We’ve gotten so used to using the term single sign-on (SSO) that we don’t even realize the definition doesn’t make sense anymore. Today most people think of single sign-on as the way to sign in once using one set of credentials to access web applications. But since that definition of SSO only covers web applications, shouldn’t we be calling it “web application SSO”?
In theory, single sign-on should describe exactly what the name implies — the ability to leverage a single set of credentials to sign on to all resources needed. That being said, even web app SSO is not really single sign-on, as it doesn’t facilitate identity federation to all of the other resources people use to get work done.
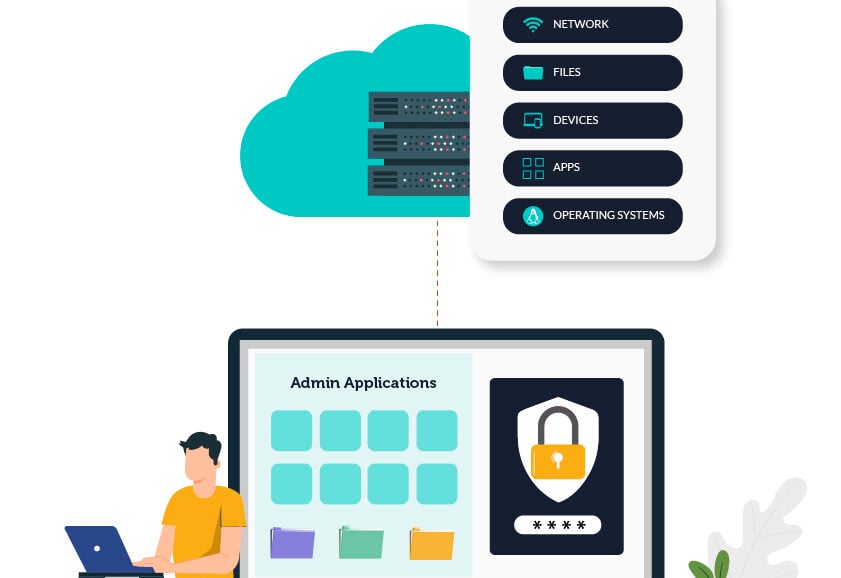
In a modern IT environment, users need to sign into resources such as cross-OS devices, WiFi networks, VPNs, physical and virtual file servers, legacy apps, web apps, and more. So, even though web app SSO provides a simple way to access web applications, with only a web app SSO point solution in place, users still have to sign in separately to access all of these other resources. From the user’s perspective, this version of “single sign-on” is actually single sign-on to each silo.
This is where the term True Single Sign-On™ comes into play — True SSO™ is the means to allow users to securely and efficiently access virtually all of their IT resources, including the ones listed above, with a single, secure set of credentials. JumpCloud offers True SSO solutions among many other features across the JumpCloud Directory Platform which enable remote and traditional work while solving a multitude of identity and access management (IAM) problems that IT teams and organizations face.
Why Web App SSO Isn’t Enough
Even with web app SSO in the mix, it has been a hassle for IT to keep track of all the different identities a single user might have in order to access all of their resources, which means that onboarding that user, keeping them activated and productive while they work, and then (eventually) deprovisioning that user should they leave temporarily or permanently from all of those resources is a nightmare.
For the IT admin, True SSO from the cloud means a central place to manage a single identity for each person that is then federated to each resource they need from the core identity provider (IdP) promoting security, productivity, and tighter control over identities. For the user, it means fewer passwords to remember and easier access to their devices, networks, apps, and other frequently used resources, resulting in higher productivity.
Today, a complex cloud-forward environment demands a modern and complete cloud SSO solution. Providing true single sign-on services to an organization’s users is a core part of what IT admins are charged with, so it’s important to understand why SSO often revolves around web apps, how it’s changing to meet modern needs, and how to implement a complete single sign-on solution.

