery method for security training was found to significantly impact users’ understanding. A 2014 study on user preference for security training suggested that the best approach is to combine training methods and use them together to teach users about a specific cyber security topic. For example, the study focused on teaching users how to identify phishing attacks. They used a game-based training method to teach users what to look for in URLs in combination with text- and video-based training methods to cement their knowledge. The study found that users gain a more complete understanding from this multimodal approach, and almost all participants walked away with a correct idea about phishing.17 In theory, once phishing is recognized in the wild, the jig is up for hackers so to speak, and the temptation to open a curious email can be sidestepped.
In addition to making sure employees understand email security, here are a few other recommended talking points that should be discussed in your quarterly security training:
- IDENTITIES: Enable MFA everywhere possible and use passwords that are impossible to guess
- SYSTEMS: Remember, don’t insert flash drives of questionable origin and lock systems when leaving them unattended
- BROWSERS: Use a reputable browser like Chrome, Safari, or Firefox, only add plugins if they have a true business need, use an ad blocker, and don’t accept invalid SSL. certificates
- PHONES: Have a PIN that wipes your phone after a certain number of incorrect attempts and have remote wipe enabled on your phone
While security training is a fantastic starting point to mitigate human curiosity, technology can be a powerful layer to add to your security strategy; one that often works well at preventing users from making choices based on convenience.
Fighting Convenience with Convenience
In order to greatly combat the human factor of convenience, implementing single sign-on (SSO) technology has been recommended.10 This technology largely removes the temptation to repeat passwords for convenience. Thus, many security malpractices disappear.

However, not all SSO solutions are created equal. In fact, the term ‘SSO’ has become synonymous with web-based authentication using AD credentials because most SSO providers emerged as a means to connect Active Directory to the flood of web-based applications that had emerged in the early 2000s. But, as mentioned a few sections ago, web-based applications were only part of the changes that have taken place in the IT landscape. Modern IT environments are also leveraging cloud infrastructure hosted in AWS® or Google Cloud Platform™ , wireless networks, Mac® and Linux® systems, and file storage solutions like on-prem Samba-based file servers and cloud solutions such as Box™, Google Drive™, and more. Active Directory still does not natively support many of these modern IT resources. Therefore, solely implementing a web app SSO provider isn’t going to be enough for effective identity security because cloud infrastructure, Mac and Linux systems, and file storage will each require additional third-party add-ons or remain outside of IT’s control. In other words, your IT environment will largely remain decentralized and rely upon the ‘patchwork’ of vendors to ensure you’re covered.
Clearly, an effective identity security strategy doesn’t benefit from an approach that utilizes AD and a string of third-party solutions. Instead, it needs a new kind of directory service altogether. One that joins the move to the cloud, embraces resources of all protocols, providers, and platforms, and securely connects users to their resources regardless of location. Such a solution would make it possible to centrally manage user authentication to all IT resources, giving IT full control and widespread visibility over their environment.
Fortunately, there is one solution on the market that is providing a more comprehensive approach to SSO. By JumpCloud®, the concept of True Single Sign-On™ is delivered via the Directory-as-a-Service® platform. And, by implementing a True SSO solution for the enterprise as a whole, users no longer have to remember multiple passwords.
Securing Identities with True Single Sign-on™

Leveraging True SSO with JumpCloud enables organizations to provide their end users with a single set of credentials to access virtually all of their IT resources, including systems, servers, applications, file storage, and networks. End users only have to remember one secure password instead of hundreds, providing users with a more convenient workflow. Additionally, this comprehensive approach to SSO provides IT admins with centralized control over user authentication and authorization. When used with JumpCloud’s identity security features like MFA, Password Complexity Management, and SSH Key Authentication, IT is able to subtly guide users into making good identity security choices. For example, IT admins can ensure users are leveraging secure passwords and are rotating them on a regular basis. On top of that, IT can enable MFA across Mac and Linux systems as well as the JumpCloud admin and user console. This increases security around users accessing applications, tightens administrative access control, and bolsters Mac and Linux device security. Lastly, SSH authentication no longer has to be a hassle. Users can conveniently manage their public SSH keys without any intervention from IT—improving efficiency and security.
While you can’t stop hackers and bad actors from using phishing techniques to obtain your users’ credentials, what you can do is start taking action now to ensure their efforts to steal digital assets are in vain. Dumping the majority of your security budget into fortifying the perimeter with anti-malware, firewalls, IDS, and “anomaly threat” detection solutions has been shown to be a dated security strategy, and hackers are well aware that the weakest link lies within. As Zohar Steinberg, CEO of the security-driven payment company Token, once said:
“Any piece of your personal information, when in malicious hands, can be considered serious. Often times, once hackers get a hold of certain pieces of personal information, they can use various techniques to get more, so even something as an email can seem harmless, but can eventually lead to other information being stolen from that first step.”18
Take it from the execs who have experienced a data breach and upgraded their identity security game: revamping your identity security approach is fundamental for avoiding data breaches and defending the long-term success of your enterprise.
