Updated on August 14, 2024
(Editorial note: Although this tutorial walks you through the technical steps to bind Macs to Active Directory (AD), recent changes from Microsoft and Apple have made the tutorial below largely unnecessary, depending on how you have AD set up in your environment. The practice of binding Macs to AD has largely been deprecated due to the administrative challenges that it creates and inability to work with an identity provider (IdP) such as JumpCloud or Google. JumpCloud makes it possible to use/federate Google, Entra ID, or Okta credentials to access resources.
Apple has also introduced its Platform SSO feature to macOS, which developers can use to add single sign-on (SSO) extensions. Furthermore, it’s important to know that joining a Mac to an AD domain for authentication will result in password mismatches between the login credentials and the local user’s Keychain password.If you still find it necessary to manage Macs through AD in your environment, the steps below outline the process. However, you should consider using JumpCloud’s integration with AD because it solves this identity and access problem for you by centralizing communications between AD and your workforce. You can activate a free demo today or check out our guided simulations.)
This article continues our series on helpful commands for every Mac admin. The first article in the series explored how to enable SSH to access a remote Mac’s Shell securely while the second article examined how to change the computer name, hostname, and local hostname.
Active Directory (AD) provides crucial user and device management capabilities as an identity provider for IT systems. However, many IT admins find it challenging to manage Macs with Active Directory. Given that Active Directory is a sought-after identity and access management solution, IT admins must still face the challenge of integrating it effectively with macOS.
This article will examine how you can join a Mac to Active Directory services via the use of a command in the terminal app.
What Is a Directory Service and What Is Active Directory?
Directory Services
Before delving into Active Directory, it is critical to understand what directory services are all about. Simply put, directory services organize and manage users and IT resources within a network and enable administrators to granularly control user access to those IT resources. For instance, employees in the marketing department would have access to sales content but would be restricted from accessing financial information.
A directory can be defined as the ultimate source of truth used in verifying a user identity, and maintains information such as user ID, group membership, SSH keys, passwords, and other unique identifiers.
Directory services own the authentication and authorization process. They verify users’ identities (authentication) against the directory’s user database. If the specific access credentials provided match the credentials in the database, a user is granted access (authorization) to their respective IT resources. Otherwise, the user is denied access, which makes directory services a key cybersecurity tool.
Active Directory
Active Directory, a common identity provider, was developed by Microsoft. It pioneered the era of identity management at a time when the majority of IT infrastructure was Windows-based and managed on premises.
With AD in place, IT admins can connect users and/or groups to IT resources and control policies. The information stored in Active Directory includes users, groups, networks, digital assets, systems, and applications. It also defines the relationship between those entities.
How to Join a Mac to Active Directory Services via Terminal
There are several ways to bind a Mac into Active Directory services. Methods include running a command in the terminal app, using Apple Directory Utility, or using a cloud identity bridge. In this section, we will explore how to connect Mac to Active Directory services using the terminal app.
1. Launch the terminal app on your Macbook.
You can do this by searching “terminal” using the Spotlight search option on your computer or navigating through Applications > Utilities > Terminal.
2. Enter and run the command.
You can use the dsconfigad command to bind a Mac to Active Directory via the terminal app. All you need to do is run the following command. Note that you need to replace the domain name, computer name, password, etc. with your specific information.
sudo dsconfigad -preferred <adserver.example.com> -a <computername> –domain example.com -u administrator -p <password>
The arguments in the command are explained as follows:
-a: This adds your computer to the Active Directory. Replace<computer-name>with your actual computer name.-u: Specifies the admin username that has the rights to bind the Mac to AD. Replace<username>with your computer’s username.-domain: States the domain name of the domain you want to join. Replaceexample.comwith the domain you want to join.
After you have binded a Mac to the domain, you can also use dsconfigad to set the admin options in Directory Utility by running the command below:
sudo dsconfigad -alldomains enable -groups domain <[email protected]>, enterprise <[email protected]>
Per Apple, the Directory client can sign and encrypt the LDAP connections used to communicate with Active Directory. You shouldn’t downgrade your domain’s security policy to support Macs.
Using Mac’s Built-In Apple Directory Utility
One of the services in Apple Directory Utility is Active Directory Connector which generates all the necessary attributes for macOS authentication from AD user accounts. It also supports AD authentication policies like password changes, expirations, and security options. You can take the following steps to bind Mac to Active Directory using the utility.
Open User & Groups and Join the Network Account Server
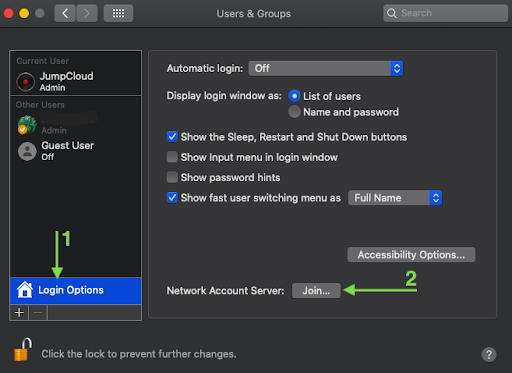
- Navigate through System Preferences > User & Groups.
- Click the lock icon and provide your user password.
- Click Login Options (Figure 1).
- Next to Network Account Server, click Join (Figure 1).
Open the Directory Utility
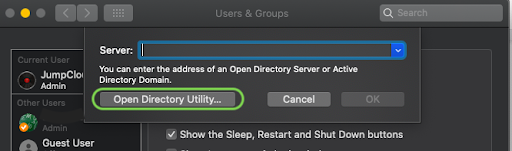
A pop-up shown in Figure 2 will appear. Click Open Directory Utility as shown in Figure 2.
Connect to Active Directory
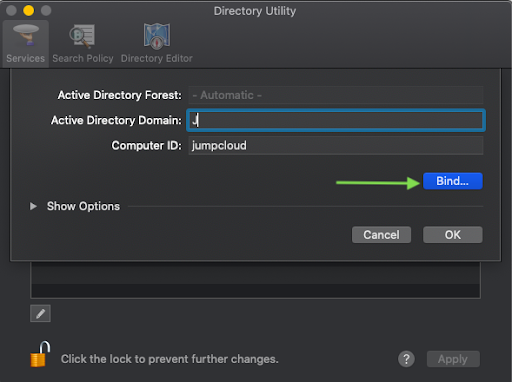
Type your Active Directory domain and click Bind (Figure 3).
Wrap Up
Binding a Mac to Active Directory enables macOS access to the legacy identity management solution. In this article, we have explored how you can join a Mac to AD services either through the terminal app or via the use of Apple Directory Utility.
Another option for a more seamless connection is to leverage a cloud identity bridge, i.e., a bridge that allows you to extend AD-bound identities to IT resources unable to directly bind to AD, such as Mac devices, Linux servers, remote Windows machines, and web applications.
While historically it was possible to layer together multiple point solutions to act as that bridge, today’s IT environments have become much more complex as the cloud has matured and remote work has gained prevalence. The JumpCloud Directory Platform was built to eliminate this complexity and empower modern IT admins to build connections between all of their IT resources with a single cloud-based console.
If you’re not ready to replace AD altogether, then JumpCloud’s Active Directory Integration could be the answer. This lightweight approach integrates with a cloud-hosted directory service that allows IT admins to have full user and device control over their Mac fleet, as well as Windows and Linux devices.
To learn more about what is possible with AD and JumpCloud, check out our whitepaper AD and JumpCloud: A Complete IAM Approach.