The Creation of Web Application SSO
The reality is that when single sign-on first entered the market over a decade ago, it was possible to use it in a way that allowed you to access all of the resources you needed. This was all at a time when just about everything was on-prem: users had to be physically present at their desks, systems were hardwired into private networks, applications were primarily Windows-based and came in a box with installation disks. You had Microsoft Active Directory (AD) and a domain controller to authenticate and authorize access to everything on-premise, which was largely Windows-based devices and applications.
Then, as cloud apps emerged and increased in popularity, web application SSO providers also surfaced, marketing a product that was meant to be an add-on solution to AD. The idea was that by extending AD, users could then leverage one set of credentials to gain access to on-prem resources and web applications, admins could retain control over user access and management beyond what was possible with AD alone — and everybody wins. It seemed like SSO and AD were a perfect match. So when it began, true SSO was a reality, albeit a multi-tool solution in a simplistic environment.

How Modern SSO Has Evolved
However, nothing is constant in the IT world, and before long, this seemingly perfect relationship between AD and SSO began to break down. Over the next decade, IT infrastructure exploded into a complex set of cross-OS devices, applications, network infrastructure pieces, and services. The traditional concept of single sign-on slowly became SSO access to one fraction of resources within the IT environment, and then became synonymous with web application access. Your devices, on-premise applications, networks, and other resources were, and continue to be, excluded from this version of SSO.
This meant that Active Directory, which was and has always been designed for managing on-prem Windows resources, wasn’t as effective. As a result, the SSO solutions that were built on top of AD suffered the same fate — they became obsolete for many organizations that needed a more comprehensive approach to SSO and identity access management.
These monumental changes in the IAM space created a significant opportunity in the realm of single sign-on. A need for more comprehensive IAM and SSO emerged, and the solution was created in the form of a cloud-based directory platform. JumpCloud has revolutionized how people think about single sign-on with the JumpCloud Directory Platform that provides a true central identity for users to connect to virtually any IT resource they need to be productive and efficient, including cross-OS devices, legacy and cloud applications, networks, servers, and more, regardless of provider, platform, protocol, or location.
Why True Single Sign-On Is an Important Achievement
In response to all of the changes that have happened in IT over the last decade or so, SSO providers are experiencing an identity crisis. Users still want one set of credentials for access, but for all of their IT resources. Web app SSO alone won’t do — instead, admins want the ability to flip a switch to authorize access for everything. Unfortunately, traditional web app SSO providers cannot handle this request.
What’s more, the entire market is shifting toward True SSO solutions that are part of bigger, modern IAM platforms. This can be seen through recent acquisitions that highlight a common theme — the market is moving away from web app point solutions to holistic solutions that allow admins to control and facilitate access to virtually all IT resources.
True Single Sign-On is the holy grail for IT organizations. It simplifies an end user’s life and allows them to be more productive. The end user spends far less time worrying about how to access IT resources and more on just using whatever tools they need to do their job.
For IT admins, the concept of True SSO is massively beneficial too. It centralizes control, increases security, and reduces support time. The only reason IT organizations haven’t pursued it is because for a long time, they thought that it was impossible (mainly due to the heterogeneous nature of IT today). There are just so many different platforms and protocols that need to be supported, how could one identity management platform do it all?
This is all possible through a modern cloud IAM and SSO solution that integrates with devices, on-prem and cloud applications, networks, servers, and more. A solution like this includes the following capabilities:
- Support for Mac, Windows, and Linux devices
- Support and use of a wide range of protocols: LDAP, SAML, RADIUS, SSH, and more
- Multi-factor authentication (MFA)
- Conditional access policies
- Password policies
- Privileged access management (PAM)
- Group-based access control
- Immediate provisioning and deprovisioning of access to different resources (JIT/SCIM)

JumpCloud’s Modern IAM and SSO Platform
The JumpCloud Directory Platform takes a new approach to single sign-on and includes all of the capabilities and features listed above. Get True Single Sign-On capabilities across virtually all of your IT resources, and enjoy a cloud directory platform that offers comprehensive identity and access management with JumpCloud. Forget about managing an on-prem directory that requires a variety of extra add-on solutions to get it to the level you need.
With JumpCloud, you get a centralized place where you can manage and control identities, devices, and your overall IT environment from a single pane of glass. This allows IT admins to retain a high level of control over devices, identities, and access, all without leaving any resources out of reach and unmanaged.
Try JumpCloud’s Solution Free
With the modernization of the IT environment, the traditional concept of web app SSO isn’t enough for many organizations, nor does it rival true identity and access management solutions.
Test out JumpCloud’s modern, simplified IAM solution with True SSO, and see if it’s right for your organization! Start a free 30 Day Trial to access the entirety of the platform for free.