UK businesses have experienced a sharp increase in cyber incidents over the past several years. In 2022, 39% of UK businesses reported having experienced a cyber attack, according to the government’s Cyber Security Breaches Survey of 2022.
The most common offender by far was phishing, followed by more sophisticated security breach methods such as ransomware, malware, and denial of service. The UK government responded by increasing its list of security controls for Cyber Essentials Plus in early 2022.
The recommended security framework for UK businesses now includes standards for multi-factor authentication (MFA), mobile device management (MDM), cloud systems, and Bring Your Own Device (BYOD), among other cybersecurity best practices.
In addition, applicants must now provide evidence to support their self-assessment questionnaire responses. The good news?

Meeting compliance requirements for Cyber Essentials Plus isn’t as complex as it may initially seem. With the right tools and systems in place, IT admins can breeze through most checklist items fairly quickly.
Keep reading to learn how to complete and document your organisation’s Cyber Essentials Plus requirements with less stress.
What Is Cyber Essentials Plus?
Cyber Essentials Plus is a government-backed data security framework designed to provide organisations with a strong defense against cybercrime.
The National Cyber Security Center (NCSC) and the IASME Consortium worked in partnership to develop the latest security recommendations included within the Cyber Essentials framework.
Essentially, the standard provides a security baseline for every business in every industry against five key areas:
- Access control
- Firewalls and routers
- Malware protection
- Secure configurations
- Software updates
Cyber Essentials Plus is the more stringent version of Cyber Essentials; the latter includes a lightweight self-assessment and internal vulnerability scan.
Cyber Essentials Plus, on the other hand, requires an additional technical audit of in-scope systems, an on-site or remote assessment, internal vulnerability scans, and an external vulnerability scan conducted by the certification body.
The internal scan is set up to check patches and system configurations. Security and anti-malware tests ensure your organisation’s systems are resistant to malicious email attachments and web-downloadable binaries.
And, finally, the external scan verifies patches and system configurations for public-facing infrastructure.
Why Is Cyber Essentials Plus Important?
Following the Cyber Essentials Plus security framework is crucial for any organisation wanting to avoid security breaches and safeguard stakeholder data. Here are the most common reasons businesses choose to achieve Cyber
Essentials Plus certification:
- Prevent approximately 80% of cyber attacks.
- Secure potential discounts on cyber insurance.
- Avoid costly downtime (due to security breaches).
- Avoid class action lawsuits facilitated by customers.
- Avoid reputational damage and loss of goodwill.
- Avoid theft of intellectual property.
- Improve supply chain security.
According to the Gauntlet Group, many insurers have “lost an appetite to insure cyber risks and have withdrawn from the market. Some have chosen to tighten up policy wordings, or not cover certain cyber scenarios such as social engineering, or insist on the insured having much higher levels of cyber security protection in place.”

As reported by Fitch Ratings, premiums increased a record 34% in Q4 2021 alone and standalone cyber coverage policies increased in price by 92% across the year.
Translation: many insurers now see latent “silent” cyber risk exposures as too risky to include in general commercial policies. Of course, many factors go into calculating insurance premiums: industry, volumes of data collected, types of data stored, and annual revenue are just a few of them.
With that said, organisations can reduce their cyber insurance premiums by proving an increased level of self-protection. Of course, the most fool-proof way to put insurance providers’ minds at ease is with verified compliance.
How to Streamline Cyber Essentials Plus Preparation
The Cyber Essentials Plus assessment includes a total of 32 data compliance requirements. Find a tool capable of checking off as many boxes as possible, and you will dramatically cut your compliance preparation time.
This is where the JumpCloud Directory Platform comes into play. JumpCloud can assist IT managers with 20 of the 32 requirements as shown below. In most instances, the requirements JumpCloud cannot help with involve simple actions that don’t require a toolkit.