Sources
- 2018 Verizon Data Breach Investigations Report. Report. 2018. Accessed July 31, 2018. http://www.documentwereld.nl/files/2018/Verizon-DBIR_2018-Main_report.pdf.
- “Gartner Forecasts Worldwide Security Spending Will Reach $96 Billion in 2018, Up 8 Percent from 2017.” Hype Cycle Research Methodology | Gartner Inc. December 7, 2017. Accessed July 31, 2018. https://www.gartner.com/newsroom/id/3836563.*
- *Editors, Forbes Technology Council. “CEO Disconnect On Cybersecurity Increases Risk Of Breaches.” Forbes. March 21, 2018. Accessed July 31, 2018. https://www.forbes.com/sites/forbestechcouncil/2018/03/21/ceo-disconnect-on-cybersecurity-increases-risk-of-breaches/#4ec28f393e53.
- **”The Password Expose.” LastPass. November 1, 2017. Accessed July 31, 2018. https://lp-cdn.lastpass.com/lporcamedia/document-library/lastpass/pdf/en/LastPass-Enterprise-The-Password-Expose-Ebook-v2.pdf.
- ***”‘The Most Popular Passwords of 2018 Revealed: Are Yours on the List?’.” welivesecurity. December 17, 2018. Accessed December 17, 2018. http://welivesecurity.com/2018/12/17/most-popular-passwords-2018-revealed.
- †”2018 Annual Data Breach Year-End Review.” Identity Theft Resource Center (ITRC). February 2019. Accessed February 2019. https://www.idtheftcenter.org/images/breach/2017Breaches/2017AnnualDataBreachYearEndReview.pdf.
- Mathews, Lee. “File With 1.4 Billion Hacked And Leaked Passwords Found On The Dark Web.” Forbes. December 12, 2017. Accessed August 06, 2018. https://www.forbes.com/sites/leemathews/2017/12/11/billion-hacked-passwords-dark-web/.
- Kindervag, John. Build Security Into Your Network’s DNA: The Zero Trust Network Architecture. Report. November 5, 2010. Accessed July 31, 2018. http://www.virtualstarmedia.com/downloads/Forrester_zero_trust_DNA.pdf
- “What Is Shadow IT? How Do I Control It? Download Checklist.” Skyhigh. Accessed July 31, 2018. https://www.skyhighnetworks.com/cloud-security-university/what-is-shadow-it/.
- Tam, L., M. Glassman, and M. Vandenwauver. 2010. “The Psychology of Password Management: A Tradeoff Between Security and Convenience.” Behaviour & Information Technology 29, no. 3: 233-244. Academic Search Premier, EBSCOhost (accessed July 31, 2018).
- MBE, Oz Alashe. “The Psychology Of Cyber Security: How Hackers Exploit Human Bias.” HuffPost UK. November 27, 2017. Accessed July 31, 2018. https://www.huffingtonpost.co.uk/entry/the-psychology-of-cyber-security-how-hackers-exploit-human-bias_uk_5a159c0ce4b0815d3ce65bbd?guccounter=1.
- Schöbel, Markus, Jörg Rieskamp, and Rafael Huber. 2016. “Social Influences in Sequential Decision Making.” Plos ONE 11, no. 1: 1-23. Academic Search Premier, EBSCOhost (accessed July 31, 2018).
- “One in Two Users Click on Links from Unknown Senders › Friedrich-Alexander-Universität Erlangen-Nürnberg.” Friedrich-Alexander-Universität Erlangen-Nürnberg. August 25, 2016. Accessed July 31, 2018. https://www.fau.eu/2016/08/25/news/research/one-in-two-users-click-on-links-from-unknown-senders/.
- “Down to the Wire.” Data Breach Digest, February 2017. Accessed August 7, 2018. http://www.verizonenterprise.com/resources/reports/rp_data-breach-digest-2017-perspective-is-reality_xg_en.pdf.
- Cheng, Long, Fang Liu, and Danfeng Daphne Yao. “Enterprise Data Breach: Causes, Challenges, Prevention, and Future Directions.” Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery 7, no. 5 (2017). Accessed July 31, 2018. doi:10.1002/widm.1211.
- “The Positive Outcomes of Information Security Awareness Training in Companies – A Case Study.” ScienceDirect. June 09, 2010. Accessed July 31, 2018. https://www.sciencedirect.com/science/article/pii/S1363412710000099.
- Abawajy, Jemal. 2014. “User Preference of Cyber Security Awareness Delivery Methods.” Behaviour & Information Technology 33, no. 3: 236-247. Academic Search Premier, EBSCOhost (accessed July 31, 2018).
- Paul, Kari. “Everything You Wanted to Know About Data Breaches, Privacy Violations and Hacks” last modified April 3, 2018. https://www.marketwatch.com/story/at-what-point-should-you-be-concerned-about-a-data-breach-2018-04-03