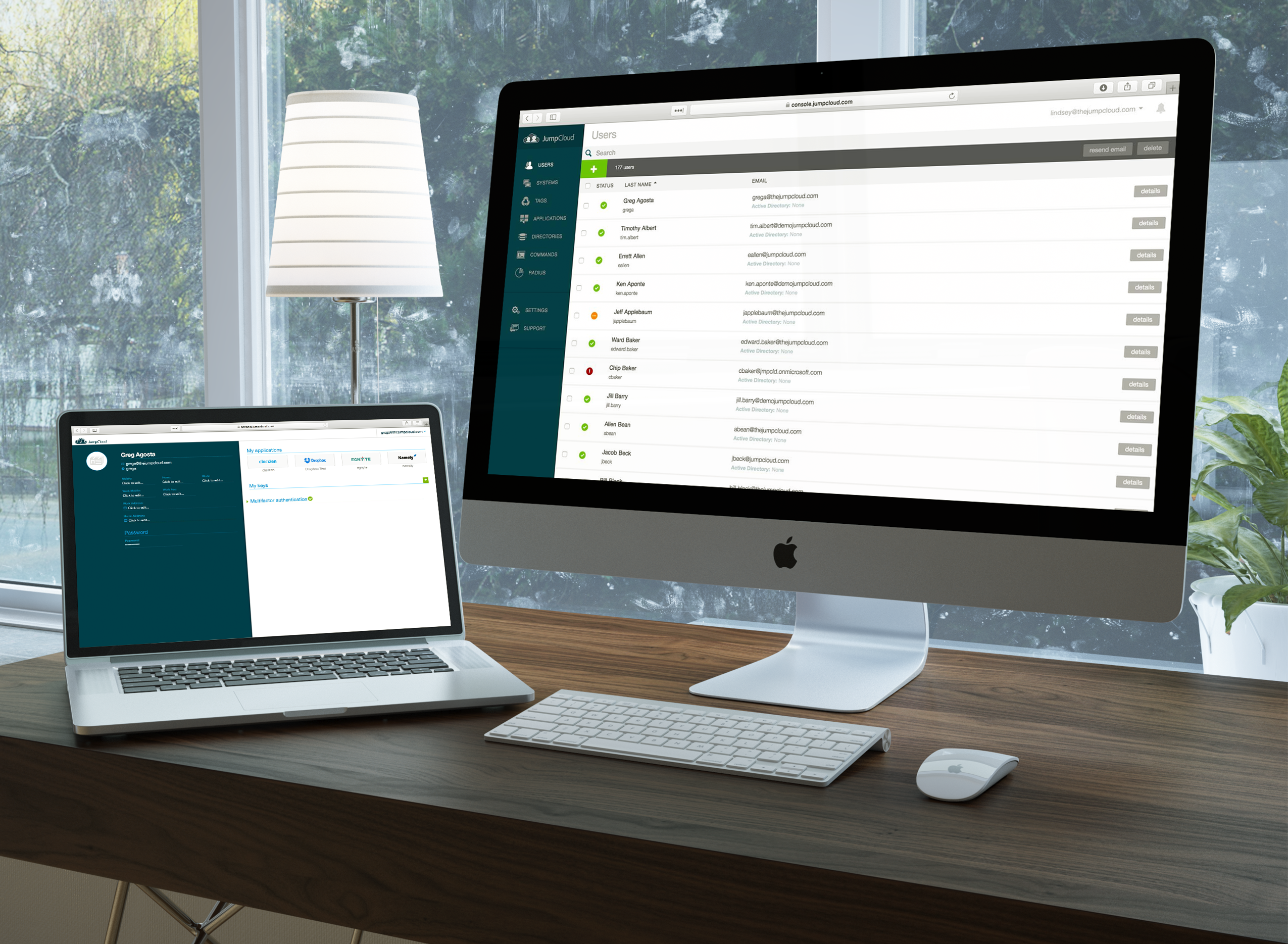
JumpCloud includes capabilities for overseeing hardware devices, software/firmware updates, secure configurations, password management, malware protection, and identity and access management.
Some of the Cyber Essentials Plus Element Checks it Can Simplify are:
1. Does someone in your organisation have a list of all hardware devices (laptops, smartphones, firewalls, routers) that you use?
One of the simplest aspects of data compliance is maintaining a list of organisation-wide devices. If you don’t already have a list you may need to consult with coworkers, check purchase requests/receipts, and piece together every traceable device you can.
Lost devices that contain proprietary information pose a significant security risk.
The JumpCloud Directory Platform can assist in the creation of a Device List. Any workstation, mobile device, or server managed by JumpCloud will auto-populate in the Devices Section of the management console. Admins can then download the list as a CSV for auditing purposes.
2. Do you have a list of all software/firmware used on devices within your organisation?
In addition to device lists, aim to always know which types of software and firmware are in use across departments. JumpCloud’s System Insights feature makes it easy-peasy to determine which software has been installed on which devices.
The platform automatically interrogates the device relative to software and allows it to be downloaded as a CSV. This functionality also extends to browser plugins, Chrome extensions, and Firefox add-ons.
3. Do you have any virtualization infrastructure within your organisation?
If you’re subscribing to Infrastructure as a Service from a cloud service provider (e.g., Microsoft’s Azure Virtual Desktop, Citrix managed desktops) you’re responsible for applying the Cyber Essentials controls to the virtual environment you configure and use.
This includes virtual desktops, virtual local area networks (VLANS) including virtual firewalls, and virtual Switches. Those who own or rent on-site servers will need to apply the Cyber Essentials controls to them.
Translation: always keep everything licensed, updated, and patched. You can install the JumpCloud agent on AWS Servers, Azure Servers, and GCP servers for streamlined management and reporting.
4. Do you have automatic updates enabled on all your software?
Ensure software is always up to date by turning on automatic updates on each of your company devices. This way patches will automatically be applied as they are released. Many devices now have automatic updates conveniently turned on by default. JumpCloud’s OS patch management functionality allows for simple remote enforcement of all devices.
5. If not, do you have a process for applying all high and critical updates within 14 days?
Many larger organisations must consider that certain software updates can stop other software from working properly or cause features to break. If you fall into this category, aim to fully test each update on a controlled sample of devices, before applying it company-wide.
Using JumpCloud, IT admins can seamlessly create an effective and practical plan to roll out OS patches, taking into consideration their organisation’s and employees’ time, resources, and needs.
By defining and automating specific rollout schedules as needed for Windows, Mac, and Linux (Ubuntu) devices, manual work is practically eliminated. In addition, admins can customise notification settings to devices and access a Visibility Dashboard with fleet OS distribution and current OS release trains
6. Do you have a list of all the cloud services you use in your organisation?
Cyber Essentials Plus requires admins to maintain a list of all the cloud services used within the organisation. This includes Software as a Service ( SaaS) for everyday tasks such as creating and sharing files, signing and sending contracts, and project management.
Although JumpCloud can not audit what cloud services are being utilised within the organisation it can integrate with these services. Once completed JumpCloud can act as an inventory of cloud services used within the organisation, report on who is authorised to access them, and through directory insights provide a rich audit of who has accessed them.
7. Have you enabled MFA on all accounts to access all the cloud services that you use?
One of the major updates to the Cyber Security Plus 2022 protocols is the requirement for two-factor authentication, also known as multi-factor authentication. In addition to a username and password, users must provide a secondary for identification to access data.
JumpCloud Conditional Access policies make it easy to enforce MFA on cloud services using JumpCloud to protect Push, OTP, or WebAuthN such as touchID, Windows Hello, or FIDO2 keys.
JumpCloud can also take this one step further by restricting service access from certain geographies, restricting the service to known IP addresses, and restricting access to managed devices. You can implement these policies individually or in combination.
8. Have you been through the devices that you have and disabled the software that you don’t use?
Review your devices with a view to removing services, software, or applications that are not required. This might include a server running a default web server that you don’t use, additional accounts on some devices that are not required, or any additional software that you don’t use.
JumpCloud Policies and commands can be used to both report on and disable software running on devices that are not needed
9. Have you ensured that all the accounts on your devices and cloud services are only those used as part of your day-to-day business?
JumpCloud can assist in the auditing of user accounts on devices. If dormant accounts exist JumpCloud’s commands functionality can be used to either disable or remove those accounts. Relative to cloud applications where supported user lifecycle management can be used for both provisioning and de-provisioning of accounts
10. Is “AutoRun” or “AutoPlay” disabled on all of your systems?
Auto-Run or Auto-Play is a setting that automatically runs software on a DVD or memory stick. It is important to disable Auto-Run or Auto-Play in order to avoid automatic installations of unauthorised software.
When Auto-Run or Auto-Play is disabled, the user is prompted to give permission every time before the software is allowed to run or play. Use JumpCloud policies to disable autorun/autoplay on JumpCloud managed devices
11. For mobile devices, do you set a locking mechanism on your devices to access the software and services installed? This might be a pin number, a password, face scan, or a fingerprint.
Unfortunately, company devices sometimes get lost, stolen, or misplaced. Setting a unique 6-character or more password, pin number, or biometric method to unlock devices minimises the risk of a breach in these situations.
JumpCloud’s iOS device management allows you to configure both corporate and personal devices with device locks. Android is coming soon.
12. Do you ensure that all default passwords on all devices are changed?
It’s not difficult to find device default passwords with a quick internet search. Attackers sometimes use a default username and password combination to attempt a connection, even if the device is within your internal network.
Simply by changing the default password (and username if possible), you have immediately made a hacker’s job more difficult. JumpCloud user management ensures employees change default passwords at first login.
13. Do you make sure that each user requires their own username and password and that there are no shared usernames/passwords?
JumpCloud MDM ensures no shared usernames and passwords exist. When shared usernames and passwords are unavoidable the JumpCloud password manager allows for the auto-creation of long complex passwords that can be securely shared between team members.
The password manager also allows for the sharing of OTP codes giving JumpCloud users the unique ability to share both passwords and OTPs.
14. Do you have something written down to advise all users about creating good passwords? Does your policy specify the technical controls to manage the quality of passwords used within your organisation? Does the policy include a process for when you believe that a password or an account has been compromised?
A password policy must detail the process for creating passwords for all work
accounts. A password for a work account must include one of the following:
- Using multi-factor authentication
- A minimum password length of at least 12 characters, with no maximum length restrictions
- A minimum password length of at least 8 characters, with no maximum
- Length restrictions and automatic blocking of common passwords using a deny list.
JumpCloud’s password policy allows you to centrally configure a password policy that meets your requirements in terms of length, complexity, originality, and aging.
15. Have you put measures in place to protect accounts against brute-force password guessing?
Brute force attacks use computers to target a login page where hackers may try different character combinations until the correct combination is found to crack the password.
Depending on the length and complexity of the password, cracking it can take anywhere from a few seconds to many years! Using a long and complicated password is a good way to protect your data from a brute-force attack.
Use JumpCloud to implement MFA for SaaS apps, device login, LDAP, and radius-connected resources. A central configurable lockout policy further enhances protection against brute force attacks
16. Are all of your computers, your laptops, and your mobile phones protected against malware by using one of these options? (Select the ones that apply.)
You can largely avoid the potential harm from malware by:
- Detecting and disabling malware before it causes harm (anti-malware software)
- Executing only software that you know to be worthy of trust (allow listing)
- Executing untrusted software in an environment that controls access to other data (sandboxing)
Although JumpCloud is not an EDR product, the platform gives admins the option of denying and/or allowing application access to devices. It’s worth emphasising that both application whitelisting and blacklisting have their respective pros and cons.
In addition, JumpCloud provides seamless integration with antimalware software.
17. Is there a process you follow in order to create a new user account?
Consider whether a user account creation process would help your organisation. It might be that only once someone has signed their paperwork and received clearance (if appropriate) they are issued with a computer user account.
JumpCloud streamlines the new user account process making it both easier and more secure for IT teams.
18. Have you a process for tracking user accounts of people who join or leave?
Consider whether you could develop a movers, leavers, or joiners process. That means when someone joins your organisation, their account permissions are recorded and approved. Conversely, when they leave, their account is disabled (or removed).
Use JumpCloud to improve user provisioning, de-provisioning, and modification. For example, a manager notifies the HR department that an employee just put in their 2-week notice.
If the organisation has integrated the JumpCloud platform with its HCM system, any changes made within the HCM will automatically carry over to the central directory and IT resources.
Not only does this save time, but it improves organisational security by reducing identity sprawl and ensures the IT department always has the most recent employee information at their fingertips.
19. Is there a process that is followed before a member of staff is given an administrator account?
JumpCloud’s user account creation process can help your organisation build this process. Once someone has signed their paperwork and received clearance (if appropriate) they are issued with a computer user account.
You can then create a set of rules around administrator accounts, clarify who has the administrator accounts, and ensure that these accounts were not used for emails and web browsing.
Regular account activity is risky on an administrator account as any compromise can happen with a higher set of permissions, meaning there is potential for greater harm to your System.
JumpCloud can be used in conjunction with a policy to centrally control what rights a user has on any device. Users can be easily switched from standard users to admins and back again centrally from the JumpCloud admin consoles
20. Do you have a process for ensuring that employees do not use administrator accounts for day-to-day activities such as browsing the internet and checking emails?
Staff should have separate user accounts if they are expected to perform both administrative and routine functions and they should log in with their standard user accounts for day-to-day tasks.
Administrator accounts should be used only to install or modify the software and to change system settings. It’s often necessary to use a combination of policy and staff training to achieve this requirement.
Use JumpCloud to ensure all user accounts are standard accounts and elevated to admin accounts when required. Click here to check out a complete CyberSecurity Plus checklist.
Streamline CyberSecurity Plus Compliance with JumpCloud
Unifying your stack with JumpCloud simplifies the compliance process by relieving admins from tool sprawl overwhelm. The platform combines Linux, Windows, Mac, and iOS devices behind one pane of glass for convenient heterogeneous device management.
JumpCloud also handles patch management, multi-factor authentication (MFA), and several other crucial cybersecurity measures. Learn more about how much easier compliance can be with the JumpCloud Directory platform.





